22H2 update for Windows 11 will arrive later this year and although Microsoft is not releasing anything big there will be some interesting improvements and fixes. We take a look at some that caught our attention.
One of the most interesting upcoming features is enhanced phishing protection. Microsoft Defender SmartScreen will be upgraded to alert users when they try to store passwords in plain text files and also if they accidentally type in a Microsoft account password on phishing sites.
"These enhancements will make Windows the world's first operating system with phishing safeguards built directly into the platform and shipped out of the box to help users stay productive and secure without having to learn to be their own IT department,"
Microsoft
Finally, Windows File explorer is getting tabs that will allow much easier management of folders and files inside it.
It is confirmed that Microsoft is also working on a new 'HOME' sidebar that should be modern in design and in features including OneDrive so you can find everything in one place.
Pinning of favorite files was also mentioned so you can easily pin favorites for quick access.
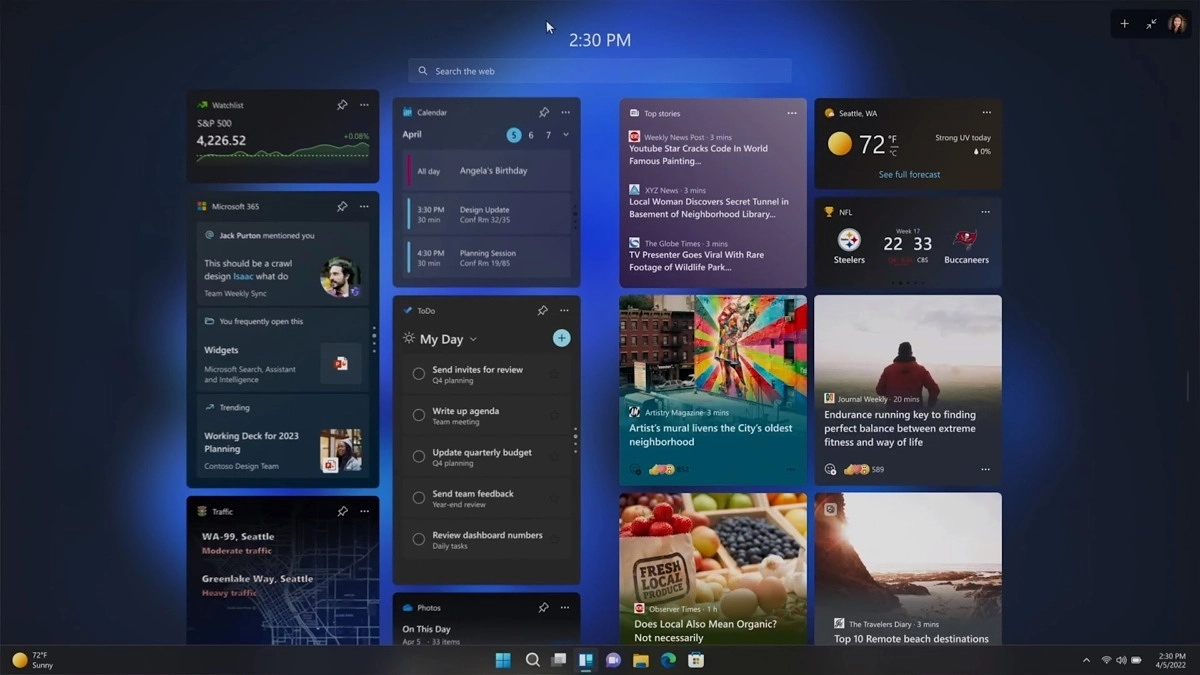
Windows 11 has brought back widgets in a new way and from all the feedback users are loving them. Currently, you have a widget sidebar on the left part of the screen where you have your chosen store widgets but from the Microsoft teaser, we will have soon the option to have them in full screen.
If you are using a widget for reading news, blogs, etc. this feature will be very good since you will be able to use your whole screen for information and not just a part of it.
Another new feature is 'suggested actions' which is going to be particularly useful in apps like Microsoft Teams. With this new feature, you can highlight a date in a Teams message and Windows will suggest actions.
For example, if you highlight a date, you'll see a recommendation to create an event in Microsoft Calendar for that day.

 Error Causes
Error CausesAnother driver device error message you might encounter is error code 41.“The drivers for this device are not installed. (Code 28)”
“This policy setting determines whether User Activities can be published. If you enable this policy setting, activities of type User Activity are allowed to be published. If you disable this policy setting, activities of type User Activity are not allowed to be published. Policy change takes effect immediately.”
 Error Causes
Error Causes Microsoft’s initial Windows 11 hardware requirements were not really well received by users and they were not really clearly represented from the start making a lot of potential customers slowly drift away from the hype.
It seems that Microsoft has acknowledged this since they have changed their tune about system hardware requirements for the upcoming Windows 11.
It seems that Windows 11 will be able to be officially installed on unsupported computers but with a little inconvenience.
Microsoft’s initial Windows 11 hardware requirements were not really well received by users and they were not really clearly represented from the start making a lot of potential customers slowly drift away from the hype.
It seems that Microsoft has acknowledged this since they have changed their tune about system hardware requirements for the upcoming Windows 11.
It seems that Windows 11 will be able to be officially installed on unsupported computers but with a little inconvenience.
 Error Causes
Error Causes