This post will guide you in fixing high CPU, Memory, and Disk usage problems caused by NTOSKRNL.exe. NTOSKRNL stands for “NT Operating System Kernel. This file is a kernel image that is responsible for a lot of systems-based processes such as Hardware Virtualization, Process, and Memory. Aside from that, it is also the one that compresses the old pages of memory that reduces the overall amount of memory being used. If you notice that your computer is running slowly and you find that the NTOSKRNL.exe file is hogging your resources such as disk usage, CPU usage as well as memory usage, then read on as this post will guide you in fixing the problem caused by NTOSKRNL.exe.
Make use of the options given below to resolve the issues caused by NTOSKRNL.exe.
1] Scan your computer for potential malware
There might be a good chance that your computer might be infected with malware. And this malware might be associated with the NTOSKRNL.exe file and hence making it consume a lot of system resources. So, I would really recommend you to make sure that your Antivirus is up to date and then scan your computer with it specifically the C:/Windows/System32 folder because this is the location where the NTOSKRNL.exe file is located.
Option 1 – Put your computer in a Clean Boot State
The first thing you have to do is to put your computer in a Clean Boot State as this can help you in finding any incompatible programs that are causing the problem.
- Log onto your PC as an administrator.
- Type in MSConfig in the Start Search to open the System Configuration utility.
- From there, go to the General tab and click “Selective startup”.
- Clear the “Load Startup items” check box and make sure that the “Load System Services” and “Use Original boot configuration” options are checked.
- Next, click the Services tab and select the “Hide All Microsoft Services” check box.
- Click Disable all.
- Click on Apply/OK and restart your PC. (This will put your PC into a Clean Boot State. And configure Windows to use the usual startup, just simply undo the changes.)
- From there, start to isolate the problem by checking which one of the programs you installed recently is the root cause of the problem.
Once you’ve found any incompatible programs, you need to uninstall them. Refer to the steps below to do so.
- In the search box, type in “control” and then click on Control Panel (desktop app) among the search results.
- After that, select Programs and Features from the list which will give you a list of all the programs installed on your computer.
- From there, look for the concerned program and select it and then uninstall it.
Note: If you have downloaded the app from the Windows Store, you can simply right-click on it from the application list and then uninstall it.
Option 2 – Update or rollback drivers
If the first option didn’t work for you, then it’s time to either update or roll back the device drivers. It is most likely that after you updated your Windows computer that your driver also needs a refresh. On the other hand, if you have just updated your device drivers then you need to roll back the drivers to their previous versions. Whichever applies to you, refer to the steps below.
- Open the Devices Manager from the Win X Menu.
- Then locate the device drivers and right-click on them to open the Properties.
- After that, switch to the Driver tab and click on the Uninstall Device button.
- Follow the screen option to completely uninstall it.
- Finally, restart your computer. It will just reinstall the device drivers automatically.
Note: You can install a dedicated driver on your computer in case you have it or you could also look for it directly from the website of the manufacturer.
Option 3 – Try to run the DISM tool
If the first two options didn’t work, then running the Deployment Imaging and Servicing Management might. Using this built-in tool, you have various options such as the “/ScanHealth”, “/CheckHealth”, and “/RestoreHealth”.
- Open the Command Prompt with admin privileges.
- Then type in the following commands and make sure to hit Enter right after you type each one of them:
- Dism /Online /Cleanup-Image /CheckHealth
- Dism /Online /Cleanup-Image /ScanHealth
- exe /Online /Cleanup-image /Restorehealth
- Do not close the window if the process takes a while as it will probably take a few minutes to finish.
Option 4 – Try to stop the Runtime Broker process
The RuntimeBroker.exe or the Runtime Broker process is the one that monitors access to Windows APIs to make sure that the apps do not violate the core security of Windows. This process usually leaves a very small footprint. However, there are times when it consumes more resources than it’s supposed to and does not release memory after the work is done that results in a memory leak. As a result, it affects NTOSKRNL.exe which is why you have to stop the Runtime Broker process. To do so, refer to these steps:
- Tap the Ctrl + Shift + Esc to open the Task Manager.
- After opening Task Manager, go to the Processes tab and look for the Runtime Broker process.
- Once you find it, check if it is using more than 15% of your memory. If it is, then you most likely have an issue with an app installed on your computer.
- Select the Runtime Broker process and right-click on it and then click on the End Task option to end its process.
Option 5 – Try to run the Performance Troubleshooter
- Tap the Win + R keys to open the Run dialog box.
- Type “msdt.exe /id PerformanceDiagnostic” in the field and hit Enter to open the Performance troubleshooter.
- Then click on Next to get started. Wait until the process is completed.
Option 6 – Try using the Windows Performance Toolkit
You can also use the Windows Performance Toolkit in finding the root cause of the problem. Just refer to the following steps to use this toolkit.
- Search for “cmd” in the Cortana Search box and click on Command Prompt from the search results to open it.
- Next, type in the command given below or copy and paste it and then hit Enter:
xperf -on latency -stackwalk profile -buffersize 1024 -MaxFile 256 -FileMode Circular && timeout -1 && xperf -d cpuusage.etl
- After executing the command, wait for at least 60 seconds and then check the logs of the Windows Performance toolkit which is stored in a file named cpuusage.etl in the folder located at C:/Windows/System32. From there, you should see a list of all the causes of the System Resources being hogged.
 Guide
Guide
 When Task Manager opens, click on the startup tab on top.
When Task Manager opens, click on the startup tab on top.
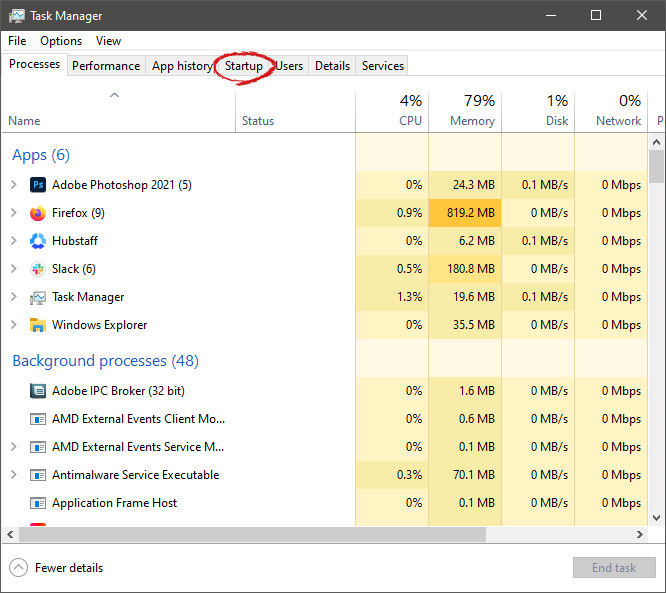 Once you click on startup you will get a list of applications that are set to be started when Windows is booted.
Once you click on startup you will get a list of applications that are set to be started when Windows is booted.
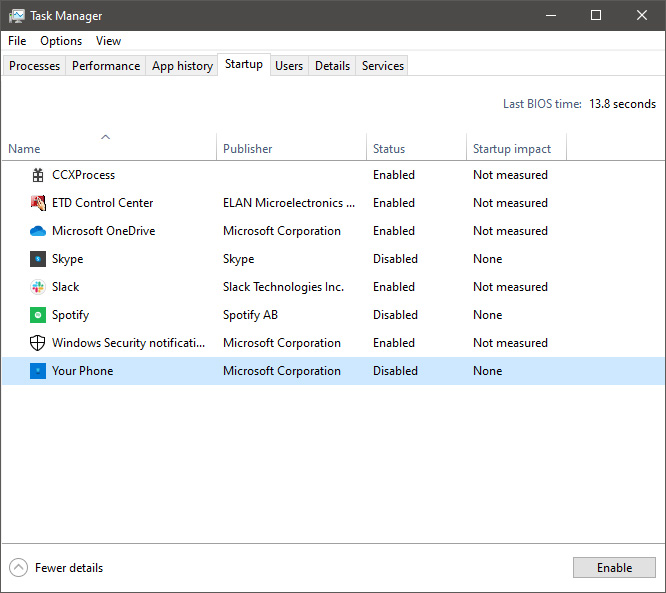 You can now click on the application and then click on disable on the bottom button, the application status will update in task manager to disabled and it will not be booted anymore when Windows starts. In this same manner, you can enable back some applications if you changed your mind about them.
Please note that some applications are using some services and must have them running or they will not work properly. The best practice is to disable applications you are positive you will not use or use rarely so you do not want them to slow down Windows.
You can now click on the application and then click on disable on the bottom button, the application status will update in task manager to disabled and it will not be booted anymore when Windows starts. In this same manner, you can enable back some applications if you changed your mind about them.
Please note that some applications are using some services and must have them running or they will not work properly. The best practice is to disable applications you are positive you will not use or use rarely so you do not want them to slow down Windows. 
 For people not familiar with recent events, the state of California has sued Blizzard for various things including discrimination and offensive behavior. Later Blizzard executives were caught shredding some evidence and things just started to go to worse from there.
After much drama, many people believed that this is the end for Blizzard entertainment and that they would not be able to recover from this since the community has sided with California and Blizzard has received a large punch as many subscribed WOW players have left the game.
Things are not so grim as they were looking as their Diablo 2 remake has made moderate success despite being released in these troubling times and there are rumors of Overwatch 2 planned release date as of the first quarter of 2022.
For people not familiar with recent events, the state of California has sued Blizzard for various things including discrimination and offensive behavior. Later Blizzard executives were caught shredding some evidence and things just started to go to worse from there.
After much drama, many people believed that this is the end for Blizzard entertainment and that they would not be able to recover from this since the community has sided with California and Blizzard has received a large punch as many subscribed WOW players have left the game.
Things are not so grim as they were looking as their Diablo 2 remake has made moderate success despite being released in these troubling times and there are rumors of Overwatch 2 planned release date as of the first quarter of 2022.

