What is Error Code 0x80070715?
Seeing obscure error codes like 0x80070715 on the screen again and again can be annoying simply because you have no idea why it keeps popping up? What does it mean? Well, for beginners you don’t have to decode it, we’ll make it simple for you. This error code indicates missing .dll files in the system or a corrupt registry. Due to this, you get locked from accessing and running applications on your system.Solution
 Error Causes
Error Causes
This error occurs largely because of two reasons:
- Disk damage due to cluttered registry
- The system gets infected by malware or a virus(es)
Further Information and Manual Repair
Many people pay hundreds of dollars to technicians to resolve this issue on their systems. Is it worth it? Not exactly!How about we tell you a time and a money-saving way to fix the error code 0x80070715 on your PC?
The best way to resolve this issue on your system in seconds and also for free is to install Restoro. This is an advanced, powerful, and multi-functional system repair and a PC optimizer tool. It is smoothly integrated with numerous performance-driven utilities like registry cleaner, privacy error detector (anti-virus), Active X and Class error, and system stability detector. With this helper, you can resolve not only the error code 0x80070715 but also other types of PC-related errors. Whether the cause of the error code 0x80070715 on your PC is malware or cluttering cluttered disk, Restoro can be used to resolve them all. Its powerful and intuitive registry cleaner scans the registry and repairs it successfully. It removes junk files, internet history, temporary internet files, invalid entries, and also the files from the uninstalled programs still saved in the system’s registry. It wipes out all the clutter on your hard disk and cleans it in seconds freeing up plenty of space. It repairs the registry resolving the error 0x80070715 quickly. Nonetheless, if the error 0x80070715 is triggered due to viral infection or malware it removes them too. By downloading unknown files, accessing malicious websites, and opening phishing emails viruses can enter your PC. You may not be aware of these until error code 0x80070715 pops on your screen. It is wise to remove viruses right away because these give hackers access to your system which often results in data breaches and exposes users to system security threats. Restoro also works as a powerful antivirus. All malware, spyware, and viruses affecting your PC are scanned with the help of the advanced built-in privacy error detector utility. This utility embedded in the system detects viruses and malware in your system and removes them from your system successfully. Restoro is an easy-to-use repair tool. It has a simple layout and a user-friendly interface. It is easy to navigate through the repair tool, scan for errors and repair them without any hassle. Users of all levels, novice and experienced can use this tool with ease. You don’t need to be technically sound to work around this tool. Here's how to Install and run Restoro PC Fixer: In addition to this, you can run it on any Windows version. It is compatible with practically all versions. No matter what the cause for error code 0x80070715 maybe, you don’t need to get into the nitty-gritty of it and find a specific tool to resolve the issue. All you have to do is install this multi-functional Restoro on your system. Here are the 3 simple steps that you need to follow for successful repair:- Click here to install Restoro.
- Scan your PC
- Press the Repair Tab to fix the issue right away

 Once disguised it will wait patiently for a user's click and once that happens it will replicate itself and further infect the system. This rapid spread can lead to stolen personal data, some system hick-ups, and other system-related issues.
This malware mainly affects physical file transfer devices like for example and most USB drives, hard drives, and SD memory cards and it can easily transfer itself to the computer.
The advantage of this shortcut virus comparing it to others is that it is mostly undetected by a vast variety of antivirus software. So running just anti-virus software maybe not be enough to remove it from your system. Luckily for all unfortunate users that have caught this annoyance, it can be easily removed fully manually in a short time.
Once disguised it will wait patiently for a user's click and once that happens it will replicate itself and further infect the system. This rapid spread can lead to stolen personal data, some system hick-ups, and other system-related issues.
This malware mainly affects physical file transfer devices like for example and most USB drives, hard drives, and SD memory cards and it can easily transfer itself to the computer.
The advantage of this shortcut virus comparing it to others is that it is mostly undetected by a vast variety of antivirus software. So running just anti-virus software maybe not be enough to remove it from your system. Luckily for all unfortunate users that have caught this annoyance, it can be easily removed fully manually in a short time.
 In run dialog type RegEdit and press ENTER
In run dialog type RegEdit and press ENTER
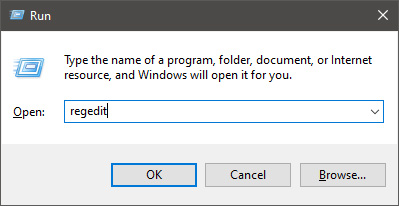 In registry editor find HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Right-click on Parameters> New> DWORD 32
Name it IRPStackSize and change the value to 32
Save and reboot your computer.
In registry editor find HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Right-click on Parameters> New> DWORD 32
Name it IRPStackSize and change the value to 32
Save and reboot your computer.
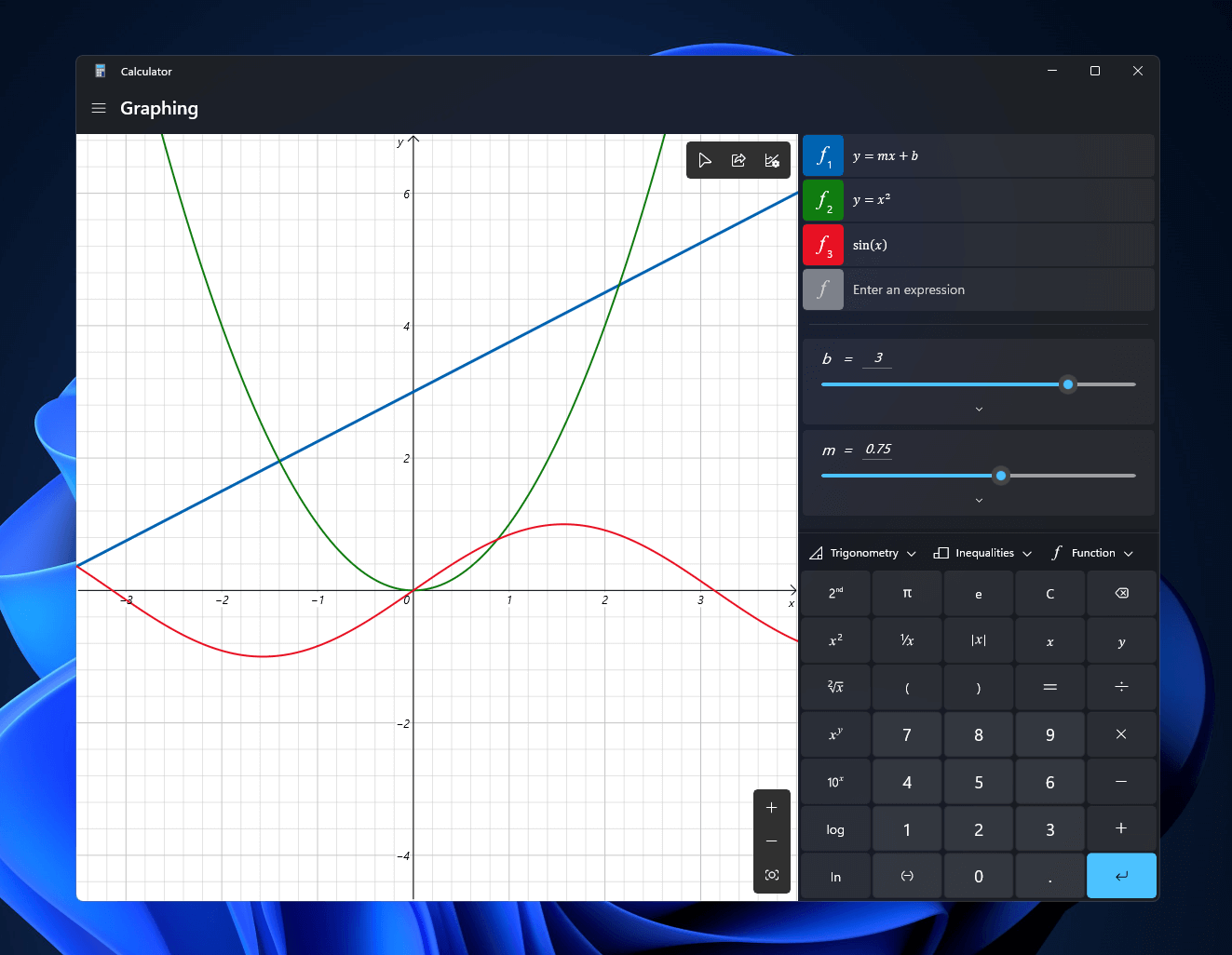 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
 Once it opens, click on Device Manager to open it,
Once it opens, click on Device Manager to open it,
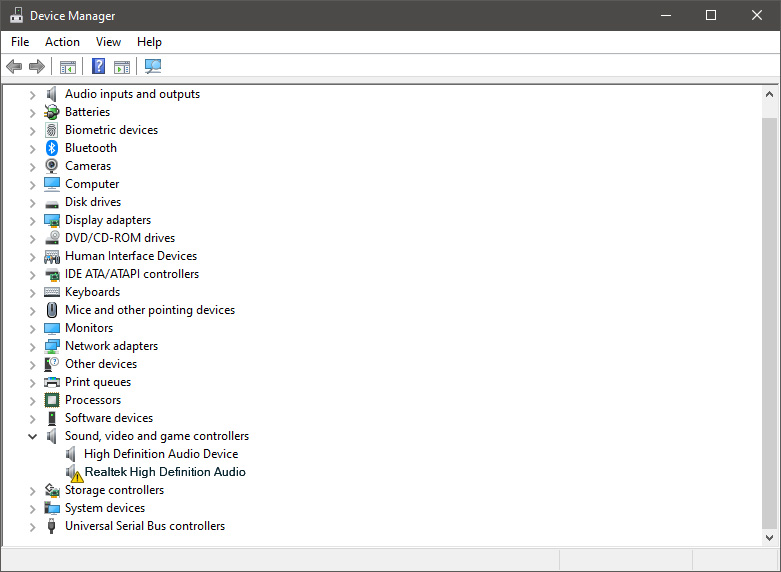 If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.