Error 10013 is a type of Socket Windows PC error. Socket error 10013 occurs when the attempt to access the server is denied. This indicates that the needed socket connection is denied which further implies that a port is blocked or unreachable.
 Error Causes
Error CausesThe socket error 10013 can occur due to multiple reasons:
To resolve the socket error 10013 on your PC, here are some methods that you can try:
To resolve this issue on your PC, you may have to temporarily disable Firewall. Sometimes Firewall can stop you from connecting to the server. Try doing this; it is most likely to resolve the error. If the Firewall is the reason for the denied access, turning it off will surely help.
If disabling the Firewall doesn’t resolve the issue, try disabling your antivirus software temporarily. If the error still persists, then try other solutions listed below.
Incompatible drivers could be a reason too for denied server access.
Your server may no longer be using the drivers that you have on your PC which is why you may not be getting permission to access it. If this is the cause, then the best way to resolve it is to upgrade drivers. To find out about new drivers, visit the software manufacturer’s website for new drivers and then download them to your PC.
Sometimes the underlying cause of the error could be registry issues and misconfigured files.
If you don’t wipe out unnecessary and obsolete files from your systems like junk files, cookies, internet history, temporary files, and other files from your PC, it can damage and corrupt the registry and misconfigured files thereby causing socket error 10013 on your system.
To resolve registry issues and repair your PC, download Restoro. It is an advanced, easy to use, and highly functional PC fixer embedded with multiple utilities including a powerful registry cleaner. It is deployed with an intuitive algorithm that scans and detects all registry issues in seconds.
It removes all the unnecessary and obsolete files stored in your PC overloading your registry. This registry cleaner repairs the damaged and misconfigured files and restores the registry, thereby resolving socket error 10013 on your system right away.
It has simple navigations and a user-friendly interface which makes it very easy for all levels of users to work around and use it to its maximum advantage. Furthermore, it can be installed on all Windows PC.
Restoro is compatible with all Windows versions.
In addition to this, it also includes several other value-added features such as an antivirus, a system optimizer, and an Active X controls and class scanner. These utilities can be used to resolve numerous other PC-related errors.
Click here to download Restoro today and resolve socket error 10013 on your PC right away.

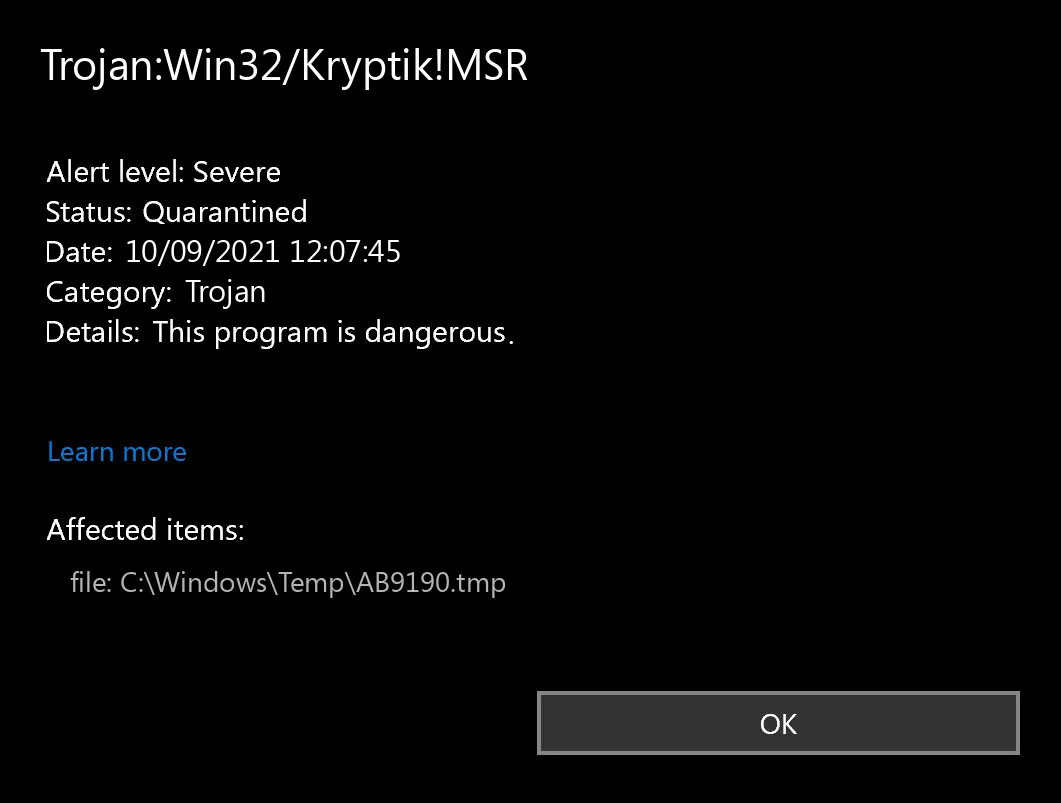 Trojan.Kryptik creates the following registry entry or registry entries:
Trojan.Kryptik creates the following registry entry or registry entries: Error Causes
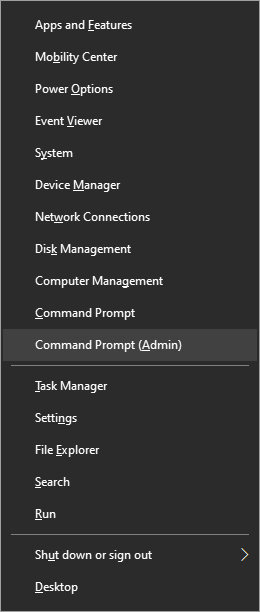
Error Causes Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
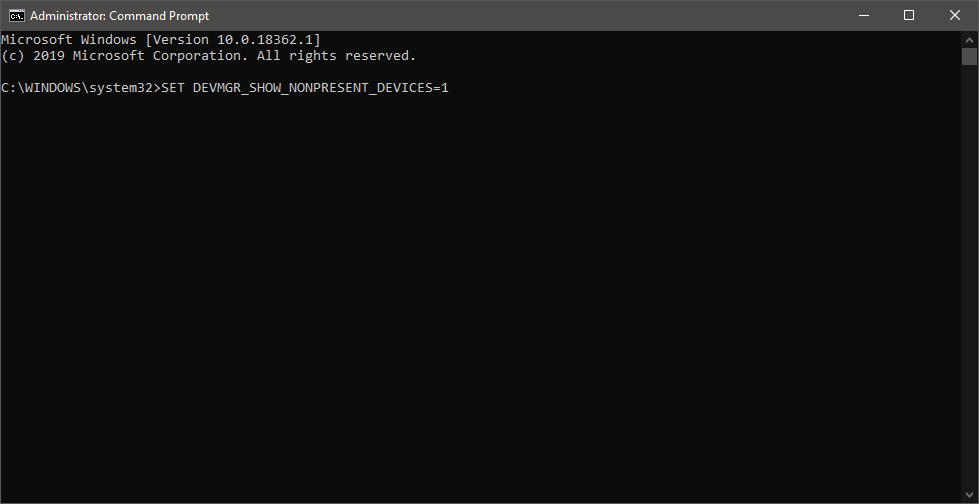 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
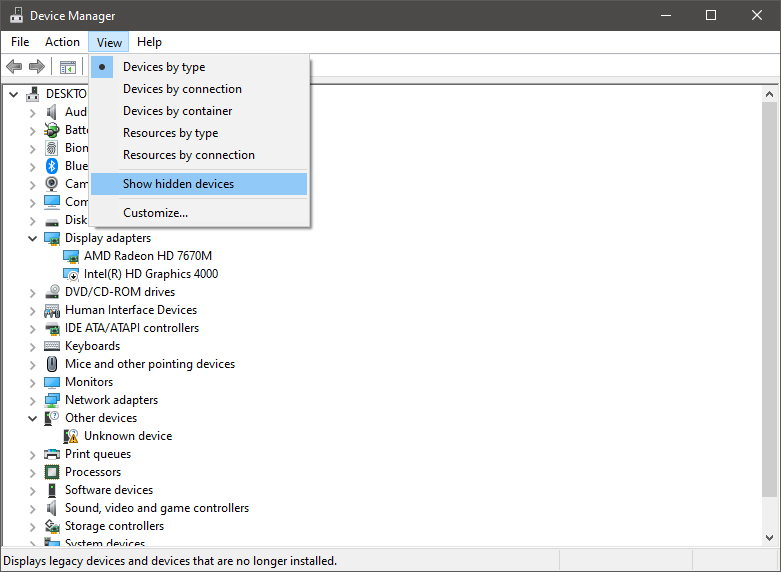
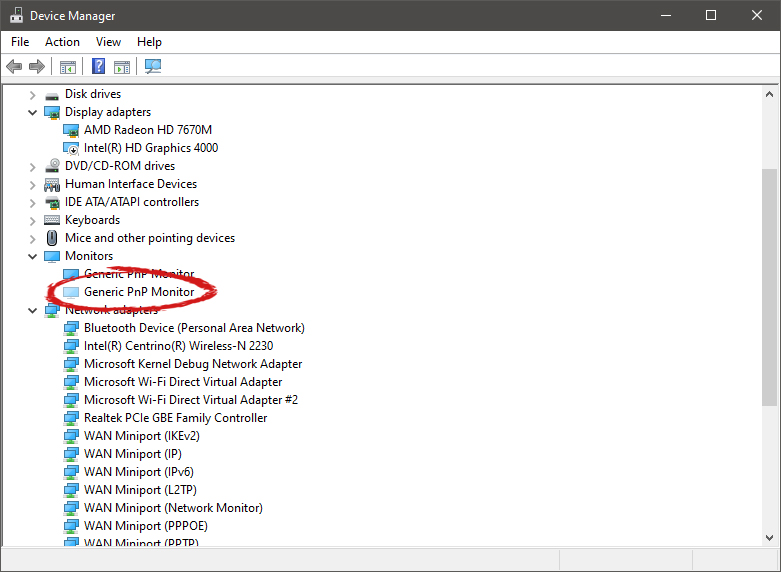 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
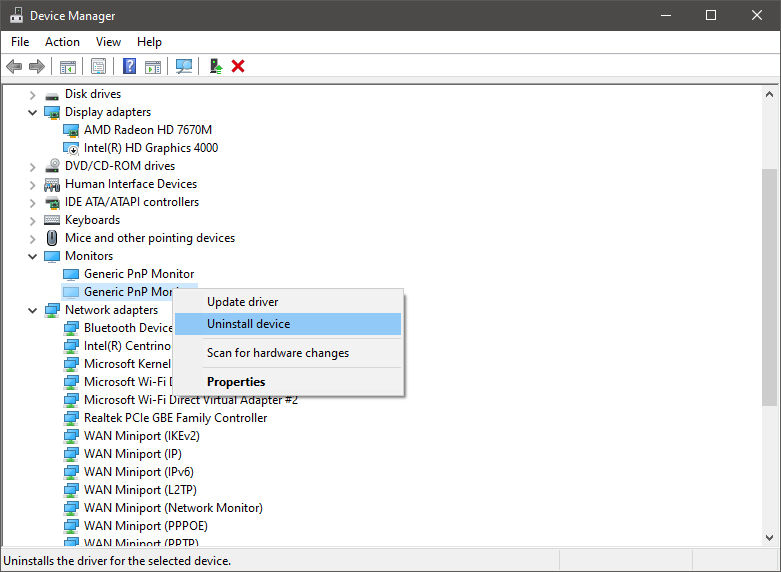 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. CHKDSK /R /X C:
/ipk <ProductKey> or /ato [<Activation ID>]
Stable Diffusion is a machine learning model developed by Stability AI to generate digital images from natural language descriptions. The model can be used for different tasks like generating image-to-image translations guided by text prompts and upscaling images.
Unlike competing models like DALL-E, Stable Diffusion is open source and does not artificially limit the images it produces. Stable diffusion was trained on a subset of the LAION-Aesthetics V2 data set. It can run on most consumer hardware equipped with a modest GPU and was hailed by PC World as "the next killer app for your PC".

Since Stable Diffusion is run locally and not in the cloud, as mentioned there is no limit to the number of images that you can produce but in order to use it you will have to get down a little dirty with setting your PC environment for it since it is not really an application, it is a command line text based descriptor that will use python to generate your images, so there is no install nor GUI.
In this guide, we will show you how to both install and run Stable Diffusion on your local PC so you can start producing some cool images all by yourself.
Make no mistake, Stable Diffusion will not run on a potato PC, in order to harvest the power of AI-generated imagery this is what you will need:
For this tutorial, we are covering the installation and running of Stable Diffusion on Windows PC. The steps presented here are presented in a way that installation can be performed on any operating system but precise instructions will be for Windows OS.
The first thing to do is to install GIT. It is a tool that will let you easily maintain and install repos from the internet. to install it go to: https://git-scm.com/ and click on download. Follow the instructions for your version of the operating system. If you are a developer you are familiar with GIT and if you already have it installed you can skip this step.
One thing that is important when installing GIT locally is to select to use it via the command line (the second option that says "Git from the command line and also from 3rd-party software").
Now when we have GIT installed, next thing is to use Miniconda3 to install python and all required libraries that are needed. Get the installer at: https://docs.conda.io/en/latest/miniconda.html
Miniconda3 is basically an easy installer so you do not have to install tons of stuff manually from different websites and sources, it is nicely packaged in the installer that will take care of everything.
After the previous two steps, we are ready now to actually install Stable Diffusion. Go to https://huggingface.co/CompVis/stable-diffusion#model-access and install the latest library (as of the writing of this article currently it is stable-diffusion-v1-4-original, the last one on the right), the library is almost 5GB in size so be prepared for big download.
After installing stable diffusion's latest library it is time to update it to the newest version. You can download ZIP from GIT HUB https://github.com/CompVis/stable-diffusion
Once downloaded click on the Windows start button and type in Miniconda3 and click on open. Create a folder and name it how you want on a drive of your choice. For this example, we will install it all in disk C under folder AI_art, follow the instructions below but use your own names and destination instead. Do not close Minicoda3 after typing commands!!!
cd c:/
mkdir AI_art
cd AI_art Extract GitHub files that you have downloaded into your new folder and get back to Minicoda3 and type the next commands:
cd C:\AI_art\stable-diffusion-main
conda env create -f environment.yaml
conda activate ldm
mkdir models\ldm\stable-diffusion-v1Let the whole process finish, some files are large and it might take a while. After the whole process is finished and completed, copy the checkpoint file that you have downloaded into: C:\AI_art\stable-diffusion-main\models\ldm\stable-diffusion-v1
After the file is copied rename it to model.ckpt and you are finished.
The created environment is needed in order to actually use Stable Diffusion to create images. Each time you want to use it you will have to run it, so go into Miniconda3, and inside it type:
conda activate ldm
cd C:\AI_art\stable-diffusion-mainafter we are inside the folder call the script with the parameters:
python scripts/txt2img.py --prompt "TXT DESCRIPTION OF IMAGE THAT YOU WANT TO CREATE" --plms --n_iter 5 --n_samples 1and that's it, your image is created and it is located in C:\AI_art\stable-diffusion-main\outputs\txt2img-samples\samples
chkdsk /f /r
MyWebFace is a browser extension developed by Mindspark. This extension claims to allow users to easily access websites that allow them to make a cartoon portrait of themselves. While this may seem interesting in the beginning, all this extension does is to add links to already popular websites that are easy to find.
When installed MyWebFace changes your default search engine and your home page to MyWay.com.
While the extension is running it gathers user browsing information, allowing it to mine data and better server unwanted ads throughout your browsing sessions. MyWebFace has been marked as a Browser Hijacker by many anti-virus programs, and while not considered malware, it is not recommended to keep it on your computer.