 So if you ever wanted to learn about photoshop, maya, substance, unreal engine, or some general skills like sketching, drawing, etc. Now is the perfect time to level up your skills. Drop to the artstation website and start learning today!
So if you ever wanted to learn about photoshop, maya, substance, unreal engine, or some general skills like sketching, drawing, etc. Now is the perfect time to level up your skills. Drop to the artstation website and start learning today! One of the selling points of Windows 11 was the ability to run Android apps natively in it without the need for any third-party software. It is not a big surprise that even after its release Microsoft is evolving and expanding Windows 11 and its features.
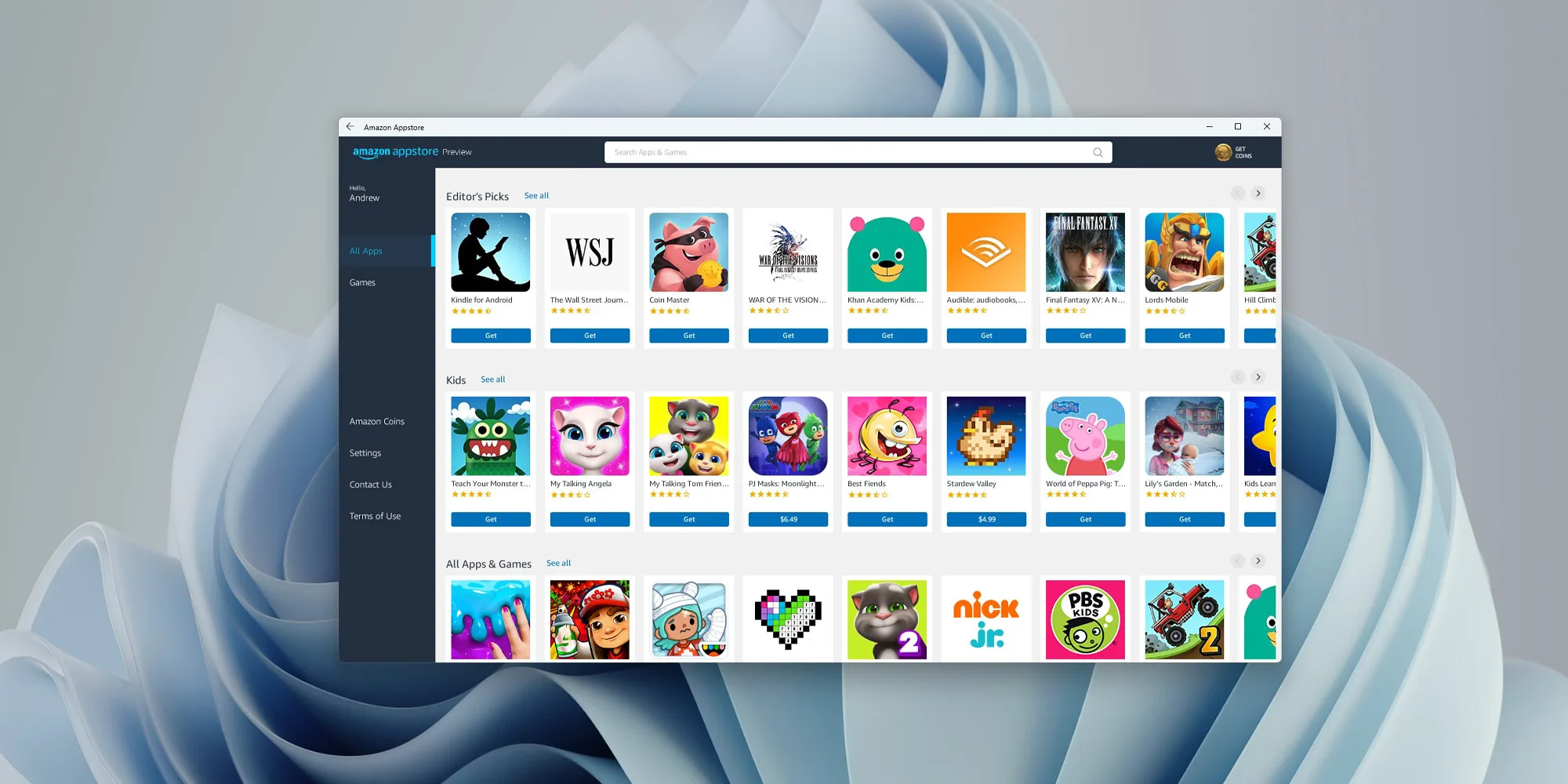
Microsoft is now rolling out an update for the Windows Subsystem for Android on the Dev Channel of the Windows Insiders program. The new version upgrades the core operating system from Android 11 to Android 12.1 (also known as Android 12L), which means the new system and app features in Android 12 and 12.1 are now available on Windows for the first time. However, not the new features in those updates apply to the modified version that runs on top of Windows. For example, one of the main improvements in 12.1 was a dual-pane notification panel for larger screens, but Android app notifications on Windows just show up in the Windows notification panel.
The upgrade also improves how Android apps integrate into Windows. The Windows taskbar will now show which Android apps are currently using the microphone, location, and other system services — similar to many native Windows applications. Toasts messages (the small popups that some apps use for temporary messages) are now displayed as Windows notifications, and the titlebar on Android apps will use the current activity name for the title.
Full changelog
The new update is limited to Windows Insiders for now, but once Microsoft fixes all the bugs, it should start rolling out to everyone on Windows 11 that has the Android Subsystem enabled.

 So if you ever wanted to learn about photoshop, maya, substance, unreal engine, or some general skills like sketching, drawing, etc. Now is the perfect time to level up your skills. Drop to the artstation website and start learning today!
So if you ever wanted to learn about photoshop, maya, substance, unreal engine, or some general skills like sketching, drawing, etc. Now is the perfect time to level up your skills. Drop to the artstation website and start learning today!  Restart graphic driver
Restart graphic driverUsers when upgrading to Windows 10 operating system from Windows 8/8.1 or Windows 7, often encounter error code 8007002c. This error occurs when there’s an attempt made in performing an overall clean boot procedure. During the installation process, it will reach a certain maximum limit, for instance, 75%, and then reverts to its original state. Sometimes, after installation, users will encounter a black screen issue and there is no cursor visible.
 Error Causes
Error CausesMisconfigured system files that create registry errors within your operating system normally cause error code 8007002c in Windows 10. This registry error happens when there are new programs being installed over old ones without the old programs uninstalled entirely. Another possible cause could be from some malicious software like spyware, adware, and viruses.
Caution: The following steps are complicated. The risk of being in a no-boot situation or data loss might be encountered. It would be best to be supervised by an experienced user, especially in using the command line.
In order to fix Error code 8007002c occurring in Windows 10 upgrade, you can follow this step-by-step manual repair method. Once the repair method is correctly executed, users will most likely quickly resolve issues such as the Error code 8007002c and be able to upgrade to Windows 10 operating system smoothly.
However, in such cases where there are complex instructions and thus need an expert, seek help from a Windows professional. You may also want to consider making use of an automated tool whenever needed.
There are several ways to fix Error code 8007002c, but here are the most effective and efficient methods:
To be able to download and install the necessary updates, you may use the force Windows Update tool. See below for the steps:
NOTE: Don’t forget to hit Enter after every command.
Dism /Online /Cleanup-Image /CheckHealth
Dism /Online /Cleanup-Image /ScanHealth Dism /Online /Cleanup-Image /RestoreHealth
Here’s how you can input a machine name:
Another reason why Error code 8007002c occurs is when there’s a defective and wrongly installed memory chip. Try using the Windows Memory Diagnostic to diagnose if there are RAM Issues.
One more possible cause why Error code 8007002c occurs is due to third-party software. To fix this error, you can try booting up your device with Selective Startup -- a boot type where you can load a limited set of startups and services.
Can’t seem to put up with the long and technical manual repair process? You can still fix this error by downloading and installing a powerful automated tool that will surely get the job done in a jiffy!
“This site can’t be reached, The webpage at [website URL] might be temporarily down or it may have moved permanently to a new web address, ERR_QUIC_PROTOCOL_ERROR”This kind of error message pops up when the URL is down. However, if you are certain that the site is not down and you’re still seeing this error message, then troubleshoot further using the suggestions given below.
 ⊞ WINDOWS + N - notification panel
⊞ WINDOWS + W - News and Interests feed
With the News and Interests feed, Windows 11 offers users the ability to check the latest news, the weather, and more without opening a browser window.
⊞ WINDOWS + Z - Snap Layout
Instead of the usual two windows snapping capability, Windows 11 allow users to snap their windows in a three-column layout. Users can access this by pressing Windows Key and Z to access the Snap layout.
⊞ WINDOWS + PRT SCN - taking screenshots
This one isn’t exactly new, but pressing the Windows Key and Print Screen will automatically capture the entire screen and save a copy of the image on your PC. Once the screen flashes, you will know that the screenshot has been taken, after which you can find the file saved under your Pictures folder in a subfolder called Screenshot.
⊞ WINDOWS + C - Microsoft Teams chat
Microsoft Teams app, the service allows anyone with a Microsoft account to quickly start a chat using the Windows + C shortcut.
⊞ WINDOWS + N - notification panel
⊞ WINDOWS + W - News and Interests feed
With the News and Interests feed, Windows 11 offers users the ability to check the latest news, the weather, and more without opening a browser window.
⊞ WINDOWS + Z - Snap Layout
Instead of the usual two windows snapping capability, Windows 11 allow users to snap their windows in a three-column layout. Users can access this by pressing Windows Key and Z to access the Snap layout.
⊞ WINDOWS + PRT SCN - taking screenshots
This one isn’t exactly new, but pressing the Windows Key and Print Screen will automatically capture the entire screen and save a copy of the image on your PC. Once the screen flashes, you will know that the screenshot has been taken, after which you can find the file saved under your Pictures folder in a subfolder called Screenshot.
⊞ WINDOWS + C - Microsoft Teams chat
Microsoft Teams app, the service allows anyone with a Microsoft account to quickly start a chat using the Windows + C shortcut. Error Code 0x80072ee7 is an error code that is most commonly associated with Windows 10 and the use of the Windows Store. Several things can cause this error, which has been present as an error message in Windows 10 and all the way back through Windows 8.
Common symptoms include:
Fortunately, there are several simple methods that can be used to attempt to resolve Error Code 0x80072ee7 on your Windows machine. These methods don’t require advanced computer knowledge or familiarity with high-level tools, so the average user should be able to complete them without help. However, if you feel like you need assistance in resolving Error Code 0x80072ee7, always contact a qualified Windows repair technician who can assist you.
 Error Causes
Error CausesThere are four basic things that can cause Error Code 0x80072ee7 to appear on a Windows device. The first is that the connection to the Internet is limited in some manner, either due to a system or equipment error. Secondly, some parts of the update components could be missing. Next, an error within the DNS can be a cause. Finally, having any kind of compatibility errors on the machine (for example, between the antivirus software that you run and the Windows Update tool) can lead to the appearance of Error Code 0x80072ee7.
There are a few different methods that you can try in order to resolve the appearance of Error Code 0x80072ee7 on your Windows machine. These are fairly simple to complete, but if you do not feel confident in your ability to carry them out successfully, you may want to get in touch with a qualified computer repair technician to help you.
Here are the best methods to employ as you seek to resolve Error Code 0x80072ee7 on your Windows device:
Make sure that you are able to connect to the Internet by visiting several common sites like Google in order to ensure that your issue is not related to your Internet service provider or the equipment that you are using to access the Internet.
If you believe that your DNS connection may be the problem, you can change the specific DNS that you are using to one that is provided by Google. This can resolve any conflicts that may occur because of the IP address detected on your device. In order to do this, simply follow these steps:
Once these steps are complete, you can reattempt to connect to the Windows Store. You may need to restart your computer before connecting.
Microsoft has created a great tool that can automatically scan your computer for a number of common errors and attempt to fix them as they are encountered. This can be downloaded directly from the Windows site and can be used to try to fix not only Error Code 0x80072ee7 but also many other error messages that may pop up on your computer.
After you have run the Fix It tool, it is always a good idea to restart your computer to allow any changes that have been made to fully take effect.
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise, download and install a powerful automated tool.
“0xC1900209, Incompatible software is blocking the upgrade process. Uninstall the application and try the upgrade again.”This error message comes under the umbrella of the Windows 10 pre-upgrade validation using Setup.exe. And for you to identify the incompatible app, you need to grab a Windows 10 install image using the Windows Media Creation tool to download the suitable Windows 10 version and mount it. After that, execute the setup.exe file that’s located in the root folder of the Windows 10 install image. Once you execute the setup file, the upgrade wizard will give you a list of incompatible apps. Once you have determined which software is not compatible with the Windows Update, there are two options you can try to resolve the Windows Update error 0xC1900209 – you can either try to update the conflicting software or uninstall it. For more details, follow the given options below.