PC Fix Speed is a Potentially Unwanted Program designed to improve the speed of your computer. This program usually comes bundled with other software, and when installs automatically scan your PC and displays exaggerated messages on the status of the PC’s performance, to get users to pay for the PRO version of the software. It also adds registry entities that allow it to run each time the computer is started, and the application itself will constantly keep reminding users that they have errors by putting the application windows on top.
From the Author: The Service is provided by PCRx through Crawler, LLC. Clean and repair your PC’s registry, optimize PC performance and free up disk and memory space. With everything you do on your PC, including adding on devices, a new entry is created in your Windows® registry, and seldom are any removed after they’re no longer needed. As a result, your PC gets bogged down with unnecessary entries, slowing your PC speed, the start-up, and your Internet browser. PC Fix Speed cleans up registry entries and puts your PC back on track for optimal performance. PC Fix Speed is an essential application that should be a part of every computer. PC Fix Speed especially helps computers that are unusually slow, freeze up often or show error messages, by cleaning the system registry and improving overall performance.
About Potentially Unwanted Applications
If you have ever downloaded software from the internet (shareware, freeware, etc,), it’s quite possible you’ve unconsciously installed unwanted programs on your computer system. A Potentially Unwanted Program, often known as PUP, in short, is software that contains adware, installs toolbars, or has other hidden goals. These kinds of programs are usually bundled up with free applications that you download from the internet or will also be bundled inside the custom installers on many download sites.
It’s clear by its name – unwanted programs – but did not actually constitute “malware” in the traditional sense. An important difference between malware and PUP is distribution. Malware is normally dropped through vulnerability exploitation while PUP gets installed with the consent of the user, who intentionally or unwittingly approves the PUP installation on their computer. PUP developers can argue their programs aren’t malicious software however, it can nevertheless be unsafe software and put your PC at risk much the same way malware does.
Exactly how do PUPs look like?
Unwanted programs come in various forms. More often, they can be found in adware bundlers which are known to utilize aggressive and misleading advertising. Most bundlers install many adware programs from a number of vendors, each of which possesses its own EULA policy. Safebytes Anti-malware entirely eliminates this threat and safeguards your computer against unwanted programs or adware infection. Several PUPs also show up as toolbars or add-ons, mounted on your preferred web browser. These toolbars change your homepage and your search engine in the installed browser, track your web activities, control your search results with redirects and sponsored links, and eventually slow down your browser and diminish your web browsing experience.
Potentially Unwanted Programs occasionally act very much like viruses or spyware. Some PUPs carry keyloggers, dialers, and other software to collect your personal details that can cause identity theft. Because of this unwanted program, your application may freeze, your security protections can get disabled which could leave your computer susceptible, your system may get ruined, and the list goes on and on.
Some tips on protecting yourself from PUPs
• Read meticulously before you install anything. Don’t click accept until you have read the fine print. There could be a clause about PUPs.
• Use ONLY custom or manual install method – and don’t blindly click Next, Next, Next.
• Use good anti-malware software. Try Safebytes Anti-malware which can spot PUPs and handle them as malware by flagging them for removal.
• Be alert if you install freeware, open-source programs, or shareware. Disable or eliminate toolbars and browser extensions you don’t really need.
• Only download applications from the original providers’ websites. Avoid download portals since they use their very own download manager to pack additional programs together with the initial download.
Remember the fact that although PUPs could cause damage and hinder the proper function of the computer, they can’t get into your system without your consent, so be watchful not to provide them with it.
What To Do If You Cannot Install Any Antivirus?
Malware could cause a great deal of damage to your PC. Some malware sits in between your PC and your net connection and blocks some or all internet sites that you would like to check out. It could also prevent you from adding anything to your PC, especially the antivirus program. So what should you do when malware prevents you from downloading or installing Anti-Malware? Although this kind of issue will be tougher to get around, there are some steps you can take.
Start your computer in Safe Mode
If the malware is set to load at Windows start-up, then booting in Safe Mode should prevent it. Only the bare minimum required applications and services are loaded whenever you start your laptop or computer into Safe Mode. Listed below are the steps you should follow to boot into the Safe Mode of your Windows XP, Vista, or 7 computers (check out the Microsoft website for instructions on Windows 8 and 10 PCs).
1) At power-on/startup, tap the F8 key in 1-second intervals. This will bring up the Advanced Boot Options menu.
2) Make use of the arrow keys to select Safe Mode with Networking and press ENTER.
3) When you are into this mode, you will have an internet connection again. Now, use your web browser to download and install an anti-malware program.
4) After the application is installed, allow the diagnostic scan run to eliminate trojans and other threats automatically.
Switch to an alternate web browser
Web-based viruses could be environment-specific, aiming for a particular internet browser or attacking specific versions of the web browser. The ideal way to avoid this problem is to select an internet browser that is well known for its security features. Firefox contains built-in Malware and Phishing Protection to keep you safe online.
Make a bootable USB anti-virus drive
Here’s yet another solution which is using a portable USB anti-malware software package that can check your computer for malware without needing installation. To run anti-virus from a USB drive, follow these simple steps:
1) Make use of another virus-free PC to download Safebytes Anti-Malware.
2) Plug in the pen drive to a USB port on the uninfected computer.
3) Double-click the executable file to run the installation wizard.
4) Choose a USB drive as the location when the wizard asks you where you want to install the application. Follow the instructions on the computer screen to finish off the installation process.
5) Now, insert the USB drive into the corrupted PC.
6) Double-click the EXE file to run the Safebytes tool right from the thumb drive.
7) Click the “Scan” button to run a full system scan and remove viruses automatically.
SafeBytes AntiMalware Overview
Want to download the best anti-malware software program for your system? There are various applications available that come in free and paid versions for Microsoft Windows systems. A few are good ones, some are decent, while some are merely bogus anti-malware programs that can damage your personal computer themselves! When searching for an anti-malware tool, select one which gives dependable, efficient, and complete protection against all known viruses and malware. On the list of highly recommended software is SafeBytes Anti-Malware. SafeBytes carries a superb track record of excellent service, and customers appear to be happy with it.
SafeBytes can be described as a powerful, real-time antivirus application that is created to assist the typical computer end user in protecting their PC from malicious threats. This tool can easily detect, remove, and protect your computer from the most advanced malware intrusions including adware, spyware, trojan horses, ransomware, worms, PUPs, parasites, and other potentially harmful software programs.
There are plenty of amazing features you will get with this particular security product. Here are some of the features you will like in SafeBytes.
Active Protection: SafeBytes provides a totally hands-free active protection that is set to observe, block, and remove all computer threats at its first encounter. This utility will always keep track of your PC for suspicious activity and updates itself continuously to keep abreast of the constantly changing threat landscape.
Anti-Malware Protection: This deep-cleaning anti-malware software goes much deeper than most antivirus tools to clean your computer system. Its critically acclaimed virus engine finds and disables hard-to-remove malware that hides deep inside your PC.
Web protection: Through its unique safety rating, SafeBytes informs you whether a site is safe or not to access it. This will make sure that you’re always certain of your online safety when browsing the web.
Low Memory/CPU Usage: SafeBytes is a lightweight and easy-of-use anti-virus and antimalware solution. As it uses very little computer resources, this application leaves the computer’s power exactly where it belongs: with you.
24/7 Premium Support: SafeBytes provides 24/7 technical support, automatic maintenance, and updates for the best user experience.
SafeBytes has developed a wonderful anti-malware solution that can help you conquer the latest malware threats and virus attacks. You can rest assured that your computer system will be protected in real-time as soon as you put this software to use. So if you need sophisticated forms of protection features and threat detections, purchasing SafeBytes Anti-Malware will be well worth the dollars!
Technical Details and Manual Removal (Advanced Users)
If you do not want to use malware removal software and prefer to get rid of PC Fix Speed manually, you might do so by going to the Add/Remove Programs menu in the control panel and removing the offending software; in cases of web browser plug-ins, you could un-install it by going to the browser’s Add-on/Extension manager. You will definitely also want to reset your browser.
Finally, examine your hard drive for all of the following and clean your computer registry manually to remove leftover application entries after uninstalls. However, this is a tough task and only computer professionals can perform it safely. Moreover, some malware keeps replicating which makes it tough to get rid of. It is advised that you carry out the removal procedure in Windows Safe Mode.
Folders:
C:\Program files\PC Fix Speed\
C:\Documents and Settings\All Users\Start menu\Programs\PC Fix Speed\
C:\Program filesx7Help\
Registry:
HKLM\SOFTWARE\PCFixSpeed
HKCU\Software\PCFixSpeed
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\PCFixSpeed
 Error Causes
Error Causes
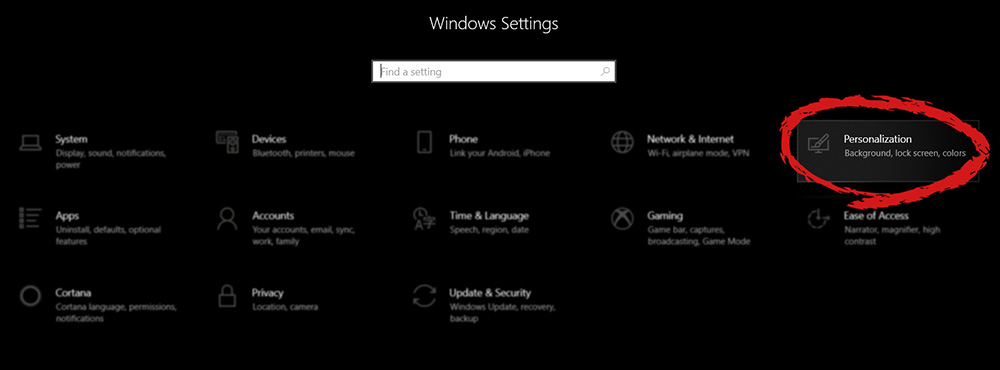 When the personalization setting opens go-to color tab on left and scroll down until you find 2 checkboxes under "show accent color on the following surfaces:"
When the personalization setting opens go-to color tab on left and scroll down until you find 2 checkboxes under "show accent color on the following surfaces:"
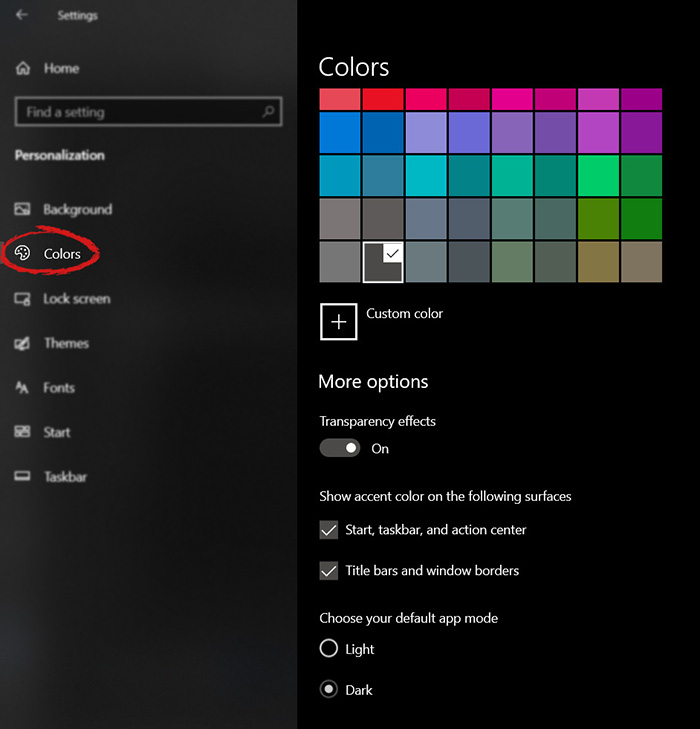 check ones you wish to apply the effect to and you are done. Now your START menu and/or title bars are using the color scheme of your choice.
check ones you wish to apply the effect to and you are done. Now your START menu and/or title bars are using the color scheme of your choice. 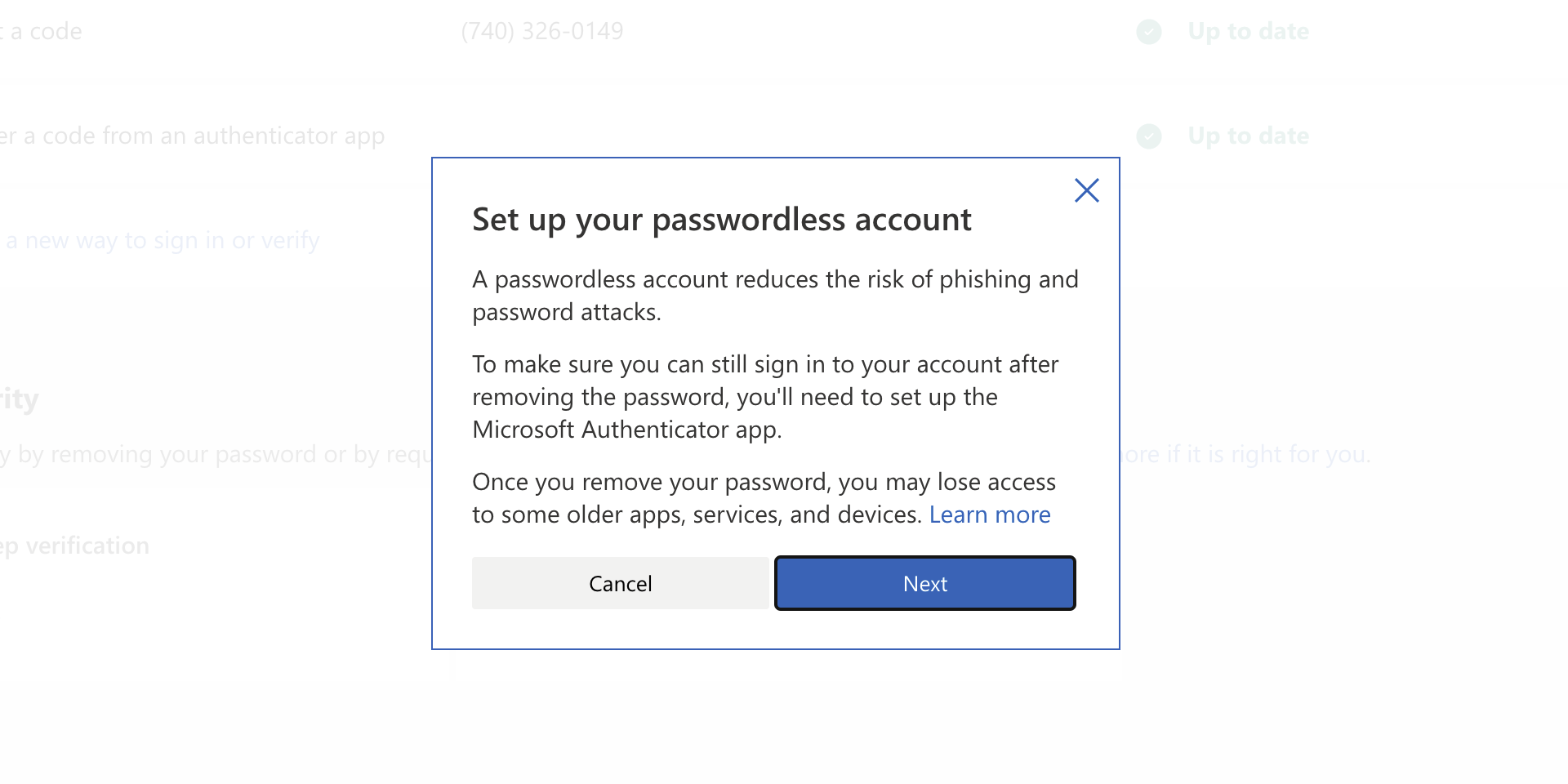 As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
