Runtime Error r6034 is one of the most commonly occurring errors. This error usually arises in Windows Vista and Windows 7.
The message that appears to the user states ‘An application has made an attempt to load C runtime library incorrectly, please contact the support team for more information’.
As the message suggests, this problematic error occurs simply because an application attempts to load the C runtime library without a manifest.
 Error Causes
Error CausesRuntime Error r6034 occurs when the system compiler fails to compile the working application. While this is the primary reason, there are some other conditions that trigger Runtime Error r6034 which are outlined below.
There are several other reasons that may trigger Runtime Error r6034 that are beyond the scope of this article. Regardless of what triggers this error, it is crucial to ensure that it is fixed as soon as possible.
There are several ways to deal with Runtime Error r6034. However, one of the most effective ways is listed below as follows.
After restarting your computer, you will notice that the Runtime Error r6034 has been removed. If this approach fails to deliver the desired results, it is advised to follow the steps listed below.

 Check cables
Check cables‘An error is preventing the photo or video from being displayed’ Error code 0x80010108
 Error Causes
Error Causes“Your PC ran into a problem and needs to restart. We’re just collecting some error info, and then we’ll restart for you. (100% complete) If you’d like to know more, you can search online later for this error: DRIVER_IRQL_NOT_LESS_OR_EQUAL (wrUrlFlt.sys)”The iaStorA.sys file is a software component that’s related to the Intel Rapid Storage Technology by Intel. It is a software solution supported by Intel Smart Response Technology which allows the PC to communicate with the hardware as well as externally connected devices. The Intel Rapid Storage Technology enables the Peripheral Component Interconnect Express or PCIe storage support, serial ATA RAID or Redundant Array of Independent Disks 0, 1, 5, and 10 support, and the PUIS or power-up in standby is also supported. To resolve this kind of BSOD error, you have to update, roll back or fresh-install the problematic driver. Refer to the options laid out below for detailed instructions.
FoxTab Toolbar is a browser hijacking toolbar add-on for IE, Firefox, Chrome, and Opera browsers that claims that it allows you to access your favorite sites faster, and improving your overall search and browsing experience. 1-click access to search results, most popular websites, and web services directly from our Foxtab browser toolbar.
Fox tab will integrate itself into your browser, modifying the search engine, welcome page, and new tab. This toolbar may change some browser settings, display unwanted ads, and sometimes displays additional ads from its ad sponsor. Some of the settings that this toolbar changes can lower the security of your browser.
Upon installation the toolbar ads scheduled tasks in Windows, allowing it to run with your browser every time, and to automatically update itself. Several anti-virus programs have flagged this software as Malware and therefore it is classified as a browser hijacker and recommended for optional removal.
There is a lot of software on the market today, but from time to time we discover something extraordinary and unique worth sharing and today we have a threat for you. Ventoy is a tool that will help you with system reinstallations and system maintenance once and for all.
If you are a computer user that has multiple operating systems or you are installing and maintaining different hardware via different OS there is a high chance that you have multiple USB sticks with different operating systems on them.
Now the problem with that is that there are probably too many unlabeled sticks around or you do not have enough so you keep making system USBs depending on which one you might need.
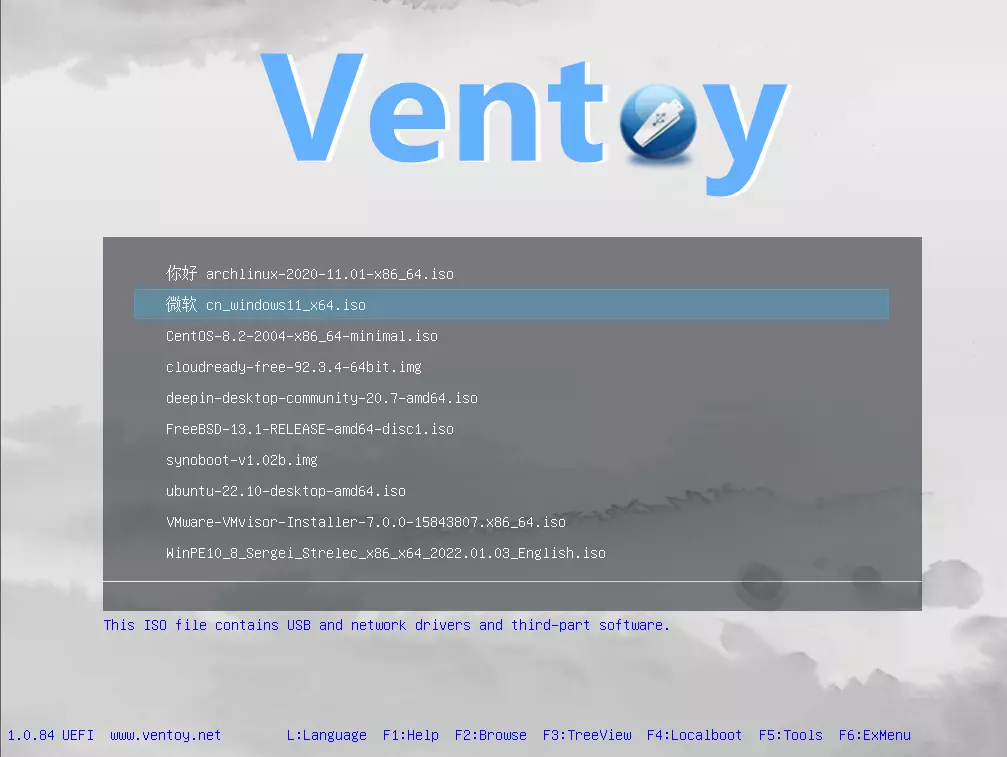
Ventoy solves all of these problems by letting you have as many operating systems images as your USB has capacity. The only thing you need to do is get the software here: https://www.ventoy.net/en/index.html and make a USB with it, then you can freely just copy your ISO images onto the USB and once it is inserted into the computer you will be given a menu to choose which one you would like to start with, simple as that.
2021 is nearing toward the end and with just a couple of days remaining in this year, we are happy to look forward to the next year. So in large anticipation of what will next year bring us, we are taking a good design look at this one and making a list for you of what graphic design software you should learn and use in the upcoming 2022.
 Before we dive into it in more detail and predictions please be aware that this article is based upon my personal opinion drawn from the research of current trends and standards. That being said let's dive right into details.
Before we dive into it in more detail and predictions please be aware that this article is based upon my personal opinion drawn from the research of current trends and standards. That being said let's dive right into details.
Whether you like it or not, Adobe has cemented itself with its flagship application Photoshop and how things are looking this situation will not change any time soon. Photoshop is an extraordinary pixel manipulation software that has the ability to work with both animations and vector graphics as well making it a great single application for all-around design needs. It has been industry-standard design software for the web, print, and all other kinds of design all over the globe and this will not change in near future. With its constant updates and expansion of its abilities, this is a must-have tool in your design tool belt. If you are looking to find work as a designer you will have to know how to work with photoshop.
Many will tell you that is photoshop for raster graphics, the illustrator is for vectors. First started as illustrator 88 on Mac right away it took first place for vector graphics from FreeHand and it continued on its path of vector dominance. After some time and more integration with photoshop Adobe managed to overthrow Corel Draw as well winning the title for best vector editing software with illustrator. Same as with photoshop, if you are planning to work in a serious industry you will need to know the illustrator.
We are still in Adobe train and it is moving hard, InDesign is graphic design software aimed for paper publications. If you need to create and prepare any kind of professional publication for printing InDesign is the application to go to. With its specific print aimed features it is a must-have for any graphic designer.
Once the king of vector and print design but dethroned by Adobe Corel Draw still has some punches to stay relevant in the field. With some cool features like symmetry and long shadows, it stands out from its competitors for its ease of use. Corel was always focused on easy to learn, and difficult to master and it is still following that kind of thinking. Granted not many employers will require you to be a master of Corel Draw but some of them will request that you are familiar with the application. One of perhaps the greatest advantages of Corel over Adobe is not locking you into a subscription making Draw suit a great choice for freelancers and designers that want to own software, not rent it.
The first software from Affinity was Photo, made as a cheap version one-time purchase competitor for photoshop. Later it has released Designer, also a one-time purchase competitor for illustrators. If we are going to take a good look into a feature for feature comparison, both Adobe and Corel will win over Affinity but if we take a look at a price that is a one-time purchase Affinity will win over easily. Priced only at $54.99 it is a steal, and taking into account that many designers will not require any very advanced features found in Corel or Adobe applications Affinity is the way to go.
Speaking of price, nothing beats free, and both Inkscape and GIMP are completely free. offering very decent and competitive features applications will require you to get used to their own specific UI and workflow, but once you get a grasp of them, you will be able to do most design work in them. One of the downsides of using these free open source apps is their limited export options but if all that is required from you is to deliver a typical SVG, JPG, EPS, PNG, or PDF file you are good to go.
Free with basic functionality with the option to purchase more advanced features Colorcinch is a great application if you are on quickly developing and creating graphics for social media posts. Add quickly text or filters, quickly do the color adjustment and save for social apps. The application also within its basic boundaries can work directly on the website without you requiring to even install it making it one of a kind. Go try it at the official site and enjoy yourself.
If you have followed the graphic design scene you will notice that nothing has changed and it will not change in near future. This just speaks about how much industry is defined and how little change is there over time. I advise if you can to get and learn adobe suite since it is industry standard and is required from almost every employer today. Rest applications on the list are great alternatives and can bring you income and offer you a way to finish your project.
“SYSTEM [DRIVER] USB AUDIO DEVICE An audio stream is currently in use [DRIVER] Legacy Kernel Caller.”Step 2: The next thing you have to do is remove all the external hardware connected to your computer. In this step, you have to disconnect external hardware from your computer. Based on reports from users who experienced the same issue, the “TV card” is the culprit so make sure you remove that one. Once you’ve removed it, open Command Prompt and run the “powercfg –requests” command again and you’ll see that the “Legacy Kernel Caller” will no longer be on the list. In addition, your computer will get into its regular sleep mode once the hardware is removed. Once you do that, the driver gets hung and won’t release the power request despite being used. Step 3: Try using the request override option The powercfg command also offers a request override option which allows users to disable the requests from applications and services to wake the computer from sleep mode. To run this command, simply open Command Prompt with admin privileges. After you open Command Prompt, type the following command and hit Enter to disable requests from applications and services that causes the computer to wake from sleep state.
Powercfg -requestsoverride Driver "Legacy Kernel Caller" SystemStep 4: Check the streaming and media applications You also have to check if your computer is running an audio or video service in the background. In such cases, your computer won’t be able to go to sleep mode if these services are running in the background. You might have noticed that when you play a video or audio, your computer never goes to sleep. And if you have put it to sleep in between watching the video, then it’s probably why your computer is waking up. Thus, you have to stop these services. Step 5: Check the devices that can wake your computer If you didn’t see the Legacy Kernel Caller in the result after you execute the ”powercfg –requests” command, then you can try to execute the following command instead.
powercfg –devicequery wake_armedAfter you enter this command, it will give you a list of all the devices that can wake your computer. So if there is anything other than the mouse, keyboard, touchpad, you have to check the power configuration of that device. To do that, go to the Device Manager and disable the device’s “Allow this device to wake the computer” option in its Properties Step 6: Check the Sleep Advanced Settings
ComputerHKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlStorageDevicePolicies