For three decades, Wolfram Mathematica has defined the state of the art in technical computing and provided the principal computation environment for millions of innovators, educators, students, and others around the world.
Widely admired for both its technical prowess and elegant ease of use, Mathematica provides a single integrated, continually expanding system that covers the breadth and depth of technical computing—and seamlessly available in the cloud through any web browser, as well as natively on all modern desktop systems.
With energetic development and consistent vision for three decades, Mathematica stands alone in a huge range of dimensions, unique in its support for today's technical computing environments and workflows.
A Vast System, All Integrated
Mathematica has nearly 5,000 built-in functions covering all areas of technical computing—all carefully integrated so they work perfectly together, and all included in the fully integrated Mathematica system.
Not Just Numbers, Not Just Mathematica But Everything
Building on three decades of development, Mathematica excels across all areas of technical computing—including neural networks, machine learning, image processing, geometry, data science, visualizations, and much more.
Unimaginable Algorithm Power
Mathematica builds in unprecedentedly powerful algorithms across all areas—many of them created at Wolfram using unique development methodologies and the unique capabilities of the
Wolfram Language.
Higher Level Than Ever Before
Superfunctions, meta-algorithms... Mathematica provides a progressively higher-level environment in which as much as possible is automated—so you can work as efficiently as possible.
Everything Is Industrial Strength
Mathematica is built to provide industrial-strength capabilities—with robust, efficient algorithms across all areas, capable of handling large-scale problems, with parallelism, GPU computing, and more.
Powerful Ease of Use
Mathematica draws on its algorithmic power—as well as the careful design of the Wolfram Language—to create a system that's uniquely easy to use, with predictive suggestions, natural language input, and more.
Documents As Well As Code
Mathematica uses the Wolfram Notebook Interface, which allows you to organize everything you do in rich documents that include text, runnable code, dynamic graphics, user interfaces, and more.
The Code Makes Sense
With its intuitive English-like function names and coherent design, the Wolfram Language is uniquely easy to read, write, and learn.
Make Your Results Look Their Best
With sophisticated computational aesthetics and award-winning design, Mathematica presents your results beautifully—instantly creating top-of-the-line interactive visualizations and publication-quality documents.
150,000+ Examples
Get started with almost any project with help from 150,000+ examples in the
Documentation Center, over 10,000 open-code Demonstrations in the
Wolfram Demonstrations Project—and a host of other resources.
Instant Real-World Data
Mathematica has access to the vast
Wolfram Knowledgebase, which includes up-to-the-minute real-world data across thousands of domains.
Seamless Cloud Integration
Mathematica is now
seamlessly integrated with the cloud—allowing sharing, cloud computing, and more in a unique and powerful hybrid cloud/desktop environment
Connected to Everything
Mathematica is built to be connected to everything: file formats (180+), other languages,
Wolfram Data Drop, APIs, databases, programs, the
Internet of Things,
devices—and even distributed instances of itself.
If you would like to
read more helpful
articles and tips about various software and hardware visit
errortools.com daily.
 Error Causes
Error Causes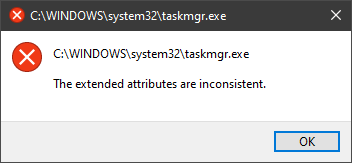 In this guide, we will show you common ways in fixing Extended Attributes are inconsistent errors inside your Windows that are easy to do and less time-consuming than complete reinstallation of the system.
In this guide, we will show you common ways in fixing Extended Attributes are inconsistent errors inside your Windows that are easy to do and less time-consuming than complete reinstallation of the system.
 Check the Epic Games Status page
Check the Epic Games Status page
