intel's first gaming card that will hit the market soon has been shown in its innovation event, the Intel Arc A770. In its core ticks ACM-G10, coming with 32 Xe-cores and all the way up to 16GB of GDDR6 memory (the basic entry-level version will have 8GB of GDDR6). The card will support ray tracing and supersampling with Intel's XeSS.

This is Intel's first gaming desktop GPU and after testing with some YouTube channels it turned out that the card itself sits somewhere between nVIDIA RTX 3060 Ti and an RTX 3070 so it will still be low in performance compared with the new RTX 4090 or AMD's new RDNA3 upcoming lineup. But as stated this is Intel's first gaming graphics card and having this kind of performance is no small feat for the first-time product.
One thing that is really great tho and that is going for Arc A770 GPU is its price! The Limited Edition card will cost $329 which is at this moment most cheapest GPU currently on the market in that performance range. nVIDIA is between $500 and $700 for comparison and if Intel can hold on to its performance with almost half the price card could be a great hit among gamers. GPU itself will launch on October 12th.

“<PATH OF THE EXECUTABLE FILE>, This application has failed to start because its side-by0side configuration is incorrect. Please see the application event log or use the command-line sxstrace.exe tool for more detail”.This kind of problem has something to do with the C++ runtime package in the background. It could also be related to an error for a registry value. Whatever the cause is, you can fix this error with the help of some suggestions provided in this post. You can try to reinstall the application or check the registry setting or reinstall the suitable Visual C++ Runtimes or re-enable the Microsoft .NET Framework. For more details, refer to the instructions given below.
USB Kill, a USB device is able to fry and damage your computer, mobile phone, router, etc. This device is quite dangerous and can kill electronics the moment it is inserted into an available port. By now people should know that they should not put unknown USB sticks into their devices because of potential virus and malware threats but this raises using unknown sticks to a whole new level.

Kill kits are not really new to the market, they have existed before but lately, technology really progressed and the latest USB sticks are really good, their success rate is around 95% which is pretty high and should not be taken lightly.
The second thing that you really should not play with strange USB sticks is that they dropped in price really hard, although top Kill kits will still go as high as around 300 USD, there are really cheap ones lurking in Ali Express that are just 6 USD!!! that makes them affordable devices for the mass market.
The device is made to take energy and current from the port it is plugged in, multiply it and release its charge back into the device, successfully frying some components immediately. Some more professional Kill sticks can even fry devices even when the device itself is not powered and can be even started remotely.
The point of this article is to make you aware that you should not in any kind of circumstances use and plug-in USB sticks into your devices that you do not know where they come from, especially from the mail!!
“This policy setting prevents File Explorer from encrypting files that are moved to an encrypted folder. If you enable this policy setting, File Explorer will not automatically encrypt files that are moved to an encrypted folder. If you disable or do not configure this policy setting, File Explorer automatically encrypts files that are moved to an encrypted folder. This setting applies only to files moved within a volume. When files are moved to other volumes, or if you create a new file in an encrypted folder, File Explorer encrypts those files automatically.”
ExpressFiles is a program developed by Express Solutions. A number of Anti-Virus programs have flagged this program as a Potentially Unwanted Application. In many instances, it is bundled with additional programs on installation.
The program claims it offers users easy to search for various currently popular search terms. During our testing, the software never displays any search results, no matter the search words. Upon installation and setup, it defines an auto-start registry entry which makes this program run on each Windows boot for all user logins. A scheduled task is added to Windows Task Scheduler in order to launch the program at various scheduled times. The program defines an exception rule in Windows Firewall, allowing it to connect to the internet without limitations and auto-update itself.
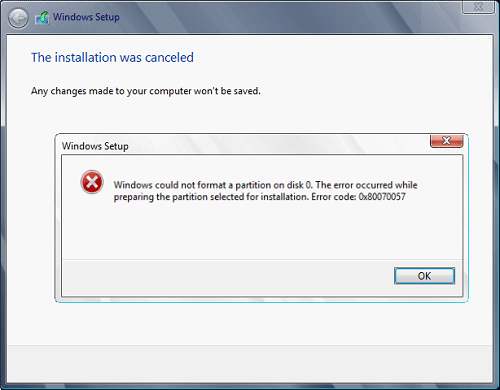 This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.