Easy Directions Finder is a browser extension developed by Mindspark Inc. for Google Chrome. This extension offers users quick access to popular websites for navigation and evens. While at first glance this might look useful, keep in mind that this extension has been marked as a Browser Hijacker by several anti-virus applications.
When installed EasyDirectionsFinder will record your browsing history, visited links, clicked URL-s, and viewed products. This data is later forwarded/sold to Mindspark's ad network and used to better target ads to users.
While browsing the internet with this extension installed (it does not have to be enabled) you will see additional injected ads, sponsored links, and pop-up ads throughout your browsing sessions.
Due to its information mining behavior and aggressive ad injections, it is recommended to remove this extension from your computer.
About Browser Hijackers
Browser hijacking is a type of unwanted software, often a web browser add-on or extension, which causes modifications in web browser’s settings. Browser hijackers are capable of doing more than just modifying homepages. In general, browser hijacking is utilized for earning advertising revenue from forced ad mouse clicks and site visits. While it may seem naive, all browser hijackers are dangerous and thus always classified as security risks. When the malware attacks your laptop or computer, it starts to mess things up a whole that slows your system down to a crawl. In the worse case, you may be pushed to deal with serious malware threats as well.
How one can know whether the web browser is hijacked?
The common symptoms that suggest having this malicious software on your computer are: the browser’s home page is modified; you find yourself regularly directed to some other webpage than the one you actually intended; the default web browser settings have been modified and/or your default search engine is altered; unsolicited new toolbars are added to your web browser; your internet browser displays endless pop-up ads; web pages load slowly and often incomplete; you can’t navigate to certain webpages, like computer security software related sites.
So how does a browser hijacker infect a computer?
Browser hijackers may use drive-by downloads or file-sharing networks or an e-mail attachment in order to reach a targeted PC. They could also be deployed via the installation of an internet browser toolbar, add-on, or extension. A browser hijacker could also come bundled up with some freeware that you unintentionally download to your PC, compromising your internet security. Some of the most popular hijackers are EasyDirectionsFinder, Babylon Toolbar, Conduit Search, Sweet Page, OneWebSearch, and CoolWebSearch.
Browser hijacker removal tips
Some browser hijacking could be easily reversed by discovering and eliminating the corresponding malware software through your control panel. Sometimes, it can be a tough task to discover and eliminate the malicious component since the associated file will be running as part of the operating system process. Moreover, browser hijackers could modify the Computer registry therefore it can be quite tough to restore all the values manually, especially when you’re not a very tech-savvy individual.
Industry experts always suggest users eliminate any malware including browser hijacker with an automatic removal tool, which is better, safer, and quicker than the manual removal solution. SafeBytes Anti-Malware could counter persistent browser hijackers and give you active PC protection against all types of malware. Together with the antivirus tool, a PC optimizer, such as SafeBytes Total System Care, can help you in deleting all related files and modifications in the computer registry automatically.
How To Get Eliminate Malware That Is Preventing Antivirus Downloads?
Malware could cause many different types of damage to computers, networks, and data. Some malware sits in between the computer and the internet connection and blocks a few or all sites that you really want to visit. It will also prevent you from adding anything to your PC, particularly anti-virus applications. So what to do when malicious software prevents you from downloading or installing Safebytes Anti-Malware? There are a few actions you can take to get around this issue.
Boot your computer in Safe Mode
If any malware is set to load immediately when Microsoft Windows starts, getting into Safe Mode could very well block the attempt. Since only the minimal programs and services launch in Safe Mode, there are hardly any reasons for conflicts to happen. Below are the steps you should follow to start into the Safe Mode of your Windows XP, Vista, or 7 computers (check out Microsoft site for directions on Windows 8 and 10 computers).
1) At power on, press the F8 key while the Windows splash screen starts to load. This will conjure up the “Advanced Boot Options” menu.
2) Choose Safe Mode with Networking with arrow keys and hit ENTER.
3) Once you get into this mode, you should have an internet connection again. Now, utilize your internet browser normally and go to https://safebytes.com/products/anti-malware/ to download and install Safebytes Anti-Malware.
4) After the software program is installed, let the diagnostic scan run to remove trojans and other malware automatically.
Switch over to an alternative web browser
Web-based malware can be environment-specific, targeting a specific web browser or attacking particular versions of the browser. If you seem to have malware attached to Internet Explorer, then switch to an alternate browser with built-in security features, such as Chrome or Firefox, to download your preferred antivirus program – Safebytes.
Install security software on a flash drive
Another option is to create a portable antivirus program onto your USB flash drive. Abide by these steps to run the anti-malware on the infected PC.
1) Download the anti-malware on a virus-free computer.
2) Plug the pen drive into the clean PC.
3) Run the setup program by double-clicking the executable file of the downloaded application, with a .exe file format.
4) Select the USB stick as the location for saving the software file. Follow the on-screen instructions to complete the installation process.
5) Now, insert the USB drive into the infected computer.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Run Full System Scan to detect and clean-up up all sorts of malware.
SafeBytes AntiMalware Overview
If you’re looking to purchase anti-malware for your laptop or computer, there are plenty of brands and packages for you to consider. A few are very good ones, some are ok types, while some are just fake anti-malware applications that will damage your computer themselves! You need to purchase a product that has obtained a good reputation and detects not just viruses but other sorts of malware too. While thinking about reliable applications, Safebytes AntiMalware is certainly the strongly recommended one.
Safebytes is among the well-established computer solutions companies, which provide this complete anti-malware tool. Using its outstanding protection system, this tool will quickly detect and remove most of the security threats, including adware, viruses, browser hijackers, ransomware, PUPs, and trojans.
There are numerous wonderful features you’ll get with this security product. Here are some of the good ones:
Best AntiMalware Protection: With its enhanced and sophisticated algorithm, this malware elimination tool can detect and eliminate the malware threats hiding in the computer system effectively.
Live Protection: SafeBytes offers totally hands-free real-time protection and is set to observe, prevent and eliminate all threats at its very first encounter. It’ll regularly monitor your pc for hacker activity and also gives end-users superior firewall protection.
SuperSpeed Scanning: Safebytes Anti-Malware, with its enhanced scanning engine, provides extremely fast scanning that can promptly target any active internet threat.
Website Filtering: SafeBytes provides an instant safety rating about the pages you’re going to check out, automatically blocking dangerous sites and making sure that you are certain of your online safety while browsing the net.
Low CPU Usage: SafeBytes is a lightweight and easy-of-use antivirus and antimalware solution. As it uses low computer resources, this program leaves the computer power exactly where it belongs: with you.
24/7 Live Professional Support: You may get high levels of support 24/7 if you are using their paid version.
Overall, SafeBytes Anti-Malware is a solid program since it has plenty of features and can detect and eliminate any potential threats. You can be sure that your computer will be protected in real-time once you put this software to use. So if you’re searching for the absolute best malware removal tool out there, and if you don’t mind paying out a few bucks for it, go for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you do not wish to use a malware removal software and like to remove EasyDirectionsFinder manually, you could possibly accomplish this by going to the Windows Add/Remove Programs menu in the Control Panel and delete the offending program; in cases of browser plug-ins, you may uninstall it by going to the browser’s Add-on/Extension manager. You’ll likely also want to reset your browser.
Finally, examine your hard drive for all of the following and clean your Windows registry manually to remove leftover application entries after uninstallation. But bear in mind, editing the registry is often a hard task that only advanced computer users and professionals should attempt to fix the problem. Moreover, some malicious programs have the capability to defend against its deletion. Completing this task in Safe Mode is advised.

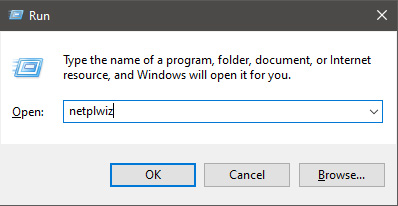
 In the dialog, type in netplwiz and press ENTER.
In the dialog, type in netplwiz and press ENTER.
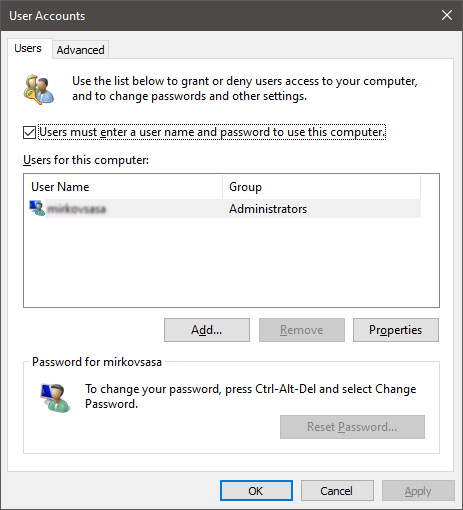
 You will find yourself in the User Accounts window, inside deselect Users must enter a user name and password to use this computer. Press OK
You will find yourself in the User Accounts window, inside deselect Users must enter a user name and password to use this computer. Press OK
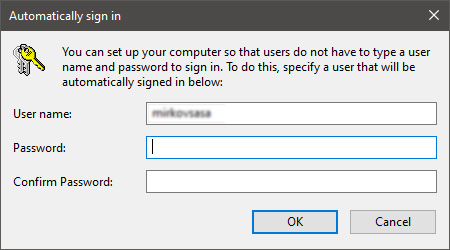
 Sign in the window will pop up where you will have to type in your password and confirm it in order to start the feature.
Sign in the window will pop up where you will have to type in your password and confirm it in order to start the feature.
 After typing in your password and confirming it, press OK. That's it, next time you wake your computer from hibernation or turn it ON, you will automatically be greeted with a desktop instead of a Windows login screen.
After typing in your password and confirming it, press OK. That's it, next time you wake your computer from hibernation or turn it ON, you will automatically be greeted with a desktop instead of a Windows login screen.  Is There Any Deal
Is There Any Deal Cheap Shark
Cheap Shark Humble Bundle
Humble Bundle Fanatical
Fanatical Slick Deals
Slick Deals Green Man Gaming
Green Man Gaming Antivirus software has become the kind of a must-have in every computer in this day and age. When you think about it, our systems are connected to the internet most of the time if not always, and therefore kind placed in from the line of various cyber-attacks. Here antivirus software comes into focus, especially because it has evolved long from just a simple virus removal tool to full security suites.
We will be going through the best of these applications in order to present both their good and bad sides and hope that we will help you in picking the right one for you. Remember, picking either one of the presented solutions is way better than not having one at all. The list is made from best down in our opinion so number one is highly recommended.
Antivirus software has become the kind of a must-have in every computer in this day and age. When you think about it, our systems are connected to the internet most of the time if not always, and therefore kind placed in from the line of various cyber-attacks. Here antivirus software comes into focus, especially because it has evolved long from just a simple virus removal tool to full security suites.
We will be going through the best of these applications in order to present both their good and bad sides and hope that we will help you in picking the right one for you. Remember, picking either one of the presented solutions is way better than not having one at all. The list is made from best down in our opinion so number one is highly recommended.
 Once it opens, click on Device Manager to open it,
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.
Once it opens, click on Device Manager to open it,
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.
