Same as in previous Windows versions, Windows 11 will also use certain applications as default ones for opening certain file types and file extensions. And yes, same as in previous versions it will come preconfigured for certain file types and associated applications like for example photos for pictures.
Of course, users usually have their own favorite applications for certain file types and much more prefer to open them inside the application of their choice instead of the default one.
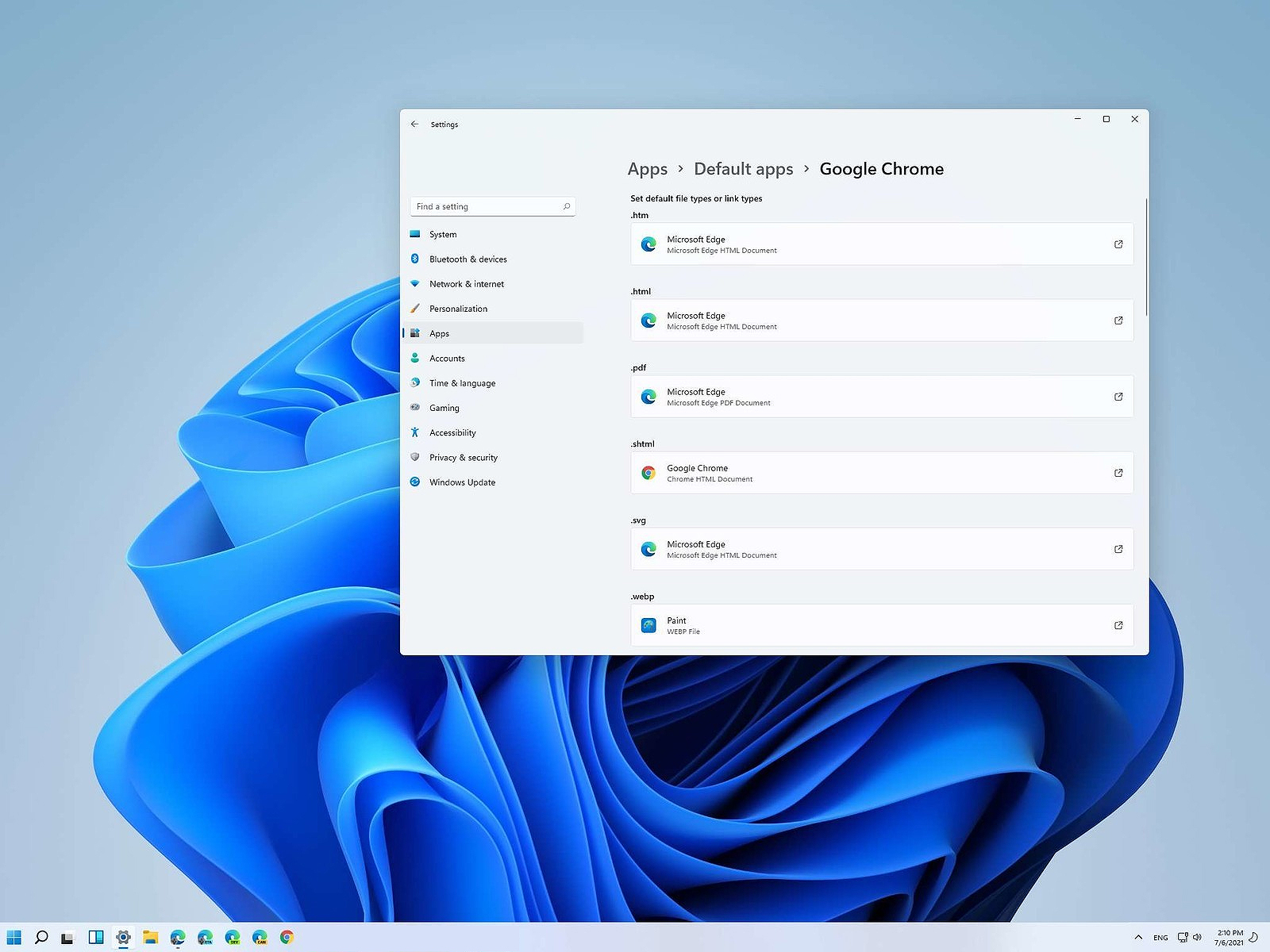
We can change the default application like in previous Windows versions but this time there are two ways and overall more control of this process. Windows 11 has settings for choosing default file type applications and default file extension applications giving you more control of this process.
The opening setting for apps
Whatever you wish to change default application or default extension application you will need to open settings for default application. Follow steps to quickly go into it.
- Press ⊞ WINDOWS + I to open settings
- Select Apps on left
- On the right part select Default Apps
Now you are in settings for choosing default applications
Choosing default application by file type extension
This is considering by Microsoft as a typical way to set default applications inside Windows 11. Once you are inside the settings app there is a box labeled
Enter a file type or link type. Inside the search box, type in file extension that you wish to associate the application with like .JPG, .TXT, or other.
If the file extension is not associated with any application you will be presented with a
Choose a Default button, if however, the file extension is already associated with the app, you will need to click on the app box itself.
In any case, a pop-up will appear and ask
How do you want to open YOUR FILE EXTENSION files from now on? Choose Application from the list of presented ones and click on
OK.
Choosing default file type
Another method is to select the default application by file type selecting application for it. In the settings screen, under the search box, you will have a list of installed applications. Choose the application that you would like to associate a file type with and click on it. On the next details screen scroll down and select the file type that you want to associate with the selected application and click on OK.
Other/third method
There is also the third method for choosing the default application for file type but it includes some surfing on your hard drive and it can be more time-consuming for first-time settings. But it is fairly quick when you need to only use it once on some new file type (for example you have a new application installed and want to switch just one file type extension to that application).
Locate the file that you want to associate with the application and right-click on it. Select
Open With from the menu and then
Choose Another App. Pop up will appear, select the application that you would like to use, and check the box beside
Always use this app to open CHOOSEN EXTENSION files followed by clicking on the
OK button.
 Same as in previous Windows versions, Windows 11 will also use certain applications as default ones for opening certain file types and file extensions. And yes, same as in previous versions it will come preconfigured for certain file types and associated applications like for example photos for pictures.
Of course, users usually have their own favorite applications for certain file types and much more prefer to open them inside the application of their choice instead of the default one.
We can change the default application like in previous Windows versions but this time there are two ways and overall more control of this process. Windows 11 has settings for choosing default file type applications and default file extension applications giving you more control of this process.
Same as in previous Windows versions, Windows 11 will also use certain applications as default ones for opening certain file types and file extensions. And yes, same as in previous versions it will come preconfigured for certain file types and associated applications like for example photos for pictures.
Of course, users usually have their own favorite applications for certain file types and much more prefer to open them inside the application of their choice instead of the default one.
We can change the default application like in previous Windows versions but this time there are two ways and overall more control of this process. Windows 11 has settings for choosing default file type applications and default file extension applications giving you more control of this process.





