AVFoundationCF.dll is a type of Dynamic Link Library file.
This DLL file is associated with AVFoundationCF and is developed by Apple Computer Inc. for Windows PC. This file functions similarly to any other DLL files. It comprises of small programs. This DLL file is typically needed to load and start the Apple iTunes utility.
The inability to call this file or the files to load triggers the AVFoundationCF.dll error message on your system.
The error message can be displayed in either of the formats on your PC:
“The program can’t start because AVFoundationCF.dll is missing from your computer. Try reinstalling the program to fix this problem.”
"This application failed to start because avfoundationcf.dll was not found.”
"Cannot find %COMMONFILES%AppleApple Application Supportavfoundationcf.dll."
"Cannot start AVFoundationCF. A required component is missing: avfoundationcf.dll.”
“Avfoundationcf.dll Access Violation."
"Cannot register avfoundationcf.dll."
 Error Causes
Error CausesAVFoundationCF.dll error can occur due to numerous reasons. However, the most common reasons for this error code include:
It is recommended to resolve the error as soon as you experience it virtually because if the error code is related to viral infection on your system, it can expose your PC to privacy errors and data security risk.
And if the error is triggered by registry issues, it can lead to serious threats like system crash, failure, and data loss.
Therefore, the AVFoundationCF.dll error not only hampers your ability to access and start Apple iTunes program but it also puts your PC at serious risk.
To fix the error AVFoundationCF.dll on your PC, here are some of the best and easy to do solutions that you can try:
Since dll files are shared files, there is a possibility that this file accidentally got deleted when you were uninstalling some other program on your system. If you experience missing AVFoundationCF dll file error message after performing any program on your PC, then chances are that it got deleted and maybe in your recycle bin.
So, first, check your recycle bin and search for the dll file. If you find it, restore it to fix the error.
To resolve the issue, try performing a driver update.
This can be done by downloading the latest drivers from the hardware manufacturer’s website. Now open Device Manager from the Control Panel and locate the hardware device that you want to update the driver for.
Once you find the hardware you are updating the driver for, right-click on the hardware icon and choose properties. In the properties windows, click the driver tab. Now click the update driver button. To activate changes, restart your PC.
To automatically update your computer's drivers when necessary, download and install DriverFIX.
To do this, simply go to the control panel, select programs and then uninstall a program and then select iTunes. Uninstall it and then repeat the same program and install the Apple iTunes program again on your PC by downloading the program from Apple’s official website.
If the error still persists, then it is advisable to scan your PC for viruses. This can be easily done by running a powerful antivirus on your PC. However, please note anti-viruses are notorious for slowing down PC performance. So, may have to compromise on the speed of your system.
If the error is caused by invalid and corrupt registry entries and damaged Avfoundationcf dll file, then the best way to resolve is to download a powerful registry cleaner.
We advise you to install Restoro on your PC. This is an advanced and a multi-functional PC Fixer integrated with multiple powerful utilities including a high functional registry cleaner, an antivirus and a system optimizer.
The registry cleaning utility scans all the registry issues and removes all errors triggered by the registry immediately.
It cleans the registry by wiping out all the unnecessary, obsolete and redundant files including invalid entries and bad registry keys. Furthermore, it also fixes the damaged and corrupt dll files including Avfoundationcf dll file. Thereby resolving the error right away.
Furthermore, the antivirus deployed in this software scans for all types of malicious codes like viruses, Trojans, spyware, and malware and removes them. To ensure you don’t compromise on your PC performance, it is deployed with a system optimizer utility that boosts the speed of your computer dramatically.
This tool is bug free, has a user-friendly interface and compatible with all Windows versions.
Click here to download Restoro and resolve Avfoundationcf.dll error on your PC today!

Error Code 0x8007000d is a common error code that can be found on the Windows 10 Operating system, although it can also appear in previous versions of the operating system, as well.
Common symptoms include:
There are four basic ways to try to resolve Error Code 0x8007000d on your Windows machine. Three of these are pretty simple for even the most basic users, while the final method requires some familiarity with running commands in the Command Prompt. If you don’t feel that you have the skill or confidence to complete the steps listed below, it is generally recommended that you get in touch with a qualified computer repair technician that can assist you in error resolution.
The main cause for the appearance of Error Code 0x8007000d on a Windows machine is that one of the files that the Update tool uses to run one or more updates cannot be found or has experienced damage. Fortunately, there are a few things that you can try on your machine that can be used to attempt to resolve the issues at hand.
Three primary methods exist for the resolution of Error Code 0x8007000d on a Windows machine. As mentioned above, two of these methods can usually be accomplished by basic users, while the third requires some degree of familiarity with the tools associated with the Command Prompt. If you don’t feel that you have the knowledge or skill necessary to follow these steps, contact a computer repair technician to aid you.
Here are the best ways to try to resolve Error Code 0x8007000d on your device:
From the Windows Update tool, you can attempt to run a scan using the Windows Update Troubleshooter, which can try to identify the specific issue that is occurring and to fix it automatically.
Not only will this tool often fix the problem at hand, but it can also help you to avoid other errors that you may have encountered later on in the Update process. This tool should always be your starting point when you encounter an error as you attempt to download or install updates for your Windows machine.
After the tool has been run, restart your computer to apply any changes and then reopen the Update tool to reattempt installation.
In some cases, the missing or corrupted files may be extensive enough that you need to restore your computer to an earlier point. If you create regular backups of your information or have a past version of the software that you can install, this can help you to resolve the issue. Otherwise, you may need to restore your device to its factory settings to resolve the error.
Always make sure to backup your important files and information before you perform a reset of your device, in order to ensure that you are able to return the computer to its original state when you have finished.One of the ways that you can try to resolve this particular error code is the use a DISM tool. This is accessed through the Command Prompt. In order to use this method, follow the steps below:
If you have not been able to resolve the error code using the steps above or if you are unsure of your ability to follow these steps on your own, get in touch with a trusted computer repair professional that is familiar with the Update process and the errors associated with it.
When Windows evolved into Windows 10, the program known as Windows Security Essentials is no longer. It is now the program known as Windows Defender. When a computer is upgraded from a previous version of Windows up to Windows 10, the Windows Defender takes over and will replace the Security Essentials. In a small percentage of Windows 10 upgrades, something will go wrong and the new program will fail to replace Security Essentials. The result will be that the operating system has both of the programs installed. In this case, Windows Defender will not offer any protection and Security Essentials will not be able to defend either. This error code will also present itself when the Windows Mail App in Windows 10 fail to retrieve and sync email from the user's account.
Common symptoms include:
 Error Causes
Error CausesError code 0x80070426 will present itself when a PC user has upgraded their OS from a previous version of Windows to the new Windows 10 version. When this happens, a small portion of users will experience the disconnect between older versions of specific programs, namely the virus protection. When the previous version of the program under a different name is not completely removed and the new virus protection program is installed, the programs will cancel each other out and collectively offer no protection.
This error code may also be found when Windows 10 tries to sync the user's email with the Windows Mail App.
Hold down the Windows Key and press R. Type in taskmgr into the run dialogue. You should locate the Windows Defender Service (this may show up as Windefend). Right-click on it and then choose Stop.
This will stop the program, but the program will start back up automatically when the computer restarts. While this program is stopped, uninstall Essentials.
To do this: go to Control Panel, Programs, and Features, Uninstall a Program. Alternately, you may hold down the Windows Key and press R, type in appwiz.cpl, click OK, and then locate Microsoft Essentials. Uninstall it, and then restart your computer.
After this is done, go to Settings, Update, and Security. Choose Windows Defender and ensure that Real-time protection is on. Refer back to the Task Manager, Services. Make sure that Defender service is on and running.
When error code 0x80070426 presents itself in the form of an error with the Mail app, it may be necessary to run an SFC scan.
Right-click on the Start menu or Windows icon, and select Command prompt. The command prompt may be navigated by using shortcut keys Win and X and then select it.
Run the command prompt and then type in sfc /scannow and then press enter. The SFC scan will be run, and be careful not to abort the process before it has finished. This will scan for any files that are lost or corrupt on the PC.
If the scan has found any corrupt files, type in this code and then hit Enter: findstr /c:”[SR]” %windir%LogsCBSCBS.log >”%userprofile%Desktopsfcdetails.txt.
To skip the repair of corrupt or missing files, type in: Dism /Online /Cleanup-Image /RestoreHealth. The details of the scan can be found on the sfcdetails.txt file that will be on the desktop.
 The console itself is coming in cylindrical shape powered by Intel CPU and ASUS GPU of the unknown chipset. It has Seagate Baraccuda 1TB SSD and it is VR-ready. The console will have raytracing and will be 4K ready.
The console itself is coming in cylindrical shape powered by Intel CPU and ASUS GPU of the unknown chipset. It has Seagate Baraccuda 1TB SSD and it is VR-ready. The console will have raytracing and will be 4K ready.
 Error Causes
Error Causesmountvol /E
mountvol /N
mountvol /R
diskpart
automount
automount enable
automount disable
automount scrub
Disk Write Error in Steam is thrown at you while you try to download or update the game in your library. If you are an unfortunate user of Steam that has encountered this error do not sweat, the error is usually tied to permission in windows or file corruption and not to hardware issues and can be easily resolved.
In this guide, we will go through solutions for this specific error and it is advisable to go through solutions as they are presented since they go from the easiest and most common issues.
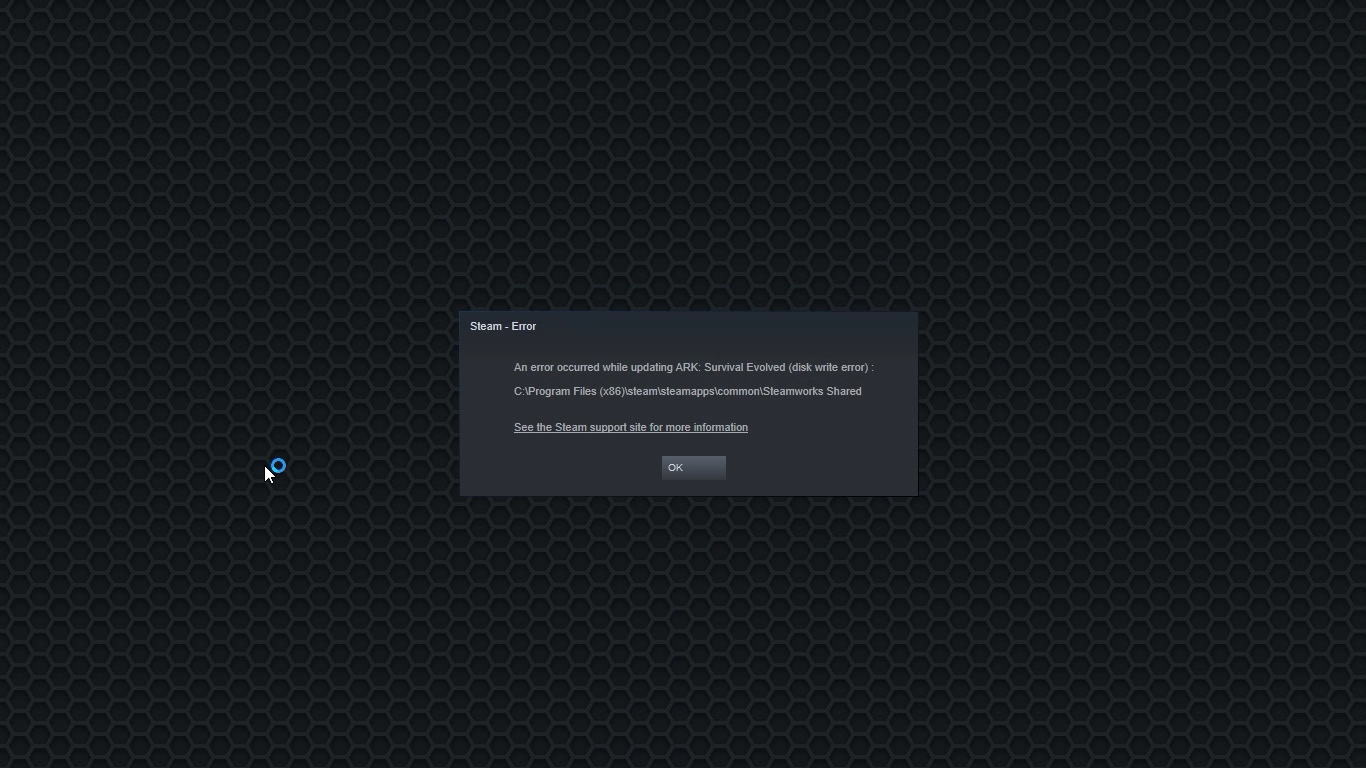
The easiest and quickest way of resolving this issue is just a simple restart of the Steam client. Just completely quit Steam and they run it again, if this has not solved the issue try rebooting your PC. In most cases, this can solve the issue since this error is known to be introduced with some communication issues with OS (Windows)
Disk write permissions could also cause this error because if by any chance the Steam library folder has been set or changed to the read-only client would be unable to write anything in it. To easily solve this issue completely exit the Steam client and rerun it as administrator. Just right-click on it and select Run as Administrator. If this has solved your issue run Steam always as an administrator.
To run always as an administrator right click on the steam executable, go to properties, and inside properties go to the compatibility tab. In the compatibility tab check run as administrator and click on OK.
If for any reason cache has become corrupted there is a big chance that this might be an issue why there is a disk drive error in Steam. To clear download, cache goes into your client, and on top drow down menu click on steam. Find and open settings and inside go to the downloads tab. Locate a clear download cache and immediately you will be prompted to restart Steam. After restart, you will be asked to login into steam and the issue with disk write should be gone.
Library folder issues can also be the source of disk write annoyance so let's repair them. Click steam in the top left and go to the settings. Locate and click on Downloads and then go to Steam library folders. You will be here shown all disk drivers you are using for steam games and all of the games that are downloaded.
Select the game you are getting errors with and click on three dots on the far right. From the menu choose the repair folder option. Take note that the more games you have installed, the more time the repair process will need.
Sometimes the issue is not at your end at all, servers can experience problems and outrages and this can directly reflect at your end with a disk write error. If any of the previous solutions have not resolved the issue this is the next logical step to try. If the server is facing issues then changing the download server will resolve the issue at your end.
Click on settings in the top drop-down menu and then click on the Steam library folder. Find the downloads page and then click on download region, Choose another server than one nearest to your location since that's what will Steam choose by default.
 Task View feature inside Windows 11 is actually a great feature, letting you quickly view open windows and virtual desktops. How Task view itself could be reached with keyboard shortcut combination of ⊞ WINDOWS + TAB some users will prefer this way of using it and thus button on the taskbar is something you do not want or need.
There is a very easy way to remove mentioned button and I will show you how to do it.
Right-click the taskbar button itself and click on Hide From Taskbar.
That’s it, you have done it.
Now in order for you to bring it back if you change your mind, you will have to do some extra steps but it is nothing difficult.
Right-click on the taskbar and click on Taskbar settings, you will be lead to Personalization > Taskbar.
Inside locate Taskbar Items and switch Task View to ON, you will see the Task View button right away showing itself again.
Task View feature inside Windows 11 is actually a great feature, letting you quickly view open windows and virtual desktops. How Task view itself could be reached with keyboard shortcut combination of ⊞ WINDOWS + TAB some users will prefer this way of using it and thus button on the taskbar is something you do not want or need.
There is a very easy way to remove mentioned button and I will show you how to do it.
Right-click the taskbar button itself and click on Hide From Taskbar.
That’s it, you have done it.
Now in order for you to bring it back if you change your mind, you will have to do some extra steps but it is nothing difficult.
Right-click on the taskbar and click on Taskbar settings, you will be lead to Personalization > Taskbar.
Inside locate Taskbar Items and switch Task View to ON, you will see the Task View button right away showing itself again. Problems occur when your PST file becomes corrupted or hits the size limit. Outlook will start to display error messages. These errors include like 0x80040119, 0x80040600, and 0x8004060c.
You might think Outlook problems are just a minor inconvenience. You can’t access your emails and contact information, but that doesn’t actually affect computer security, right? Wrong! Outlook problems can indicate serious corruption issues within your system.
In many cases, your PST file can even be targeted specifically by a virus.
Today, many viruses are specially designed to steal personal information and then sell that information on the online black market. Since so much personal data is stored within Outlook’s PST file, this is often the first place that viruses look.
If you don’t want some hacker in a foreign country to read your emails, steal your contact information, or do all sorts of other dangerous tasks, then we advise you to fix your PST problem as soon as possible.
Other causes include hitting the 2GB memory limit on older versions of Outlook, erroneous SMTP settings, etc,.
PST errors are an incredibly annoying problem. However, thanks to powerful software like Stellar Phoenix Outlook PST Repair, it has never been easier to fix Outlook and recover all of the data inside your PST file. That means that you won’t lose contact information, calendar entries, emails, or any other information stored in Outlook.
ScanPST.exe rarely fixes problems with the PST file. Since the application is only a few megabytes in size, its effectiveness is very limited. Although Microsoft designed ScanPST.exe to be an effective solution to any PST files, it fails miserably.
Ultimately, after downloading ScanPST.exe and running it, your Microsoft Outlook will still be unable to send or receive emails. And, to make matters worse, you might also be unable to access contact data or read your old emails.
Unlike other PST repair solutions, ScanPST.exe will not recover deleted emails or other lost Outlook data. In fact, using ScanPST.exe can sometimes cause your personal data to become even more difficult to recover.
If you do want to try out ScanPST.exe, then go ahead. While it probably won’t make your PST errors worse, it won’t even come close to fixing them. If you’re ready for a more serious solution to PST problems, then keep reading.
You might think Outlook problems are just a minor inconvenience. You can’t access your emails and contact information, but that doesn’t actually affect computer security, right? Wrong!
Outlook problems can indicate serious corruption issues within your system. In many cases, your PST file can even be targeted specifically by a virus.
Today, many viruses are specially designed to steal personal information and then sell that information on the online black market. Since so much personal data is stored within Outlook’s PST file, this is often the first place that viruses look.
If you don’t want some hacker in a foreign country to read your emails, steal your contact information, or do all sorts of other dangerous tasks, then we advise you to fix your PST problem as soon as possible.
Microsoft’s ScanPST.exe application clearly doesn’t work. So what’s the next best option? Well, a program called Stellar Phoenix Outlook PST Repair has been helping PC users solve Outlook problems for several years. As the world’s leading Outlook solution, Stellar Phoenix Outlook PST Repair will quickly and effectively repair any PST problems you encounter.
So how does Stellar Phoenix Outlook Repair work? Well, it starts by finding your PST file. Once the PST file has been found, Stellar Phoenix Outlook PST Repair determines if the file is corrupt or full. It will then repair your PST file either by removing the size limit or by fixing the corrupt files.
Once Stellar Phoenix Outlook PST Repair determines that your calendar appointments, contact data, and emails have all been successfully recovered, it permanently restores access to your PST file.
In fact, Stellar Phoenix Outlook PST Repair can even restore Outlook data that you deleted a long time ago. So, instead of just being a PST error recovery tool, Stellar Phoenix Outlook PST Repair is also a powerful data recovery program.
After letting Stellar Phoenix Outlook PST Repair go to work, open up Outlook and try it out. You’ll have full access to all of your Outlook files and folders, and all of those ScanPST.exe problems will be a thing of the past.
Stellar Phoenix Outlook PST Repair comes with many advantages. Here are just a few reasons why it’s such a popular program:
Stellar Phoenix PST Repair is superior to ScanPST.exe in every way. But Stellar Phoenix’s most important advantage is that it actually works. If you’re ready to quickly fix your Outlook PST errors, then Stellar Phoenix Outlook PST Repair can help. Download it here today to experience the magic of PST repair for yourself.