As you know, Microsoft’s Windows Media Creation Tool is a useful tool that helps you download and install the latest version of the Windows 10 operating system. However, there are times when it could encounter some problems during the update process. One of these programs is the following error message:
“0x8007001F-0x20006, The installation failed in the SAFE_OS phase with an error during REPLICATE_OC operation.”
The error pointed out the “Safe OS phase”. It is the phase that’s initiated to install all the required Windows Updates. Thus, the possible cause for this error could have something to do with an interrupted download, internet connection, and many more. Although this error could be caused by a lot of factors, fixing it shouldn’t be that hard. You can try to reset the Windows Update Components or delete the Windows Update cache. You could also disable both the Firewall and your antivirus program temporarily or run the Windows Update in a Clean Boot state, as well as run the Windows Update troubleshooter. To get started troubleshooting the error, follow each one of the suggestions provided below.
Option 1 – Try to reset the Windows Update components
Resetting the Windows Update components could help you resolve the Windows Update error 0x8007001f – 0x20006. How? Refer to the following steps:
- Open Command Prompt with admin privileges.
- After that, type each one of the following commands and hit Enter after you key in one after the other.
- net stop wuauserv
- net stop cryptsvc
- net stop bits
- net stop msiserver
Note: The commands you entered will stop the Windows Update components such as Windows Update service, Cryptographic services, BITS, and MSI Installer.
- After disabling WU components, you need to rename both the SoftwareDistribution and Catroot2 folders. To do that, type each one of the following commands below, and don’t forget to hit Enter after you type one command after the other.
- ren C:WindowsSoftwareDistribution SoftwareDistribution.old
- ren C:WindowsSystem32catroot2 Catroot2.old
- Now, restart the services you’ve stopped by entering another series of commands. Don’t forget to hit Enter after you key in one command after the other.
- net start wuauserv
- net start cryptsvc
- net start bits
- net start msiserver
- Exit Command Prompt and then restart your computer.
Option 2 – Try to delete the Windows Update Cache
You might also want to delete the Windows Update cache since there are times when existing corrupt or incomplete Windows Update files can cause some problems in downloading and installing Windows Updates. To achieve this, simply delete the “$Windows.~BT” & “$Windows.~WS” folders in your computer. Once you’re done, try to run Windows Update again and see if the error is now fixed.
Option 3 – Try to temporarily disable anti-virus and Windows Defender Firewall
As mentioned, the error could be due to the antivirus program or the Windows Defender Firewall installed on your computer. Thus, disabling them or any security software installed in your computer is always a good idea you can try when you’re not able to access the shared drive on your computer. There are times when you encounter problems like error 0x8007001f – 0x20006 due to interference of antivirus or security programs. Thus, you have to disable both your antivirus program and Windows Defender Firewall for the meantime and check if it fixes the error or not
Option 4 – Run the Windows Update in a Clean Boot State
It is possible that some third-party application is the one that’s causing the problem so it’s best if you put your computer in a Clean Boot state. During this state, you can start the system with a minimum number of drivers and startup programs that will surely help you in isolating the root cause of the issue.
- Log onto your PC as an administrator.
- Type in MSConfig in the Start Search to open the System Configuration utility.
- From there, go to the General tab and click “Selective startup”.
- Clear the “Load Startup items” check box and make sure that the “Load System Services” and “Use Original boot configuration” options are checked.
- Next, click the Services tab and select the “Hide All Microsoft Services” check box.
- Click Disable all.
- Click on Apply/OK and restart your PC. (This will put your PC into a Clean Boot State. And configure Windows to use the usual startup, just simply undo the changes.)
- After that, try to run Windows Update again.
Note: If you are able to install the app without any trouble at all then it means that the error is caused by some third-party application on your computer. You need to look for the culprit and uninstall it once you found it.
Option 5 – Run the Windows Update Troubleshooter
You might also want to run the Windows Update Troubleshooter as it could also help in fixing error 0x8007001f – 0x20006. To run it, go to Settings and then select Troubleshoot from the options. From there, click on Windows Update and then click the “Run the troubleshooter” button. After that, follow the next on-screen instructions and you should be good to go.


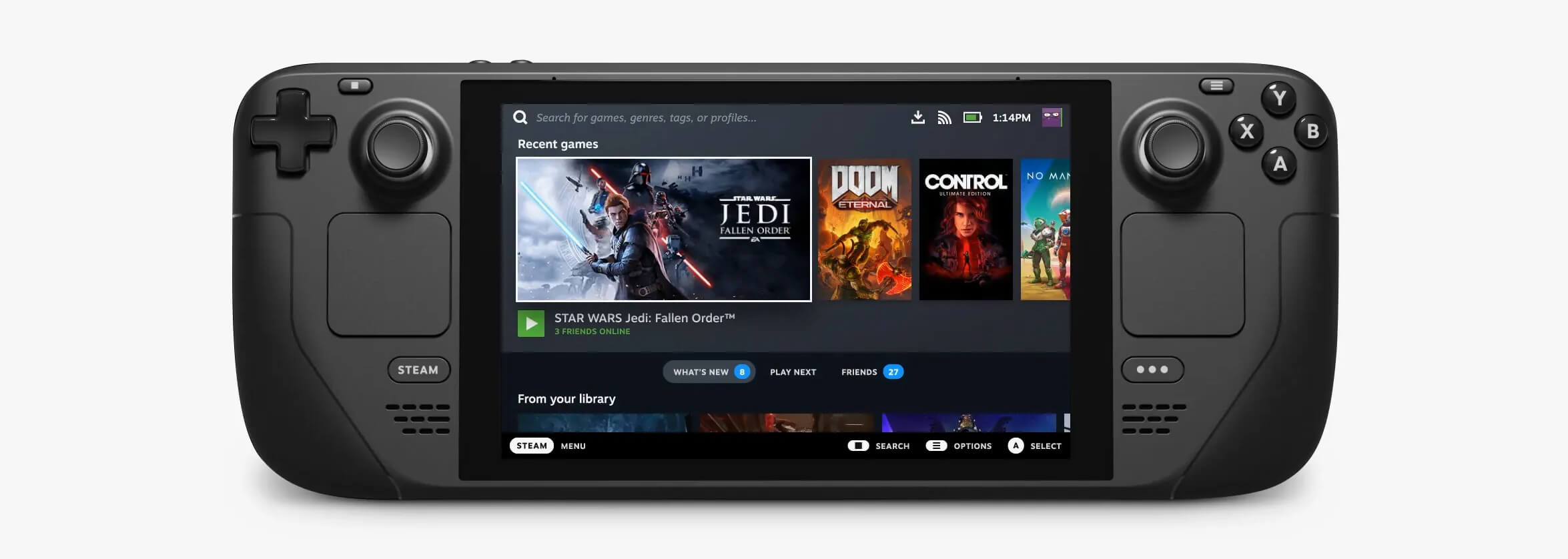 Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11.
Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11.  When it comes to computer peripherals first thing that comes to people's minds is probably Mouse and Keyboard. Also when discussing peripherals brands, Razer is not a stranger and over the years it has built its name and cult following.
Razer’s mechanical keyboards have been always in the upper field of quality and trust from users and Huntsman is no different.
When it comes to computer peripherals first thing that comes to people's minds is probably Mouse and Keyboard. Also when discussing peripherals brands, Razer is not a stranger and over the years it has built its name and cult following.
Razer’s mechanical keyboards have been always in the upper field of quality and trust from users and Huntsman is no different.
