TranslationBuddy is a browser extension developed by MindSpark Inc. for Google Chrome. This extension allegedly offers users the ability to translate any text to any language.
From the Author: Now enjoy immediate access to the FREE web, email, and text translations, Multilanguage Virtual Keyboards, words of the day, and more!
This extension configures your New Tab page to TranslationBuddy™ to provide these features.
Get FREE translations instantly. An easy way to translate web pages, texts, and emails.
Unfortunately, this extension hijacks your browser's new tab page, and default search engine, changing it to MyWay. While installed, it monitors browser activity such as visited websites, clicked links, downloaded information, and sometimes even personal information that it later uses to display additional unwanted ads in your browser.
About Browser Hijackers
Browser hijacking is a type of unwanted program, usually a web browser add-on or extension, which then causes modifications in the web browser’s settings. Browser hijackers are capable of doing a number of things on your PC. Generally, browser hijacking is used for earning advertising revenue from forced advert clicks and site visits. Though it might appear harmless, these tools are made by vicious people who always try to take advantage of you, so that hackers can earn money from your naivety and distraction. Some browser hijackers are designed to make particular modifications beyond the browsers, like altering entries in the system registry and letting other malware further damage your machine.
Indications of browser hijack
There are several symptoms that point to a browser hijacking: you see unauthorized modifications to your Internet browser’s home page; bookmark and the new tab are likewise modified; The default search page of browser is modified; unwanted new toolbars are added to your web browser; unstoppable flurries of popup advertisements appear on your computer screen; your web browser gets sluggish, buggy, crashes very often; you’re blocked to access the websites of computer security solution providers.
Exactly how they invade computer systems
Browser hijackers can enter a PC by some means or other, for example via file sharing, downloads, and email also. They may also come from any BHO, browser extension, toolbar, add-on or plug-in with malicious intent. Some internet browser hijackers spread in user’s computers using a deceptive software distribution strategy called “bundling” (commonly through shareware and freeware).
Browser hijacking may lead to severe privacy problems and even identity theft, affect your web browsing experience by taking control over outbound traffic, substantially slows down your computer or laptop by deleting lots of resources, and cause system instability at the same time.
Removing browser hijackers
Some hijackers could be removed by deleting the free software they came with or by deleting any add-ons you’ve recently added to your computer system. Having said that, many hijackers are extremely tenacious and require specialized applications to remove them. Inexperienced PC users shouldn’t ever attempt the manual form of removal, as it demands thorough system knowledge to perform fixes on the system registry and HOSTS file.
You might opt for automatic browser hijacker removal methods by simply installing and running an efficient anti-malware program. One of the recommended tools for fixing browser hijacker infections is SafeBytes Anti-Malware. It will help you remove any pre-existing malicious software in your system and provides you real-time monitoring and protection from the latest internet threats. Together with the anti-malware tool, a system optimizer could help you in deleting all associated files and modifications in the registry automatically.
How To Get Remove Virus That Is Preventing Anti-Malware Downloads?
Malware can cause all kinds of damage when they invade your system, from stealing sensitive details to deleting data files on your PC. Certain malware variants modify browser settings by adding a proxy server or modify the computer’s DNS configurations. In these cases, you’ll be unable to visit certain or all websites, and thus unable to download or install the required security software to eliminate the malware. If you are reading this article now, you might have perhaps realized that virus infection is the reason behind your blocked net connectivity. So how to proceed if you want to download and install an antivirus program such as Safebytes? Refer to the instructions below to remove malware through alternative ways.
Install the antivirus in Safe Mode
In Safe Mode, you are able to modify Windows settings, uninstall or install some programs, and eliminate hard-to-delete viruses. In the event, the malicious software is set to load automatically when the PC starts, switching to this mode may prevent it from doing so. In order to get into Safe Mode or Safe Mode with Networking, press F8 while the system is booting up or run MSConfig and look for the “Safe Boot” options under the “Boot” tab. Once you’re in safe mode, you can try to install your anti-malware software application without the hindrance of the malware. After installation, run the malware scanner to eliminate most standard infections.
Switch to an alternate internet browser
Malicious code may exploit vulnerabilities on a particular internet browser and block access to all antivirus software sites. If you seem to have a virus attached to Internet Explorer, then switch over to an alternate browser with built-in safety features, such as Firefox or Chrome, to download your preferred anti-malware program – Safebytes.
Make a bootable USB anti-virus drive
Another approach is to download and transfer an anti-malware application from a clean PC to run a scan on the infected computer. Adopt these measures to run the antivirus on the affected computer system.
1) On a virus-free PC, download and install Safebytes Anti-Malware.
2) Plug the Flash drive into the clean computer.
3) Double-click the Setup icon of the antivirus software to run the Installation Wizard.
4) Select the USB flash drive as the location for saving the file. Follow the directions to complete the installation process.
5) Disconnect the pen drive. Now you can use this portable anti-malware on the infected computer system.
6) Double-click the EXE file to run the Safebytes tool from the pen drive.
7) Hit the “Scan” button to run a full system scan and remove malware automatically.
Let's Talk About SafeBytes Security Suite!
Today an anti-malware program can protect your computer from various kinds of internet threats. But wait, how to choose the right one amongst the many malware protection software that’s available out there? As you might be aware, there are numerous anti-malware companies and tools for you to consider. A few of them do a good job in getting rid of malware threats while some will damage your PC themselves. You need to be careful not to choose the wrong product, especially if you purchase a premium program. Among few good programs, SafeBytes Anti-Malware is the highly recommended software program for the security-conscious individual.
SafeBytes anti-malware is really a powerful, very effective protection application made to assist users of all levels of computer literacy in finding and removing malicious threats out of their PC. Using its cutting-edge technology, this application can assist you to eliminate several types of malware which include viruses, worms, PUPs, trojans, adware, ransomware, and browser hijackers.
SafeBytes anti-malware takes computer protection to a totally new level with its enhanced features. Below are some typical features found in this software:
Real-time Threat Response: SafeBytes provides complete and real-time security for your laptop or computer. This utility will constantly monitor your computer for any suspicious activity and updates itself continuously to keep abreast of the newest threats.
Anti-Malware Protection: This deep-cleaning anti-malware program goes much deeper than most antivirus tools to clean out your personal computer. Its critically acclaimed virus engine finds and disables hard to remove malware that hides deep inside your computer.
“Fast Scan” Features: SafeBytes Anti-Malware has a multi-thread scan algorithm that works up to 5 times faster than any other protection software.
Web Protection: Safebytes allots all websites a unique safety ranking that helps you to have an idea of whether the website you are about to visit is safe to browse or known to be a phishing site.
Light-weight: SafeBytes provides total protection from online threats at a fraction of the CPU load because of its enhanced detection engine and algorithms.
24/7 Online Support: You could get high levels of support around the clock if you’re using their paid software.
To sum it up, SafeBytes Anti-Malware offers great protection combined with very low system resource usage with both great malware prevention and detection. Now you may know that this tool does more than just scan and remove threats from your PC. So if you are looking for the best anti-malware subscription for your Windows-based PC, we suggest SafeBytes Anti-Malware software.
Technical Details and Manual Removal (Advanced Users)
If you wish to carry out the removal of TranslationBuddy manually rather than using an automated software tool, you may follow these steps: Proceed to the Windows Control Panel, click on the “Add/Remove Programs” and there, select the offending application to uninstall. In case of suspicious versions of web browser plugins, you can easily get rid of them via your web browser’s extension manager. Additionally, it is recommended to factory reset your browser to its default condition to fix corrupt settings.
To ensure the complete removal, manually examine your hard drive and registry for all of the following and eliminate or reset the values accordingly. But bear in mind, this is often a challenging task and only computer professionals could carry it out safely. Furthermore, certain malware is capable of replicating or preventing deletion. It is recommended that you carry out the removal process in Windows Safe Mode.


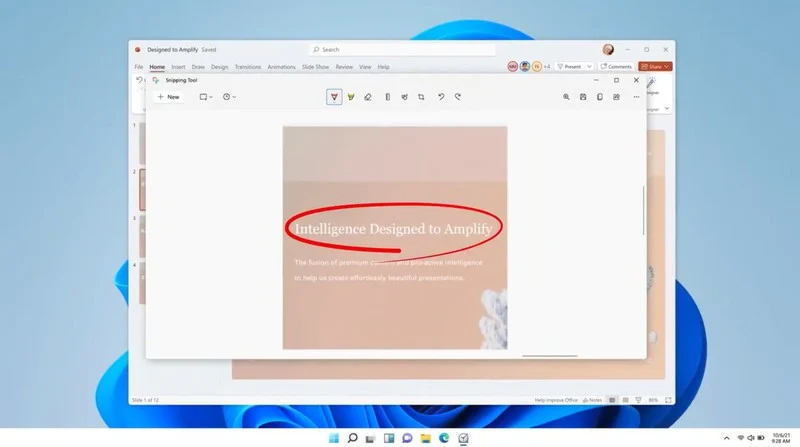 The latest update from Panos Panay on Twitter is including New and redesigned Snipping tool inside Windows 11. From the shared video, we can see that it includes modern Windows 11 UI redesign and it looks and feels like a part of Windows 11.
More things that can be seen from the shared video is that it looks like the new snipping tool is a merged version of the old with snip & sketch.
It is good to see that it is still possible to capture screen with easier way natively inside Windows 11 but some more functionality would be more welcome I guess.
Users were asking for added functions for a long time like adding simple text for example but from shared video, no new features were presented so for some users 3rd party solutions will still be the way to go.
The new and redesigned Snipping tool will roll out with the next update and we will see then about all new features inside it firsthand. Until then, take care.
The latest update from Panos Panay on Twitter is including New and redesigned Snipping tool inside Windows 11. From the shared video, we can see that it includes modern Windows 11 UI redesign and it looks and feels like a part of Windows 11.
More things that can be seen from the shared video is that it looks like the new snipping tool is a merged version of the old with snip & sketch.
It is good to see that it is still possible to capture screen with easier way natively inside Windows 11 but some more functionality would be more welcome I guess.
Users were asking for added functions for a long time like adding simple text for example but from shared video, no new features were presented so for some users 3rd party solutions will still be the way to go.
The new and redesigned Snipping tool will roll out with the next update and we will see then about all new features inside it firsthand. Until then, take care. 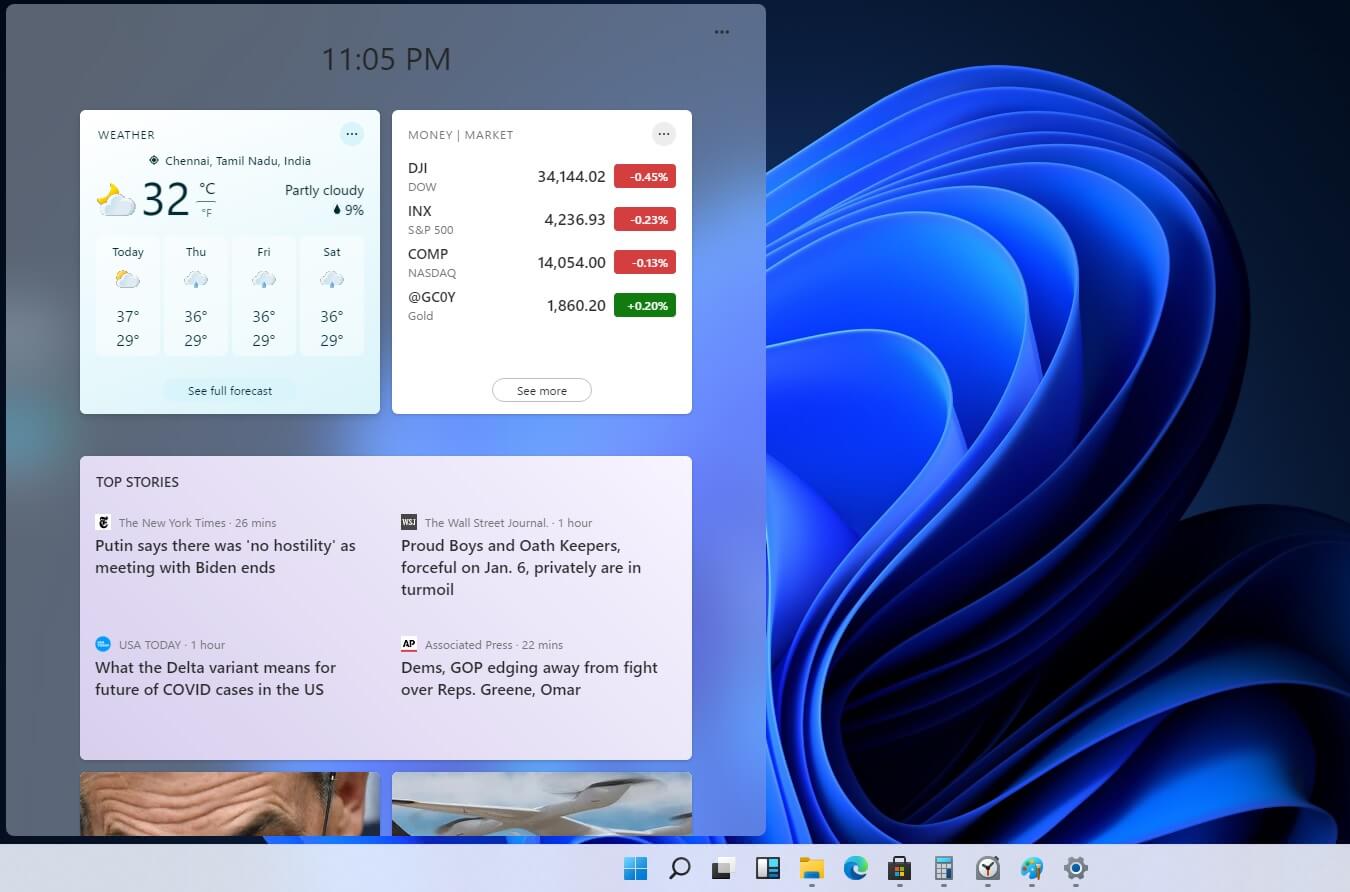 Originally Microsoft has imagined its widgets menu as Microsoft-only widgets but it seems that they have changed their mind.
Due to the latest leak, it seems that Microsoft will open the widgets menu to 3rd party developers as well but at launch, it will be only official widgets. It was hinted that later widgets menu will be open to developers who want to bring their own stuff into it.
Distribution, date, and technology that will need to be used in order to create your widget have not been discussed nor leaked at a given time but in some way, I am very glad that at least some customization will be in Windows 11.
It is funny and amusing how some things that were in Windows Vista are getting back like glass design, round corners, and widgets. Let’s just hope Windows 11 will be a better Windows than Vista was.
Originally Microsoft has imagined its widgets menu as Microsoft-only widgets but it seems that they have changed their mind.
Due to the latest leak, it seems that Microsoft will open the widgets menu to 3rd party developers as well but at launch, it will be only official widgets. It was hinted that later widgets menu will be open to developers who want to bring their own stuff into it.
Distribution, date, and technology that will need to be used in order to create your widget have not been discussed nor leaked at a given time but in some way, I am very glad that at least some customization will be in Windows 11.
It is funny and amusing how some things that were in Windows Vista are getting back like glass design, round corners, and widgets. Let’s just hope Windows 11 will be a better Windows than Vista was. 