Driver Pro Description
DriverPro is a program developed by PC Utilities Pro. This program is often found bundled in other installations.
From the author: PC Utilities Pro is a leading software development company founded in 2009. As a group of young enthusiastic programmers, we constantly strive in creating powerful, yet easy-to-use solutions that would enable even the most basic computer users to keep their PCs running like new.
When installed, DriverPro will add registry entries for the current user that allow it to run each time to computer is started. It will also add a scheduled task in Windows, that allows it to run at various times. The optimizing nature of the application allows it to access any file and information on your computer without your knowledge.
Multiple anti-virus programs have marked this application as a Potentially Unwanted Program, and it is not recommended to keep it on your computer.
About Potentially Unwanted Applications
Have you ever discovered an unwanted program running on your PC and wondered exactly how the heck it got there? A PUA / PUP (potentially unwanted application / potentially unwanted program) is a software program that comes bundled with freeware/shareware and you agree to install on your computer. These are programs you certainly don’t want on your computer since it doesn’t provide any useful service.
Despite being regarded very dangerous, PUPs aren’t necessarily computer viruses or malware What makes a PUP different from malware is the fact that whenever you download one, you are doing it with your consent – though in most instances unwittingly and unwillingly. PUPs might not be malware but still, they’re harmful programs to your computer. At best, these unwanted applications provide hardly any benefit, and at worst, they could be quite damaging to your computer.
What do PUPs do on your computer, really?
Most Potentially Unwanted Programs will come in the form of adware, which typically aims to exhibit numerous irritating pop-up ads, banners, coupons, and bargains on websites you go to. PUPs that come as browser add-ons and toolbars are readily identifiable. They’ll track your online activities, redirect your search results to unsafe websites where spyware and adware can be downloaded, hijack your home page, and slow your internet browser down to a crawl.
PUPs load up a dangerous bite if kept unchecked. They will often include things like information gathering program code which could gather and send your sensitive information back to 3rd parties. These are programs that don’t really do anything good for you; in addition to occupying space on the hard drive, they also slow down your PC, often alter settings without your authorization, the list of annoying features goes on and on.
Great tips on protecting yourself from unwanted software
• When setting up anything on your computer system, always study the fine print, like the license agreement. Don’t accept terms of use that are for bundled programs.
• Only Use the “custom” or “manual” install method – and never blindly click Next, Next, Next.
• Use an advert blocker/pop-up blocker; Install anti-malware products such as Safebytes Anti-malware. These software programs could establish a wall between the computer and cybercriminals.
• Think twice before you decide to download any type of freeware or shareware. Just before adding a plug-in or web browser extension, think about whether it is really necessary.
• Only download programs from the original providers’ websites. Avoid download portals because they use their very own download manager to pack extra programs along with the initial download.
Help! Malware Blocking Anti-virus Installation And Access To The Web
All malware is bad, but certain kinds of malicious software do a lot more damage to your computer than others. Some malware is meant to hinder or block things that you wish to do on your computer. It may well not allow you to download anything from the net or it will stop you from accessing some or all websites, particularly the anti-malware sites. So what you should do if malware prevents you from downloading or installing Safebytes Anti-Malware? Do as instructed below to get rid of the malware in alternate ways.
Get rid of malware in Safe Mode
The Windows operating system has a special mode known as “Safe Mode” where just the bare minimum required programs and services are loaded. In the event, the virus is set to load automatically when the PC starts, shifting to this mode may well prevent it from doing so. To start the computer into Safe Mode, press the “F8” key on the keyboard just before the Windows boot screen appears; Or right after normal Windows boot up, run MSConfig, check the Safe Boot under the Boot tab, and click Apply. After you restart into Safe Mode with Networking, you could download, install, and update the anti-malware program from there. Now, you are able to run the anti-virus scan to eliminate computer viruses and malware without any interference from another malicious application.
Switch to some other internet browser
Web-based viruses could be environment-specific, aiming for a particular internet browser or attacking particular versions of the browser. If you appear to have malware attached to Internet Explorer, then switch over to a different internet browser with built-in safety features, such as Firefox or Chrome, to download your favorite antivirus program – Safebytes.
Run anti-virus from your USB drive
Another way is to download and transfer an anti-malware program from a clean computer to run a scan on the affected system. Adopt these measures to run the anti-malware on the infected computer system.
1) On a clean computer, download and install Safebytes Anti-Malware.
2) Plug the pen drive into the uninfected computer.
3) Run the setup program by double-clicking the executable file of the downloaded application, which has a .exe file format.
4) Select the USB flash drive as the location when the wizard asks you where you intend to install the software. Follow the activation instructions.
5) Remove the flash drive. You may now utilize this portable antivirus on the infected computer.
6) Run the Safebytes Anti-malware directly from the flash drive by double-clicking the icon.
7) Press the “Scan” button to run a full system scan and remove viruses automatically.
Detect And Remove Viruses With SafeBytes Anti-Malware
Want to download the very best anti-malware software for your laptop or computer? There are many applications available that come in paid and free versions for Microsoft Windows computers. A few are worth your money, but many aren’t. You need to pick a company that creates industry-best antimalware and has earned a reputation as reliable. Among few good programs, SafeBytes Anti-Malware is the strongly recommended software for the security-conscious end user.
Safebytes is one of the well-established PC solutions firms, which provide this complete anti-malware software program. This software program can easily detect, remove, and protect your computer from the most advanced malware intrusions such as adware, spyware, trojan horses, ransomware, parasites, worms, PUPs, along with other potentially harmful software applications.
SafeBytes anti-malware offers a plethora of advanced features that set it apart from all others. The following are some of the good ones:
Real-time Protection: SafeBytes provides complete and real-time security for your personal machine. It will regularly monitor your computer for hacker activity and also gives users superior firewall protection.
Best AntiMalware Protection: This deep-cleaning anti-malware program goes much deeper than most antivirus tools to clean out your computer system. Its critically acclaimed virus engine finds and disables hard to remove malware that hides deep within your PC.
Web Protection: SafeBytes gives an instant safety rating about the web pages you are about to check out, automatically blocking unsafe sites and ensuring that you are certain of your safety while browsing the world wide web.
Fast Scan: SafeBytes Anti-Malware has a multi-thread scan algorithm that works up to 5x faster than any other antivirus software.
Very Low CPU and RAM Usage: This software program is not “heavy” on your computer’s resources, so you’ll not notice any overall performance problems when SafeBytes is operating in the background.
Fantastic Tech Support Team: You will get 24/7 technical assistance to promptly resolve any issue with your security application.
Technical Details and Manual Removal (Advanced Users)
To remove Driver Pro manually, navigate to the Add/Remove programs list in the Control Panel and choose the offending program you want to get rid of. For web browser plug-ins, go to your web browser’s Addon/Extension manager and select the add-on you want to remove or disable. You may also want to reset your web browser settings, as well as clear your web browser cache and cookies.
Lastly, check your hard disk for all of the following and clean your registry manually to remove leftover application entries after uninstalls. Please note that only professional computer users should try to manually edit the system files mainly because removing any single vital registry entry leads to a major problem or even a computer crash. Also, certain malware is capable of replicating itself or preventing its removal. Carrying out this in Safe Mode is suggested.
Files:
%Program Files%\Driver Pro\Driver Pro.exe
%UserProfile%\Desktop\Driver Pro.lnk
%UserProfile%\Start Menu\Driver Pro\Driver Pro.lnk
%UserProfile%\Start Menu\Driver Pro\Help.lnk
%UserProfile%\Start Menu\Driver Pro\Registration.Lnk
Registry:
HKEY_CURRENT_USER\Software376694984709702142491016734454
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run 13376694984709702142491016734454
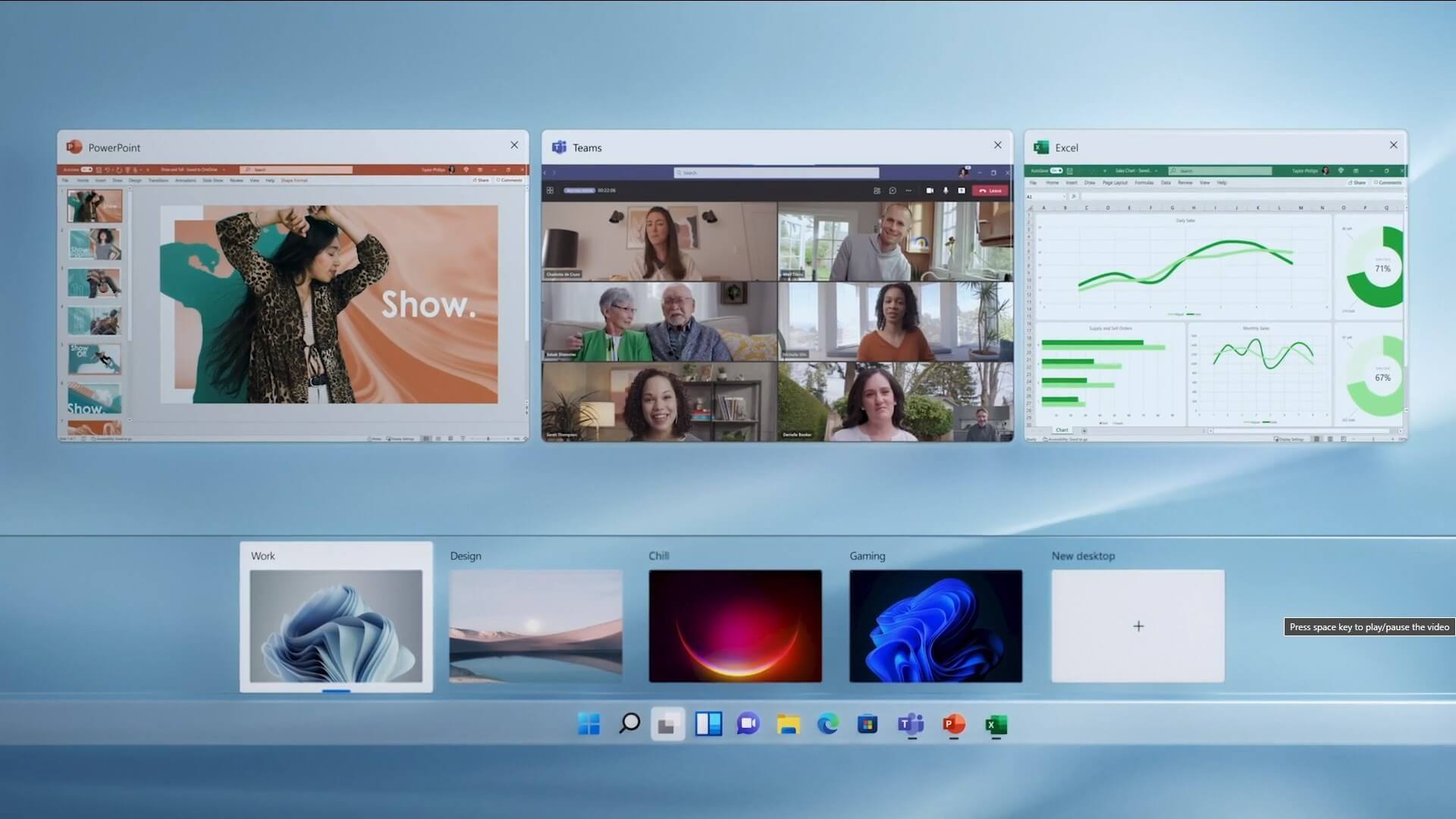 The feature that was originally planned for now scrapped Windows 10X is included in Windows 11. You will be able to customize your Virtual desktop with different wallpapers for each screen.
In order to fully customize your virtual desktops with different wallpapers follow this easy step-by-step guide.
The feature that was originally planned for now scrapped Windows 10X is included in Windows 11. You will be able to customize your Virtual desktop with different wallpapers for each screen.
In order to fully customize your virtual desktops with different wallpapers follow this easy step-by-step guide.


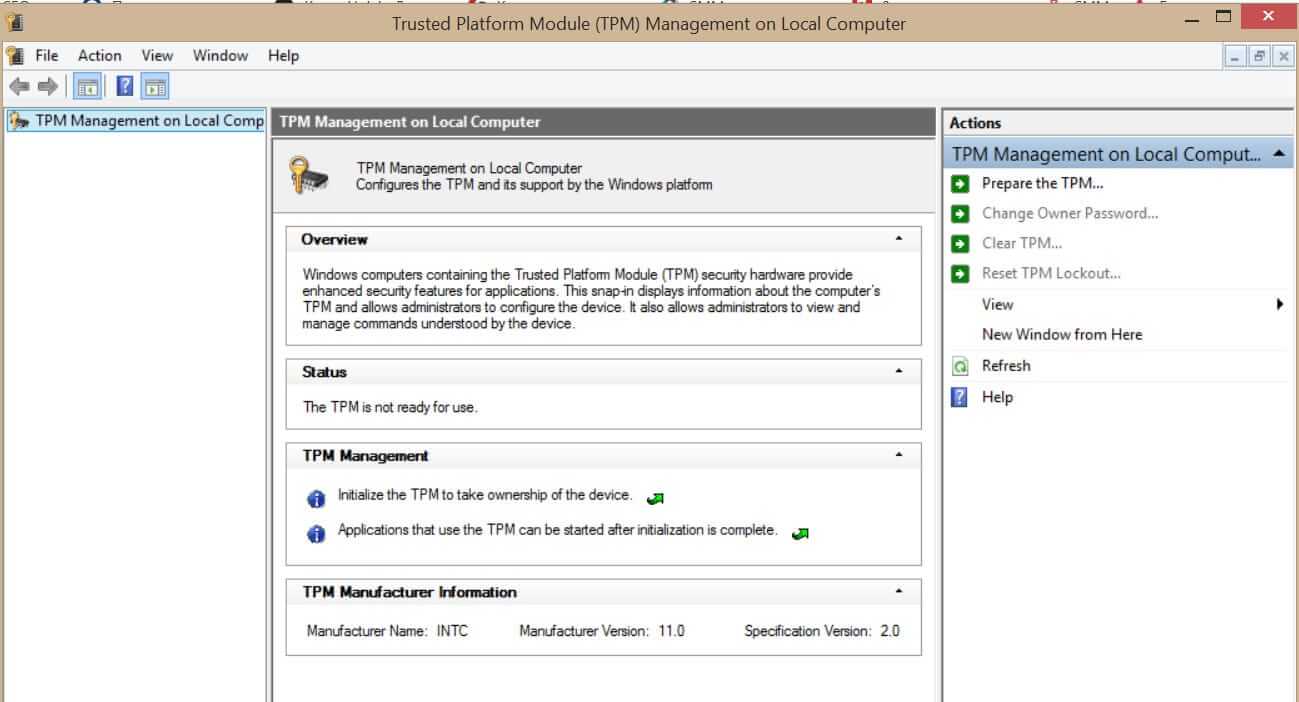 What exactly is TPM?
What exactly is TPM?