SweetIM Toolbar for Internet Explorer is a browser add-on which adds various shortcuts to your browsers for easy access. This toolbar also changes your homepage to home.sweetim.com. The toolbar is typically bundled with the free Sweet Instant Messenger program and does not necessarily get uninstalled when Instant Messenger is removed from the user’s PC. Additionally, if the home page and search settings were modified by this toolbar, they need to be manually reverted back by the user.
This extension injects various ads into your browser search results and changes your default search engine. While you are browsing the internet, this software records your website surfing data, clicks, and possibly private information. Several Anti-virus programs have classified SweetIM Toolbar as a potentially unwanted application and are not recommended to keep.
About Browser Hijackers
Browser hijacking means that a malicious program code has power over and modified the settings of your web browser, without your approval. They are made to disrupt browser functions for many different reasons. Generally, the idea would be to force users to visit particular sites that are looking to increase their visitor traffic and produce higher ad revenue. Most people assume that such websites are legitimate and harmless but that is incorrect. Nearly every browser hijacker poses an actual threat to your online safety and it is vital to categorize them under privacy dangers. On top of that, hijackers can make the whole infected system vulnerable – other harmful malware and viruses would grab these opportunities to intrude into your system effortlessly.
Major signs that an internet browser has been highjacked
The common signs that indicate having this malicious software on your PC are: the home page of your respective browser is changed unexpectedly; bookmark and the new tab are also modified; the default search engine and the default web browser settings are altered; discover new toolbars that you didn’t add; you find lots of pop-up ads on your computer screen; web pages load very slowly and sometimes incomplete; Inability to navigate to particular sites, particularly antivirus and also other computer security software websites.
Exactly how they get into your computer or laptop
There are several ways your computer can get infected with a browser hijacker. They usually arrive by way of spam e-mail, via file sharing websites, or by a drive-by download. Many browser hijackings originate from add-on software, i.e., toolbars, browser helper objects (BHO), or extensions added to browsers to give them additional features. A browser hijacker may also come bundled up with some freeware that you unwittingly download to your computer system, compromising your internet security. A good example of some notorious browser hijackers includes Anyprotect, Conduit, Babylon, SweetPage, DefaultTab, RocketTab, and Delta Search, but the names are continually changing.
Browser hijackers can record user keystrokes to gather potentially invaluable information that leads to privacy concerns, cause instability on systems, severely disrupt the user experience, and eventually slow down the PC to a stage where it becomes unusable.
Removal
Some browser hijacking could be quite easily corrected by identifying and removing the corresponding malware application through your control panel. But, many browser hijackers are hard to eliminate manually. Regardless of how much you attempt to remove it, it may keep returning over and over. You should consider doing manual repairs only if you are a tech-savvy person, as there are risks associated with tinkering around with the computer registry and HOSTS file.
Browser hijackers could be effectively removed by installing the anti-malware application on the affected computer. One of the finest tools for repairing browser hijacker malware is Safebytes Anti-Malware. It will help you get rid of any pre-existing malware on your computer and gives you real-time monitoring and protection from new internet threats. Along with the antivirus tool, a PC optimizer will help you in getting rid of all related files and modifications in the registry automatically.
Can't Install Safebytes Anti-malware because of Malware? Do This!
Viruses could potentially cause a great deal of damage to your personal computer. Certain malware variants alter browser settings by including a proxy server or change the computer’s DNS settings. In such cases, you will be unable to visit certain or all internet sites, and thus unable to download or install the necessary security software to remove the infection. If you’re reading this, chances are you’re stuck with a virus infection that is preventing you to download or install Safebytes Anti-Malware software on your system. Although this kind of issue will be difficult to get around, there are some actions you can take.
Eliminate malware in Safe Mode
The Windows-based PC has got a special mode referred to as “Safe Mode” in which only the minimum required programs and services are loaded. If the malware is blocking access to the internet and affecting your computer, launching it in Safe Mode enables you to download anti-virus and run a diagnostic scan while limiting potential damage. To boot into Safe Mode, hit the “F8” key on the keyboard just before the Windows logo screen shows up; Or after normal Windows boot up, run MSCONFIG, check the Safe Boot under the Boot tab, and then click Apply. As soon as you restart the PC into Safe Mode with Networking, you can download, install, and update the anti-malware program from there. At this point, you can actually run the anti-virus scan to remove computer viruses and malware without any hindrance from another malicious application.
Switch over to an alternate browser
Malicious code could exploit vulnerabilities on a specific internet browser and block access to all antivirus software sites. If you appear to have malware attached to Internet Explorer, then switch over to an alternate internet browser with built-in safety features, such as Firefox or Chrome, to download your preferred antivirus program – Safebytes.
Make a bootable USB anti-virus drive
Another solution is to create a portable antivirus program onto your USB thumb drive. Follow these steps to run the anti-virus on the affected PC.
1) On a clean computer, install Safebytes Anti-Malware.
2) Mount the USB drive onto the same computer.
3) Double-click the Setup icon of the anti-malware software to run the Installation Wizard.
4) Pick a USB flash drive as the place when the wizard asks you exactly where you want to install the application. Follow activation instructions.
5) Disconnect the USB drive. You may now utilize this portable antivirus on the infected computer.
6) Double-click the EXE file to open the Safebytes program from the thumb drive.
7) Click “Scan Now” to run a complete scan on the infected computer for viruses.
Overview of SafeBytes Anti-Malware
Nowadays, an anti-malware program can protect your laptop or computer from different forms of online threats. But wait, how do choose the best one amongst plenty of malware protection applications that’s available on the market? You may be aware, there are numerous anti-malware companies and tools for you to consider. A few of them are good, some are ok types, and some will affect your computer themselves! You should go with a product that has gained a strong reputation and detects not just viruses but other kinds of malware as well. On the list of highly recommended applications by industry, analysts are SafeBytes Anti-Malware, a well-known security application for Windows computers.
SafeBytes anti-malware is a trusted software that not only protects your system completely but is also very user-friendly for people of all ability levels. Once you’ve got installed this application, SafeBytes advanced protection system will ensure that absolutely no viruses or malicious software can seep through your PC.
There are many great features you’ll get with this security product. Listed below are some of the great ones:
Active Protection: SafeBytes offers complete and real-time security for your laptop or computer. This tool will constantly monitor your PC for suspicious activity and updates itself regularly to keep current with the latest threats.
Antimalware Protection: With its advanced and sophisticated algorithm, this malware elimination tool can identify and remove the malware threats hiding within your computer system effectively.
Web protection: Through its unique safety score, SafeBytes informs you whether a site is safe or not to visit it. This will make sure that you’re always certain of your safety when browsing the net.
Lightweight Tool: This program is not “heavy” on the computer’s resources, so you’ll not see any overall performance difficulties when SafeBytes is operating in the background.
24/7 Live Expert Support: Support service is available 24 x 7 x 365 days via chat and email to answer your concerns.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove SweetIM without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by SweetIM

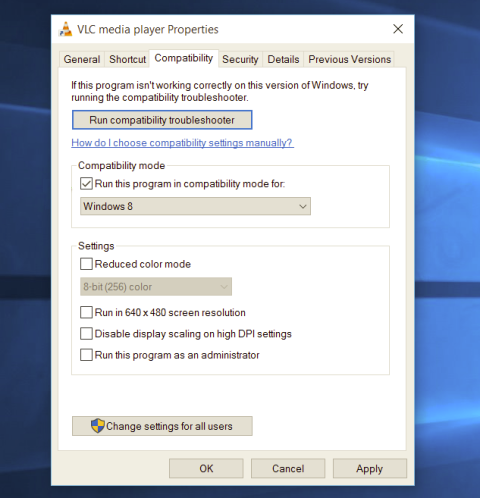 Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
 Jokes aside, I truly believe that choosing to upgrade your System to Windows 11 at this point in time is a bad decision and I will explain why I do believe it.
Jokes aside, I truly believe that choosing to upgrade your System to Windows 11 at this point in time is a bad decision and I will explain why I do believe it.
