Error Code 0x80070020 – What is it?
One of the problems encountered by Windows users when upgrading to Windows 10 from Windows 7 or Windows 8/8.1 is the Error Code 0x80070020. This error code normally occurs when users try to download updates from the Windows Update Website or simply by upgrading to Windows 10. Error Code 0x80070020 also occurs when the device already has a Windows 10 installed.
Once this error is encountered, it will cause malfunction of update installs and display the following message:
An error (-5006 : 0x80070020) has occurred while running the setup. Or The process cannot access the file because it is being used by another process”
Solution
Error Causes
In an attempt to fix Error Code 0x80070020, it is important to pinpoint what the cause is. The most probable cause of this error is due to interference. This error code most likely occurs when there is another automatic update running, for instance, an Antivirus scanning in real-time. If you’re scheduled to have an automatic update during real-time scanning, the Windows 10 update might malfunction.
Further Information and Manual Repair
In trying to fix Error Code 0x80070020, you can perform manual repair methods to resolve the issue effectively and efficiently. Most Windows users can easily employ these manual repair methods, even those who do not have technical abilities. However, there are certain instances where a Windows professional’s help is needed. If you don’t want to face any risk in resolving the issue, it would be best to consult a professional Windows technician or you can also make use of a powerful automated tool.
NOTE: It is best to attend immediately to errors encountered since unresolved errors can result in slowing down your computer’s performance. This might also cause other error messages to arise such as Error Code 0x80070057.
Method One: Restart Your Device
Since Error Code 0x80070020 is most likely encountered due to interference during your update, the easiest method you can do is to close all opened programs and restart your device. After restarting, try to start the update process again.
Method Two: Disable Antivirus Temporarily
Another quick and safe way to fix Error Code 0x80070020 is to disable your antivirus. You must take note though that in doing so, your computer will be susceptible to virus attacks. If you want to proceed with this method, follow these steps:
- Locate all programs in process in the notifications area, found in the lower right-hand section of your screen. If in case the antivirus icon is not visible on the taskbar, you may have to click an arrow pointing up to show what programs are currently running.
- Right-click on the antivirus icon then select the disable option.
Method Three: Run the Update Troubleshooter for Windows
The Windows Update Troubleshooter may resolve many of the errors encountered by Windows users when installing updates from Windows Update. To execute the troubleshooter, follow the steps below:
- Access a menu by holding the Windows key and X. Wait for the menu to appear on the bottom left corner of the screen.
- Open the Control Panel.
- Change the appearance of files by selecting large or small icons in the View by option located on the upper right section of your screen.
- Once you change the appearance of the files, choose the troubleshooting
- Run the Windows Update Troubleshooter.
- Restart your device then check if this resolves the problem.
Method Four: Execute A Clean Boot
Executing a clean boot means starting Windows using only a few resources, including startup programs and drivers. This safeguards minimizing conflicts and prevent software clash when an update is received. In performing a clean boot, you will be able to pinpoint what caused the manifestation of error code 0x80070020. Check Microsoft’s Support website to know how to execute a clean boot.
Method Five: Reset Windows Update Components
Performing this method is a bit risky and should be your last option if all methods were unsuccessful. This process will alter your device’s registry so you must ensure to perform accurately the steps. A single mistake can lead to modifying your registry erroneously, which might result in the occurrence of other error messages. Carefully follow the steps found on Microsoft’s Support website to successfully reset Windows Update components.
Resetting Windows Update components can also be done by implementing the following steps:
- Open the Command Prompt by pressing Windows Key + X. Select Command Prompt (Admin) from the menu.
- Stop the BITS, MSI Installer, Cryptographic, and the Windows Update Services.
- Rename both the SoftwareDistribution and Catroot2 folders to <name of folder> old.
- Start now the BITS, MSI Installer, Cryptographic, and the Windows Update Services.
- Exit the Command Prompt then restart your device. After restarting, try installing the updates again.
Method Six: Disable Third-Party Antivirus
A third-party antivirus such as BitDefender may recognize the Windows Update as a threat since the new update of Windows 10 is probably not yet registered with this third-party antivirus vendor. To solve this, you must disable temporarily the antivirus before performing the update. Once the third-party antivirus is disabled, you can now proceed with the updating process. Update as well your third-party antivirus.
Method Seven: Use the DISM Tool for Windows 10
The Deployment Image Servicing and Management (DISM) is a command-line utility that is installed by default in Windows 10 system. This program is used to fix images in Windows. In the case of Error Code 0x80070020, the DISM can repair the recovery image in Windows 10 and can perform as a virtual hard disk as well.
- Scan and check files for errors.
- Open the Command Prompt by pressing Windows Key + X. Select Command Prompt (Admin) from the menu.
- Type sfc /scannow
- You can also use the following commands to check for corrupted files:
/CheckHealth – to check for corrupted files or components
/ScanHealth – to check for corrupted Windows image. This may take up to 10 minutes to finish
/RestoreHealth – to check for corrupted Windows image and do an automatic repair. This may take up to 20 to 30 minutes to finish
NOTE: In an instance where you cannot locate the good files in your computer, the system image files may be corrupted. If this happens, you need to have a copy of install.wim from a computer with good Windows 10 OS or the Windows 10 ISO file. Make sure that the source of the good files has the same language, version, and edition of your OS.
Cleaning corrupted files using DISM utility:
Enter the following commands one by one to perform the /RestoreHealth switch using the source path location of good files you copied:
- DISM /Online /Cleanup-Image /RestoreHealth /Source:repairSource install.wim
- DISM /Online /Cleanup-Image /RestoreHealth /Source:repairSource install.wim /LimitAccess
- DISM /Online /Cleanup-Image /RestoreHealth /Source:repairSource install.wim:1 /LimitAccess
For example purposes, the “repairSource” is the source of the good files.
 Error Causes
Error Causes
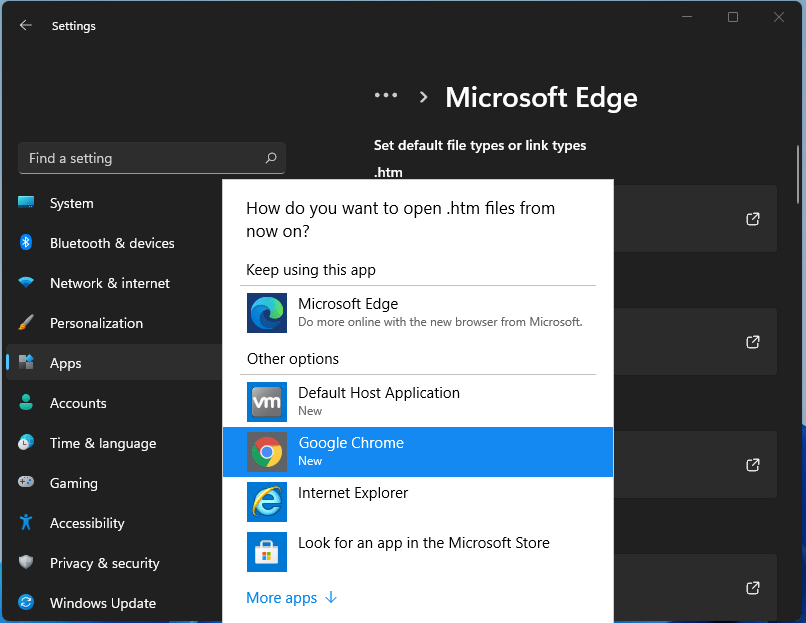 For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required.
For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required. 
 The true cause is that there is no working Border Gateway Protocol (BGP) routes into Facebook's sites. BGP is the standardized exterior gateway protocol used to exchange routing and reachability information between the internet top-level autonomous systems (AS). Most people, indeed most network administrators, never need to deal with BGP.
Cloudflare VP Dane Knecht was the first to report the underlying BGP problem. This meant, as Kevin Beaumont, former Microsoft's Head of Security Operations Centre, tweeted,
"By not having BGP announcements for your DNS name servers, DNS falls apart = nobody can find you on the internet. Same with WhatsApp btw. Facebook has basically de-platformed themselves from their own platform."
Many people are very annoyed by this and with the fact that they cannot use their social media platforms but it seems that Facebook employees are in even bigger annoyance as it was reported that Facebook employees can't enter their buildings because their "smart" badges and doors were also disabled by this network failure. If true, Facebook's people literally can't enter the building to fix things.
Reddit user u/ramenporn, who claimed to be a Facebook employee working on bringing the social network back from the dead, reported, before he deleted his account and his messages:
"DNS for FB services has been affected and this is likely a symptom of the actual issue, and that's that BGP peering with Facebook peering routers has gone down, very likely due to a configuration change that went into effect shortly before the outages happened (started roughly 1540 UTC). There are people now trying to gain access to the peering routers to implement fixes, but the people with physical access is separate from the people with knowledge of how to actually authenticate to the systems and people who know what to actually do, so there is now a logistical challenge with getting all that knowledge unified. Part of this is also due to lower staffing in data centers due to pandemic measures."
Ramenporn also stated that it wasn't an attack, but a mistaken configuration change made via a web interface.
Both BGP and DNS are down, the "connection to the outside world is down, remote access to those tools don't exist anymore, so the emergency procedure is to gain physical access to the peering routers and do all the configuration locally."
Technicians on site don't know how to do that and senior network administrators aren't on site.
It seems that it will all be down for a couple of more hours before the issue is resolved.
The true cause is that there is no working Border Gateway Protocol (BGP) routes into Facebook's sites. BGP is the standardized exterior gateway protocol used to exchange routing and reachability information between the internet top-level autonomous systems (AS). Most people, indeed most network administrators, never need to deal with BGP.
Cloudflare VP Dane Knecht was the first to report the underlying BGP problem. This meant, as Kevin Beaumont, former Microsoft's Head of Security Operations Centre, tweeted,
"By not having BGP announcements for your DNS name servers, DNS falls apart = nobody can find you on the internet. Same with WhatsApp btw. Facebook has basically de-platformed themselves from their own platform."
Many people are very annoyed by this and with the fact that they cannot use their social media platforms but it seems that Facebook employees are in even bigger annoyance as it was reported that Facebook employees can't enter their buildings because their "smart" badges and doors were also disabled by this network failure. If true, Facebook's people literally can't enter the building to fix things.
Reddit user u/ramenporn, who claimed to be a Facebook employee working on bringing the social network back from the dead, reported, before he deleted his account and his messages:
"DNS for FB services has been affected and this is likely a symptom of the actual issue, and that's that BGP peering with Facebook peering routers has gone down, very likely due to a configuration change that went into effect shortly before the outages happened (started roughly 1540 UTC). There are people now trying to gain access to the peering routers to implement fixes, but the people with physical access is separate from the people with knowledge of how to actually authenticate to the systems and people who know what to actually do, so there is now a logistical challenge with getting all that knowledge unified. Part of this is also due to lower staffing in data centers due to pandemic measures."
Ramenporn also stated that it wasn't an attack, but a mistaken configuration change made via a web interface.
Both BGP and DNS are down, the "connection to the outside world is down, remote access to those tools don't exist anymore, so the emergency procedure is to gain physical access to the peering routers and do all the configuration locally."
Technicians on site don't know how to do that and senior network administrators aren't on site.
It seems that it will all be down for a couple of more hours before the issue is resolved. 