FromDocToPDF Toolbar is a browser extension published by Mindspark InteractiveNetwork, that usually comes bundled with other potentially unwanted programs. The toolbar is distributed heavily through advertising networks.
This toolbar automatically sets your default search engine to MyWebSearch, it also sets your new tab to the DocToPDF welcome page. This toolbar ads startup registration tasks that allow it to start automatically with Windows, it gathers website traffic, clicks, data, and personal information and sends it to its ad network. Multiple anti-virus programs have detected FromDocToPDF as a browser hijacker and therefore is potentially unwanted and recommended for optional removal
About Browser Hijackers
Browser hijacking is actually a form of unwanted software, commonly a web browser add-on or extension, which causes modifications in the web browser’s settings. Browser hijacker malware is developed for numerous reasons. Often, hijackers will force hits to internet sites of their preference either to increase traffic producing higher advertisement earnings, or to gain a commission for every user visiting there. While it might seem naive, these tools were created by vicious individuals who always attempt to take full advantage of you, so that they could make money from your naive and distraction. Furthermore, hijackers could make the whole infected system vulnerable – other dangerous malware and viruses will seize these opportunities to get into your computer system very easily.
Key signs that your web browser has been highjacked
There are several signs that could indicate a browser hijacking: home-page is changed; you see new unwanted favorites or bookmarks added, typically directed to ad-filled or porn websites; the default online search engine is changed and your browser security settings have been cut down without your knowledge; unwanted new toolbars are added to your browser; your browser will display constant pop-up ads; your web browser starts running slowly or exhibits frequent errors; You can’t access specific sites, in particular anti-malware websites.
Precisely how browser hijacker infects PCs
A browser hijacker could be installed on your PC when you visit an infected website, click on an email attachment, or download something from a file-sharing website. Many browser hijackings originate from add-on applications, i.e., browser helper objects (BHO), toolbars, or plug-ins added to browsers to give them additional functionality. A browser hijacker could also come bundled up with some free software that you unknowingly download and install, compromising your PC security. Typical examples of browser hijackers include CoolWebSearch, Conduit, OneWebSearch, Coupon Server, RocketTab, Delta Search, Searchult.com, and Snap.do.
The presence of any browser hijacker on your system might significantly diminish the browsing experience, track your online activities that lead to serious privacy concerns, degrade overall system efficiency, and lead to software instability also.
Tips on how to get rid of browser hijackers
Certain browser hijacking could be simply stopped by discovering and eliminating the corresponding malware application through your control panel. However, most hijackers will be more difficult to locate or eliminate as they might get themselves connected with some important computer files that enable it to operate as a necessary operating system process. Novice computer users should never try for the manual form of removal, as it demands comprehensive system knowledge to carry out fixes on the system registry and HOSTS file.
How One Can Get rid of a Virus that is Blocking Websites or Preventing Downloads
Malware could cause all kinds of damage if they invade your computer, starting from stealing your private details to deleting data files on your computer. Some malware sits in between your computer and the internet connection and blocks a few or all websites that you would like to check out. It might also prevent you from installing anything on your PC, particularly anti-malware software. If you are reading this now, you may have perhaps recognized that virus infection is the reason behind your blocked net traffic. So what to do if you want to download and install anti-malware software like Safebytes? Although this kind of issue will be harder to circumvent, there are some actions you can take.
Download the antivirus in Safe Mode with Networking
If the malware is set to load at Windows startup, then booting in Safe Mode should prevent it. Since just the minimum programs and services start-up in “Safe Mode”, there are seldom any reasons for conflicts to take place. You will have to do the following to get rid of malware in Safe mode.
1) At power on/start-up, tap the F8 key in 1-second intervals. This should bring up the Advanced Boot Options menu.
2) Select Safe Mode with Networking using arrow keys and press Enter.
3) When you are into this mode, you should have access to the internet once again. Now, make use of your web browser normally and go to https://safebytes.com/products/anti-malware/ to download Safebytes Anti-Malware.
4) After the application is installed, allow the scan run to eliminate trojans and other threats automatically.
Switch to some other internet browser
Some malware only targets particular web browsers. If this is your situation, employ another internet browser as it might circumvent the malware. If you’re not able to download the antivirus software using Internet Explorer, this means the virus is targeting IE’s vulnerabilities. Here, you need to switch over to another web browser such as Chrome or Firefox to download Safebytes software.
Create a portable USB antivirus for removing viruses
Another solution is to create a portable anti-malware program on your USB stick. To run anti-malware using a flash drive, follow these simple steps:
1) Download Safebytes Anti-Malware or MS Windows Defender Offline onto a clean computer system.
2) Plug the USB drive into the uninfected computer.
3) Double-click on the downloaded file to open the installation wizard.
4) Choose a USB drive as the place when the wizard asks you exactly where you intend to install the application. Follow the instructions on the screen to finish off the installation process.
5) Transfer the flash drive from the uninfected computer to the infected computer.
6) Double click the Safebytes Anti-malware icon on the thumb drive to run the program.
7) Click on “Scan Now” to run a scan on the infected computer for viruses.
Ensure the Safety of Your PC by Installing SafeBytes Anti-Malware Software
If you are planning to purchase anti-malware for your laptop or computer, there are lots of brands and packages for you to consider. A few of them do a good job in getting rid of threats while some will harm your PC themselves. You should look for a product that has obtained a good reputation and detects not just computer viruses but other kinds of malware as well. One of the recommended software programs is SafeBytes Anti-Malware. SafeBytes carries a superb track record of top-quality service, and customers are very happy with it.
SafeBytes is a powerful, real-time anti-malware application that is designed to assist the everyday computer end user in safeguarding their computer from malicious internet threats. With its cutting-edge technology, this software will let you remove multiples types of malware including viruses, trojans, PUPs, worms, ransomware, adware, and browser hijackers.
SafeBytes anti-malware comes with a plethora of enhanced features that sets it apart from all others. Let’s take a look at a few of them below:
Live Protection: SafeBytes gives real-time active supervision and protection from all known viruses and malware. It’ll constantly monitor your laptop or computer for hacker activity and also provides users with superior firewall protection.
World-class AntiMalware Protection: Built upon a greatly acclaimed antivirus engine, this malware removal application can find and remove many obstinate malware threats like browser hijackers, PUPs, and ransomware that other common antivirus applications will miss.
Quick Multithreaded Scanning: SafeBytes’s very fast malware scanning engine reduces scan times and extends battery life. At the same time, it’ll effectively identify and eliminate infected computer files or any online threat.
Web Protection: Safebytes allots all sites a unique safety ranking that helps you to get an idea of whether the website you’re about to visit is safe to view or known to be a phishing site.
Lightweight: SafeBytes is a lightweight and easy-of-use antivirus and antimalware solution. As it utilizes very low computer resources, this application leaves the computer power exactly where it belongs to: with you.
24/7 Live Expert Support: You can get 24/7 technical support to immediately resolve any issue with your security software.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove FromDocToPDF without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by FromDocToPDF



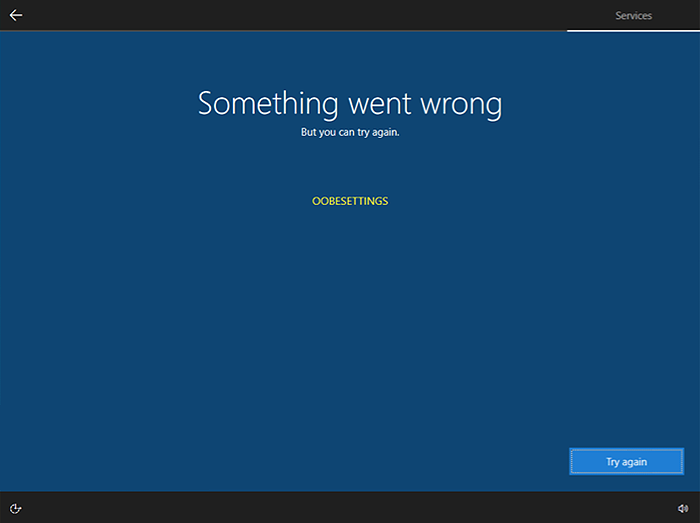 Oobesttings error is the blue screen of death error caused by some faulty settings inside the Windows registry. The good news is that this is not a hard error to fix and if by any chance you are one of the unfortunate people getting this dreaded annoying error, please do keep reading because we have several things that you can do in order to eliminate this issue from your computer.
Oobesttings error is the blue screen of death error caused by some faulty settings inside the Windows registry. The good news is that this is not a hard error to fix and if by any chance you are one of the unfortunate people getting this dreaded annoying error, please do keep reading because we have several things that you can do in order to eliminate this issue from your computer.
