RealOnlineRadio is a Browser Extension for Google Chrome. This extension offers users the ability to listen to radio stations across the web.
From the Author: Real Online Radio is different, as it is a simple radio aggregator. This means Real Online Radio puts together thousands of independent radio stations from all parts of the world in a browser extension that is free and easy to use. It is made for people, who want to have control over their radio streaming. With our simple radio widget, you can get an overview of thousands of radio stations both from your hometown and from the rest of the world. With Real Online Radio, you can listen to your favorite radio station or get an impression of all styles and sorts of music – without being guided in a specific direction by anybody – or anything (such as those radio bots). Real Online Radio returns the control to you, to discover exactly the kind of music that you love.
While this may look useful, this extension changed your default search engine and hijacks your home page. While this extension is active, all your searches are redirected through fileupsticks.com, where a database of your search queries is kept to better server ads that are later delivered through the Yahoo search engine.
About Browser Hijackers
Browser hijackers (also known as hijackware) are a type of malware that changes internet browser configurations without the user’s knowledge or approval. These kinds of hijacks happen to be rising at an astonishing rate across the world, and they can be truly nefarious and sometimes harmful too. Nearly all browser hijackers are created for marketing or advertising purposes. These are generally used to force visitors to a specific website, manipulating web traffic to generate ad revenue. Even though it might appear naive, these tools are designed by vicious individuals who always attempt to take full advantage of you, so that they could make money from your naive and distraction. Browser hijackers can also allow other vicious programs without your knowledge to further damage your PC.
Signs of browser hijacker malware
Below are some signs and symptoms that indicate your internet browser has been hijacked: your browser’s home page has been reset to some mysterious site; you find redirected to websites you never intended to visit; the default web browser settings are changed and/or your default search engine is altered; you find multiple toolbars on the browser; you’ll find random pop-ups start showing regularly; your internet browser starts running sluggishly or displays frequent glitches; you can’t visit certain sites such as homepages of antivirus software.
How it infects the computer
Browser hijackers can get into a computer by some means or other, including via file sharing, downloads, and e-mail as well. They may also be deployed via the installation of an internet browser toolbar, add-on, or extension. A browser hijacker could also be installed as a part of freeware, shareware, demoware, and fake programs. An example of some infamous browser hijackers includes Babylon, Anyprotect, Conduit, SweetPage, DefaultTab, Delta Search, and RocketTab, however, the names are continually changing.
The presence of any browser hijacker malware on your system can substantially diminish the web browsing experience, record your online activities that lead to serious privacy concerns, develop system stability issues and finally cause your PC to slow down or to a nearly unusable condition.
Browser Hijacker Malware – Removal
The one thing you could try to eliminate a browser hijacker is to locate the malicious software in the “Add or Remove Programs” list in the Microsoft Windows Control Panel. It might or might not be there. If it is, try and uninstall it. However, the majority of hijacking codes are certainly not very easy to get rid of manually, as they go deeper into the operating system. Also, browser hijackers can modify the Computer registry so it could be very tough to restore all the values manually, particularly if you are not a tech-savvy person.
You can go for automatic browser hijacker removal by just installing and running a reliable anti-malware application. SafeBytes Anti-Malware will counter persistent browser hijackers and provide you real-time PC protection against all types of malware.
Can't Install Safebytes Anti-malware due to the presence of Malware? Try This!
Practically all malware is detrimental and the level of the damage will differ greatly in accordance with the type of infection. Certain malware goes to great lengths to stop you from installing anything on your computer, especially anti-virus software programs. If you’re reading this, odds are you’re stuck with a malware infection that is preventing you to download and/or install the Safebytes Anti-Malware program on your computer system. There are some actions you can take to get around this problem.
Install anti-malware in Safe Mode with Networking
If the virus is set to load automatically when Microsoft Windows starts, stepping into safe mode could very well block the attempt. Only the bare minimum required applications and services are loaded when you start your personal computer into Safe Mode. You need to do the following to get rid of malware in Safe mode.
1) After switching on the computer, hit the F8 key before the Windows splash screen begins to load. This will conjure up the “Advanced Boot Options” menu.
2) Choose Safe Mode with Networking with arrow keys and press Enter.
3) As soon as this mode loads, you will have the internet. Now, obtain the malware removal software you need by utilizing the web browser. To install the application, follow the directions in the installation wizard.
4) Immediately after installation, run a complete scan and allow the software to delete the threats it detects.
Download the security program using an alternate web browser
Certain viruses may target vulnerabilities of a specific browser that block the downloading process. If you’re not able to download the security application using Internet Explorer, this means the virus is targeting IE’s vulnerabilities. Here, you should switch to an alternate web browser like Chrome or Firefox to download Safebytes Anti-malware software.
Install and run anti-malware from the Thumb drive
To successfully get rid of the malware, you have to approach the issue of installing an anti-virus software program on the infected computer system from a different perspective. Adopt these measures to run the antivirus on the affected computer system.
1) Download the anti-malware software on a virus-free computer.
2) Put the USB drive into the clean computer.
3) Double-click the executable file to open the installation wizard.
4) When asked, select the location of the USB drive as the place where you would like to put the software files. Follow the on-screen instructions to complete the installation.
5) Transfer the flash drive from the clean PC to the infected computer.
6) Double click the Safebytes Anti-malware icon on the USB drive to run the software.
7) Hit the “Scan Now” button to start the virus scan.
Overview of SafeBytes Anti-Malware
These days, anti-malware software can protect your laptop or computer from various kinds of internet threats. But exactly how to choose the right one amongst countless malware protection application that’s available out there? As you may be aware, there are several anti-malware companies and products for you to consider. Some are really worth your money, but most aren’t. When searching for an anti-malware program, choose one that gives dependable, efficient, and total protection against all known computer viruses and malware. One of the recommended software programs is SafeBytes AntiMalware. SafeBytes carries a good track record of excellent service, and customers seem to be happy with it.
SafeBytes anti-malware is a trustworthy tool that not only protects your computer completely but is also extremely user-friendly for people of all ability levels. With its outstanding protection system, this tool will instantly detect and remove the majority of the security threats, which include browser hijackers, viruses, adware, PUPs, trojans, worms, and ransomware.
There are many great features you’ll get with this security product. Listed here are some of the great ones:
Real-time Active Protection: Malware programs trying to enter the system are discovered and stopped as and when detected by the SafeBytes real-time protection shields. This tool will always keep track of your computer for any suspicious activity and updates itself regularly to keep abreast of the constantly changing threat situation.
Best AntiMalware Protection: Using a critically acclaimed malware engine, SafeBytes offers multilayered protection that is made to find and remove threats that are concealed deep in your computer’s operating system.
Safe Web Browsing: Safebytes assigns all websites a unique safety rating that helps you to have an idea of whether the webpage you are about to visit is safe to view or known to be a phishing site.
Low CPU/Memory Usage: This software is lightweight and will work quietly in the background, and will not have an effect on your computer efficiency.
Fantastic Tech Support: You will get 24/7 technical assistance to quickly resolve any concern with your security application.
SafeBytes has put together a wonderful anti-malware solution that can help you conquer the latest malware threats and virus attacks. Malware issues will become a thing of the past when you put this tool to use. If you want sophisticated forms of protection features and threat detections, purchasing SafeBytes Anti-Malware could be worth the dollars!
Technical Details and Manual Removal (Advanced Users)
If you would like to carry out the removal of RealOnlineRadio manually instead of utilizing an automated software tool, you may follow these steps: Navigate to the Windows Control Panel, click the “Add or Remove Programs” and there, select the offending program to remove. In cases of suspicious versions of browser plugins, you can actually get rid of it via your browser’s extension manager. You will probably also want to reset your internet browser.
Finally, check your hard drive for all of the following and clean your registry manually to remove leftover application entries following uninstalls. However, this is often a tricky task and only computer professionals could perform it safely. In addition, some malicious programs have the capability to defend against its removal. Doing this in Safe Mode is recommended.

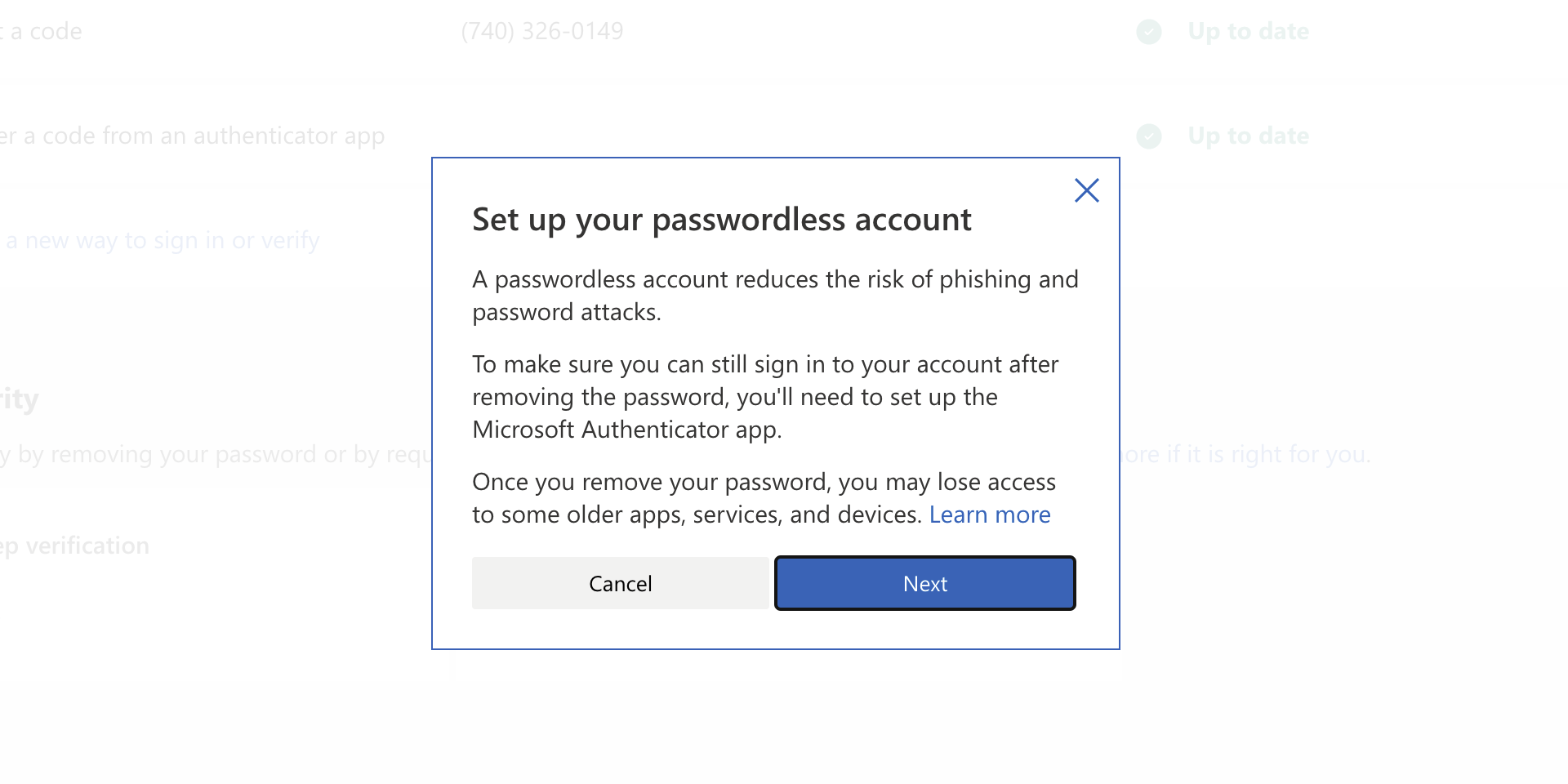 As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
 5 Essential IT skills everybody should know
5 Essential IT skills everybody should know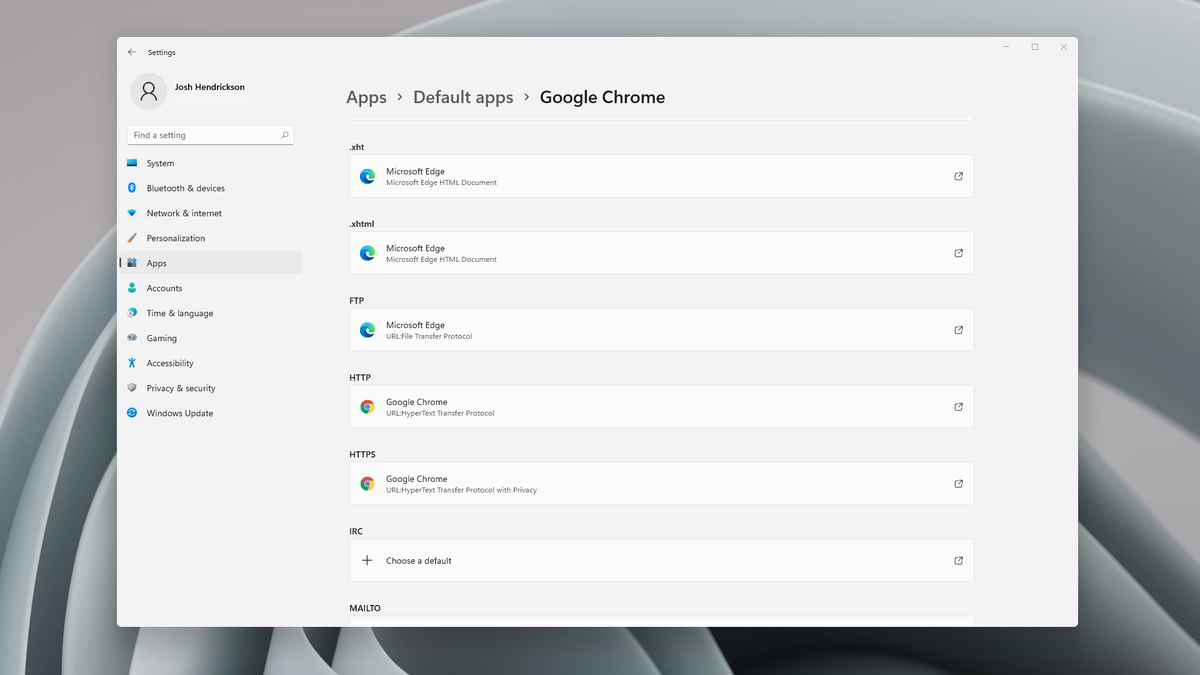 Choosing default browser in settings
Choosing default browser in settings

