Gables is a browser extension developed by MindSpark Inc. This browser extension lets you create gifs and memes with a few simple clicks. This extension usually comes bundled up with the ASK toolbar.
While active this extension monitors your browser activity and records website visits, clicked links, and potentially personal data. This data is later forwarded to MindSparks ad servers where it is used to better target ads.
This extension hijacks your browser home screen, as well as your default search provider, and changes them to MyWay.com. This extension has been marked as a Browser Hijacker by several anti-virus scanners, and due to its behavior, it is not recommended to keep it on your computer for security reasons.
About Browser Hijackers
Browser hijacking means that a malicious program code has taken control over and altered the settings of your browser, without your approval. Browser hijacker malware is designed for a number of reasons. It redirects you to the sponsored websites and injects adverts on your internet browser that helps its creator generate earnings. Most people believe that these sites are legitimate and harmless but that is not true. Nearly every browser hijacker poses an existent threat to your online safety and it’s important to categorize them under privacy dangers. In a worst-case scenario, your internet browser could be hijacked to download malicious software that will do a lot of damage to your computer system.
Indications of browser hijack
There are numerous signs of web browser hijacking: your browser’s home page has been reset to some mysterious site; you find yourself regularly directed to some other web page than the one you actually meant; The default search page of web browser is modified; unwanted new toolbars are added to your browser; unstoppable flurries of popup advertisements appear on your computer screen; your browser has instability problems or displays frequent errors; You cannot access certain websites, in particular anti-virus sites.
Exactly how browser hijacker finds its way to your PC
Browser hijackers infect computers in numerous ways, including through a drive-by download, a file-share, or an infected email. They can be included with toolbars, add-ons, BHO, plugins, or browser extensions. Other times you may have mistakenly accepted a browser hijacker as part of an application bundle (generally freeware or shareware). A good example of a popular browser hijacker is the most recent Chinese malicious software called “Fireball”, which has infected 250 million computers globally. It works as a hijacker but can be turned into a full-functioning malware downloader later on.
Browser hijackers could affect the user’s browsing experience significantly, record the websites frequented by users and steal personal information, cause difficulty in connecting to the internet, and ultimately create stability issues, making software programs and computers crash.
Learn how to get rid of browser hijackers
Some browser hijacking could be easily stopped by identifying and removing the corresponding malware program from your control panel. Often, it could be a challenging job to discover and delete the malicious program because the associated file will be running as part of the operating system process. Also, browser hijackers could modify the Computer registry so that it can be extremely difficult to restore all of the values manually, particularly if you are not a tech-savvy individual.
What To Do If You Cannot Install Any Antivirus?
Malware can cause a great deal of damage to your computer. Some malware is designed to hinder or block things that you wish to do on your computer system. It may well not allow you to download anything from the web or it will prevent you from accessing some or all of the sites, in particular the antivirus sites. If you’re reading this article, odds are you’re stuck with a malware infection that is preventing you to download and install Safebytes Anti-Malware software on your computer system. Refer to the instructions below to remove malware by alternate methods.
Use Safe Mode to resolve the problem
Safe Mode is a special, basic version of Microsoft Windows in which only essential services are loaded to prevent viruses and other problematic applications from loading. In the event, the virus is set to load immediately when PC boots, shifting to this particular mode may prevent it from doing so. To enter into Safe Mode or Safe Mode with Networking, press the F8 key while the PC is starting up or run MSCONFIG and locate the “Safe Boot” options under the “Boot” tab. Once you are in safe mode, you can attempt to install your antivirus software program without the hindrance of the malware. At this point, you could run the anti-malware scan to get rid of computer viruses and malware without hindrance from another malicious application.
Download the security software using an alternate browser
Some malware mainly targets specific internet browsers. If this sounds like your case, make use of another web browser as it might circumvent the malware. The best way to avoid this problem is to opt for a web browser that is known for its security features. Firefox has built-in Phishing and Malware Protection to help keep you secure online.
Create a bootable USB antivirus drive
Here’s another solution which is creating a portable USB antivirus software package that can check your system for viruses without needing installation. Adopt these measures to run the anti-virus on the affected computer.
1) Make use of another virus-free computer to download Safebytes Anti-Malware.
2) Plug the Flash drive into the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded application, which has a .exe file format.
4) Select the drive letter of the pen drive as the location when the wizard asks you exactly where you want to install the anti-malware. Follow the on-screen instructions to complete the installation.
5) Now, transfer the pen drive to the infected computer.
6) Double click the Safebytes Anti-malware icon on the USB drive to run the application.
7) Run Full System Scan to detect and clean-up up all kinds of malware.
How SafeBytes Anti-Malware Keep your Computer Virus Free
Do you wish to install the best anti-malware program for your system? There are many applications on the market that come in paid and free versions for Windows computers. Some are worth your money, but most aren’t. You really should select a company that creates industry-best anti-malware and has earned a reputation as reliable. While thinking about reliable applications, Safebytes AntiMalware is undoubtedly the highly recommended one.
SafeBytes antimalware is a highly effective and user-friendly protection tool that is designed for end-users of all levels of IT literacy. This tool can easily identify, remove, and protect your computer from the latest malware intrusions including adware, spyware, trojan horses, ransomware, parasites, worms, PUPs, as well as other possibly damaging software programs.
SafeBytes anti-malware takes computer protection to a whole new level with its enhanced features. Below are some of the good ones:
World-class AntiMalware Protection: Using its advanced and sophisticated algorithm, this malware removal tool can detect and get rid of the malware threats hiding in your computer system effectively.
Real-time Active Protection: SafeBytes gives round-the-clock protection for your computer limiting malware attacks instantly. It will continuously monitor your pc for hacker activity and also provides users with advanced firewall protection.
Safe Browsing: Through its unique safety ranking, SafeBytes informs you whether a site is safe or not to visit it. This will ensure that you’re always certain of your online safety when browsing the online world.
“Fast Scan” Features: This program has got one of the fastest and most powerful virus scanning engines in the industry. The scans are very accurate and take a little time to complete.
Minimal CPU Usage: SafeBytes is renowned for its minimal influence on processing power and great detection rate of numerous threats. It runs quietly and efficiently in the background so you are free to use your PC at full power all of the time.
Fantastic Technical Support: Support service is accessible 24 x 7 x 365 days through chat and email to answer your questions.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove GIFables without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by GIFables
Files:
%UserProfile%Local SettingsApplication DataGoogleChromeUser DataDefaultSync Extension Settingsjahgjnedbefhiimghmiemdmgiegiddjg
%LOCALAPPDATA%GoogleChromeUser DataDefaultLocal Extension Settingsjahgjnedbefhiimghmiemdmgiegiddjg
%UserProfile%Local SettingsApplication DataGoogleChromeUser DataDefaultLocal Extension Settingsjahgjnedbefhiimghmiemdmgiegiddjg
Search and Delete: chrome-extension_jahgjnedbefhiimghmiemdmgiegiddjg_0.localstorage-journal
Search and Delete: chrome-extension_jahgjnedbefhiimghmiemdmgiegiddjg_0.localstorage
 Error Causes
Error Causes
 Windows 11 has some cool animations including fading effects which make working in it feels nice and futuristic but the cost of this is that there is a slight delay to certain actions performed. If you want the snap fast feature in Windows 11 and do not care about this eye candy there is an easy way to turn animations off inside it.
Windows 11 has some cool animations including fading effects which make working in it feels nice and futuristic but the cost of this is that there is a slight delay to certain actions performed. If you want the snap fast feature in Windows 11 and do not care about this eye candy there is an easy way to turn animations off inside it.
 Therefore we are presenting a couple of solutions that will fix your issue, it is advisable to follow them as presented since they will go from the most common to the more complex one.
Therefore we are presenting a couple of solutions that will fix your issue, it is advisable to follow them as presented since they will go from the most common to the more complex one.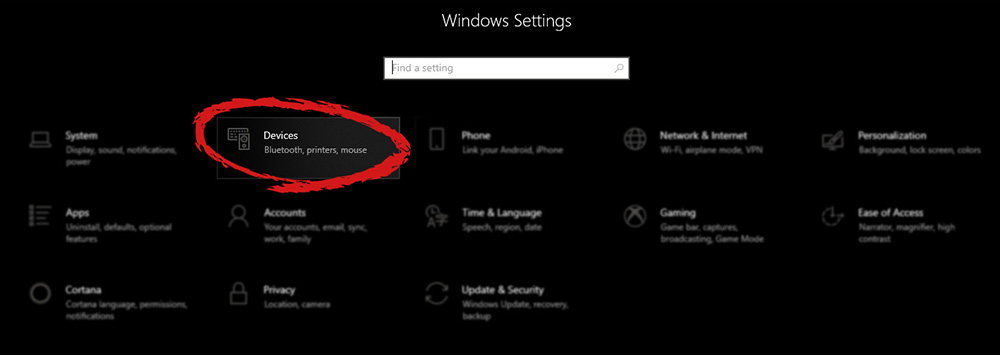 Once the device window opens, click once on printers and scanners, and on the right window go to the bottom and uncheck Let windows manage my default printer.
Once the device window opens, click once on printers and scanners, and on the right window go to the bottom and uncheck Let windows manage my default printer.
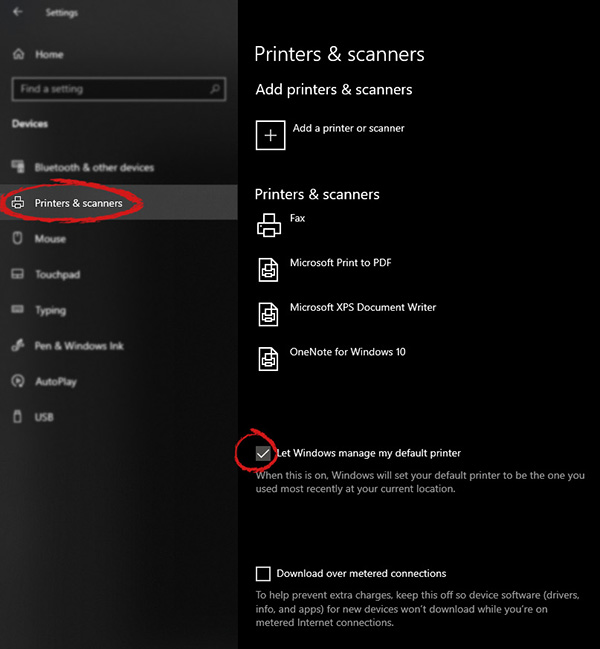 Unchecking that box will let Windows know that we do not wish anymore for him to set our default printers according to their use. Once the checkbox is clear go up to your printer list and click on the printer you wish to use as the default one. I will choose Microsoft Print to PDF as my default printer and click on it. Once the printer is clicked option menu will appear.
Unchecking that box will let Windows know that we do not wish anymore for him to set our default printers according to their use. Once the checkbox is clear go up to your printer list and click on the printer you wish to use as the default one. I will choose Microsoft Print to PDF as my default printer and click on it. Once the printer is clicked option menu will appear.
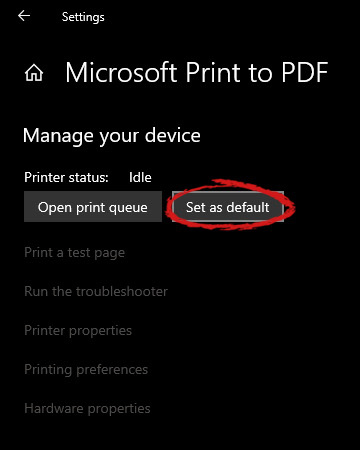
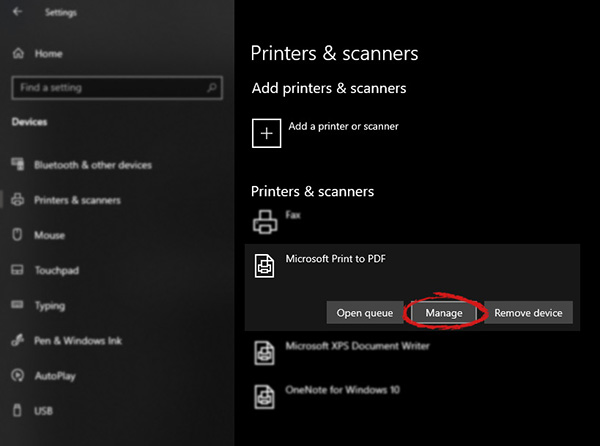 When the option menu appears under the printer name, click on Manage which will take you to the printer management screen. When you are on the manage screen, click on the Set as default button, and you are done.
When the option menu appears under the printer name, click on Manage which will take you to the printer management screen. When you are on the manage screen, click on the Set as default button, and you are done.