Having any kind of hardware malfunction is not a pleasant place to be. Even a minor malfunction like a broken key on a keyword can introduce certain bad feelings, frustration, and difficulty in working.
So, what are your options when the dreaded key on the keyboard breaks? From my point of view, there are three options that could be accomplished in order to continue working.
Yes, the best and most expensive solution, just bite the bullet and buy a new working one.
So you broke some key, if you can replace it with another key which you do not use, this option will work only tho if the broken key is not Space bar, enter or similar with specific shape and size.
use Windows power tools to remap key function to another working key
There you go, three options to continue working with a broken key on the keyboard.

“Shell Infrastructure Host has stopped working. A problem caused the program to stop working correctly. Please close the program”.This error indicates that the Shell Infrastructure Host or SiHost.exe process that is used for handling graphical elements, has crashed. And to fix this error, there are several options you can check out. You can try to reinstall the Microsoft Redistributable Packages or run a System File Checker scan. In addition, you can also use a new Guest Account or troubleshoot the problem in a Clean Boot State.
Social media is here to stay it seems, from Facebook, Instagram, Twitter, etc each site has its users and its rules. Companies, bloggers, public figures, and people, in general, are using them on a daily basis and some are posting cool ads, nice graphics, videos, and many more in order to gain followers or just to share something that they think is worth.
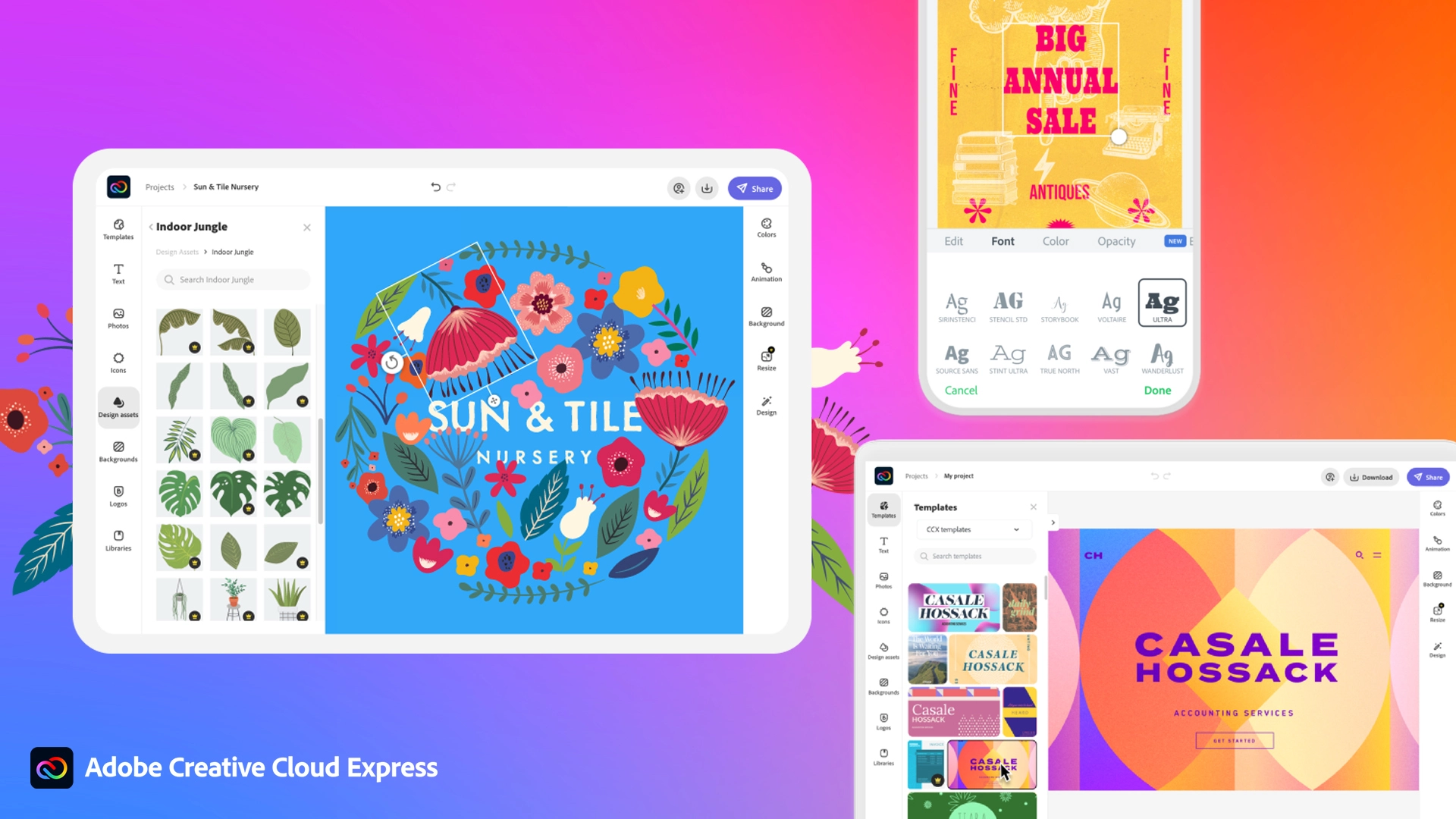
Making your post look good is somewhat essential if you plan on reaching a larger audience and Adobe's Express aims to fill that gap. It is the latest Adobe product that is purposely made for graphic and video creation for social media.
Adobe is well known in the world of professional design in all spheres like print, web, and motion, with this application, they want to take over social media design with Express. The direct competitor to Spark and canva, Express is filled with high-quality adobe templates and some great stuff found in photoshop like automatic background removal which gives it an edge over other applications.
The good thing about Express is that there is a completely free version and premium, like its competitors but with some benefits that clearly show that Adobe is determined to place its application on top of the game. The free plan includes:
For 10 USD per month of 100 USD prepaid annual fee, you get a premium plan that includes:
The application itself is incredibly easy to learn and to work with and literally, anyone can pick it up and start creating immediately. No matter are you just starting with social media or using Canva or Spark, give Express a go, make a free account and try it, I guarantee that you will find some features amazing, and its ease of use relaxing.
 If you are about to install Windows 10, then during the installation process, your computer boots into the Install and Configure Windows 10 screen with Cortana that assist you during the setup. Once you reach the last page which is “Choose privacy settings for your device”, you will see the Advertising ID of your computer. Under the Advertising ID, you have to disable or toggle off the “Apps can use advertising ID to provide more personalized advertising in accordance with the privacy policy of the app provider” option. After you disable it, click on the Accept button to proceed with the installation. After that, the copy of your Windows 10 you are using will have the Advertising ID disabled by default.
If you are about to install Windows 10, then during the installation process, your computer boots into the Install and Configure Windows 10 screen with Cortana that assist you during the setup. Once you reach the last page which is “Choose privacy settings for your device”, you will see the Advertising ID of your computer. Under the Advertising ID, you have to disable or toggle off the “Apps can use advertising ID to provide more personalized advertising in accordance with the privacy policy of the app provider” option. After you disable it, click on the Accept button to proceed with the installation. After that, the copy of your Windows 10 you are using will have the Advertising ID disabled by default.
 Error Causes
Error Causes“Something went wrong You can contact Microsoft support for help with this error. Here is the error code 0xa0000400.”As you know, keeping your computer up to date with all the Windows Updates is important and is imperative especially if you are experiencing a couple of issues like the Windows Upgrade error 0xa0000400. At the time of writing, there is no specific cause that has been found for this error. However, there are some potential fixes that might help you. You can try to recreate the Windows 10 installation USB and get the ISO files or you could also get a newer version of the Windows Media Creation Tool, or turn off your internet connection at a specific time or run the Windows Update troubleshooter. For more details, refer to the options given below.
 Error Causes
Error Causes