
Steam has cemented itself as the largest digital game shop in the World. First, release all the way back on September 12
th, 2003, it was meant to be a standalone software client aimed to deliver updates to Valve’s games. It was soon expanded to include titles from third parties.
The greatest Steam expansion and its popularity started in 2004 with the release of Half-life 2. Steam allowed prepurchased editions to be downloaded before the official release of the game making it available for play the moment it was officially out.
Very soon after Steam gained its popularity, Valve has opened doors to other developers and offered them to use Steam as means for a digital distribution platform. Today it hosts over 30000 different game titles, not including DLC or applications.
And how soon Valve’s steam deck is coming out soon we would like to share some great tips and tricks about Steam itself for easy everyday gaming.
Steam guard account security
Security of any of your accounts should be something that you really take seriously. So as always use a strong password for Steam but if you want an extra layer of security for it, and you should, use the Steam built-in feature: Guard Account Security.
In order to activate Security Guard go to
Steam>Settings>Account>Manage Steam Guard Account Security. Once enabled you will be able to use the Steam mobile application for special code when opening Steam or your email address.
Use Steam beta feature
Once a Steam account is created by default you will download and install the client. In the client, you will have the latest features available but there are more Steam features than default ones, beta features that can offer some improved and new functionality, and do not worry, they are stable and bug-free.
I have been in Steam beta for years and not even once have I had any issues with the client itself but I have always had the latest features that will come to regular users later.
To enable beta participation to go to
Steam>Settings>Account, open the drop-down Beta participation menu, and choose Steam Beta Update. Confirm on OK and restart the Steam client. You will now get all the latest features first.
Manage your library via Collections
The collection is a neat idea for organizing your large game library into different collections or sections easily expanded and contracted for easier navigation and organization. To add the game to a collection just right-click on it and select
Add To>New Collection, make a name for a collection like action, RPG, or whatever rocks your boat, and you are done. Once the collection is created other games can be added to it simply just by dragging it into the desired collection.
Make shelves
Shelves are ways to see your collections in the larger areas of the Steam clients. By clicking
Add Shelf>Choose a Shelf, you can now add your collection to a shelf on the larger part of the client as a horizontal scrolling container with your chosen games. There are also some predefined shelves like All Games, Recent friend activity, and more.
Hide Game from Library
By right-clicking on a game and selecting
Manage>Hide This Game you will remove the game from the active view of your Steam library. Note that the game will still be owned and a part of your library, you will just not be able to see it.
This is a great feature when for example you have some things that came as a part of the game pack you are not really interested in when you have 2 different versions of the same game as for example standard and deluxe edition or just by simply not wanting to have game visible in the library.
You can find a hidden game by typing its name in the search box and from there you can unhide it.
Play game soundtracks inside Steam
Some games offer you to purchase their soundtracks if you like music from them and some even include OST with a regular purchase. Steam lets you play these soundtracks and even lets you import your own music library folder into it in order to play all of your music inside the client itself.
It has even options to automatically stop music playing once the game is run and you can make playlists as well. Your purchased game soundtracks are automatically included, the rest you will need to add by pointing Steam to the folder where you keep music in.
Configure gamepad
Inside Steam, you can configure your gamepad’s general settings, big picture settings, desktop settings, etc. Steam embraced the idea that many OC users these days own and play with gamepads so it has implemented configuration options inside it. To configure your pad go to
Steam>Settings>Controller.
Use big picture Steam mode
Big picture mode is Steam's idea of making Steam an entertainment center. Once it is activated it switches from the application into full-screen mode aimed at large TV screens or monitors. You can easily navigate through it via gamepad, mouse, keyboard, or other devices.
You have access to the store, your game library, etc. Same as your typical steam app but a little different. You can easily activate it via
View> Big Picture Mode and see for yourself is this something you prefer over a standard application layout.
Enable Steam Cloud
Steam Cloud is a great feature that uses cloud storage to save your game progress meaning that you can easily switch to another PC, install games there and continue where you have left off. Many games support this feature instead of keeping saves locally and it is a great feature worth turning it ON.
To turn and use Steam Cloud service go to
Steam>Settings>Cloud>Enable Steam Cloud Synchronization. Just remember to check does game you are playing supports this option.
Share your Games via Family sharing
Family sharing is a Steam feature allowing you to share your game library with up to 5 accounts on up to 10 different devices. This is a great way to let other members of your family or even close friends enjoy some games you have or vice versa. They will get as well their own save games so you can sleep safe knowing that your progress can not be changed or hindered.
Family sharing can be turned ON by logging into PC Steam client where you would like to share your library and navigate to
Steam>Settings>Family and then clicking on Authorize Library Sharing On This Computer.
Refund a game
Sometimes the game is not the same as advertised, sometimes it will not work on your PC, sometimes hardware specifications are too high making the game unplayable, etc. For whatever reason, you might have Steam offers you a full game price refund if you wish to do so, you only need to meet 2 criteria, the game must have been purchased within 2 weeks period, older purchases cannot be refunded, and your game playtime must not be over 2 hours of game time.
If you fit into this category all you need to do in order to get the full money back is going to
Help>Steam Support, pick a recent game from the eligible list, and ask for a refund.
Gift a game
As you can buy gifts for your friends or loved ones in real life, Valve made sure you can do it in digital as well. Gifting game via Steam is simple and straightforward. Choose a game you wish to gift, go to your shopping cart and instead of clicking Purchase for myself, click on
Purchase As a Gift, from there you will be taken to your friend list to choose to whom you would like to gift a game along with the option to write a little note to the receiver like happy birthday, enjoy or whatever.
Stream games in Steam itself
Although Steam is not there yet in streaming as Twitch or Facebook gaming is, there is an option to stream your game sessions on it. Click on
Steam>Settings>Broadcast to make all adjustments and start streaming.
You can also watch streams from your friend list and Steam is now broadcasting popular streams directly to its client if you want to watch it.
Take a game screenshot
By pressing
F12, you can take a screenshot from any game and save it inside your Steam cloud library. You can change of course this default screenshot key via
Settings>In-Game and if you would like to see your screenshots you can always do it under
View Screenshot Library on a game’s page.
That’s it, our Steam tips and tricks for easy and good gaming life, I hope to see you soon on errortools.com for your daily articles, tips, and tricks.


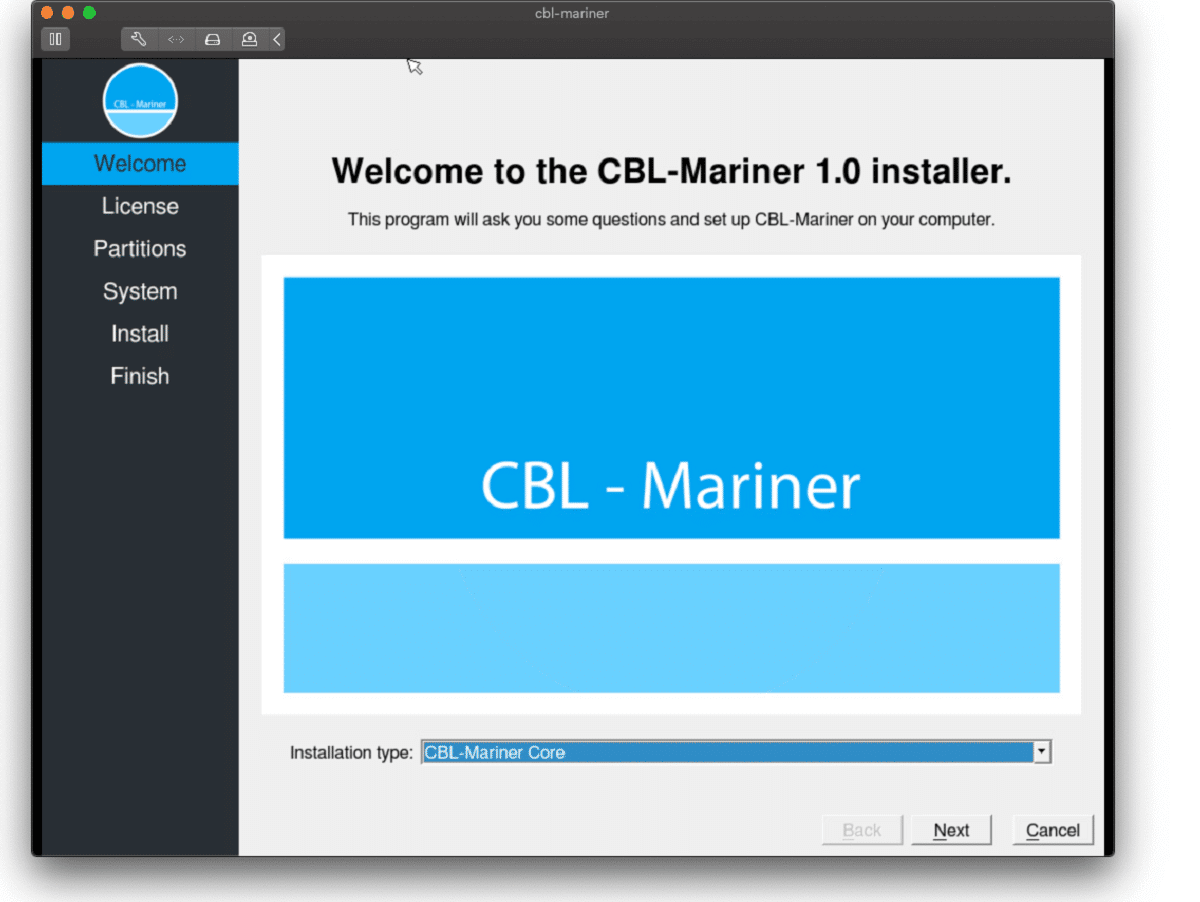 Well if anyone told me just a few years ago that I will see the day when Microsoft releases a new OS based on Linux I would be very amused, but that day has come. Mariner is the newest OS out of nowhere.
Microsoft’s new Linux Distro, dubbed Common Base Linux (CBL)-Mariner, isn’t the type of distro you’d want to install directly on any old machine. It’s primarily meant for cloud infrastructure and edge products. Specifically Microsoft’s Cloud and Edge products.
But if you are curious, it’s possible to run. Juan Manuel Rey, a Microsoft Senior Program Manager for Azure VMware, recently published a guide to ISO CBL-Mariner image. With that, you can easily get it up and running. And you can build CBL-Mariner on an Ubuntu 18.04 desktop. So you can try it out since it is free.
You can get it from here:
Well if anyone told me just a few years ago that I will see the day when Microsoft releases a new OS based on Linux I would be very amused, but that day has come. Mariner is the newest OS out of nowhere.
Microsoft’s new Linux Distro, dubbed Common Base Linux (CBL)-Mariner, isn’t the type of distro you’d want to install directly on any old machine. It’s primarily meant for cloud infrastructure and edge products. Specifically Microsoft’s Cloud and Edge products.
But if you are curious, it’s possible to run. Juan Manuel Rey, a Microsoft Senior Program Manager for Azure VMware, recently published a guide to ISO CBL-Mariner image. With that, you can easily get it up and running. And you can build CBL-Mariner on an Ubuntu 18.04 desktop. So you can try it out since it is free.
You can get it from here:  Steam has cemented itself as the largest digital game shop in the World. First, release all the way back on September 12th, 2003, it was meant to be a standalone software client aimed to deliver updates to Valve’s games. It was soon expanded to include titles from third parties.
The greatest Steam expansion and its popularity started in 2004 with the release of Half-life 2. Steam allowed prepurchased editions to be downloaded before the official release of the game making it available for play the moment it was officially out.
Very soon after Steam gained its popularity, Valve has opened doors to other developers and offered them to use Steam as means for a digital distribution platform. Today it hosts over 30000 different game titles, not including DLC or applications.
And how soon Valve’s steam deck is coming out soon we would like to share some great tips and tricks about Steam itself for easy everyday gaming.
Steam has cemented itself as the largest digital game shop in the World. First, release all the way back on September 12th, 2003, it was meant to be a standalone software client aimed to deliver updates to Valve’s games. It was soon expanded to include titles from third parties.
The greatest Steam expansion and its popularity started in 2004 with the release of Half-life 2. Steam allowed prepurchased editions to be downloaded before the official release of the game making it available for play the moment it was officially out.
Very soon after Steam gained its popularity, Valve has opened doors to other developers and offered them to use Steam as means for a digital distribution platform. Today it hosts over 30000 different game titles, not including DLC or applications.
And how soon Valve’s steam deck is coming out soon we would like to share some great tips and tricks about Steam itself for easy everyday gaming.
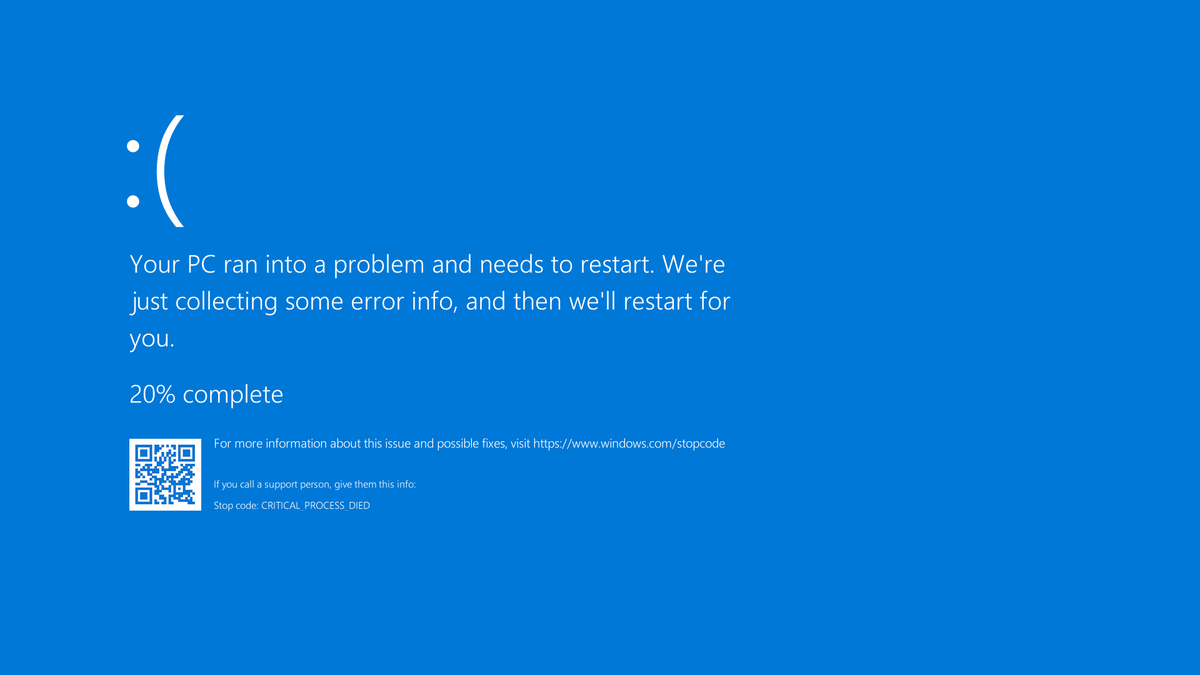 A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
 On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update.
On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update. It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
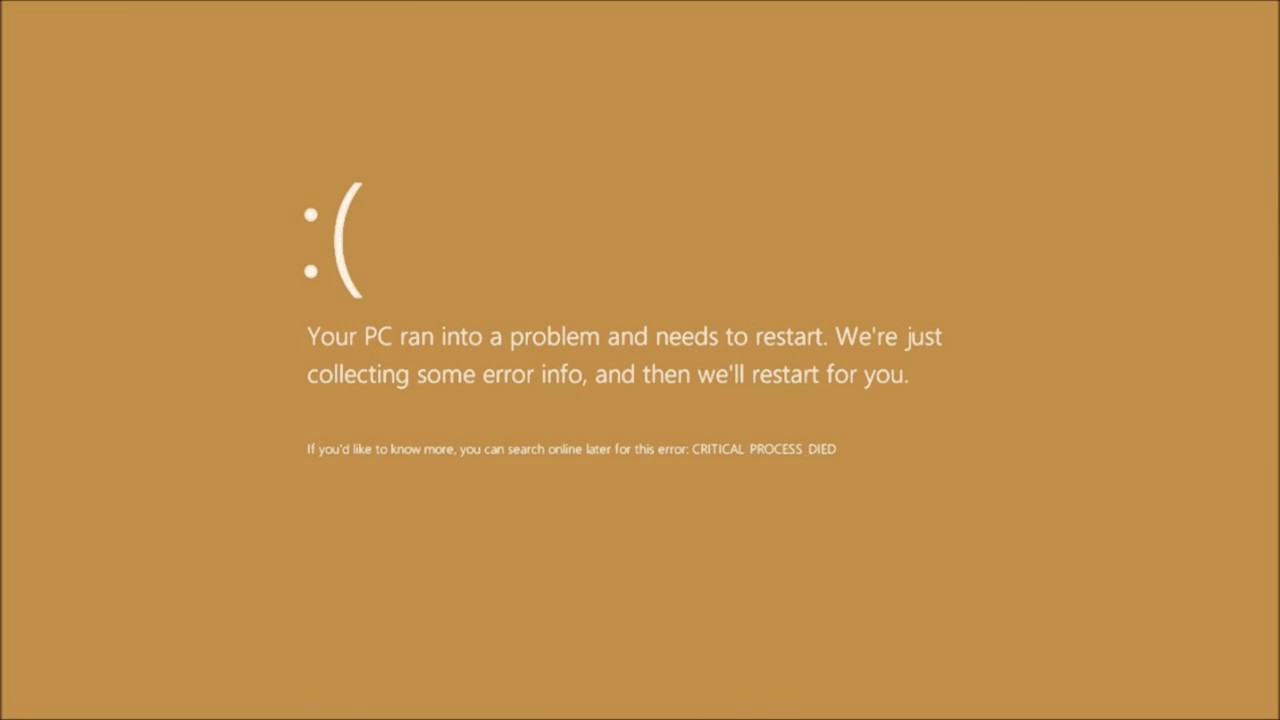 The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers).
The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers). It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
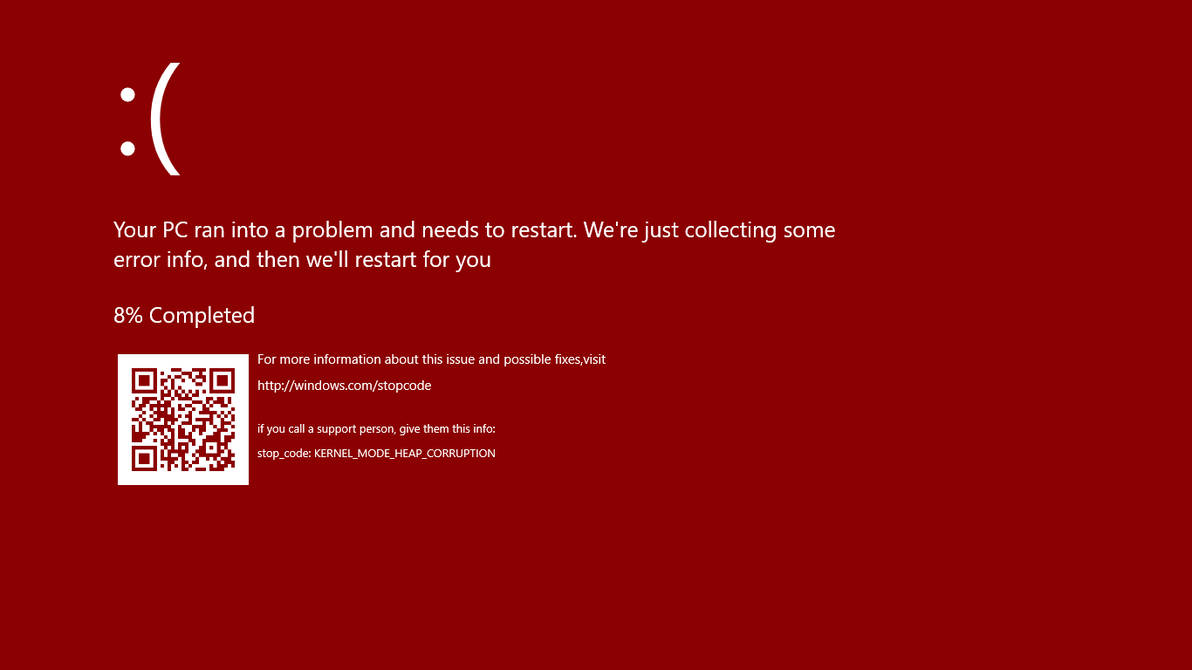 Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.
Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.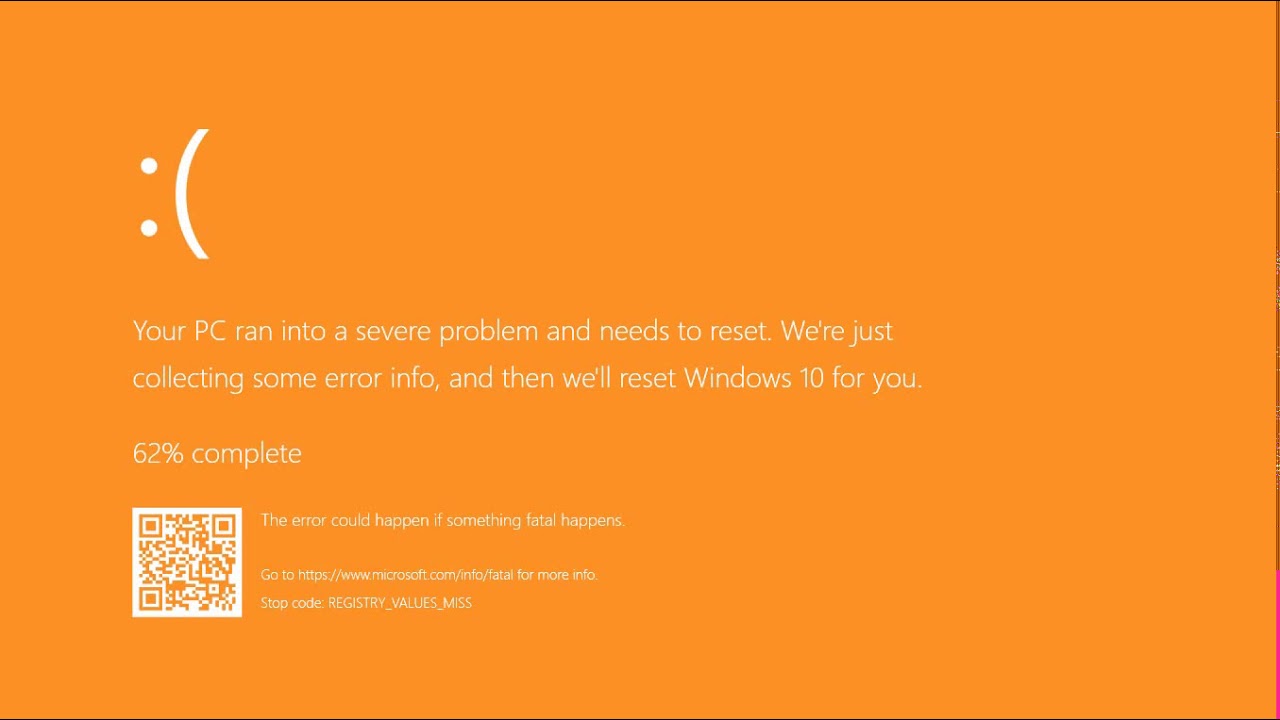 The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
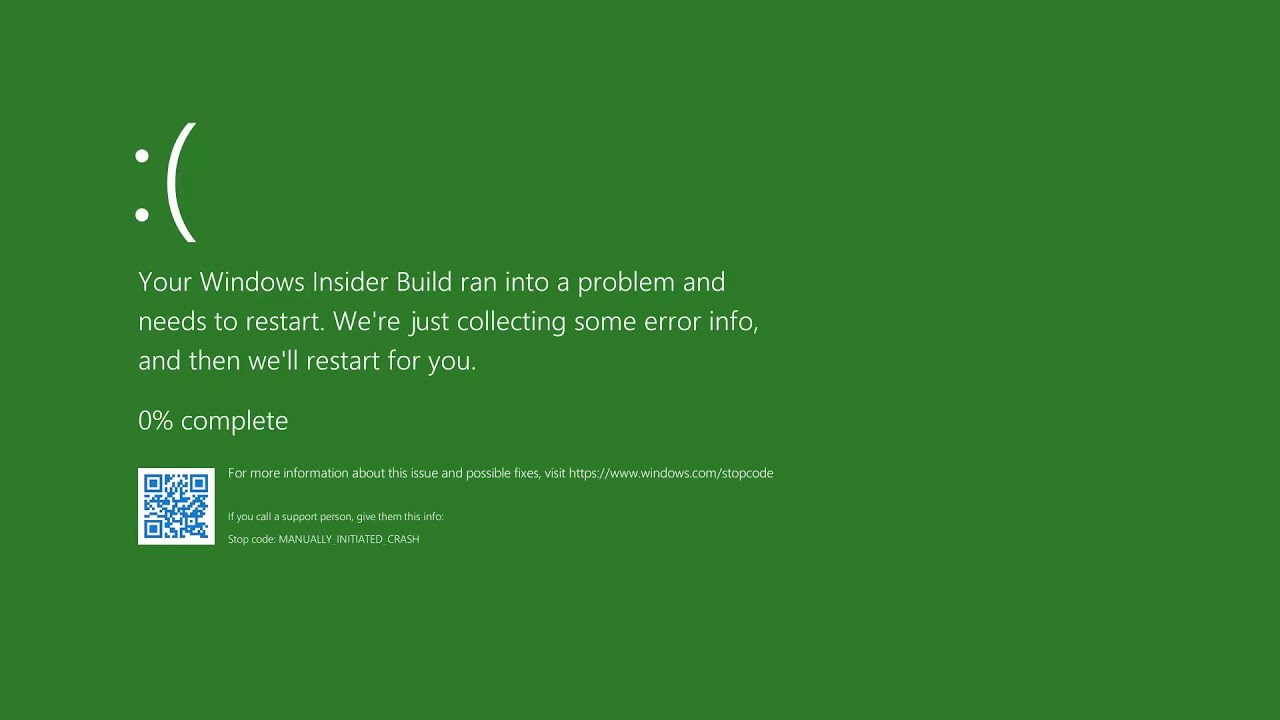 The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10.
The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10. The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware.
The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware. 
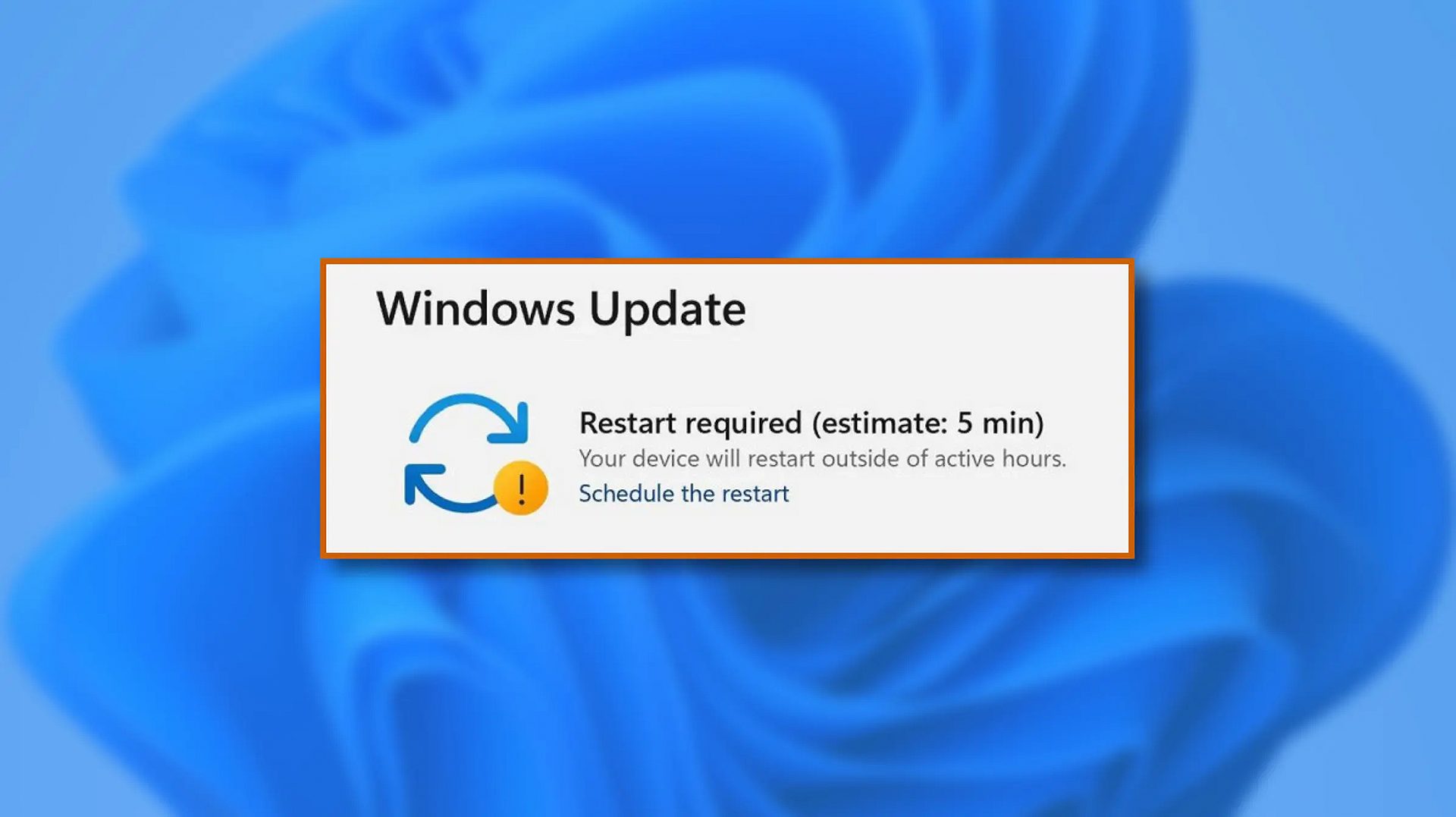 When Windows 11 update is available but you do not wish to restart right away because you are in the middle of using a computer, you can schedule a restart for up to 7 days. It is very easy and we will show you how to do it.
When Windows 11 update is available but you do not wish to restart right away because you are in the middle of using a computer, you can schedule a restart for up to 7 days. It is very easy and we will show you how to do it.
