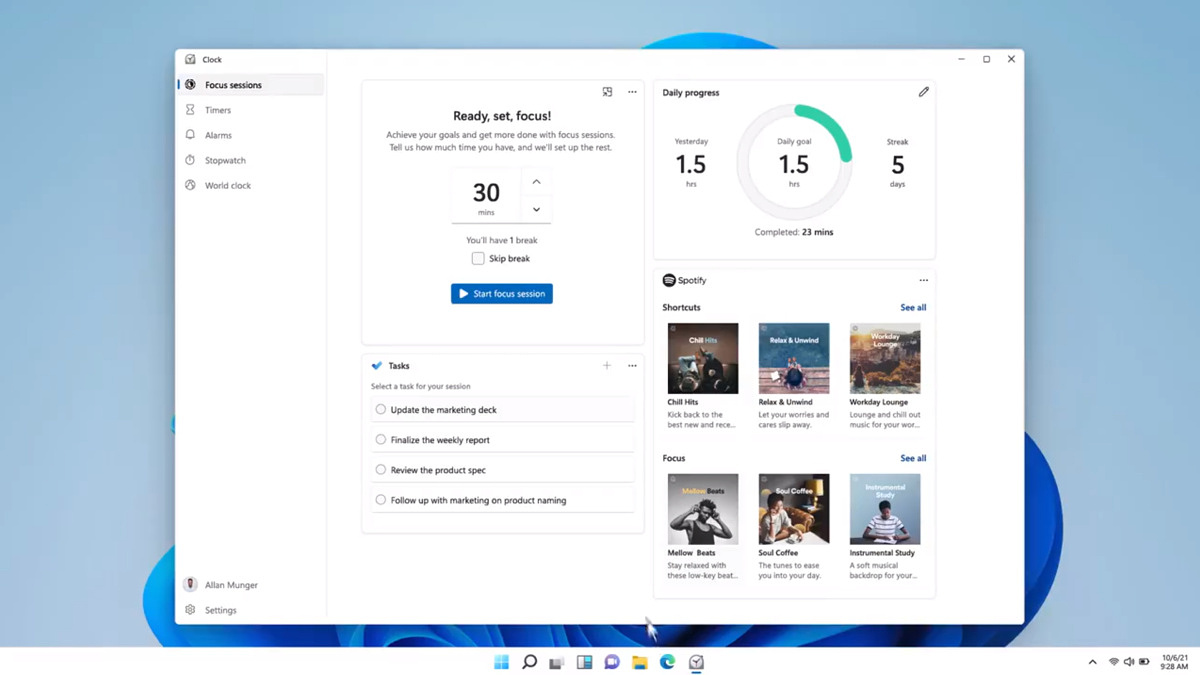
 Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
Error code 0x8007007e occurs in Windows 8 or 8.1 when users attempt to, but fail to successfully use Windows Update. When this occurs, Windows 8 or 8.1 users will not be able to access updates or certain web pages. This error manifests itself via the following common symptoms:
 Error Causes
Error CausesError code 0x8007007e is usually caused by a malfunction within your system. This malfunction may be due to several issues such as malware on your device, or the accidental removal of a registry entry or system file.
To correct issues related to error code 0x8007007e in Windows 8.1, users may need to employ one or several manual repair methods. Users will not necessarily need technical skills to accomplish this task. However, if you are uncertain of your skills or you are unable to resolve the issue after completing the tasks below, consult a Windows repair technician or use an automated tool.
System File Checker (SFC) enables users to check their system for corrupt or missing system files. You will need to use Command Prompt. To access System File Checker on Windows 8 or 8.1, follow the instructions below.
Whether you run Windows 8 or 8.1 operating system on your computer, System File Checker will begin to find and repair missing or corrupted system files. If, however, you are unable to successfully complete the task via Command Prompt, repeat the steps above. You may also consider help from a professional or simply move to the next manual repair method listed below.
A Clean Boot will help users determine if error code 0x8007007e in Windows 8.1 is caused by a problem associated with startup programs. Problems may arise when there is conflict among programs that run in the background when users turn on their device. To run a clean boot, follow the steps below:
If the Clean Boot is successful, you will be able to successfully update your system without receiving error code 0x8007007e. However, if the error code reappears while you attempt to access updates or web pages, proceed to the next manual repair method below.
Since error code 0x8007007e in Windows 8 or 8.1 can be caused by issues related to malware, it’s important for users to check their system using a powerful antivirus or anti-malware software. If you do not have one on your system, you will need to download such software as soon as possible.
Once you have the software on your PC, run a scan to check if your computer has been infected. If malware is indeed on your device, remove it using the anti-malware tool.
Another effective manual repair method relates to System Restore. This tool enables Windows users to restore their computer to an earlier period of time in which the error code was not present. When done properly, it can effectively resolve error code 0x8007007e. Before running this tool, however, be sure you select a time in which all important files and programs are present so as not to lose them.
If you wish to always have at your disposal a utility tool to fix these Windows 8 and other related issues when they do arise, download and install a powerful automated tool.

 Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
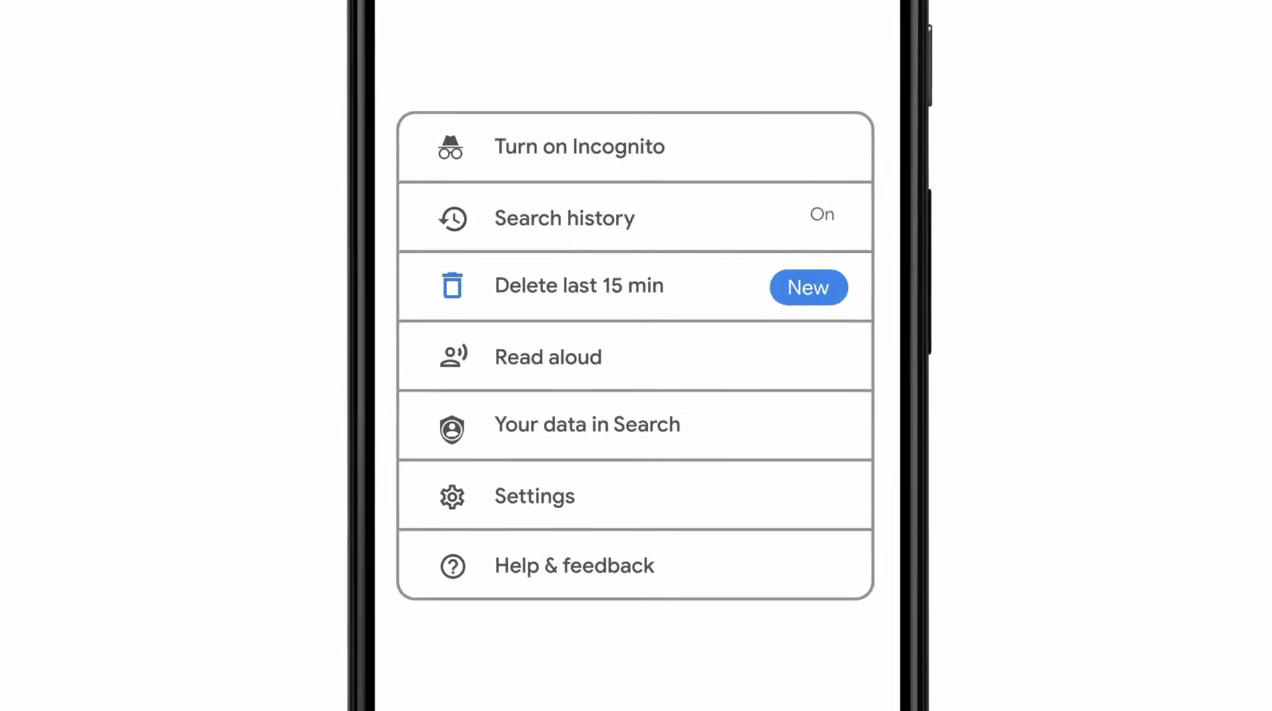 As previously announced by Google feature to quickly delete the last 15min of browsing history via one button is rolling out now.
For now, only Apple users will be available to use this feature but the Android update is scheduled for later this year, a strange move by Google but it is what it is.
For anyone who is unfamiliar with this feature, basically, Google wants a quick way to remove the last 15min of browsing history as a supposedly stated request to make deleting browsing history much easier.
Google came up with this idea so you can keep the previous history intact but remove just 15min time frame, no additional explanation was given on why 15 but I presume it is some round number that came up as the middle one with research, read telemetry info.
Using quick delete requires being signed into Search with a Google account. Users can access the option by simply tapping on the avatar icon to access the settings then choosing "Delete last 15 minutes."
As previously announced by Google feature to quickly delete the last 15min of browsing history via one button is rolling out now.
For now, only Apple users will be available to use this feature but the Android update is scheduled for later this year, a strange move by Google but it is what it is.
For anyone who is unfamiliar with this feature, basically, Google wants a quick way to remove the last 15min of browsing history as a supposedly stated request to make deleting browsing history much easier.
Google came up with this idea so you can keep the previous history intact but remove just 15min time frame, no additional explanation was given on why 15 but I presume it is some round number that came up as the middle one with research, read telemetry info.
Using quick delete requires being signed into Search with a Google account. Users can access the option by simply tapping on the avatar icon to access the settings then choosing "Delete last 15 minutes." chkdsk /f /r
In today's modern world many households have internet access, most of the connection nowadays is done via Wi-Fi or wireless but there is a high probability that you have also a few devices connected via cable. There are of course many disadvantages and advantages between cable connection and wireless connection.
The main advantages of a hard cable connection are of course faster speed and stability compared to Wi-Fi. But if we look into the cables themselves there is also a big difference between them. Not all cables are the same and quality as well as speed vary a lot between them. Choosing the right cable is essential in order to make a maximum of your internet and we have some great tips and explanations of what cables do so you can make the right choice and enjoy your full internet potential.
Cheap cables and expensive ones are not the same no matter what everyone tells you. The old proverb you get what you pay is true and more expensive cables will be made from better materials and will have a higher transfer rate.
Quality network cables are separated into different categories with proper markings and when buying one you should always look for these markings on the cables themselves, do not buy cables that do not have markings since they will often provide lower transfer rates or will not be shielded from outside influences resulting in packet drops and instability in a network.
Unless stated, these standards are typically rated at their quoted speeds for a run of around 100 meters (around 330 ft) and use a standard RJ-45 Ethernet connector. Each generation of cable is designed to be compatible with the generations that came before it, so it’s possible (for example) to use a Cat-6a cable with a router that only supports speeds of 1Gbps.
When purchasing higher quality cable you might not be able to choose if you have shielding or not since some standards like Cat-6a, Cat-7, and Cat-8 are always shielded. But if you do not have the need for these and you are satisfied with Cat-5e for example you can choose.
Shielded cables are a little more expensive but they will provide you with a coating that will eliminate interference from outside waves making cables more reliable. Of course, if the cable will go through a room that does not have many radio waves or some other interferences then buying a shielded cable is a waste of money.
Usually, there are two types of connector platings on connectors, silver, and gold, and people usually think that gold is much better but there are major differences between silver and gold platings and truth to be told there is no better one, both are different and should be considered depending on your need.
Silver plating will provide you with faster speed since its conductivity is larger than gold, but gold is slower on the oxidation front so its life span is longer. On the other hand, if your cables are always connecting and disconnecting gold will be first to be scrubbed off from the surface since the gold coating is much thinner.
Overall if you would only connect cable once and have slower internet than cable capacity gold is the way to go, in another case if you would use the cable as always connecting and switching and your internet plan is the same as cable transfer capacity you might want to go with silver one.
Network cables are made from copper, your standard conduction material but even here there are differences in quality and therefore the chance of pocket losses over it. More quality less loss and more stable connection and this will depend on the purity of copper that is used in the cable itself. More purity in copper, more stability, simple as that.
So as you can see, there are a lot of different things that will influence your pick of proper network cable but the overall best advice is to get one that will fit well into your needs and setup. pair it up with your router and your internet plan since just simply buying something that you can not use is really a waste of money.
 Since this requires registry tweak, please follow given solution step by step
Since this requires registry tweak, please follow given solution step by step
Social media is here to stay it seems, from Facebook, Instagram, Twitter, etc each site has its users and its rules. Companies, bloggers, public figures, and people, in general, are using them on a daily basis and some are posting cool ads, nice graphics, videos, and many more in order to gain followers or just to share something that they think is worth.
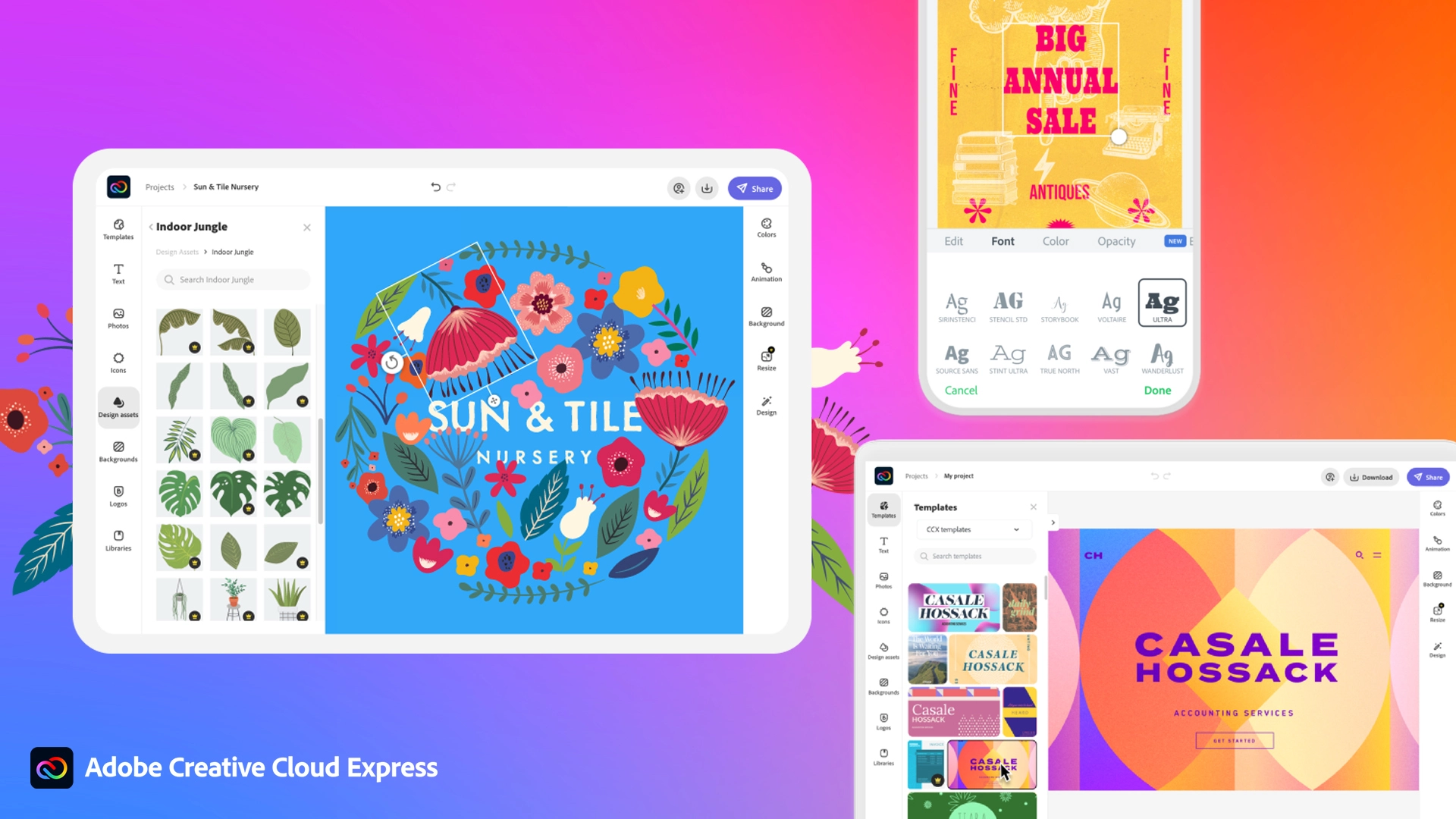
Making your post look good is somewhat essential if you plan on reaching a larger audience and Adobe's Express aims to fill that gap. It is the latest Adobe product that is purposely made for graphic and video creation for social media.
Adobe is well known in the world of professional design in all spheres like print, web, and motion, with this application, they want to take over social media design with Express. The direct competitor to Spark and canva, Express is filled with high-quality adobe templates and some great stuff found in photoshop like automatic background removal which gives it an edge over other applications.
The good thing about Express is that there is a completely free version and premium, like its competitors but with some benefits that clearly show that Adobe is determined to place its application on top of the game. The free plan includes:
For 10 USD per month of 100 USD prepaid annual fee, you get a premium plan that includes:
The application itself is incredibly easy to learn and to work with and literally, anyone can pick it up and start creating immediately. No matter are you just starting with social media or using Canva or Spark, give Express a go, make a free account and try it, I guarantee that you will find some features amazing, and its ease of use relaxing.
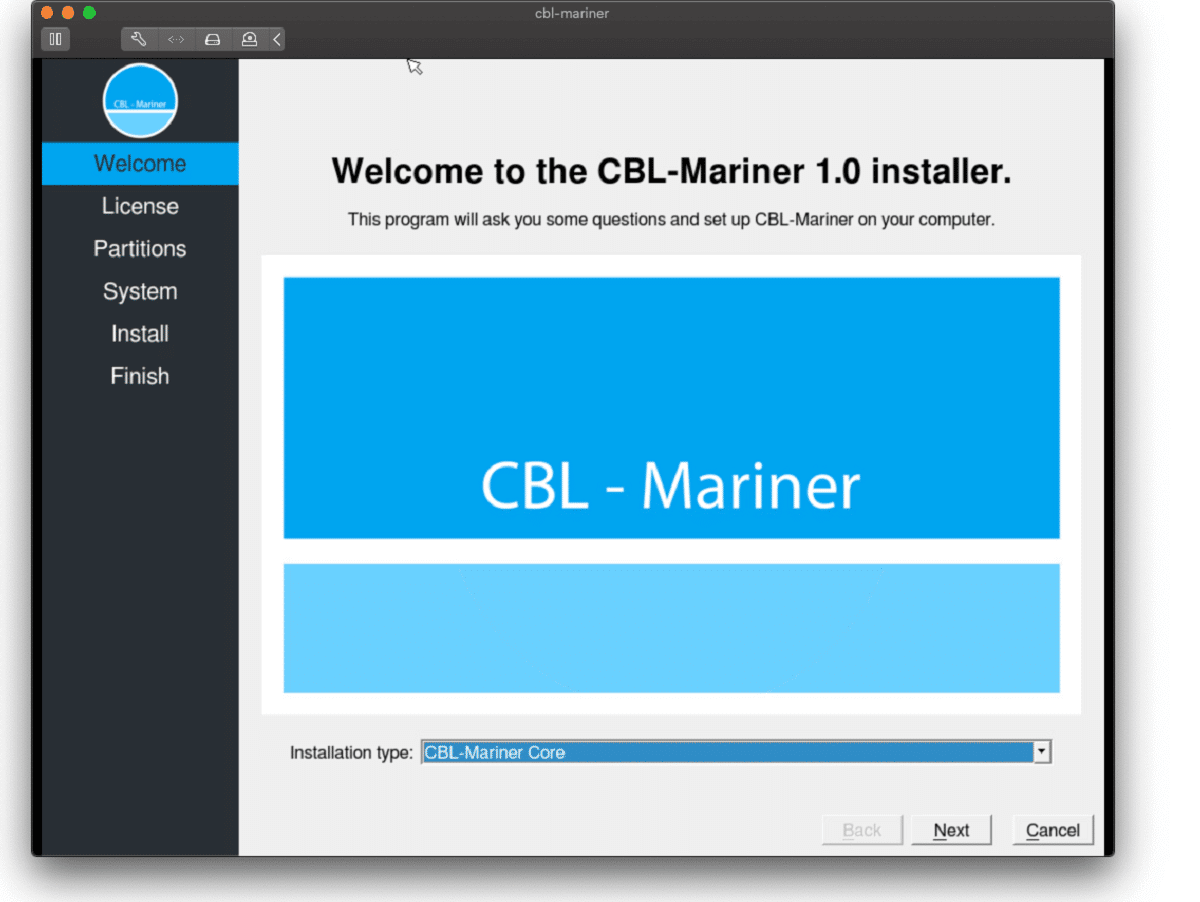 Well if anyone told me just a few years ago that I will see the day when Microsoft releases a new OS based on Linux I would be very amused, but that day has come. Mariner is the newest OS out of nowhere.
Microsoft’s new Linux Distro, dubbed Common Base Linux (CBL)-Mariner, isn’t the type of distro you’d want to install directly on any old machine. It’s primarily meant for cloud infrastructure and edge products. Specifically Microsoft’s Cloud and Edge products.
But if you are curious, it’s possible to run. Juan Manuel Rey, a Microsoft Senior Program Manager for Azure VMware, recently published a guide to ISO CBL-Mariner image. With that, you can easily get it up and running. And you can build CBL-Mariner on an Ubuntu 18.04 desktop. So you can try it out since it is free.
You can get it from here: https://github.com/microsoft/CBL-Mariner
It is obvious that Microsoft aims to set itself as a leader in enterprise server environments with this move and it is very likely that it may succeed or at least give a good shake to its competitors, mainly red hat and Suse which are two dominant distros in that field.
Many believe that they can win over by providing regular updates and package delivery via their already established system and that feature could be a turning point for some.
In any case, time will tell and we shall see.
Well if anyone told me just a few years ago that I will see the day when Microsoft releases a new OS based on Linux I would be very amused, but that day has come. Mariner is the newest OS out of nowhere.
Microsoft’s new Linux Distro, dubbed Common Base Linux (CBL)-Mariner, isn’t the type of distro you’d want to install directly on any old machine. It’s primarily meant for cloud infrastructure and edge products. Specifically Microsoft’s Cloud and Edge products.
But if you are curious, it’s possible to run. Juan Manuel Rey, a Microsoft Senior Program Manager for Azure VMware, recently published a guide to ISO CBL-Mariner image. With that, you can easily get it up and running. And you can build CBL-Mariner on an Ubuntu 18.04 desktop. So you can try it out since it is free.
You can get it from here: https://github.com/microsoft/CBL-Mariner
It is obvious that Microsoft aims to set itself as a leader in enterprise server environments with this move and it is very likely that it may succeed or at least give a good shake to its competitors, mainly red hat and Suse which are two dominant distros in that field.
Many believe that they can win over by providing regular updates and package delivery via their already established system and that feature could be a turning point for some.
In any case, time will tell and we shall see.