mixGames is an Extension for Google Chrome that adds “Games:” functions to Google Chrome. In our testing, this function did not work and only redirects you back to the extension page. There are two variations of mixGames: mixGames Search, which changes the Chrome homepage to one managed by their own advertising-driven search; and mixGames Start, which changes the homepage in Chrome. These extensions utilize Searchalo to change search engine functions from the default or user-set preferences to Yahoo, injecting additional advertising. Due to the browser function modifications, mixGames is classified as potentially unwanted and is flagged for detection and optional removal by some Antivirus programs.
About Browser Hijackers
Browser hijacking is a common type of online fraud where your web browser configuration settings are altered to allow it to do things you do not intend. They are created to disrupt web browser programs for a variety of reasons. These are typically used to force hits to predetermined sites, manipulating web traffic to generate ad revenue. Nevertheless, it isn’t that innocent. Your internet safety is jeopardized and it is also extremely annoying. What’s more, hijackers can make the entire infected system fragile – other dangerous malware and viruses would use these opportunities to get into your system very easily.
Indications of browser hijack
There are various symptoms that could indicate a browser hijacking:
1. the browser’s home page is modified
2. new bookmarks pointing to pornographic websites are added to your favorite pages
3. the main web browser settings are modified and unwanted or unsafe resources are added to the trusted websites listing
4. you’re getting new toolbars you have never noticed before
5. your browser will display constant pop-up windows
6. your internet browser starts running sluggishly or exhibits frequent errors
7. you cannot go to certain sites like home pages of antivirus software.
Exactly how browser hijacker finds its way onto your computer
Browser hijackers infect computers by numerous means, including through a file-share, a drive-by download, or an infected e-mail attachment. Many internet browser hijackings come from add-on programs, i.e., browser helper objects (BHO), toolbars, or plug-ins added to web browsers to give them extra capabilities. A browser hijacker can be installed as a part of freeware, demoware, shareware, and fake programs. A good example of a well-known browser hijacker is the latest Chinese malicious software known as “Fireball”, which has infected 250 million computer systems globally. It works as a hijacker but can be turned into a full-functioning malware downloader later on.
Browser hijacking can cause severe privacy problems and even identity theft, disrupt your web browsing experience by taking command over outbound traffic, substantially slows down your personal computer by depleting a lot of resources, and result in system instability at the same time.
How you can fix a browser hijack
Some hijackers can be easily removed by uninstalling the free software they were included with or by eliminating any extension you’ve recently added to your browser. But, the majority of hijacking codes aren’t easy to remove manually, since they go deeper into your operating system. Besides, browser hijackers can modify the Windows registry therefore it can be quite hard to restore all of the values manually, especially if you’re not a very tech-savvy individual.
How To Install Safebytes Anti-Malware On An Infected PC
All malware is bad and the consequences of the damage will vary according to the specific kind of malware. Certain malware types modify web browser settings by including a proxy server or change the computer’s DNS settings. In such cases, you will be unable to visit certain or all internet sites, and therefore unable to download or install the required security software to remove the infection. If you are reading this, you may have affected by a virus that stops you from downloading a computer security application like Safebytes Anti-Malware. Do as instructed below to remove malware by alternate methods.
Get rid of viruses in Safe Mode
In Safe Mode, you could modify Windows settings, uninstall or install some applications, and remove hard-to-delete viruses. In the event the malware is blocking internet access and affecting your computer, running it in Safe Mode allows you to download anti-malware and run a diagnostic scan while limiting possible damage. To get into Safe Mode or Safe Mode with Networking, press the F8 key while the PC is starting up or run MSConfig and find the “Safe Boot” options in the “Boot” tab. Once you are in Safe Mode, you can try to download and install your antivirus software program without the hindrance of the malware. Following installation, run the malware scanner to get rid of standard infections.
Switch over to an alternative browser
Some malware only targets specific internet browsers. If this sounds like your situation, make use of another internet browser as it could circumvent the computer virus. The ideal way to avoid this issue is to pick a web browser that is well known for its security features. Firefox contains built-in Malware and Phishing Protection to keep you secure online.
Create a portable USB antivirus for removing malware
Another option would be to make a portable antivirus program on your USB flash drive. Do these simple steps to clean up your affected computer using a portable antivirus.
1) On a clean computer, download and install Safebytes Anti-Malware.
2) Plug the USB drive into the uninfected computer.
3) Double-click the executable file to open the installation wizard.
4) Choose the drive letter of the pen drive as the location when the wizard asks you where you want to install the antivirus. Follow activation instructions.
5) Transfer the flash drive from the clean PC to the infected PC.
6) Double-click the EXE file to run the Safebytes program from the pen drive.
7) Run Full System Scan to detect and get rid of all types of malware.
Protect Your Computer & Privacy With SafeBytes Anti-Malware
These days, an anti-malware tool can protect your computer from different kinds of online threats. But how do choose the best one among several malware protection software that’s available on the market? You may be aware, there are lots of anti-malware companies and tools for you to consider. Some are well worth your money, but most aren’t. You have to be very careful not to choose the wrong application, especially if you purchase a paid software. Among few good applications, SafeBytes Anti-Malware is the highly recommended program for the security-conscious user.
SafeBytes anti-malware is a powerful, very effective protection software intended to assist users of all levels of IT literacy in identifying and removing harmful threats out of their personal computers. Using its outstanding protection system, this software will quickly detect and remove the majority of the security threats, which include browser hijackers, viruses, adware, ransomware, PUPs, and trojans.
SafeBytes anti-malware takes PC protection to a whole new level with its enhanced features. The following are some of the best ones:
World-class AntiMalware Protection: Using its enhanced and sophisticated algorithm, this malware removal tool can identify and eliminate the malware threats hiding in your computer effectively.
Active Protection: SafeBytes delivers complete and real-time security for your PC. It’ll constantly monitor your pc for hacker activity and also provides users with superior firewall protection.
Website Filtering: Through its unique safety rating, SafeBytes alerts you whether a site is safe or not to visit it. This will assure that you’re always certain of your online safety when browsing the web.
Faster Scan: This tool has one of the fastest and most efficient virus scanning engines in the industry. The scans are very accurate and take a short amount of time to complete.
Low Memory/CPU Usage: SafeBytes is really lightweight software. It consumes an extremely small amount of processing power as it works in the background therefore you will not see any computer performance problems.
24/7 Assistance: You can get totally free 24/7 technical support from their computer experts on any product queries or computer security issues.
Technical Details and Manual Removal (Advanced Users)
If you do not wish to use malware removal software and like to remove mixGames manually, you may accomplish this by going to the Windows Add/Remove Programs menu in the control panel and removing the offending program; in cases of browser extensions, you could uninstall it by going to the browser’s Add-on/Extension manager. It is also suggested to factory reset your browser settings to their default state.
Lastly, examine your hard disk for all of the following and clean your Windows registry manually to remove leftover application entries following an uninstallation. But bear in mind, this is a complicated task and only computer experts can perform it safely. In addition, certain malware is capable of replicating or preventing deletion. Completing this task in Safe Mode is recommended.
Registry:
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain Default_Page_URL
HKEY_LOCAL_MachineSoftwareClassesmixGame
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun .exe
HKCUSoftwareMicrosoftWindowsCurrentVersionInternet Settingsrandom
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionrunrandom
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings CertificateRevocation = ’0
 Over time Applications change, some for the better some for worse. Some of them even stop receiving updates and are old and vulnerable. Sometimes standards change and some file types are not used anymore. Software evolves along with technology and that is good.
Keeping old and useless applications inside your Windows is not so good. From various exploits to simply taking up space, maybe even slowing down OS it is always wise and good to clean your Windows from unwanted old applications.
In this article, we will be mentioning some relics of old and providing you with an explanation of why you should remove them from your system if by any chance you still have them on it.
Over time Applications change, some for the better some for worse. Some of them even stop receiving updates and are old and vulnerable. Sometimes standards change and some file types are not used anymore. Software evolves along with technology and that is good.
Keeping old and useless applications inside your Windows is not so good. From various exploits to simply taking up space, maybe even slowing down OS it is always wise and good to clean your Windows from unwanted old applications.
In this article, we will be mentioning some relics of old and providing you with an explanation of why you should remove them from your system if by any chance you still have them on it.






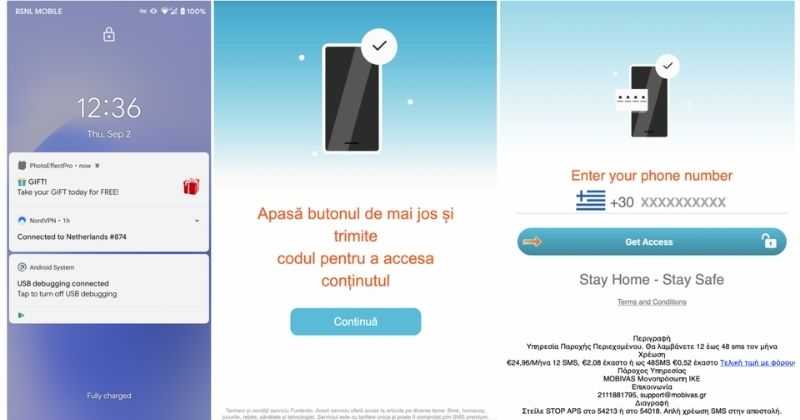 According to Zimperium zLabs, this malware that was recently detected has been doing its scams and attacks even in November of 2020 and has thus far accumulated hundreds of thousands of dollars in its scam.
On the surface it looks very harmless, asking for typical permissions like internet access, calls, and other related needed functions, and then it waits. After few months the real attack happens when users get charged with premium service they never subscribed to in the first place.
According to Zimperium zLabs, this malware that was recently detected has been doing its scams and attacks even in November of 2020 and has thus far accumulated hundreds of thousands of dollars in its scam.
On the surface it looks very harmless, asking for typical permissions like internet access, calls, and other related needed functions, and then it waits. After few months the real attack happens when users get charged with premium service they never subscribed to in the first place.
 Probably tired of even trying to hide it, Steam has released that this year's big Steam Winter sale is officially starting on December 22nd, 2021, and closing on January 5th, 2022. So if you have someone to buy a gift or just want to drop a few great games in your library at a low price this is the time when you should do it.
Probably tired of even trying to hide it, Steam has released that this year's big Steam Winter sale is officially starting on December 22nd, 2021, and closing on January 5th, 2022. So if you have someone to buy a gift or just want to drop a few great games in your library at a low price this is the time when you should do it. 