There are times when you encounter some issues while your Windows 10 computer. One of the errors you can encounter in the update process is the “Something went wrong, error code 0x8007042B”. This kind of error might be caused by several reasons and it could also pop up in lots of cases like upgrading to a new feature update or a new build using the Media Creation tool or Windows Update Assistant.
There are times when the Windows Update error code 0x8007042B is followed by another error code like 0x2000d. Whatever the extra error code that follows, the core issue still remains the same. To resolve the problem, here are some options that could help. And while going over these troubleshooting tips, you have to keep clicking the Update button right after you carry out a troubleshooting option.
Option 1 – Try to restart the Background Intelligent Transfer Service
The Background Intelligent Transfer Service or BITS is a part of the Windows Update service and is the one that manages the background download of Windows Update, as well as scans for new updates and so on. And if Windows Update is experiencing some problems, you can try restarting BITS but make sure that you have admin privileges to do so.
- Tap the Win + R keys to open the Run dialog box.
- Next, type “services.msc” in the field and hit Enter to open Windows Services.
- From the list of Services, look for the Background Intelligent Transfer Service and double-click on it to open Properties.
- After that, you need to set the Startup type to “Automatic (Delayed Start) and click on Apply.
- Now click the Stop button to stop BITS and then click the Start button to restart the service.
- Click OK to save the changes made and then restart your PC.
Option 2 – Try creating Windows 10 ISO media
In this option, you will have to create a Windows 10 bootable media and use it to install the latest Windows 10 version. The most user reported that this option works and the reason why it does have something to do with the Windows Update client since the Windows Updates downloaded from the regular Windows Update client seems to create issues such as the Windows Update error code 0x8007042B. However, issues like this one don’t occur when the very same Windows Updates are downloaded and installed via an ISO file. Take note that when using a Windows ISO file, you will be asked to choose what you want to do with the previous settings and apps. A lot of users opted for the “Not to keep the old Windows settings” option which has resolved the issue. So if you want to keep the previous settings then you must try to update Windows first while keeping the old settings. However, if it doesn’t work, you have to try installing the latest version of Windows without keeping the previous settings.
- Click this link and then click the Download Tool Now button.
- Next, click the “Use the tool to create installation media (USB flash drive, DVD, or ISO file)…” option and follow the next given instructions on the screen.
- Now select the ISO file option in step 5.
- After that, you should now have an ISO file.
- Next, go to the location where you’ve downloaded the ISO file.
- Then right-click on the Windows 10 ISO file and select the Open with option and then select File Explorer.
- Now click on “setup.exe” and follow the next instructions that appear on the screen. When asked, you have to select either the Nothing (clean install) or the Keep personal files only option. Take note that you must not select the “Keep personal files, apps, and Windows settings since it doesn’t really work.
Option 3 – Run the DISM tool
You can run the DISM tool as well to help fix the error code 0x8007042B during Windows Update. Using this built-in tool, you have various options such as the “/ScanHealth”, “/CheckHealth”, and “/RestoreHealth”.
- Open the Command Prompt with admin privileges.
- Then type in the following commands and make sure to hit Enter right after you type each one of them:
- Dism /Online /Cleanup-Image /CheckHealth
- Dism /Online /Cleanup-Image /ScanHealth
- exe /Online /Cleanup-image /Restorehealth
- Do not close the window if the process takes a while as it will probably take a few minutes to finish.
Option 4 – Perform a System File Checker scan
The SFC or System File Checker scan could detect and automatically repair damaged system files that could be causing the Windows Update Error 0x8007042B to appear. SFC is a built-in command utility that helps in restoring corrupted files as well as missing files. It replaces bad and corrupted system files with good system files. To run the SFC command, follow the steps given below.
- Tap Win + R to launch Run.
- Type in cmd in the field and tap Enter.
- After opening Command Prompt, type in sfc /scannow and hit Enter.
The command will start a system scan which will take a few whiles before it finishes. Once it’s done, you could get the following results:
- Windows Resource Protection did not find any integrity violations.
- Windows Resource Protection found corrupt files and successfully repaired them.
- Windows Resource Protection found corrupt files but was unable to fix some of them.
Option 5 – Run the Windows Update Troubleshooter
You might also want to run the Windows Update Troubleshooter as it could also help in fixing Windows Update Error 0x8007042B. To run it, go to Settings and then select Troubleshoot from the options. From there, click on Windows Update and then click the “Run the troubleshooter” button. After that, follow the next on-screen instructions and you should be good to go.
Option 6 – Contact Microsoft Support for assistance
If you’re at your wits’ end in trying to update your Windows 10 computer, you should consider contacting Microsoft Support for help as they can offer you various options that would make fixing Windows Update Error 0x8007042B a lot easier and faster.
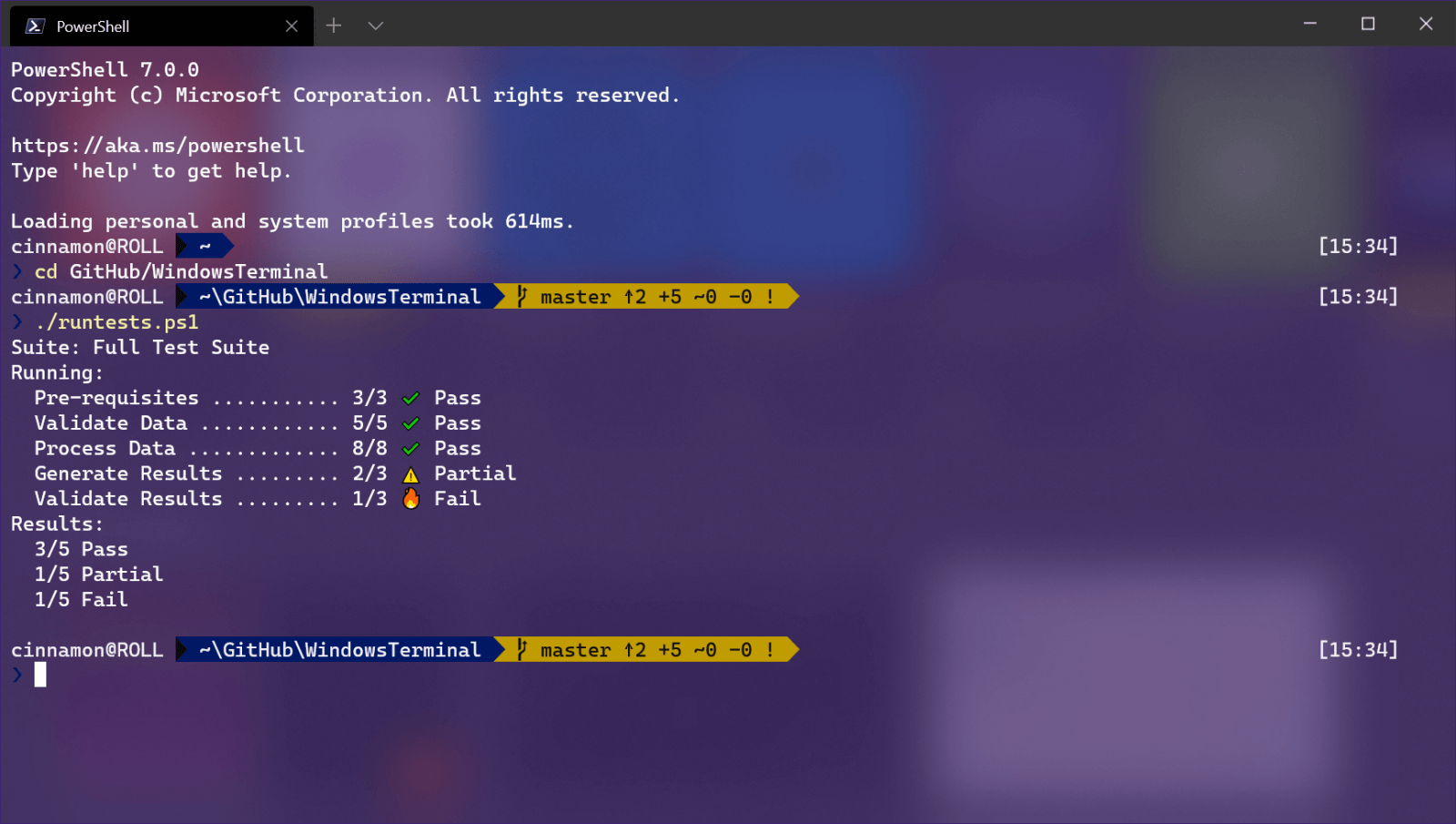 Windows Terminal is a new free Microsoft terminal sort of application. When you open either Power Shell or Command Prompt in Windows they will be opened in different windows, and if you want several of each you will have several windows of each on your screen.
Windows Terminal is a new free Microsoft terminal sort of application. When you open either Power Shell or Command Prompt in Windows they will be opened in different windows, and if you want several of each you will have several windows of each on your screen.
 This is not the first time that Intel is trying to enter the GPU field but its adventures so far were, well let us agree not so good. All of that is hoping to be changed with the upcoming ARC GPU. The first generation of Arc graphics, code-named Alchemist and previously known as DG2, will support desktop PCs and laptops and is set to arrive in the first quarter of 2022.
Alchemist will have hardware-based Ray tracing and AI-driven supersampling. This indicates that GPU is aimed to compete in the Hi-end spectrum and battle side by side with Nvidia and AMD on the market. Alchemist will also pack full DirectX 12 Ultimate support.
Intel also released names for the next upcoming future generations of ARC GPUs: Battlemage, Celestial & Druid. More information about ARC products will be released later this year.
“Today marks a key moment in the graphics journey we started just a few years ago. The launch of the Intel Arc brand and the reveal of future hardware generations signifies Intel’s deep and continued commitment to gamers and creators everywhere,” Roger Chandler, Intel vice president, and general manager of client graphics products and solutions.
This is not the first time that Intel is trying to enter the GPU field but its adventures so far were, well let us agree not so good. All of that is hoping to be changed with the upcoming ARC GPU. The first generation of Arc graphics, code-named Alchemist and previously known as DG2, will support desktop PCs and laptops and is set to arrive in the first quarter of 2022.
Alchemist will have hardware-based Ray tracing and AI-driven supersampling. This indicates that GPU is aimed to compete in the Hi-end spectrum and battle side by side with Nvidia and AMD on the market. Alchemist will also pack full DirectX 12 Ultimate support.
Intel also released names for the next upcoming future generations of ARC GPUs: Battlemage, Celestial & Druid. More information about ARC products will be released later this year.
“Today marks a key moment in the graphics journey we started just a few years ago. The launch of the Intel Arc brand and the reveal of future hardware generations signifies Intel’s deep and continued commitment to gamers and creators everywhere,” Roger Chandler, Intel vice president, and general manager of client graphics products and solutions. 
