What is SMSFromBrowser
SMSFromBrowser is a Browser Extension developed by MindSpark. This extension usually comes bundled up with other software or via online advertising. Allegedly this extension allows you to send SMS messages from your computer, however, all it does is point you to other websites that offer this service.
While active this extension monitors your browsing behavior, it records your website visits, clicks, links, and sometimes even private information, in order to use this data to better serve additional ads. During your browsing sessions, you may encounter additional unwanted ads, sponsored links, and sometimes even pop-up ads.
Several anti-virus scanners have detected this extension as a potentially unwanted extension / Browser Hijacker, and due to its privacy mining behavior, it is not recommended to keep it on your computer.
Browser hijackers (sometimes referred to as hijackware) are a kind of malicious software that modifies web browser settings without the computer owner’s knowledge or permission. These hijacks appear to be increasing at an astonishing rate around the world, and they could be actually nefarious and sometimes harmful too. Browser hijackers are capable of doing more than just modifying homepages. These are typically used to force hits to a specific site, manipulating web traffic to generate ad revenue. Though it might seem naive, these tools are made by vicious people who always try to take advantage of you, so that they can easily make money from your naive and distraction. As soon as the program attacks your laptop or computer, it starts to mess things up a whole lot that slows your system down to a crawl. In the worst-case scenario, you will be forced to deal with serious malware threats as well.
Indications of browser hijack
There are many signs of web browser hijacking:
1. home page is changed
2. your browser is constantly being redirected to porn sites
3. the default online search engine and the default browser settings are altered
4. discover new toolbars that you simply didn’t add
5. you notice numerous ads pop up on the browsers or computer screen
6. your browser gets sluggish, buggy crashes very often
7. you can’t go to specific sites such as homepages of anti-malware software.
How it infects your personal computer
A browser hijacker can be installed on your computer or laptop when you visit an infected site, click on an e-mail attachment, or download something from a file-sharing website. They can be included with toolbars, BHO, add-ons, plug-ins, or browser extensions. Some internet browser hijackers spread in user’s PC by using a deceptive software distribution technique known as “bundling” (often through freeware and shareware). A good example of a notorious browser hijacker is the most recent Chinese malware known as “Fireball”, which has attacked 250 million PCs worldwide. It acts as a hijacker but could be turned into a fully functioning malware downloader afterward.
Browser hijackers could interrupt the user’s web surfing experience greatly, keep track of the websites visited by users and steal financial information, cause difficulty in connecting to the web, and eventually create stability problems, making applications and computers freeze.
Removal
Some types of browser hijackers can be effortlessly removed from your PC by deleting malicious applications or any other recently added freeware. Many times, it could be a tough job to discover and get rid of the malicious program because the associated file will be running as part of the operating system process. And there’s no denying the very fact that manual repairs and removal methods can be a difficult job for an amateur computer user. Also, there are several risks associated with fiddling around with the pc registry files.
Browser hijackers could be effectively removed by installing and running an anti-malware application on the affected computer. To remove any browser hijacker from your PC, you can download the following professional malware removal program – Safebytes Anti-Malware. And utilize a system optimizer, such as Safebytes Anti-Malware, to erase all associated files in the registry and repair browser problems. All malware is detrimental and the degree of the damage may vary greatly according to the type of infection. Certain malware types alter web browser settings by adding a proxy server or modify the computer’s DNS configuration settings. In such cases, you will be unable to visit some or all internet sites, and thus unable to download or install the required security software to eliminate the infection. If you’re reading this article, odds are you’re stuck with a virus infection that is preventing you to download or install the Safebytes Anti-Malware program on your system. Follow the instructions below to get rid of the malware by alternative methods.
Install the anti-virus in Safe Mode
If the malware is set to run automatically when Microsoft Windows starts, entering Safe Mode could very well block the attempt. Just bare minimum required programs and services are loaded whenever you boot your PC into Safe Mode. To start your Windows XP, Vista, or 7 PCs in Safe Mode with Networking, follow the instructions below.
1) Tap the F8 key continuously as soon as your PC boots, however, before the large Windows logo shows up. This would invoke the “Advanced Boot Options” menu.
2) Use the arrow keys to choose Safe Mode with Networking and press ENTER.
3) Once this mode loads, you should have an internet connection. Now, get the malware removal application you need by using the web browser. To install the program, follow the guidelines in the installation wizard.
4) Right after the software is installed, let the diagnostic scan run to eliminate trojans and other malware automatically.
Use an alternate internet browser to download an antivirus application
Some malware only targets specific web browsers. If this sounds like your situation, employ another browser as it might circumvent the virus. The best way to avoid this problem is to opt for an internet browser that is known for its security measures. Firefox has built-in Phishing and Malware Protection to help keep you secure online.
Create a bootable USB anti-virus drive
Another option is to store and run an antivirus software program completely from a Flash drive. To run anti-malware from a flash drive, follow these simple steps:
1) On a virus-free PC, download and install Safebytes Anti-Malware.
2) Insert the pen drive on the same PC.
3) Run the setup program by double-clicking the executable file of the downloaded software, which has a .exe file extension.
4) Choose the USB flash drive as the destination for saving the software file. Follow the directions to complete the installation process.
5) Now, transfer the thumb drive to the infected computer system.
6) Double click the Safebytes Anti-malware icon on the pen drive to run the application.
7) Press the “Scan” button to run a full computer scan and remove malware automatically.
Benefits and Features of SafeBytes Anti-Malware
These days, an anti-malware tool can protect your computer or laptop from various types of internet threats. But wait, how to select the best one amongst plenty of malware protection applications that are available on the market? You may be aware, there are several anti-malware companies and products for you to consider. Some of them are good, some are ok types, and some will ruin your PC themselves! You need to be very careful not to select the wrong application, particularly if you purchase a premium application. When it comes to commercial antimalware tool options, many people opt for well-known brands, like SafeBytes, and they are quite happy with it.
SafeBytes can be described as a powerful, real-time anti-malware application that is created to assist the average computer end user in safeguarding their computer from malicious internet threats. Through its cutting-edge technology, this software will help you protect your PC against infections caused by various kinds of malware and other threats, including spyware, adware, computer viruses, worms, trojan horses, keyloggers, ransomware, and potentially unwanted program (PUPs).
SafeBytes has excellent features when compared to various other anti-malware programs. A few of them are given as below:
Real-time Active Protection: SafeBytes gives you round-the-clock protection for your personal computer limiting malware attacks instantly. They are extremely effective in screening and removing various threats because they’re continuously revised with new updates and alerts.
Robust, Anti-malware Protection: Safebytes is made on the best virus engine within the industry. These engines will detect and get rid of threats even during the early stages of a malware outbreak.
Internet Security: SafeBytes inspects the hyperlinks present on a webpage for possible threats and informs you if the website is safe to visit or not, through its unique safety rating system.
Low CPU Usage: SafeBytes is a lightweight and user-friendly anti-virus and anti-malware solution. Since it uses minimum computer resources, this application leaves the computer power exactly where it belongs to: with you actually.
24/7 Online Tech Support: You may get absolutely free 24/7 technical support from their computer experts on any product queries or computer security concerns.
SafeBytes will keep your personal computer safe from the latest malware threats automatically with almost no input needed from you again. Once you have downloaded and installed this software, you will no longer have to bother about malware or any other security concerns. You will get the best all-around protection for the money you pay on SafeBytes anti-malware subscription, there isn’t any doubt about it.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove SMSFromBrowser without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by SMSFromBrowser

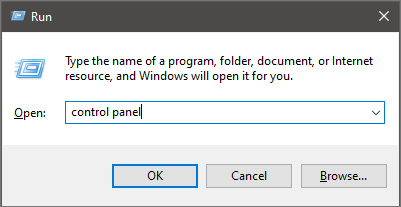
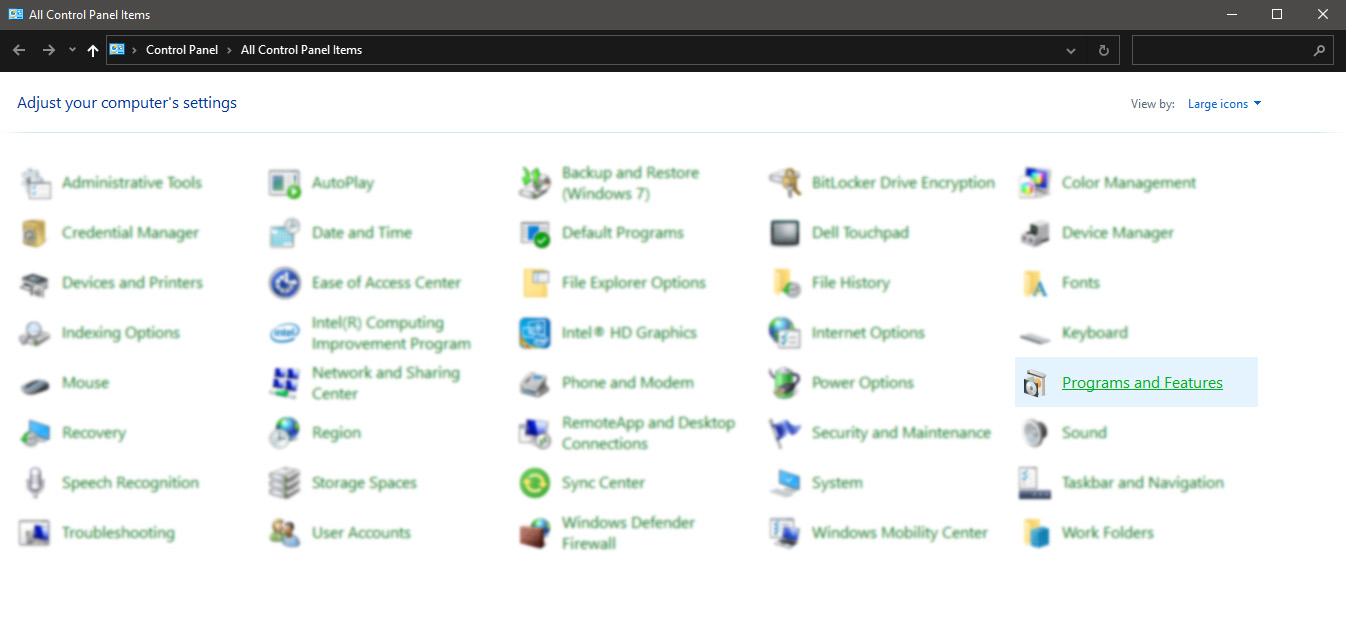
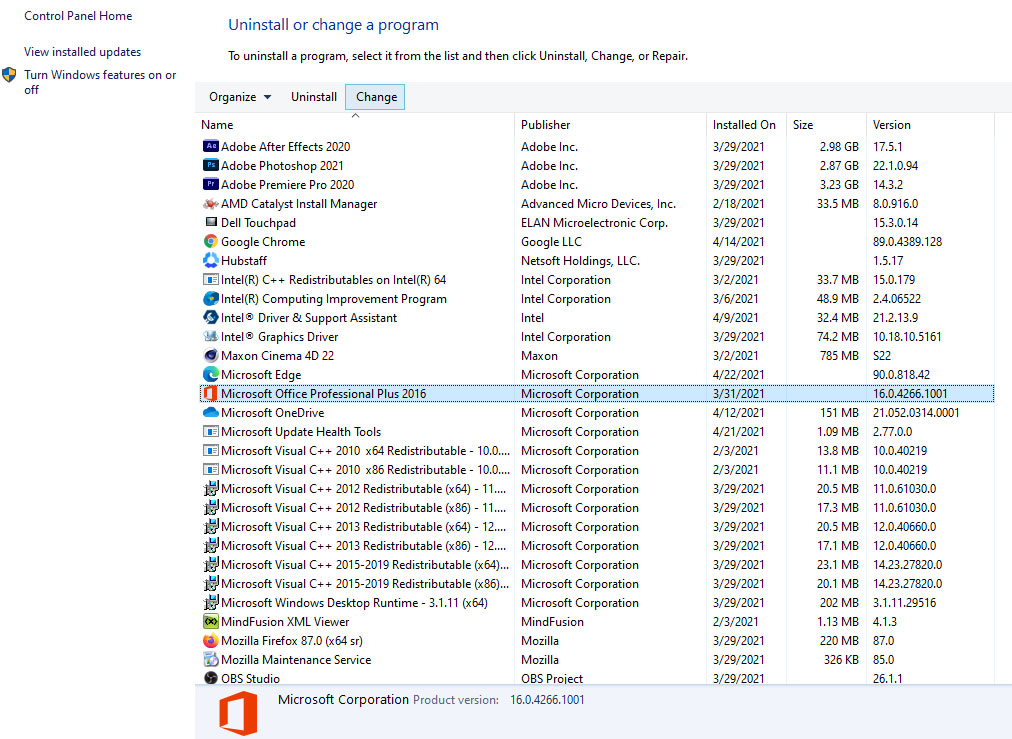
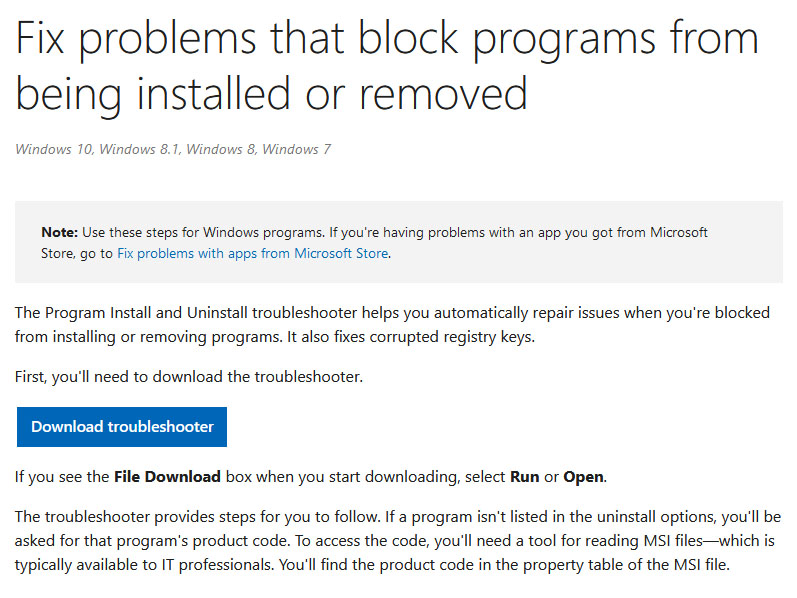

 If you are one of the users that are experiencing this kind of annoyance, we have a solution for you. Follow this guide as presented and repair this annoying error.
If you are one of the users that are experiencing this kind of annoyance, we have a solution for you. Follow this guide as presented and repair this annoying error.

