If you always use the Google Chrome browser in browsing the internet, then you might have come across an error message saying, “He’s dead, Jim!” along with a funny looking face that’s peeking its tongue out and another detailed message saying, “Either Chrome Ran out of memory or process for the webpage has terminated for some other reason. To continue, reload the webpage or go to another page”.
This error message in Google Chrome is actually quite famous and it appears for various reasons but it may have something to do with a memory issue. The Google Chrome browser is known to consume a lot of memory and the more web pages you open and load, it takes up more resources. Thus, the first thing you need to do when you encounter this error is to simply click the Reload button to continue browsing the internet or close the browser and then open it again. On the other hand, if you keep seeing this error message, then that’s a whole different story as you have to take some action to prevent it from popping up again, for good. Follow the instructions given below to fix the error in Chrome.
Option 1 – Reduce Google Chrome’s memory usage
The first thing you can try is reducing the memory usage of the Chrome browser. However, this option has a bit of a disadvantage. If a website crashes, all the instances of that website will also crash although other open tabs and websites won’t be affected. This process is referred to as “Process-per-site” mode which you will have to launch Chrome within this parameter.
Option 2 – Run Google Chrome with Strict Site Isolation
Aside from reducing Chrome’s memory usage, you can also run the browser with the Strict Site Isolation which makes sure that the crashing of one tab in the browser won’t affect the entire Windows as this feature will run every website you open on its own isolated process.
Option 3 – Run the built-in Malware Scanner and Cleanup tool in Chrome
In case you don’t know, there is actually a built-in malware scanner and cleanup tool in Chrome that helps you get rid of any unwanted ads, pop-ups, and even malware, as well as unusual startup pages, toolbars, and other things that could affect the performance of the browser.
Option 4 – Reset Google Chrome
Resetting Chrome can also help you get rid of the “He’s dead, Jim!” error message for good. Resetting Chrome means restoring its default settings, disabling all the extensions, add-ons, and themes. Aside from that, the content settings will be reset as well and the cookies, cache, and site data will also be deleted. To reset Chrome, here’s what you have to do:
- Open Google Chrome, then tap the Alt + F keys.
- After that, click on Settings.
- Next, scroll down until you see the Advanced option, once you see it, click on it.
- After clicking the Advanced option, go to the “Restore and clean up the option and click on the “Restore settings to their original defaults” option to reset Google Chrome.
- Now restart Google Chrome.
Option 5 – Perform a clean reinstall on the Chrome browser
Although reinstalling any program is easy, not so much for Google Chrome as you need to make sure that the User Data folder is deleted before you reinstall it.
- Tap the Win + R keys to open the Run prompt.
- Then type %LOCALAPPDATA%GoogleChromeUser Data in the field and hit Enter.
- Next, rename the “Default” folder inside the path you were redirected to. For instance, you can rename it to “Default-old”.
- After that, install the Chrome browser again.
Option 6 – Try to flush the DNS and reset the TCP/IP
There are instances when a network goes into haywire because of a bad DNS. Thus, a bad DNS might be the one that’s causing this headache so it’s time for you to reset the entire network to resolve the issue. To reset the network, here’s what you have to do:
- Click the Start button and type in “command prompt” in the field.
- From the search results that appear, right-click on Command Prompt and select the “Run as administrator” option.
- After opening Command Prompt, you have to type each one of the commands listed below. Just make sure that after you type each command, you hit Enter
- ipconfig /release
- ipconfig /all
- ipconfig /flushdns
- ipconfig /renew
- netsh int ip set dns
- netsh winsock reset
After you key in the commands listed above, the DNS cache will be flushed and the Winsock, as well as the TCP/IP, will reset.
- Now restart your computer and open Google Chrome then try opening the website you were trying to open earlier.
Note: You can also try changing the DNS server to the Google Server, i.e. 8.8.8.8, and then see if it works for you or not.
Option 7 – Disable both the antivirus and firewall temporarily
As you know, both the firewall and antivirus programs are there to protect the operating system from any malicious threats. So if they find that there is some malicious content in a website you are visiting, they will block the site right away. Thus, it could also be the reason why you’re getting the “He’s dead, Jim!” error so you need to disable both the firewall and antivirus program temporarily and then try opening the website again. If you are able to open the website, you need to add this site as an exception and then enable the firewall and antivirus program back.
 Error Causes
Error Causes
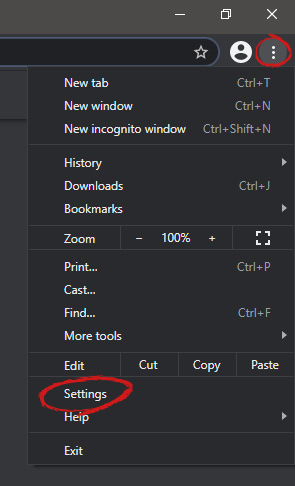 When you are in settings, on the left side move toward the bottom until you run into a tab that says On Startup and click on it. On right, a new section will open, click on Open a specific page or set of pages.
When you are in settings, on the left side move toward the bottom until you run into a tab that says On Startup and click on it. On right, a new section will open, click on Open a specific page or set of pages.
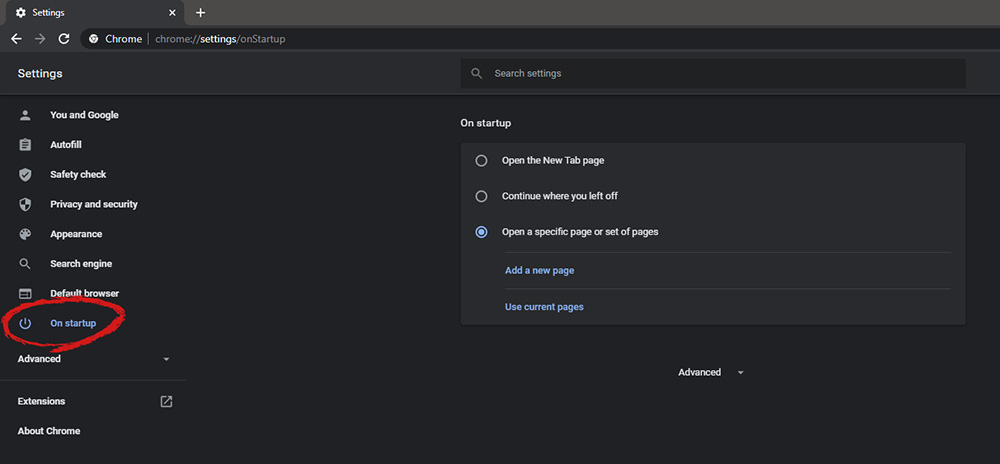 You will be presented with the option to add a new page by typing its URL or getting it from bookmarks or using a specific opened one. You can repeat this process until you have added all pages that you wish to be automatically opened once Chrome is opened for the first time.
You will be presented with the option to add a new page by typing its URL or getting it from bookmarks or using a specific opened one. You can repeat this process until you have added all pages that you wish to be automatically opened once Chrome is opened for the first time.
 Valve has announced the first gaming PC handheld console: Steam Deck. At its core, Stead Deck is just a portable, small PC in little casing. It uses AMD Zen 2 CPU and RDNA 2 GPU architecture, has 16GB of RAM, Wi-Fi, and Bluetooth.
It is a portable device with both a touchpad and joystick packing a seven-inch screen with a resolution of 1280x800 (16:10 aspect ratio). The screen has an ambient light sensor for automatic light adjustments same as your modern mobile device.
Stating to Valve battery will hold up from two to eight hours depending on the activity of the user and what exactly he is doing. The handheld comes also with a carrying case.
Valve has announced the first gaming PC handheld console: Steam Deck. At its core, Stead Deck is just a portable, small PC in little casing. It uses AMD Zen 2 CPU and RDNA 2 GPU architecture, has 16GB of RAM, Wi-Fi, and Bluetooth.
It is a portable device with both a touchpad and joystick packing a seven-inch screen with a resolution of 1280x800 (16:10 aspect ratio). The screen has an ambient light sensor for automatic light adjustments same as your modern mobile device.
Stating to Valve battery will hold up from two to eight hours depending on the activity of the user and what exactly he is doing. The handheld comes also with a carrying case.
