MyFunCards Toolbar is a browser hijacking extension for Google Chrome made by Mindspark Interactive. This extension installs a toolbar for your browser, changes your default search engine, and lowers the general performance of your browser. This extension has access to your personal information, injects your search results with potentially dangerous ads, and possibly breaks some of the browser functions. Since this extension injects its code into too many files and has access to all your browser details, upon removing it you will lose all your browser settings, themes, and login information. MyFunCards is considered a potentially unwanted application, and as a result, is flagged for optional removal by many anti-malware programs.
About Browser Hijackers
Browser hijacking is amongst the web’s constant problems that target internet browsers. It is a type of malware program that alters your web browser’s settings so that you are redirected to internet sites or pages that you had no intention of checking out. There are many reasons why you may have a browser hijack; however commercial, marketing, and advertising are the main reasons for their creation. It redirects you to the sponsored sites and injects advertisements on the browser that assists its developer to generate revenue. Even though it may seem naive, these tools were created by vicious people who always look to take advantage of you, so that they can easily earn money from your naivety and distraction. They not only mess up your browsers, but browser hijackers can also modify the computer registry to make your PC susceptible to various other types of attacks.
Key symptoms that an internet browser has been hijacked
When your web browser is hijacked, the following might happen:
1. the home page of the browser is changed all of a sudden
2. your internet browser is constantly being redirected to adult sites
3. the default search engine has been changed and the web browser security settings have been cut down without your knowledge
4. unwanted new toolbars are added to your browser
5. your browser will display endless pop-up ads
6. your internet browser has become unstable or starts running slowly
7. You cannot access certain websites, in particular anti-malware sites.
How browser hijacker finds its way onto your computer system
A browser hijacker could be installed on your PC if you visit an infected site, click an e-mail attachment, or download something from a file-sharing website. They could also be deployed via the installation of a web browser toolbar, add-on, or extension. A browser hijacker can be installed as a part of freeware, demoware, shareware, and fake programs. Common examples of browser hijackers include Conduit, CoolWebSearch, Coupon Server, OneWebSearch, RocketTab, Snap.do, Delta Search, and Searchult.com.
Browser hijacking can cause severe privacy issues and even identity theft, disrupt your web browsing experience by taking control of outgoing traffic, significantly slows down your personal computer by depleting lots of resources and result in system instability as well.
Browser hijacker removal methods
Certain hijackers can be removed by just uninstalling the corresponding freeware or add-ons through the Add or Remove Programs in the Windows control panel. Having said that, the majority of hijackers are quite tenacious and require specialized applications to eradicate them. Moreover, browser hijackers can modify the Computer registry therefore it can be quite hard to repair manually, especially when you’re not a tech-savvy individual.
Malware Blocking Internet And All Antivirus Software? Do This!
All malware is inherently dangerous, but certain kinds of malicious software do more damage to your computer than others. Some malware goes to great lengths to prevent you from installing anything on your computer system, especially anti-virus software programs. If you’re reading this article, you may have got affected by malware that prevents you from downloading a security program such as Safebytes Antimalware on your PC. There are a few options you can try to get around with this particular obstacle.
Install the anti-virus in Safe Mode
If any malware is set to load immediately when Windows starts, stepping into Safe Mode could block the attempt. Just bare minimum required applications and services are loaded when you start your personal computer in Safe Mode. You will have to do the following to eliminate malware in Safe mode.
1) After switching on the computer, press the F8 key before the Windows splash screen begins to load. This should bring up the Advanced Boot Options menu.
2) Use the arrow keys to select Safe Mode with Networking and hit ENTER.
3) As soon as this mode loads, you will have an internet connection. Now, make use of your browser normally and go to https://safebytes.com/products/anti-malware/ to download and install Safebytes Anti-Malware.
4) As soon as the software is installed, allow the scan run to eliminate viruses and other threats automatically.
Use an alternate web browser to download security application
Malicious program code might exploit vulnerabilities on a specific web browser and block access to all antivirus software websites. If you are not able to download the anti-malware application using Internet Explorer, it means malware could be targeting IE’s vulnerabilities. Here, you need to switch over to a different web browser like Firefox or Chrome to download Safebytes software.
Make a bootable USB antivirus drive
Another option is to create a portable antivirus program on your USB stick. Adopt these measures to employ a USB flash drive to clean your corrupted computer system.
1) Download Safebytes Anti-Malware or MS Windows Defender Offline onto a clean computer system.
2) Plug the Flash drive into the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded software, with an .exe file format.
4) Select the USB flash drive as the location for saving the software file. Follow the on-screen instructions to complete the installation.
5) Now, plug the USB drive into the corrupted system.
6) Run the Safebytes Anti-malware directly from the thumb drive by double-clicking the icon.
7) Run Full System Scan to detect and get rid of all kinds of malware.
SafeBytes Anti-Malware: Lightweight Malware Protection for Windows Computer
Nowadays, anti-malware software can protect your computer from various forms of online threats. But exactly how to select the best one among numerous malware protection application that is available in the market? You may be aware, there are lots of anti-malware companies and tools for you to consider. Some of them are great and some are scamware applications that pretend as authentic anti-malware software waiting around to wreak havoc on your computer. While looking for an anti-malware program, pick one which gives dependable, efficient, and total protection against all known computer viruses and malware. One of the strongly recommended software is SafeBytes Anti-Malware. SafeBytes has a really good history of excellent service, and customers are happy with it.
SafeBytes anti-malware is a powerful, very effective protection application created to assist users of all levels of IT literacy in finding and removing harmful threats from their PC. Using its outstanding protection system, this utility will easily detect and remove most of the security threats, which include viruses, adware, browser hijackers, PUPs, trojans, worms, and ransomware.
SafeBytes has great features when compared with various other anti-malware programs. Below are a few of the best ones:
Active Protection: SafeBytes provides a completely hands-free live protection that is set to monitor, prevent and destroy all computer threats at its very first encounter. They are very effective in screening and eliminating different threats because they’re continuously revised with new updates and alerts.
Anti-Malware Protection: With its enhanced and sophisticated algorithm, this malware removal tool can identify and eliminate the malware threats hiding in your PC effectively.
SuperSpeed Scanning: This application has one of the fastest and most effective virus scanning engines in the industry. The scans are extremely accurate and take a short amount of time to complete.
Safe Web Browsing: Safebytes allots all websites with a unique safety ranking that helps you to have an idea of whether the website you’re about to visit is safe to view or known to be a phishing site.
Lightweight: SafeBytes gives you total protection from internet threats at a fraction of the CPU load because of its advanced detection engine and algorithms.
24/7 Premium Support: Skilled technicians are at your disposal 24/7! They will quickly resolve any technical issues you might be encountering with your security software.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove MyFunCardsToolbar without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by MyFunCardsToolbar
Files:
C:Program FilesFunWebProductsInstallr.binF3EZSETP.DLL
C:Program FilesFunWebProductsInstallr.binF3EZSETP.DL_
C:Program Files
C:Program FilesFunWebProducts
C:PROGRA~1FUNWEB~1Installr.binF3EZSETP.DL_
C:Program FilesFunWebProductsInstallr.binF3EZSETP.DLL
Registry:
HKEY_LOCAL_MACHINESoftwareFunWebProductsInstaller
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersion
HKEY_LOCAL_MACHINESoftware
HKEY_LOCAL_MACHINESoftwareMicrosoft
HKEY_LOCAL_MACHINESoftwareMicrosoftWindows
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersion
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExt
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExtPreApproved
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExtPreApproved1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CURRENT_USERSoftware
HKEY_CURRENT_USERSoftwareMicrosoft
HKEY_CURRENT_USERSoftwareMicrosoftWindows
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersion
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExt
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExtSettings
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExtSettings1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start.1
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start.1CLSID
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start
HKEY_CLASSES_ROOTFunWebProductsInstaller.StartCLSID
HKEY_CLASSES_ROOTFunWebProductsInstaller.StartCurVer
HKEY_CLASSES_ROOTCLSID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBProgID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBVersionIndependentProgID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBProgrammable
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBInprocServer32
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBControl
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBMiscStatus
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBMiscStatus
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBTypeLib
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBVersion
HKEY_LOCAL_MACHINESOFTWAREMicrosoftOLEAUT
HKEY_CLASSES_ROOTTypeLib
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0FLAGS
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0C:Program FilesFunWebProductsInstallr.binF3EZSETP.DLL
C:Program FilesFunWebProductsInstallr.binF3EZSETP.DL_
C:Program Files
C:Program FilesFunWebProducts
C:PROGRA~1FUNWEB~1Installr.binF3EZSETP.DL_
C:Program FilesFunWebProductsInstallr.binF3EZSETP.DLL
HKEY_LOCAL_MACHINESoftwareFunWebProductsInstaller
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersion
HKEY_LOCAL_MACHINESoftware
HKEY_LOCAL_MACHINESoftwareMicrosoft
HKEY_LOCAL_MACHINESoftwareMicrosoftWindows
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersion
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExt
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExtPreApproved
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExtPreApproved1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CURRENT_USERSoftware
HKEY_CURRENT_USERSoftwareMicrosoft
HKEY_CURRENT_USERSoftwareMicrosoftWindows
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersion
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExt
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExtSettings
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExtSettings1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start.1
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start.1CLSID
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start
HKEY_CLASSES_ROOTFunWebProductsInstaller.StartCLSID
HKEY_CLASSES_ROOTFunWebProductsInstaller.StartCurVer
HKEY_CLASSES_ROOTCLSID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBProgID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBVersionIndependentProgID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBProgrammable
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBInprocServer32
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBControl
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBMiscStatus
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBMiscStatus
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBTypeLib
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBVersion
HKEY_LOCAL_MACHINESOFTWAREMicrosoftOLEAUT
HKEY_CLASSES_ROOTTypeLib
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0FLAGS
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0%#MANIFEST#%
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0%#MANIFEST#%win32
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0HELPDIR
HKEY_CLASSES_ROOTInterface
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid32
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBTypeLib
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid32
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBTypeLib
HKLMSOFTWAREMyFunCards_5m
HKLMSOFTWAREClassesMyFunCards_5m.SkinLauncher
HKLMSOFTWAREClassesMyFunCards_5m.SettingsPlugin
HKLMSOFTWAREClassesMyFunCards_5m.ScriptButton
HKLMSOFTWAREClassesMyFunCards_5m.Radio
HKLMSOFTWAREClassesMyFunCards_5m.PseudoTransparentPlugin
HKLMSOFTWAREClassesMyFunCards_5m.MultipleButton
HKLMSOFTWAREClassesMyFunCards_5m.HTMLPanel
HKLMSOFTWAREClassesMyFunCards_5m.HTMLMenu
HKLMSOFTWAREClassesMyFunCards_5m.FeedManager
HKLMSOFTWAREClassesMyFunCards_5m.DynamicBarButton
HKLMSOFTWAREClassesCLSID4bdd2be-51e9-4031-a7a7-b882b3abea12
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0C:Program FilesFunWebProductsInstallr.binF3EZSETP.DLL
HKEY_LOCAL_MACHINESoftwareFunWebProductsInstaller
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersion
HKEY_LOCAL_MACHINESoftware
HKEY_LOCAL_MACHINESoftwareMicrosoft
HKEY_LOCAL_MACHINESoftwareMicrosoftWindows
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersion
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExt
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExtPreApproved
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExtPreApproved1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CURRENT_USERSoftware
HKEY_CURRENT_USERSoftwareMicrosoft
HKEY_CURRENT_USERSoftwareMicrosoftWindows
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersion
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExt
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExtSettings
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExtSettings1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start.1
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start.1CLSID
HKEY_CLASSES_ROOTFunWebProductsInstaller.Start
HKEY_CLASSES_ROOTFunWebProductsInstaller.StartCLSID
HKEY_CLASSES_ROOTFunWebProductsInstaller.StartCurVer
HKEY_CLASSES_ROOTCLSID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBProgID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBVersionIndependentProgID
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBProgrammable
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBInprocServer32
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBControl
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBMiscStatus
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBMiscStatus
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBTypeLib
HKEY_CLASSES_ROOTCLSID1D4DB7D2-6EC9-47a3-BD87-1E41684E07BBVersion
HKEY_LOCAL_MACHINESOFTWAREMicrosoftOLEAUT
HKEY_CLASSES_ROOTTypeLib
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0FLAGS
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0%#MANIFEST#%
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0%#MANIFEST#%win32
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0HELPDIR
HKEY_CLASSES_ROOTInterface
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid32
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBTypeLib
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid32
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBTypeLib
HKLMSOFTWAREMyFunCards_5m
HKLMSOFTWAREClassesMyFunCards_5m.SkinLauncher
HKLMSOFTWAREClassesMyFunCards_5m.SettingsPlugin
HKLMSOFTWAREClassesMyFunCards_5m.ScriptButton
HKLMSOFTWAREClassesMyFunCards_5m.Radio
HKLMSOFTWAREClassesMyFunCards_5m.PseudoTransparentPlugin
HKLMSOFTWAREClassesMyFunCards_5m.MultipleButton
HKLMSOFTWAREClassesMyFunCards_5m.HTMLPanel
HKLMSOFTWAREClassesMyFunCards_5m.HTMLMenu
HKLMSOFTWAREClassesMyFunCards_5m.FeedManager
HKLMSOFTWAREClassesMyFunCards_5m.DynamicBarButton
HKLMSOFTWAREClassesCLSID4bdd2be-51e9-4031-a7a7-b882b3abea12win32
HKEY_CLASSES_ROOTTypeLib1D4DB7D0-6EC9-47A3-BD87-1E41684E07BB.0HELPDIR
HKEY_CLASSES_ROOTInterface
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid32
HKEY_CLASSES_ROOTInterface1D4DB7D1-6EC9-47A3-BD87-1E41684E07BBTypeLib
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BB
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBProxyStubClsid32
HKEY_CLASSES_ROOTInterface1D4DB7D3-6EC9-47A3-BD87-1E41684E07BBTypeLib
HKLMSOFTWAREMyFunCards_5m
HKLMSOFTWAREClassesMyFunCards_5m.SkinLauncher
HKLMSOFTWAREClassesMyFunCards_5m.SettingsPlugin
HKLMSOFTWAREClassesMyFunCards_5m.ScriptButton
HKLMSOFTWAREClassesMyFunCards_5m.Radio
HKLMSOFTWAREClassesMyFunCards_5m.PseudoTransparentPlugin
HKLMSOFTWAREClassesMyFunCards_5m.MultipleButton
HKLMSOFTWAREClassesMyFunCards_5m.HTMLPanel
HKLMSOFTWAREClassesMyFunCards_5m.HTMLMenu
HKLMSOFTWAREClassesMyFunCards_5m.FeedManager
HKLMSOFTWAREClassesMyFunCards_5m.DynamicBarButton
HKLMSOFTWAREClassesCLSID4bdd2be-51e9-4031-a7a7-b882b3abea12


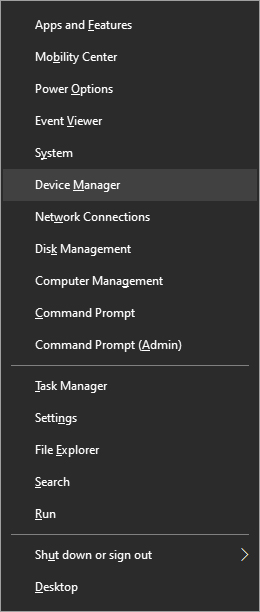
 In the menu choose device manager and click on it.
In the menu choose device manager and click on it.
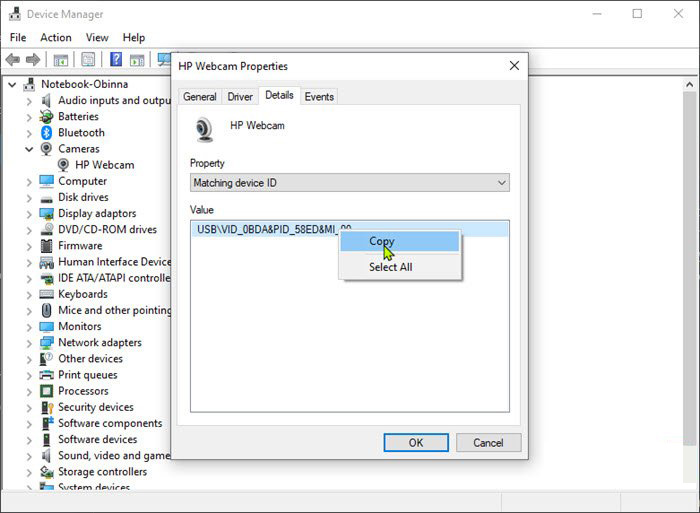
 When the device manager opens, expand the Imaging devices or Cameras section.
Right-click Integrated Camera or the primary webcam, and click Properties.
Go to the Details tab.
Under the Property section, click to select Matching device ID from the drop-down.
Right-click the value and select Copy
When the device manager opens, expand the Imaging devices or Cameras section.
Right-click Integrated Camera or the primary webcam, and click Properties.
Go to the Details tab.
Under the Property section, click to select Matching device ID from the drop-down.
Right-click the value and select Copy
 The next step is to download and install
The next step is to download and install 
