SearchApp by Blpsearch is a Browser Hijacker that is presently targeting Google Chrome browsers. It is offered as a tool gives user enhanced online search experience. Search App also has other amazing tools that let you quickly search the web from a new tab window.
This extension changed your home page and new tab search to blpsearch. While installing you will see additional ads and sponsored links displaying throughout your browsing sessions. It collects user browsing information and uses it to better serve sponsored content.
About Browser Hijackers
Browser hijacking means a malicious code has control over and altered the settings of your web browser, without your approval. There are numerous reasons why you might experience an internet browser hijack; however commercial, marketing, and advertising are the key reasons for their creation. Generally, hijackers will force hits to websites of their preference either to increase web traffic generating higher ad earnings, or to obtain a commission for every user visiting there. Nonetheless, it is not that naive. Your internet safety is jeopardized and it is also very annoying. In a much worst case, your browser could be hi-jacked to download malicious software that will do a lot of damage to your computer or laptop.
Find out how to identify a browser hijack
Symptoms that your internet browser is hijacked include: your web browser’s homepage is suddenly different; bookmark and the new tab are also modified; the default browser configurations have been changed and/or your default web engine is altered; unsolicited new toolbars are added to your web browser; you observe numerous ads appear on your web browsers or display screen; your browser has instability issues or displays frequent errors; Inability to navigate to certain sites, especially anti-malware and other computer security software sites.
How it infects your personal computer
Browser hijackers can enter a PC by some means or other, for example via file sharing, downloads, and email too. Many internet browser hijackings come from add-on applications, i.e., toolbars, browser helper objects (BHO), or extensions added to web browsers to provide them extra capabilities. Some browser hijackers spread in user’s computers by using a deceptive software distribution strategy known as “bundling” (generally through shareware and freeware). Examples of popular browser hijackers are Fireball, GoSave, Ask Toolbar, CoolWebSearch, RocketTab, and Babylon Toolbar.
Browser hijackers may record user keystrokes to gather potentially important information leading to privacy issues, cause instability on systems, drastically disrupt the user experience, and ultimately slow down the system to a stage where it becomes unusable.
How to repair a browser hijack
The one thing you could try to remove a browser hijacker is to discover the malicious software within the “Add or Remove Programs” list of the Windows Control Panel. It might or might not be there. When it is, uninstall it. Yet, some hijackers will be more difficult to locate or remove since they might get themselves associated with certain important computer files that enable it to operate as a necessary operating-system process. You should think about carrying out manual fixes only if you’re a tech-savvy individual because there are negative consequences associated with messing around with the system registry and HOSTS file.
Installing and running antivirus software on the affected computer could automatically erase browser hijackers and other malicious programs. Safebytes Anti-Malware features a cutting-edge anti-malware engine to help you prevent browser hijacker infection in the first place, and clean up any existing issues. Together with the anti-malware tool, a PC optimizer, can help you in getting rid of all linked files and modifications in the computer registry automatically.
What To Do If You Cannot Install Any Anti-Malware?
Malware can cause plenty of damage to your personal computer. Some malware goes to great lengths to stop you from downloading or installing anything on your computer, particularly anti-virus software programs. If you are reading this now, you’ve perhaps realized that a malware infection is a reason behind your blocked net traffic. So how to proceed if you need to download and install an antivirus application such as Safebytes? There are a few steps you can take to circumvent this problem.
Install anti-virus in Safe Mode with Networking
In Safe Mode, you can actually change Windows settings, uninstall or install some program, and eradicate hard-to-delete malware. In the event the malware is obstructing the internet connection and affecting your computer, running it in Safe Mode allows you to download antivirus and run a scan whilst limiting potential damage. To boot into Safe Mode, hit the “F8” key on the keyboard right before the Windows boot screen shows up; Or right after normal Windows boot up, run MSConfig, check Safe Boot under Boot tab, and click Apply. Once you’re in Safe Mode, you can attempt to install your antivirus software program without the hindrance of the malware. Following installation, run the malware scanner to eliminate most standard infections.
Use an alternate browser to download security software
Some malware only targets particular web browsers. If this is your situation, use another web browser as it could circumvent the virus. In the event you suspect that your Internet Explorer happens to be hijacked by a virus or otherwise compromised by cybercriminals, the most effective thing to do is to switch to an alternate web browser such as Google Chrome, Mozilla Firefox, or Apple Safari to download your chosen security program – Safebytes Anti-Malware.
Install antivirus on a flash drive
Here’s yet another solution which is utilizing a portable USB anti-virus software that can scan your system for malware without needing installation. Do these simple steps to clear up your affected computer using a portable antivirus.
1) On a clean PC, download and install Safebytes Anti-Malware.
2) Connect the flash drive to a USB port on the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded application, which has a .exe file extension.
4) Select thumb drive as the place when the wizard asks you where you want to install the application. Follow the directions to finish the installation process.
5) Transfer the USB drive from the clean computer to the infected computer.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Click “Scan Now” to run a scan on the affected computer for viruses.
Protect your Computer against Malware With SafeBytes Security Suite
If you’re looking to download the anti-malware program for your PC, there are various tools in the market to consider but you just cannot trust blindly anyone, irrespective of whether it is paid or free program. Some of them are excellent, some are ok types, and some will ruin your computer themselves! When searching for anti-malware software, pick one that offers reliable, efficient, and complete protection against all known computer viruses and malware. In terms of commercial tool options, most people go with well-known brands, like SafeBytes, and are quite happy with it.
SafeBytes anti-malware is a powerful, highly effective protection tool created to help users of all levels of computer literacy in identifying and eliminating harmful threats out of their computer. Through its cutting-edge technology, this software protects your personal computer against infections brought on by different types of malware and other threats, including spyware, adware, computer viruses, worms, trojan horses, keyloggers, potentially unwanted programs (PUPs), and ransomware.
SafeBytes anti-malware offers a myriad of enhanced features that sets it apart from all others. Listed below are some of the features you might like in SafeBytes.
World-class AntiMalware Protection: Using its enhanced and sophisticated algorithm, this malware elimination tool can identify and eliminate the malware threats hiding in your PC effectively.
Active Protection: SafeBytes gives round-the-clock protection for your computer restricting malware attacks in real-time. This software will always keep track of your PC for suspicious activity and updates itself regularly to keep abreast of the latest threats.
Website Filtering: SafeBytes checks and gives a unique safety rating to every single website you visit and block access to web pages considered to be phishing sites, thus safeguarding you against identity theft, or known to contain malware.
Light-weight: SafeBytes is a lightweight and user-friendly antivirus and anti-malware solution. As it utilizes minimal computer resources, this program leaves the computer’s power exactly where it belongs to: with you.
Fantastic Tech Support: You can get high levels of support round the clock if you’re using their paid software.
To sum it up all, SafeBytes Anti-Malware gives you outstanding protection combined with very low system resource usage with both great malware detection and prevention. Once you’ve installed SafeBytes Anti-Malware, you no longer need to worry about malware or any other security concerns. So when you need advanced forms of protection features and threat detections, purchasing SafeBytes Anti-Malware could be worth the dollars!
Technical Details and Manual Removal (Advanced Users)
If you don’t wish to use an automated tool and prefer to remove SearchApp manually, you could possibly do so by going to the Windows Add/Remove Programs menu in the control panel and deleting the offending program; in cases of browser extensions, you can uninstall it by going to the browser’s Add-on/Extension manager. You’ll probably also want to totally reset your internet browser to its default configuration settings.
In order to ensure the complete removal, manually examine your hard drive and registry for all the following and eliminate or reset the values as needed. But bear in mind, this is often a difficult task and only computer professionals can perform it safely. In addition, some malware is capable of replicating or preventing deletion. It is advisable that you carry out the removal procedure in Safe Mode.
Files:
%Documents and Settings%\All Users\Application Data\Blpsearch.com
%program files %\internet explorer\Blpsearch.com\random.mof
%program files (x86)%\common files\speechengines\
%programData%\suspicious folders\
%windows%\system32\driver\messy code.dll
%AppData%\blpsearch.com\toolbar uninstallStatIE.dat
%app data%\Blpsearch.comn Blpsearch.com
Registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MATS\WindowsInstaller\EAF386F0-7205-40F2-8DA6-1BABEEFCBE8914.07.30.07.52.18 ProductName=Blpsearch.com
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Tracing\Muvic_RASAPI32
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Tracing\Muvic_RASMANCS
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EAF386F0-7205-40F2-8DA6-1BABEEFCBE89\DisplayName=Blpsearch.com
HKEY_USERS\S-1-5-21-3825580999-3780825030-779906692-1001\Software\Microsoft\Windows\CurrentVersion\Uninstallf25211-852e-4d10-b6f5-50b1338a9271\DisplayName=Blpsearch.com

 Coursera was one of the pioneers when it comes to college education online. When it started all courses were free and offered certificates if the taker has done tasks with a passing grade. Today not everything is free but still, there are tons of free courses that can help you to learn something new and to advance in your work or hobby.
Google is using the Coursera platform to deliver its courses to the audience and besides google a lot of academic professors from Princeton, Stanford, John Hopkins and many more are presently offering their course material.
Coursera was one of the pioneers when it comes to college education online. When it started all courses were free and offered certificates if the taker has done tasks with a passing grade. Today not everything is free but still, there are tons of free courses that can help you to learn something new and to advance in your work or hobby.
Google is using the Coursera platform to deliver its courses to the audience and besides google a lot of academic professors from Princeton, Stanford, John Hopkins and many more are presently offering their course material.
 edX has evolved from MITx, MIT’s free initiative to place some free academic lectures from its classrooms free into the world. Since it was rebranded into edX it started including other big university names like Berkeley, University of Texas System, Harvard, and many more.
Since its infant days, edX has expanded and included many areas that it offers coursework from arts to science. Certificated today are mostly not free but course videos are, so if you care to learn and not wave certificates around this is a great place to do it.
edX has evolved from MITx, MIT’s free initiative to place some free academic lectures from its classrooms free into the world. Since it was rebranded into edX it started including other big university names like Berkeley, University of Texas System, Harvard, and many more.
Since its infant days, edX has expanded and included many areas that it offers coursework from arts to science. Certificated today are mostly not free but course videos are, so if you care to learn and not wave certificates around this is a great place to do it.
 Udemy has a little different approach to course material than previously mentioned websites. Teachers on Udemy are mostly people that are working in a given field. Programmers will teach programming, fitness instructors will teach training, etc.
There are vas variety of topics even on lifestyle, hobbies even gaming to more serious ones like software developing hardware, etc.
There are free courses but mostly are one-time purchases with unlimited access to course material and with frequent discounts udemy might be a good place to look if you can find anything interesting.
Udemy has a little different approach to course material than previously mentioned websites. Teachers on Udemy are mostly people that are working in a given field. Programmers will teach programming, fitness instructors will teach training, etc.
There are vas variety of topics even on lifestyle, hobbies even gaming to more serious ones like software developing hardware, etc.
There are free courses but mostly are one-time purchases with unlimited access to course material and with frequent discounts udemy might be a good place to look if you can find anything interesting.
 Alison is kind of Udemy if we are talking about course material and who is teaching, the difference however is that it has more free content and it is one of the rare websites on this list that has Language courses.
Courses vary from beginner level to more advanced ones.
Alison is kind of Udemy if we are talking about course material and who is teaching, the difference however is that it has more free content and it is one of the rare websites on this list that has Language courses.
Courses vary from beginner level to more advanced ones.
 Udacity was also one of the earlier websites to offer free courses, in today’s world it still has free material but there is also paying one.
The big difference from other competitors is that Udacity focuses mostly on programming, data science, and web development and it is very strong in this field. There are no courses about art. Music or similar, mostly IT stuff is covered here.
If this is something that interests you, make a free account and give it a go.
Udacity was also one of the earlier websites to offer free courses, in today’s world it still has free material but there is also paying one.
The big difference from other competitors is that Udacity focuses mostly on programming, data science, and web development and it is very strong in this field. There are no courses about art. Music or similar, mostly IT stuff is covered here.
If this is something that interests you, make a free account and give it a go.
 Codecademy is a website mainly focused on teaching you how to code. Pro plan is there but there are a lot of basic and free courses on the mentioned subject.
The curriculum is really wide covering Python, R, Java, JavaScript, SQL, Ruby, C#, C++, Swift, PHP, HTML, CSS and more so I am sure that if you are interested in coding this would be a pretty good place to find things.
Besides pure language coding courses site offers also, Cybersecurity, Web design, Data science, web development, Game Development, Mobile Development, and many more courses on provided subjects.
Codecademy is a website mainly focused on teaching you how to code. Pro plan is there but there are a lot of basic and free courses on the mentioned subject.
The curriculum is really wide covering Python, R, Java, JavaScript, SQL, Ruby, C#, C++, Swift, PHP, HTML, CSS and more so I am sure that if you are interested in coding this would be a pretty good place to find things.
Besides pure language coding courses site offers also, Cybersecurity, Web design, Data science, web development, Game Development, Mobile Development, and many more courses on provided subjects.
 Academic Earth has been built with one simple premise: Everyone deserves access to education.
Lead by this kind of mindset on Academic Earth you will find well, academic courses similar to ones found on edX and Coursera, but from mentioned sites here all courses are free and you will find only academic ones, there are no entrepreneur or expert courses here, just pure academic ones.
If you wish to see and learn something the way it is taught in Harvard, Berkeley, MIT, etc this is the place for you.
Academic Earth has been built with one simple premise: Everyone deserves access to education.
Lead by this kind of mindset on Academic Earth you will find well, academic courses similar to ones found on edX and Coursera, but from mentioned sites here all courses are free and you will find only academic ones, there are no entrepreneur or expert courses here, just pure academic ones.
If you wish to see and learn something the way it is taught in Harvard, Berkeley, MIT, etc this is the place for you.
 Khan academy is completely free and it is offering courses matching certain grades for children. It is offering courses for all 8 years of elementary school, math courses for high school and college with some coursework on topics like science, arts & humanities, reading, life skills, etc.
Despite not being on the same level as some university courses presented on other mentioned websites Khan Academy is a good place to learn a lot of basic skills that you could build upon later.
Khan academy is completely free and it is offering courses matching certain grades for children. It is offering courses for all 8 years of elementary school, math courses for high school and college with some coursework on topics like science, arts & humanities, reading, life skills, etc.
Despite not being on the same level as some university courses presented on other mentioned websites Khan Academy is a good place to learn a lot of basic skills that you could build upon later.
 EVE Online is one of the earliest MMO games out there but since its release, it is still actively developed and is receiving updates. This science-fiction Sandbox will offer space lovers everything they need and more. Large scale PvP, mining, pirating, etc. It can be daunting and complex for beginners but take your time to get familiar with its systems and you will be rewarded greatly with an immersive and complex game worth the time. Open PvP in some zones might not be everyone’s cup of tea and seeing only your ship might be a turn-off for some players, but if you do not mind these things give it a go. It is free to play with an item shop.
EVE Online is one of the earliest MMO games out there but since its release, it is still actively developed and is receiving updates. This science-fiction Sandbox will offer space lovers everything they need and more. Large scale PvP, mining, pirating, etc. It can be daunting and complex for beginners but take your time to get familiar with its systems and you will be rewarded greatly with an immersive and complex game worth the time. Open PvP in some zones might not be everyone’s cup of tea and seeing only your ship might be a turn-off for some players, but if you do not mind these things give it a go. It is free to play with an item shop.
 FF14 had a tough start, so tough that it was scrapped and destroyed and has been remade again and that idea was great. The game now is better than ever and at this time it is experiencing large players from other games surging into it. This on the rails fantasy MMO will offer you a great story and great leveling experience. It has a free trial where you can play the whole original game for free but if you wish to continue playing you will have to buy the expansion and pay a monthly subscription but the content is well worth the money.
FF14 had a tough start, so tough that it was scrapped and destroyed and has been remade again and that idea was great. The game now is better than ever and at this time it is experiencing large players from other games surging into it. This on the rails fantasy MMO will offer you a great story and great leveling experience. It has a free trial where you can play the whole original game for free but if you wish to continue playing you will have to buy the expansion and pay a monthly subscription but the content is well worth the money.
 Let’s be honest, not a single list of MMO games cannot be without a once greatest and most successful MMO ever made, World of Warcraft. But instead of me praising the game why it was the greatest and why you should play it and how great it is I am going to take a little different approach. I am going to recommend you World of Warcraft classic, yup, you read it correctly, classic. Now World of Warcraft is a retail game with a subscription service but with that one subscription you will be able to access three games in the World of Warcraft universe: World of Warcraft retail (standard game), World of Warcraft Classic (vanilla WOW without expansions offering you experience as it once was when it was released) and World of Warcraft the Burning Crusade classic (same as WOW classic but with the first expansion the Burning Crusade). Among all solutions, I would really urge you to play either WOW classic or WOW TBC classic simply for reason that they are far superior games in comparison to typical retail ones, but if you like easier game go for retail, it is included in the sub anyway.
Let’s be honest, not a single list of MMO games cannot be without a once greatest and most successful MMO ever made, World of Warcraft. But instead of me praising the game why it was the greatest and why you should play it and how great it is I am going to take a little different approach. I am going to recommend you World of Warcraft classic, yup, you read it correctly, classic. Now World of Warcraft is a retail game with a subscription service but with that one subscription you will be able to access three games in the World of Warcraft universe: World of Warcraft retail (standard game), World of Warcraft Classic (vanilla WOW without expansions offering you experience as it once was when it was released) and World of Warcraft the Burning Crusade classic (same as WOW classic but with the first expansion the Burning Crusade). Among all solutions, I would really urge you to play either WOW classic or WOW TBC classic simply for reason that they are far superior games in comparison to typical retail ones, but if you like easier game go for retail, it is included in the sub anyway.
 Guild Wars 1 was one of my favorite games and I sank a lot of times in it and once Guild Wars 2 came I must admit I was pleasantly surprised with it and I would recommend it highly. The base game is completely free to play with only expansion to be purchased and it is buy to play model without monthly fees. It has specific mechanics different from other games and interesting classes to try. The living world is a great feature of the game and it is still very strong with its player base.
Guild Wars 1 was one of my favorite games and I sank a lot of times in it and once Guild Wars 2 came I must admit I was pleasantly surprised with it and I would recommend it highly. The base game is completely free to play with only expansion to be purchased and it is buy to play model without monthly fees. It has specific mechanics different from other games and interesting classes to try. The living world is a great feature of the game and it is still very strong with its player base.
 This game is made for people who enjoy, love, and like Star Wars. Mechanically besides being able to have henchmen with you and space battles (which I do not really like how they are done) game itself does not offer anything special. Where it shines is in the story and overall Star Wars experience. If you look at this game as a single-player game with multiplayer dungeons you will have a great time, since the story is really good but sadly end game lacks in comparison.
This game is made for people who enjoy, love, and like Star Wars. Mechanically besides being able to have henchmen with you and space battles (which I do not really like how they are done) game itself does not offer anything special. Where it shines is in the story and overall Star Wars experience. If you look at this game as a single-player game with multiplayer dungeons you will have a great time, since the story is really good but sadly end game lacks in comparison.
 I am going to admit something here, I was not fond of the idea to make the beloved Elder Scrolls series into MMO, but in time I gave it a go and I am really glad I did. This game is great and it is getting better and better as time progresses. It is buy to play without monthly fees and basic game free, same as FF14 but without fees. It has a decent community and offers a really good Elder Scrolls experience and now it is packing Morrowind expansions and other great areas. Highly recommended for any Elder Scrolls fan.
I am going to admit something here, I was not fond of the idea to make the beloved Elder Scrolls series into MMO, but in time I gave it a go and I am really glad I did. This game is great and it is getting better and better as time progresses. It is buy to play without monthly fees and basic game free, same as FF14 but without fees. It has a decent community and offers a really good Elder Scrolls experience and now it is packing Morrowind expansions and other great areas. Highly recommended for any Elder Scrolls fan.
 This one is troublesome to recommend, on one side you have free to play games deeply inside Tolkien Lord of the Rings lore, on the other side, you have outdated graphics and some stupid item shop decisions like buys specific classes. But if you look past stupid item shop decisions and can live with playing free class in the game you will be pleasantly surprised. The game itself is surprisingly good, the story is great as expected from the game infused with lore taken from one of the best books series ever written, and the feeling when visiting iconic landscape is epic. But if I need to be real as I should, I would recommend this one to people appreciate good story and lore and ones that are fans of Lord of the Rings itself.
This one is troublesome to recommend, on one side you have free to play games deeply inside Tolkien Lord of the Rings lore, on the other side, you have outdated graphics and some stupid item shop decisions like buys specific classes. But if you look past stupid item shop decisions and can live with playing free class in the game you will be pleasantly surprised. The game itself is surprisingly good, the story is great as expected from the game infused with lore taken from one of the best books series ever written, and the feeling when visiting iconic landscape is epic. But if I need to be real as I should, I would recommend this one to people appreciate good story and lore and ones that are fans of Lord of the Rings itself.
 Neverwinter is a premium and licensed D&D MMO game and it is well strange. The free-to-play model of the game will let you enjoy it until you hit the end game, then you will have to shell real money if you want to be competitive but the journey until then is great. I would recommend it to D&D lovers and people that love to try other people's maps, yup you read it correctly. Neverwinter has a map editor making it one of a kind MMO game where you can create your own dungeons and post them for other players to play, this user-generated content makes it a very specific beast in this list, and for that feature alone it has my recommendation.
Neverwinter is a premium and licensed D&D MMO game and it is well strange. The free-to-play model of the game will let you enjoy it until you hit the end game, then you will have to shell real money if you want to be competitive but the journey until then is great. I would recommend it to D&D lovers and people that love to try other people's maps, yup you read it correctly. Neverwinter has a map editor making it one of a kind MMO game where you can create your own dungeons and post them for other players to play, this user-generated content makes it a very specific beast in this list, and for that feature alone it has my recommendation.
 Another one of the older titles, Tera will offer you nor depth nor anything new in terms of leveling, quests, or end game except… the COMBAT. This is maybe the greatest MMO Combat game ever created and it is quite fascinating that even after so many years no other game has managed to create a better combat system than one of Tera. If you enjoy action combat and like some specific aesthetics Tera is a game for you.
Another one of the older titles, Tera will offer you nor depth nor anything new in terms of leveling, quests, or end game except… the COMBAT. This is maybe the greatest MMO Combat game ever created and it is quite fascinating that even after so many years no other game has managed to create a better combat system than one of Tera. If you enjoy action combat and like some specific aesthetics Tera is a game for you.
 Albion is a sandbox game with open-world PvP and building mechanics where you can build your own forest, house, etc. You know, sandbox stuff, including a lot of crafting and well, other sandbox stuff. If you want great quests and some occasional play then skip Albion, this game is made for a more hardcore player base not being afraid to die and spend some time crafting and going through the economy. The best comparison might be with EVE but in fantasy settings.
Albion is a sandbox game with open-world PvP and building mechanics where you can build your own forest, house, etc. You know, sandbox stuff, including a lot of crafting and well, other sandbox stuff. If you want great quests and some occasional play then skip Albion, this game is made for a more hardcore player base not being afraid to die and spend some time crafting and going through the economy. The best comparison might be with EVE but in fantasy settings.
 Black Desert is also a sandbox game but different from Albion, here you can organize and hire a workforce and send them to different nodes on a map to harvest resources and build an economy while you are on some epic adventure. Housing is also included but you can buy already made houses instead of making your own in the world. Combat is a game that comes very close to Tera combat and it is very enjoyable. The end game is money sink and PvP based so be careful when choosing this one.
Black Desert is also a sandbox game but different from Albion, here you can organize and hire a workforce and send them to different nodes on a map to harvest resources and build an economy while you are on some epic adventure. Housing is also included but you can buy already made houses instead of making your own in the world. Combat is a game that comes very close to Tera combat and it is very enjoyable. The end game is money sink and PvP based so be careful when choosing this one.
 If you like occult and supernatural with new world order themes and conspiracy theories, Secret World Legends is the game for you. Somewhat little clunky its setting and story really set it apart in many many ways. It has semi-action combat and it is free to play with item shop but all the content can be experienced for free. Recommended for fans of deeper gameplay and horror lore.
If you like occult and supernatural with new world order themes and conspiracy theories, Secret World Legends is the game for you. Somewhat little clunky its setting and story really set it apart in many many ways. It has semi-action combat and it is free to play with item shop but all the content can be experienced for free. Recommended for fans of deeper gameplay and horror lore.
 When I said no MMO list can be without World of Warcraft, it also cannot be without Runescape, one of the oldest games it was revamped with newer mechanics and graphics, free to play all the way and you can also pick old school Runescape if you really want to go all the way on a nostalgia trip. I would recommend a newer one for newer players, the game offers a great story and unusual quests infused with puzzles and interesting storylines. If you like really good quest design without fetch and grind quests along with interesting story this is a game for you.
When I said no MMO list can be without World of Warcraft, it also cannot be without Runescape, one of the oldest games it was revamped with newer mechanics and graphics, free to play all the way and you can also pick old school Runescape if you really want to go all the way on a nostalgia trip. I would recommend a newer one for newer players, the game offers a great story and unusual quests infused with puzzles and interesting storylines. If you like really good quest design without fetch and grind quests along with interesting story this is a game for you.
 Last on my list would be AION, a very interesting game made also a long way back, but the fact that is completely free with the cosmetic shop will make it as one to recommend since you can experience the whole game for free. It has some limited flying mechanics in it and later game zone are open PvP zones, story is interesting and leveling process is enjoyable. Also game itself is not really easy and if not careful you can get yourself in danger quite quickly. Recommended for old-school feeling.
Last on my list would be AION, a very interesting game made also a long way back, but the fact that is completely free with the cosmetic shop will make it as one to recommend since you can experience the whole game for free. It has some limited flying mechanics in it and later game zone are open PvP zones, story is interesting and leveling process is enjoyable. Also game itself is not really easy and if not careful you can get yourself in danger quite quickly. Recommended for old-school feeling.
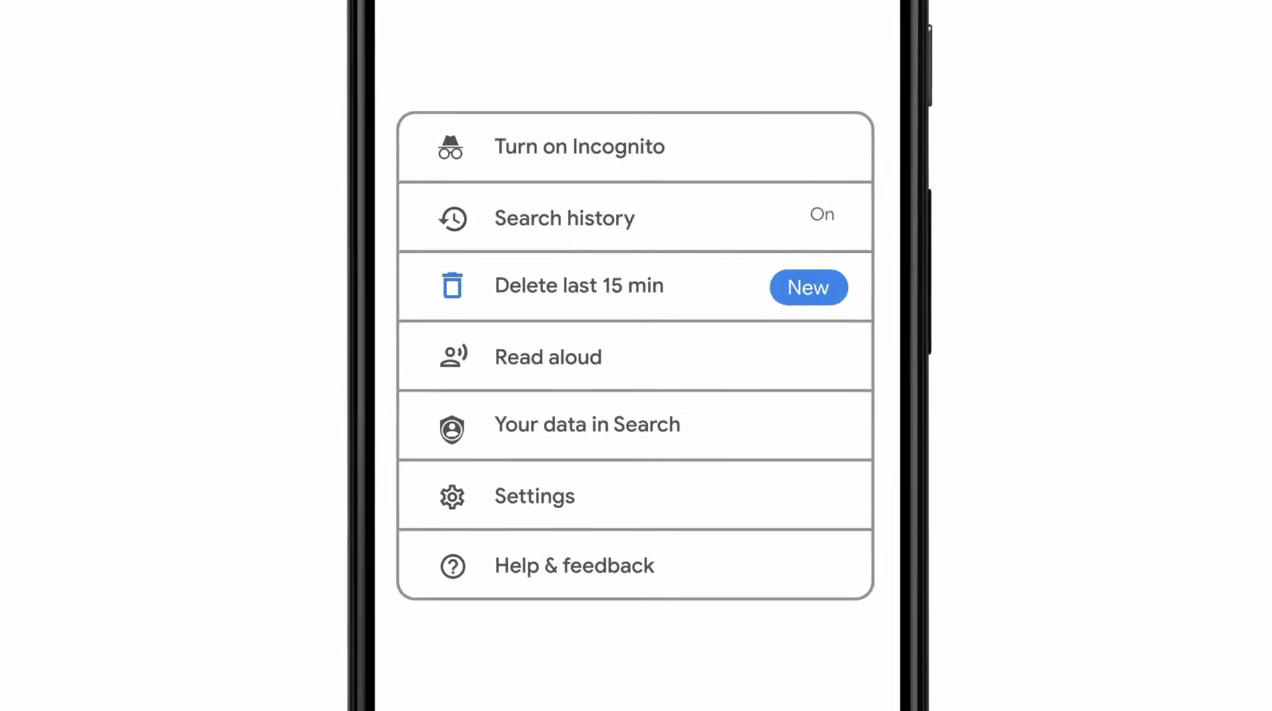 As previously announced by Google feature to quickly delete the last 15min of browsing history via one button is rolling out now.
For now, only Apple users will be available to use this feature but the Android update is scheduled for later this year, a strange move by Google but it is what it is.
For anyone who is unfamiliar with this feature, basically, Google wants a quick way to remove the last 15min of browsing history as a supposedly stated request to make deleting browsing history much easier.
Google came up with this idea so you can keep the previous history intact but remove just 15min time frame, no additional explanation was given on why 15 but I presume it is some round number that came up as the middle one with research, read telemetry info.
Using quick delete requires being signed into Search with a Google account. Users can access the option by simply tapping on the avatar icon to access the settings then choosing "Delete last 15 minutes."
As previously announced by Google feature to quickly delete the last 15min of browsing history via one button is rolling out now.
For now, only Apple users will be available to use this feature but the Android update is scheduled for later this year, a strange move by Google but it is what it is.
For anyone who is unfamiliar with this feature, basically, Google wants a quick way to remove the last 15min of browsing history as a supposedly stated request to make deleting browsing history much easier.
Google came up with this idea so you can keep the previous history intact but remove just 15min time frame, no additional explanation was given on why 15 but I presume it is some round number that came up as the middle one with research, read telemetry info.
Using quick delete requires being signed into Search with a Google account. Users can access the option by simply tapping on the avatar icon to access the settings then choosing "Delete last 15 minutes." 
