FreeMaps is a google chrome extension by Mindspark powered by Ask or MyWay. This extension offers users a quick and easy way to find the routes or locations that they desire. While all of this may seem appealing, this extension was classified as a Browser Hijacker by many anti-virus applications and was marked for removal.
When installed FreeMaps will change your home page, new tab and default search engine to MyWay.com, it will monitor your browsing activity and send it back to Mindspark ad servers. This data is later used/sold to better display targeted ads depending on your search queries.
While browsing the internet with this extension active you will see additional pop-up ads, sponsored links, and injected ads displaying throughout your browsing sessions, and even injected into websites that should be ad-free. Due to poor code optimization, these ads can sometimes cover a part of the page, making it unreadable or inaccessible.
About Browser Hijackers
Browser hijacking is a form of unwanted software, commonly a browser add-on or extension, which then causes modifications in the web browser’s settings. Browser hijackers are capable of doing more than simply changing home pages. These are typically used to force hits to a specific site, manipulating web traffic to earn ad revenue. It could seem naive, but most of such websites aren’t legitimate and could present a major threat to your online safety. As soon as the malware attacks your laptop or computer, it begins to mess things up a whole that slows your computer down to a crawl. In the worse case, you will be forced to tackle serious malware threats too.
How you can know whether the browser is hijacked?
Signs that your web browser is hi-jacked include: your browser’s homepage is suddenly different; bookmark and the new tab are likewise modified; default web engine is modified; find new toolbars which you didn’t add; unstoppable flurries of popup adverts show up on your computer screen; your browser has instability issues or exhibits frequent errors; you cannot visit specific websites such as home pages of anti-malware software.
Exactly how browser hijacker finds its way onto your computer
A browser hijacker could be installed on your PC if you check out an infected website, click an e-mail attachment, or download something from a file-sharing website. They can also be deployed via the installation of a web browser toolbar, extension, or add-on. Some browser hijackers spread in user’s computer systems by using a deceptive software distribution method known as “bundling” (usually through freeware and shareware). Typical examples of browser hijackers include Conduit, CoolWebSearch, OneWebSearch, Coupon Server, RocketTab, Searchult.com, Snap.do, and Delta Search.
Browser hijackers can record user keystrokes to gather potentially invaluable information that leads to privacy issues, cause instability on systems, drastically disrupt user’s browsing experience, and eventually slow down the system to a point where it becomes unusable.
Tips on how to remove browser hijackers
Some types of browser hijackers can be removed from your PC by deleting malicious software applications or any other recently installed shareware. Having said that, many hijackers are very tenacious and require specialized tools to eliminate them. You should think of carrying out manual repairs only if you are a tech-savvy person since there are dangers associated with messing around with the computer registry and HOSTS file.
Professionals always suggest users to remove any malicious software including browser hijacker with an automatic malware removal tool, which is better, safer and faster than the manual removal procedure. One of the best tools for repairing browser hijacker malware is SafeBytes Anti-Malware. It will help you remove any pre-existing malicious software in your pc and provides you real-time monitoring and protection against the latest threats.
How To Install Safebytes Anti-Malware On An Infected Computer
All malware is inherently harmful, but certain kinds of malware do a lot more damage to your computer or laptop than others. Certain malware goes to great lengths to prevent you from downloading or installing anything on your PC, especially antivirus applications. So what should you do if malware prevents you from downloading or installing Safebytes Anti-Malware? Follow the instructions below to get rid of the malware in alternate ways.
Start Windows in Safe Mode
In the event the malware is set to run at Windows start-up, then booting in safe mode should avoid it. Only the bare minimum required programs and services are loaded when you start your PC in Safe Mode. Here are the steps you should follow to start your computer into the Safe Mode of your Windows XP, Vista, or 7 computers (visit Microsoft website for directions on Windows 8 and 10 computers).
1) Hit the F8 key repeatedly as soon as your PC boots, however, before the big Windows logo or black screen with white texts comes up. This should bring up the Advanced Boot Options menu.
2) Use the arrow keys to choose Safe Mode with Networking and press ENTER.
3) As soon as this mode loads, you will have an internet connection. Now, obtain the malware removal software you want by utilizing the internet browser. To install the program, follow the directions within the setup wizard.
4) After installation, run a full scan and let the program get rid of the threats it discovers.
Obtain the anti-malware software in a different internet browser
Some malware mainly targets specific browsers. If this sounds like your case, employ another web browser as it could circumvent the virus. If you appear to have malware attached to Internet Explorer, then switch to an alternate internet browser with built-in safety features, such as Chrome or Firefox, to download your preferred antivirus program – Safebytes.
Install antivirus on a flash drive
Here’s yet another solution which is using portable USB anti-malware software that can scan your system for viruses without the need for installation. Abide by these steps to run the anti-virus on the affected computer system.
1) Download Safebytes Anti-Malware or Microsoft Windows Defender Offline onto a virus-free PC.
2) Insert the USB drive into the clean PC.
3) Double click on the exe file to open the installation wizard.
4) Select the flash drive as the location for saving the software file. Follow activation instructions.
5) Transfer the thumb drive from the uninfected computer to the infected PC.
6) Double-click the Safebytes Anti-malware icon on the pen drive to run the program.
7) Press the “Scan Now” button to start the virus scan.
Protect your PC from Malware With SafeBytes Security Suite
In order to protect your computer from many different internet-based threats, it is important to install an anti-malware application on your laptop. However, with so many anti-malware companies out there, these days it’s tough to decide which one you should purchase for your PC. Some of them are great while some are scamware applications that pretend as legit anti-malware programs waiting around to wreak havoc on your PC. You have to be very careful not to pick the wrong product, especially if you purchase a premium application. When it comes to commercial anti-malware software options, the majority of people go with popular brands, like SafeBytes, and they are very happy with it.
SafeBytes anti-malware is a highly effective and user-friendly protection tool that is designed for end-users of all levels of computer literacy. This program could easily detect, remove, and protect your PC from the latest malware intrusions including adware, spyware, trojan horses, ransomware, parasites, worms, PUPs, along with other potentially harmful software applications.
SafeBytes has fantastic features when compared with other anti-malware programs. The following are some of the great features included in the software.
Live Protection: SafeBytes gives real-time active supervision and protection from all known viruses and malware. It’ll continuously monitor your pc for hacker activity and also provides end-users with advanced firewall protection.
World-class AntiMalware Protection: Safebytes is built on the best virus engine in the industry. These engines will detect and remove threats even during the initial stages of a malware outbreak.
Safe Browsing: SafeBytes inspects the hyperlinks present on a web page for possible threats and tells you whether the website is safe to explore or not, through its unique safety rating system.
“Fast Scan” Features: Safebytes AntiMalware, using its advanced scanning engine, gives ultra fast scanning which can quickly target any active online threat.
Lowest CPU/Memory Usage: This software is lightweight and can work quietly in the background, and will not impact your computer efficiency.
Premium Support: You can get 24/7 technical assistance to immediately resolve any issue with your security application.
To conclude, SafeBytes Anti-Malware is really great for securing your laptop or computer against all kinds of malware threats. Now you may realize that this particular software does more than just scan and eliminate threats in your PC. If you’re searching for the best malware removal application out there, and if you don’t mind spending some dollars for it, go for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you’d like to manually get rid of FreeMaps without the use of an automated tool, it may be actually possible to do so by removing the program from the Microsoft Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browser’s AddOn/Extension manager and removing it. It’s also suggested to factory reset your browser settings to their default state.
If you opt to manually remove the system files and registry entries, use the following list to ensure that you know precisely what files to remove before executing any actions. Please remember that this is for professional users only and may be challenging, with incorrect file removal resulting in additional PC errors. In addition, certain malware is capable of replicating or preventing removal. Completing this task in Safe Mode is advised.


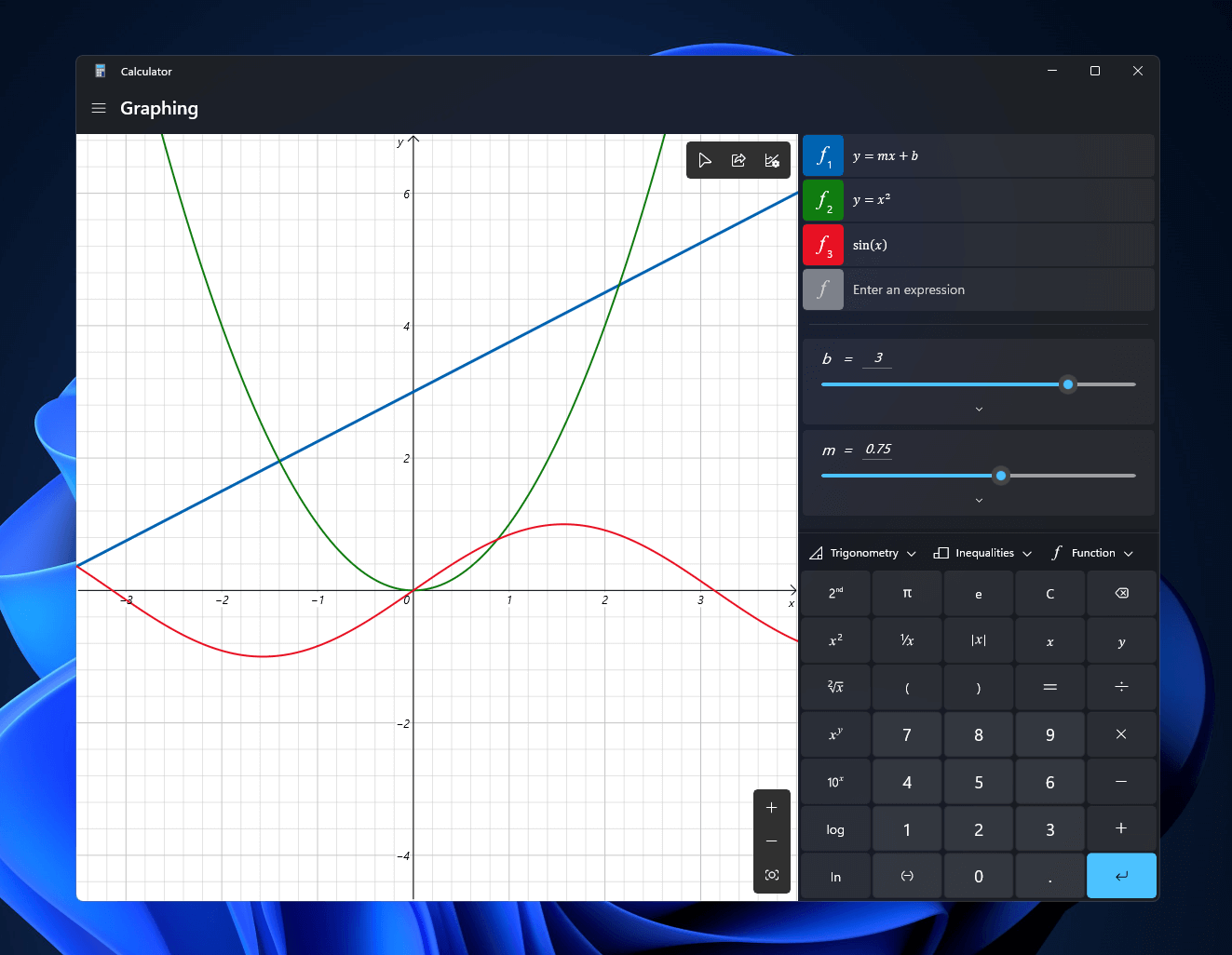 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
