Error Code 0xc00007b – What is it?
Error code 0xc00007b usually manifests itself via the inability to start an application properly. It can occur when users attempt to run a game or other programs on their computer. In such a case, the application will not start and a message box will pop up stating that error code 0xc00007b has occurred. The error code is likely to occur when users attempt to run a program in the incorrect or inappropriate bit. For instance, if you try to load a 32bit location with a 64bit location.
Solution
 Error Causes
Error Causes
Error code 0xc00007b affects various versions of the Windows operating system, including Windows 7, 8, 8.1, and Windows 10. In the case of error code 0xc00007b for Windows 10, the error may be caused by issues related to software you’ve installed on your machine. This may cause software conflict resulting in the need to install programs like DirectX. Left unchecked, error code 0xc00007b could incite other error codes in Windows 10, such as error code 0xc004f034.
Further Information and Manual Repair
To repair error code 0xc00007b for Windows 10 devices, users will need to implement at least one manual repair procedure. Manual repair methods are effective in combating these issues as they can address the issues causing the error in the first place, thus fixing the problem.
The manual repair procedures for fixing error code 0xc00007b are very straightforward and can be implemented with little technical knowledge. However, you may need to contact a Windows repair technician if you have difficulty fixing the error code after completing the manual repair methods listed below.
Method One: Install Microsoft DirectX
Microsoft DirectX is an application usually included in the Microsoft operating system. It enables users to access high-speed gaming and multimedia on their PC. The latest version of this Windows technology is available on Microsoft’s official site.
Visit the Microsoft website and search for DirectX End-User Runtime Web Installer. Once you have located the latest version of the program, select the preferred language you would like DirectX to run in, and then click download. Run the program, then be sure to reboot your computer.
Note that this solution should only be applied if you are having issues running or displaying a gaming or multimedia application. Once you’ve correctly installed the latest version of DirectX, it should be able to fix underlying issues that may be causing error code 0xc00007b to occur. If you are still unable to run applications after completing this manual repair procedure, however, you will need to apply another method to fix error code 0xc00007b for Windows 10.
Method Two: Install Latest Version of .NET Framework
.NET Framework, a framework developed by Microsoft, provides solutions for users who may be having problems with applications. To download the latest version of the .NET framework, follow the steps listed below.
- Step one: Open your favorite web browser
- Step two: Enter www.microsoft.com/net
- Step three: Click Downloads
- Step four: Select the latest version of the .NET Framework by clicking the framework at the top of the list. (Currently, the latest version is .NET Framework 4.6.2.)
- Step five: Select preferred language, then download
- Step six: Run software.
To ensure you successfully download the latest version of the .NET Framework, verify your computer is properly connected to the Internet while downloading the software. Also, follow the instructions provided on the Microsoft website.
After completing the download process, reboot your computer then check if you have successfully resolved error code 0xc00007b for Windows 10. If this manual repair method is successful, you will be able to access your gaming and multimedia programs. Otherwise, the error code message box will reoccur, stating that the application error code is present on your device. Apply the next manual repair procedure to correct the error code if this reoccurs.
Method Three: Install Windows Updates
In certain instances, application error codes like error code 0xc00007b affect PC users who fail to install the most current Windows updates on their device. That is why it’s important to check your system and ensure you have installed all the latest updates.
The updates, if any are available, will automatically be installed on your PC once you access Windows Update in Settings. Reboot your computer then check if you are able to run programs that previously would not open due to error code 0xc00007b. If problems persist resulting in the reoccurrence of the error code, reinstall the applications you are unable to open or get help from a Windows repair technician.
Method Four: Download an Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 8 and other related issues when they do arise, download and install a powerful automated tool.

 A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
 On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update.
On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update. It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
 The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers).
The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers). It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
 Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.
Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.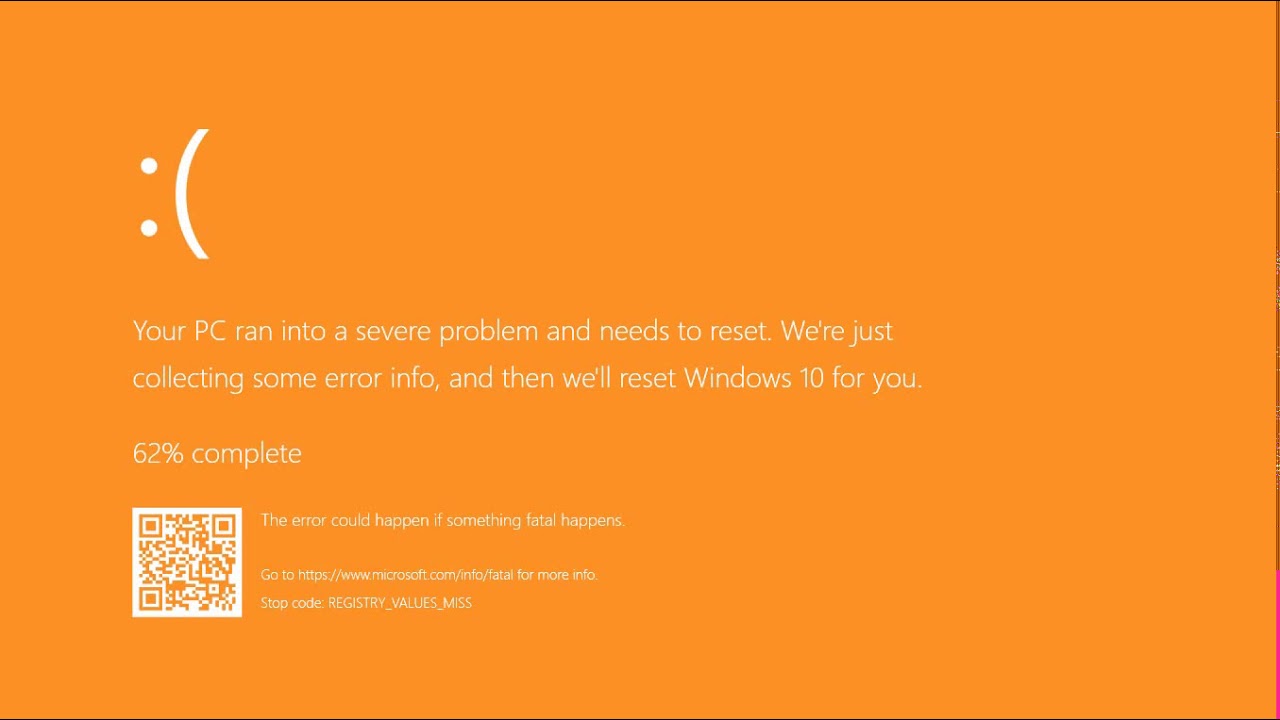 The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
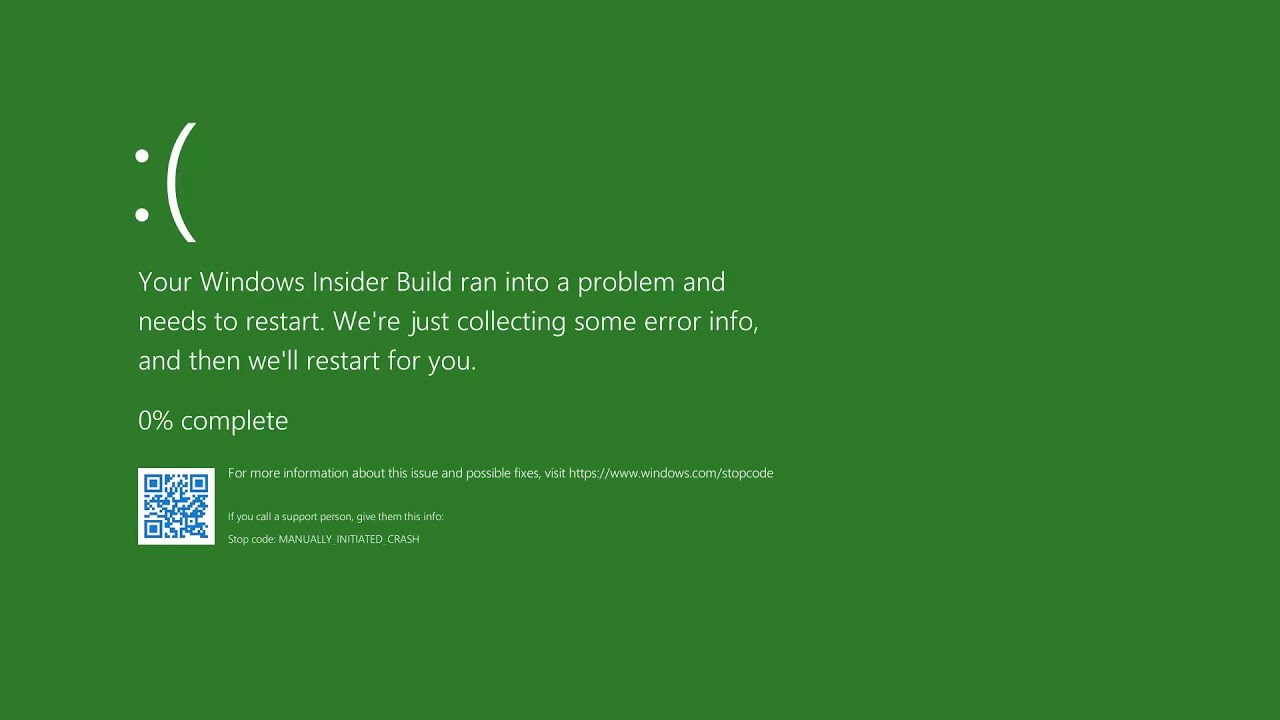 The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10.
The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10. The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware.
The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware. 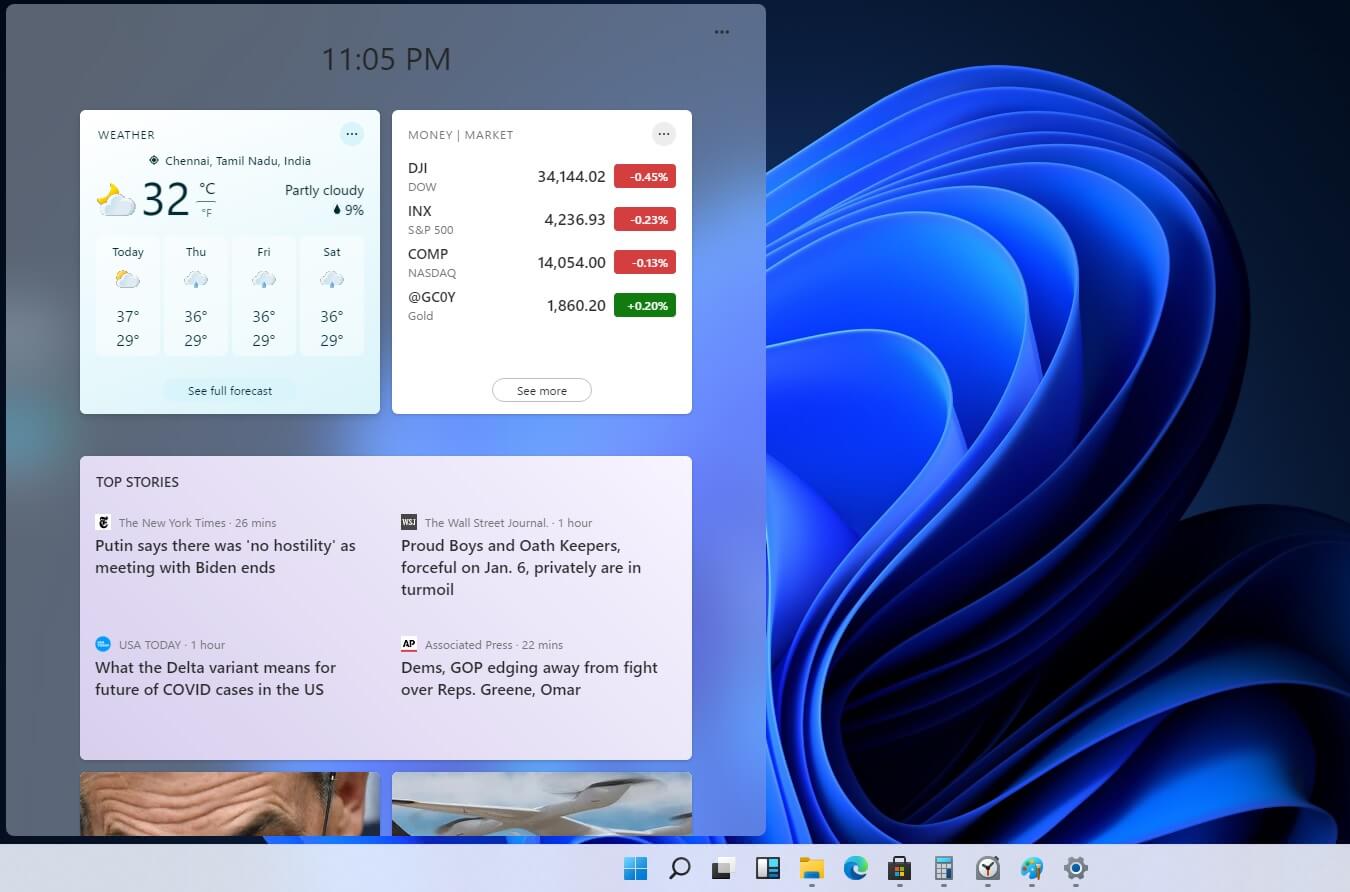 Originally Microsoft has imagined its widgets menu as Microsoft-only widgets but it seems that they have changed their mind.
Due to the latest leak, it seems that Microsoft will open the widgets menu to 3rd party developers as well but at launch, it will be only official widgets. It was hinted that later widgets menu will be open to developers who want to bring their own stuff into it.
Distribution, date, and technology that will need to be used in order to create your widget have not been discussed nor leaked at a given time but in some way, I am very glad that at least some customization will be in Windows 11.
It is funny and amusing how some things that were in Windows Vista are getting back like glass design, round corners, and widgets. Let’s just hope Windows 11 will be a better Windows than Vista was.
Originally Microsoft has imagined its widgets menu as Microsoft-only widgets but it seems that they have changed their mind.
Due to the latest leak, it seems that Microsoft will open the widgets menu to 3rd party developers as well but at launch, it will be only official widgets. It was hinted that later widgets menu will be open to developers who want to bring their own stuff into it.
Distribution, date, and technology that will need to be used in order to create your widget have not been discussed nor leaked at a given time but in some way, I am very glad that at least some customization will be in Windows 11.
It is funny and amusing how some things that were in Windows Vista are getting back like glass design, round corners, and widgets. Let’s just hope Windows 11 will be a better Windows than Vista was. 