ActiveX Controls are plugins you may constantly come across when working with Internet Explorer. An illustration of these kinds of control is the MICROSOFT IE Flash Player. They frequently result into significant problems for the Computer, yet they're vital for IE to operate correctly.
You shouldn't ever overlook that after you install Active Controls in your Personal Computer, you effectively provide them with access to other areas of your PC. The ActiveX Controls not only tracks your search routines, but in addition puts malicious software, which might possibly be hazardous to your Computer.
Solution
 Error Causes
Error Causes
ActiveX Controls make your Internet Explorer work as required and are usually great and beneficial to your own Computer. Yet, they can function as a source of problems because of the following factors.
- You should stop installing ActiveX Controls from Un Trustworthy Resources
In the event they are installed by you from un trustworthy resources new threats are likely introduced by ActiveX Controls to your PC. One of the more regular types of ActiveX Controls worth necessary for installation is Flash Player. Yet, never be in a hurry to install these Controls from resources that you don't trust.
- Limit The Number of ActiveX Controls You Install on your PC
Prevent installing java/oracle ActiveX controls, because of its weak security measures which could make your Personal Computer and any additional information there in, open to attacks.
Limit to the variety of ActiveX Controls that you install on your PC as these could increase the vulnerability canvas on your computer.
Further Information and Manual Repair
You can manually fix any malfunction that springs up from
ActiveX Controls. Yet, more than mending the harm, produce the setting that ensures you never have troubles from them to start with. Just how do you do that?
a) Stop installing or downloading ActiveX Controls from Un Trustworthy Sources
This has been mentioned above, but it's worth repeating because it's the most common reason behind ActiveX Controls malfunctions. You might anticipate that for this kind of obvious reason for ActiveX Controls malfunctions, PC consumers would be extra cautious, however that is never true.
b) Limit ActiveX Controls Softwares
You can restrict ActiveX controls from running automatically on your PC. To limit them, head to Tools in Internet Explorer, and choose Internet Options. Proceed to the Security tab, and select Customs level
Browse completely down before you get to the area designated "ActiveX". Subsequently, mark "Prompt" under every choice that you encounter. But don't mark the choice indicated "Run ActiveX Controls and Plug-Ins", together with, "Script ActiveX Controls Marked Safe for Scripting".
By performing the measures emphasized above, you happen to be in substance stating that, you will not permit any installation of ActiveX Controls, without express authorization by you.
In this manner, you have better control over different forms of ActiveX Controls you permit to be installed, therefore reducing potential threats to your PC.


 Removing options all together
Removing options all together 1. File-infecting Virus
1. File-infecting Virus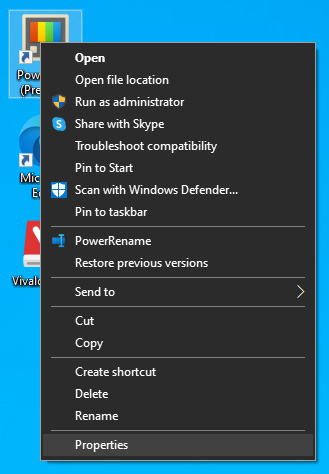 The application settings screen will open, in upper tabs locate Compatibility and left-click on it.
The application settings screen will open, in upper tabs locate Compatibility and left-click on it.
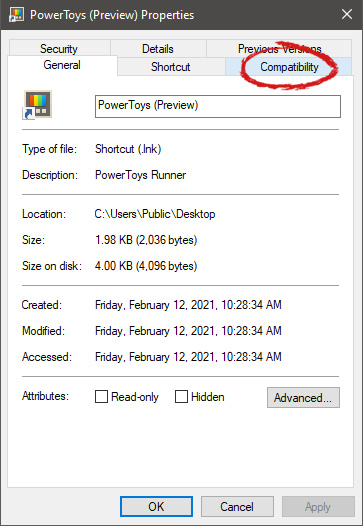 After the click, you will find yourself in application compatibility settings.
After the click, you will find yourself in application compatibility settings.
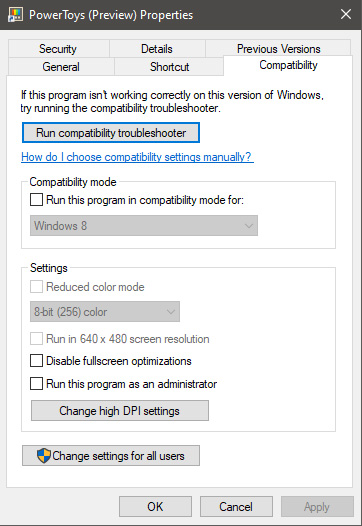 In this window, you will face different options to run the chosen application in various modes in order to make it run. How settings are self-explanatory and different applications will need different settings sadly we can not cover them all but your safest bet is to run them in an environment where they have worked.
For example, if the application was working fine in Windows XP and required administrator privileges, check Run this program as an administrator and Run this program in compatibility mode for Windows XP.
In this window, you will face different options to run the chosen application in various modes in order to make it run. How settings are self-explanatory and different applications will need different settings sadly we can not cover them all but your safest bet is to run them in an environment where they have worked.
For example, if the application was working fine in Windows XP and required administrator privileges, check Run this program as an administrator and Run this program in compatibility mode for Windows XP. 