Hello and welcome to our software series review. Weel this time we could say this is more of a service review since the application we are going through today is online and you can use it freely without ever needing to install it.
When we choose software that we are going to review and recommend we really try to recommend something that is worth your time and money, Cartoonize fits in both categories in my opinion.
First of all basic plan of this graphic software is completely free and as mentioned it is working online, also as one more feature basic plan does not even require you to have an account of any kind, all you need to do is go to the website of the application and you can start using it right away. There is also paid plan for extra features if you need them billed monthly or annually.
Features
First things first, this is not Photoshop or GIMP and it does not aim nor want to be. This is something else, directed and pointed at the different types of users. This application is aimed at people that want to make some quick graphics and post them on social media and it does that very well. Even without knowledge to use graphic software this one is so well designed and straightforward that even a complete newcomer can do something right away.
So as the application that wants to be used by people that want to place some cool pictures or ads on their social media what it offers. For starters simplicity and ease of use, every option that you can use is on the left side of the screen nicely packed into the vertical toolbox. Inside the toolbox, you have access to various tools, effects, and filters that you can apply to your image.
Tools explained
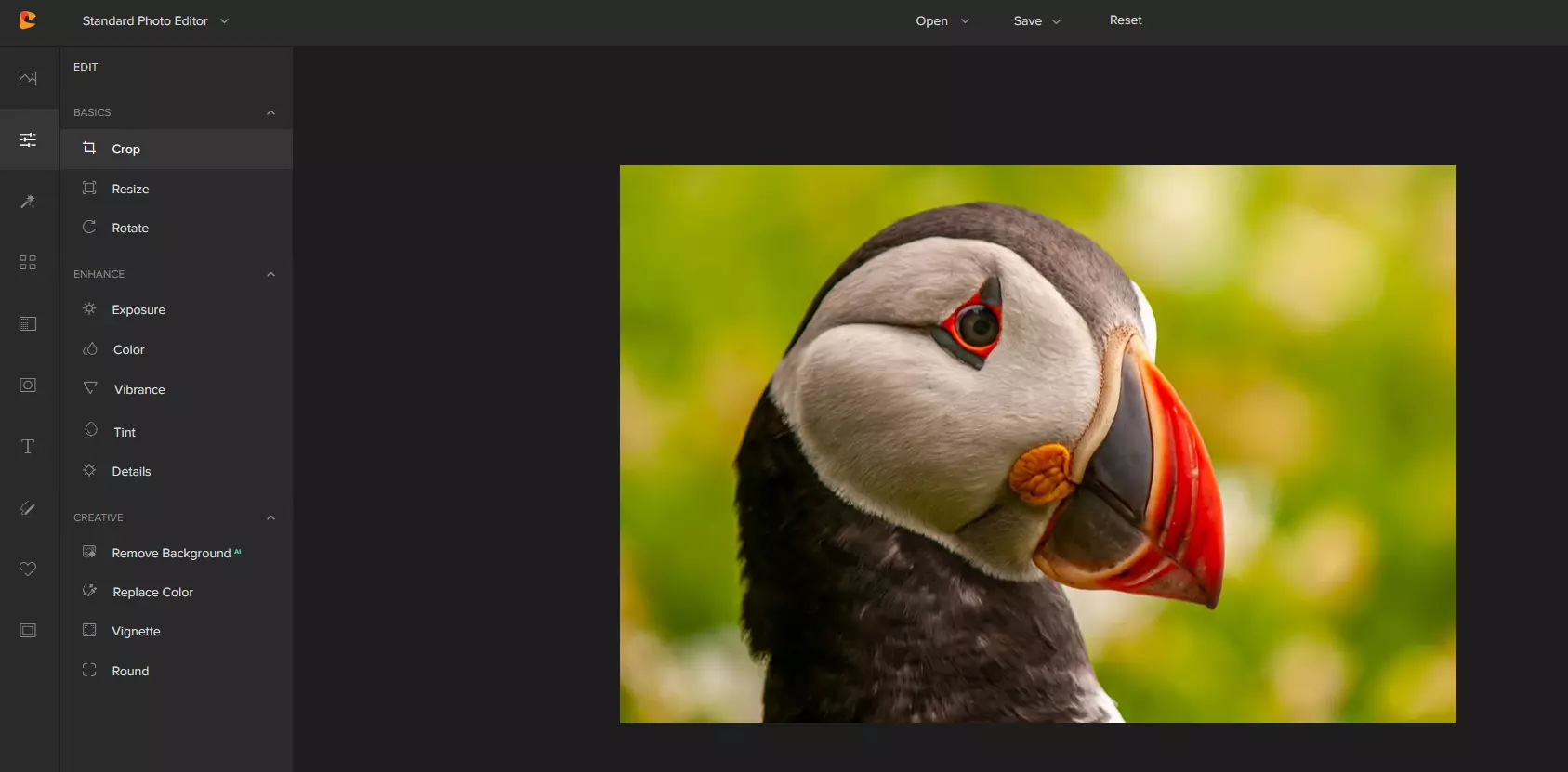
Image manager
The first section on the tool panel is the image manager, here you can upload your images, delete them, search stock images, and so forth. nothing more to say about this one as it is only a basic file manager.
Edit
In this tool panel, there are a lot of basic settings for your image manipulations divided into 3 sections: Basics, Enhance, and Creative. In the basic section, you can crop, resize and rotate your image. Enhance panel will let you set exposure, color, vibrance, tint, and details (sharpen). Finally, the Creative part will let you remove the background with AI in a single click, replace colors in the image, and add a vignette and round image.
Effects
In the effects panel, you will be given 4 options to choose from Cartoonizer, Digital art, Sketcher, and painting. Each option once clicked will open another set of options tied to chosen preset where you will be able to choose a different style from chosen template. Once you click on the desired template it will be applied to your image and in the upright corner, you will have edit options to tweak it to your liking. You can play around as much as you want because only once you click on the apply button, the effect will be applied to your image.
Filters
Same as in the effects tool panel here you will also get a series of different filters that you can apply to your image. As in the previous tool once clicked on the chosen filter, you will be given options for its variations and details edits. How there is really plenty of filters options and combined with its own presets I will not focus on explaining what each one is doing since picture thumbnails are pretty accurate and just one look at them will explain to you everything you need to know.
Overlays
In the overlays panel, you can as the name says overlay different kinds of effects on your image. You can add snow, fog, sun flares rain, and many more. Presets work identically to previous effects and filters.
Masks
If you want to place your image in a certain shape or in-text this is the section for you. You will be presented with sections as custom text, shapes, brushes, floral, animals, and patterns. Each section will once again lead to plenty of variations on the chosen subject where you can pick one that you like the most and tweak its options.
Text
As the name suggests, this section is to add text to your picture or design. If you are making some cool ad for Facebook, Instagram, or other social media I believe that you will spend most of your time in this section adding text and tweaking it so it looks best. You have all the tools that you will need to make a catchy title or smaller block of text and you can add multiple texts to your picture tweaking their own visual appearance, the font used, color, and some effects like a drop shadow.
Draw
In the draw section, you will be able to freely draw whatever you like with your mouse or pen if you have one. you have basic options for a brush and eraser so you can erase stuff. Pretty basic tool but it gives a nice touch to underline something, circle it, etc.
Graphics
This panel will let you place various already made graphic assets into a picture. You have hearts, hats, glasses, etc. There really are tons of premade graphics along with thematic ones like new year, st. Patric day and more.
Frames
As the name suggests this section will place a frame of your choice around your picture. You can choose the style of frame, position, color, and many more. There are various styles and each style has its own options.
Conclusion
Cartoonize is a great online application that will let you quickly and easily do cool and nice image edits. As mentioned you can also add various effects, text, and graphics and use this app to make some quick and nice ads for social media. You have the option to publish to your social media right from the app in the save dialog but you can also of course download your image or design to your local computer.
Please note that for this review we used the pro, paid version so all of the features were unlocked. We wanted to give you a full overview of the full potential of the app. In my opinion, the small monthly fee that they charge is well worth it when you see all things that you can do with it.
Go to the cartoonize website and check it out, basic option is completely free and it does not even require making an account. Have fun, be creative and take care, I hope to see you again tomorrow.