TotalRecipeSearch is a browser extension for Google Chrome developed by Mindspark. This extension allows access to popular cooking websites.
From the Author: Discover 1000s of tasty recipes – for FREE! Find creative, new meal ideas all in one convenient place!
When installed, this extension changes your default search engine and home page to MyWebSearch.com. While active it will monitor user activity, recording browsing data, visited websites and clicked links. This data is later used to display targeted ads throughout your browsing sessions.
While browsing the internet you will see additional unwanted ads, sponsored links, and even pop-up ads injected into your search results and websites.
This extension has been marked as a Browser Hijacker by several anti-virus programs and it is targeted for removal.
About Browser Hijackers
Browser hijacking means a malicious code has taken power over and modified the settings of your web browser, without your consent. Practically most browser hijackers are made for advertising or marketing purposes. Typically, it will drive users to particular sites which are aiming to boost their ad income. Though it might appear naive, all browser hijackers are damaging and thus always classified as security risks. They not only mess up your web browsers, but browser hijackers could also modify the computer registry, making your computer susceptible to other malicious programs.
How to determine if your browser is hijacked
The typical signs that indicate having this malware on your computer are:
1. you see unauthorized changes to your web browser’s homepage
2. when you key in a URL, you find yourself regularly directed to some other web page than the one you meant
3. the default web browser settings have been changed and/or your default web engine is altered
4. you are finding browser toolbars you have never witnessed before
5. your web browser will display constant pop-up ads
6. websites load slowly and at times incomplete
7. you are blocked to access those sites of security solution providers.
How does a browser hijacker infect a computer?
Browser hijackers can enter a computer in some way or other, for example via downloads, file sharing, and email as well. They also come from add-on applications, also called browser helper objects (BHO), web browser plug-ins, or toolbars. Browser hijackers sneak into your computer in addition to free software downloads also that you unwittingly install alongside the original. Popular examples of browser hijackers include CoolWebSearch, Conduit, RocketTab, OneWebSearch, Coupon Server, Snap.do, Delta Search, and Searchult.com.
The existence of any browser hijacker malware on your system might significantly diminish the browsing experience, monitor your internet activities that lead to critical privacy concerns, develop system stability problems and ultimately cause your PC to slow down or to an almost unusable condition.
How you can fix a browser hijack
Certain hijackers could be removed by simply uninstalling the corresponding free software or add-ons from the Add or Remove Programs in the Windows Control Panel. But, the majority of hijackers are very tenacious and need specialized tools to remove them. Novice PC users should not try for the manual form of removal, as it calls for comprehensive computer knowledge to carry out repairs on the computer registry and HOSTS file.
Professionals always recommend users to get rid of any malware including browser hijacker by using an automatic removal tool, which is better, safer, and quicker than the manual removal technique. SafeBytes Anti-Malware discovers all types of hijackers – including TotalRecipeSearch – and eliminates every trace quickly and efficiently. Along with the anti-malware tool, a system optimizer, like SafeBytes’s Total System Care, will help you in deleting all linked files and modifications in the computer registry automatically.
Help! Malware Preventing Anti-Malware Installation And Access To The Internet
Malware could potentially cause plenty of damage to your PC. Certain malware variants alter browser settings by adding a proxy server or modify the PC’s DNS settings. In these instances, you will be unable to visit some or all of the internet sites, and thus unable to download or install the necessary security software to clear out the computer virus. So what you should do if malware prevents you from downloading or installing Safebytes Anti-Malware? Refer to the instructions below to get rid of malware through alternate methods.
Download the application in Safe Mode with Networking
In the event the malware is set to load at Windows start-up, then booting in Safe Mode should prevent it. Only minimal required applications and services are loaded when you start your PC into Safe Mode. To launch your Windows XP, Vista, or 7 PCs in Safe Mode with Networking, please do as instructed below.
1) At power-on/startup, hit the F8 key in 1-second intervals. This should bring up the Advanced Boot Options menu.
2) Use the arrow keys to choose Safe Mode with Networking and hit ENTER.
3) Once you get into this mode, you should have an internet connection again. Now, use your web browser normally and navigate to https://safebytes.com/products/anti-malware/ to download Safebytes Anti-Malware.
4) Following installation, do a full scan and allow the software program to remove the threats it detects.
Obtain the antivirus software in a different web browser
Web-based viruses could be environment-specific, targeting a particular browser or attacking particular versions of the web browser. The best way to overcome this problem is to choose a browser that is well known for its security features. Firefox comprises built-in Malware and Phishing Protection to keep you safe online.
Install and run anti-malware from your flash drive
To effectively get rid of the malware, you need to approach the issue of installing anti-virus software on the infected computer system from a different angle. Adopt these measures to employ a flash drive to fix your corrupted PC.
1) Use another virus-free computer system to download Safebytes Anti-Malware.
2) Plug the Flash drive into the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded application, with a .exe file format.
4) Select the flash drive as the location for saving the software file. Follow the directions to finish the installation process.
5) Transfer the thumb drive from the clean PC to the infected computer.
6) Double-click the EXE file to open the Safebytes software from the pen drive.
7) Click on “Scan Now” to run a scan on the affected computer for viruses.
Features and Benefits of SafeBytes Anti-Malware
If you are looking to download anti-malware software for your computer, there are various tools in the market to consider however, you cannot trust blindly anyone, regardless of whether it is a paid or free software. A few are good ones, some are decent, while some are simply just fake anti-malware programs that can damage your personal computer themselves! You need to be careful not to pick the wrong application, especially if you buy a paid software. When thinking about the highly regarded applications, Safebytes AntiMalware is certainly the highly recommended one.
SafeBytes can be described as a highly effective, real-time anti-spyware application that is designed to assist everyday computer users in protecting their computers from malicious threats. This program can easily identify, remove, and protect your PC from the most advanced malware threats such as adware, spyware, trojan horses, ransomware, parasites, worms, PUPs, and other possibly damaging software programs.
SafeBytes anti-malware comes with a myriad of advanced features that sets it apart from all others. Listed below are some of the features you might like in SafeBytes Anti-Malware.
Real-time Threat Response: SafeBytes provides an entirely hands-free real-time protection and is set to check, prevent and destroy all computer threats at its very first encounter. They’re highly effective in screening and getting rid of different threats since they’re regularly improved with the latest updates and alerts.
Anti-Malware Protection: Built on a highly acclaimed anti-virus engine, this malware removal application can detect and get rid of many stubborn malware threats like browser hijackers, potentially unwanted programs, and ransomware that other typical anti-virus software will miss.
Fast Scan: This software program has one of the fastest and most effective virus scanning engines in the industry. The scans are highly accurate and take a little time to complete.
Internet Security: SafeBytes inspects the hyperlinks present on a web page for possible threats and notifies you whether the site is safe to browse or not, through its unique safety rating system.
Very Low CPU and RAM Usage: SafeBytes provides complete protection from online threats at a fraction of the CPU load because of its advanced detection engine and algorithms.
Fantastic Technical Support: Skilled technicians are at your disposal 24/7! They will immediately fix any technical issues you may be experiencing with your security software.
Put simply, SafeBytes has formulated a meaningful anti-malware solution that is aimed to protect your computer against various malware. Now you may realize that this software does more than just scan and eliminate threats from your computer. So when you want sophisticated forms of protection features & threat detections, buying SafeBytes Anti-Malware could be worth the dollars!
Technical Details and Manual Removal (Advanced Users)
To remove TotalRecipeSearch manually, navigate to the Add or Remove programs list in the Control Panel and choose the offending program you want to get rid of. For web browser plug-ins, go to your web browser’s Addon/Extension manager and choose the plug-in you want to remove or disable. It’s also advised to factory reset your web browser to its default condition to fix corrupt settings.
If you opt to manually delete the system files and Windows registry entries, utilize the following checklist to ensure that you know exactly what files to remove before carrying out any actions. Please keep in mind that only experienced computer users should try to manually edit the system files simply because removing any single critical registry entry results in a major problem or even a system crash. Also, certain malware is capable of replicating itself or preventing deletion. Doing this malware-removal process in Safe Mode is suggested.
Files:
%PROGRAMFILES%\TotalRecipeSearch_14\bar.bin\AppIntegrator.exe
%PROGRAMFILES%\TotalRecipeSearch_14\bar.binSrcAs.dll
%PROGRAMFILES%\TotalRecipeSearch_14\bar.binbar.dll
%UserProfile%\Local Settings\Application Data\TotalRecipeSearch_14
%LOCALAPPDATA%\TotalRecipeSearch_14
%USERPROFILE%\Desktop\TotalRecipeSearch.exe
%PROGRAMFILES%\TotalRecipeSearch_14\bar.binmedint.exe
%PROGRAMFILES%\TotalRecipeSearch_14
%LOCALAPPDATA%\Google\Chrome\User Data\Default\cnbegpgknjllkedcnkfailmjbiahbfba
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\cnbegpgknjllkedcnkfailmjbiahbfba
%PROGRAMFILES%\TotalRecipeSearch_14\bar.binHighIn.exe
%PROGRAMFILES%\TotalRecipeSearch_14\bar.binbarsvc.exe
%PROGRAMFILES%\TotalRecipeSearch_14\bar.binbrmon.exe
%USERPROFILE%\Local Settings\Application Data\TotalRecipeSearchTooltab
%LOCALAPPDATA%\TotalRecipeSearchTooltab
Registry:
HKEY_CURRENT_USER\Software\AppDataLow\Software\TotalRecipeSearch_14
HKEY_CURRENT_USER\Software\TotalRecipeSearch_14
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.DynamicBarButton
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.DynamicBarButton.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.FeedManager
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.FeedManager.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.HTMLMenu
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.MultipleButton
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.MultipleButton.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.PseudoTransparentPlugin
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.PseudoTransparentPlugin.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.Radio
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.Radio.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.RadioSettings
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.SettingsPlugin
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.SettingsPlugin.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.SkinLauncher
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.SkinLauncher.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.SkinLauncherSettings
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.SkinLauncherSettings.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.ThirdPartyInstaller
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.UrlAlertButton
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.UrlAlertButton.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TotalRecipeSearch_14.XMLSessionPlugin
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\03f3147c-cea6-4aae-b0ae-8d8abe7a8080
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\435e56d9-92df-4d38-bdff-fe316064953c
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\4a80a60d-bdef-4d70-bccc-d0dad25ff951
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\8cab2773-5453-4778-90d9-6672805b41ca
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\b723e5aa-0f63-47df-971c-ae8ea0f8393a
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Toolbar, value: a0154e07-2b48-475c-a82a-80efd84ea33e
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects\ab56dfde-0c14-45b3-9df6-7b0eba617870
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects\df22384f-cf68-4d19-969f-10423715528b
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\96b8a0ef-0d9d-4a92-b548-376db4bbb58b
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\A4503EC3-1111-4B62-8F46-0D88508F8A7B
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\b38fbaed-ded1-4ba6-ba2e-f2515fd49442
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\e8106344-16d4-41d1-9a2a-0521a59199ea
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\fd79f359-e577-46db-aa74-d6e6b8b45ba8
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run, value: TotalRecipeSearch Search Scope Monitor
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\TotalRecipeSearch_14bar Uninstall Firefox
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\MozillaPlugins\@TotalRecipeSearch_14.com/Plugin
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\TotalRecipeSearch_14
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\0384459a-9d5e-4ae1-b154-8eac39721c97
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\03f3147c-cea6-4aae-b0ae-8d8abe7a8080
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\435e56d9-92df-4d38-bdff-fe316064953c
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\4a80a60d-bdef-4d70-bccc-d0dad25ff951
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\8cab2773-5453-4778-90d9-6672805b41ca
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\b723e5aa-0f63-47df-971c-ae8ea0f8393a
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects\df22384f-cf68-4d19-969f-10423715528b
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\2502086b-5a46-4d05-8d5b-a1e77ab8bb32
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\76f3207c-3a0a-461b-b958-5653c5718243
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\96b8a0ef-0d9d-4a92-b548-376db4bbb58b
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\A4503EC3-1111-4B62-8F46-0D88508F8A7B
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\b38fbaed-ded1-4ba6-ba2e-f2515fd49442
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\e8106344-16d4-41d1-9a2a-0521a59199ea
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\fd79f359-e577-46db-aa74-d6e6b8b45ba8
HKEY_LOCAL_MACHINE\SOFTWARE\MozillaPlugins\@TotalRecipeSearch_14.com/Plugin
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TotalRecipeSearch_14Service
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\DOMStorage\totalrecipesearch.dl.myway.com
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\DOMStorage\totalrecipesearch.com


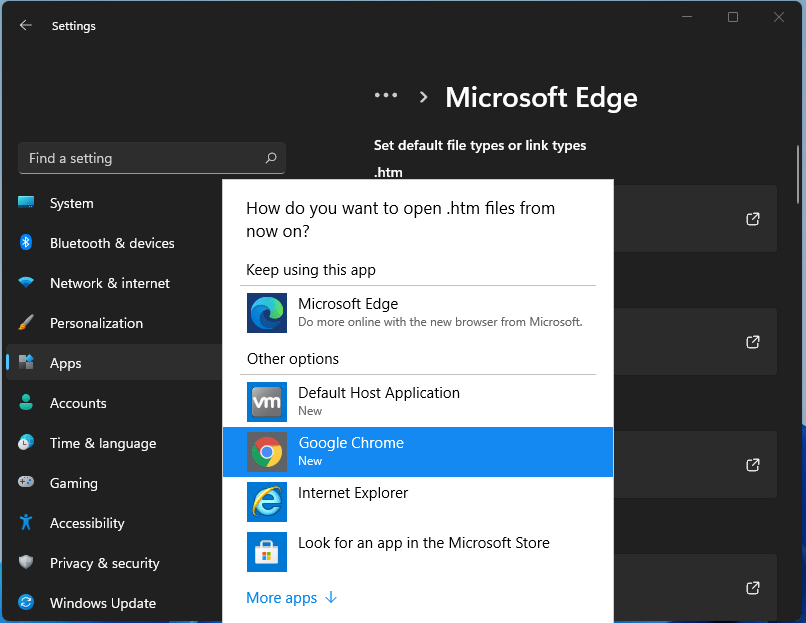 For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required.
For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required.