RegClean Pro is a program developed by Systweak Inc. RegClean Pro cleans such invalid registry errors using its advanced scan engine. It not only fixes invalid registry entries, it also defragments the registry, keeping it streamlined for smoother system performance.
RegClean Pro defines auto-start registry entities that allow the program to run each time the system is restarted, it also adds various Scheduled tasks in Windows Task Manager in order to launch the application at various times. This application has been found bundled up with various other potentially unwanted applications, also several anti-virus programs have detected this application for optional removal.
About Potentially Unwanted Applications
What is a Potentially Unwanted Program (PUP)?
Have you ever detected an unwanted program on your computer system and pondered how it got there since you’re confident that you didn’t consciously download or never gave authorization to be installed? Potentially Unwanted Programs (PUP), also known as Potentially Unwanted Applications (PUA), are programs that you never wanted in the first place and sometimes come bundled with freeware software. Once installed, the majority of these applications can be hard to eliminate and become much more of a nuisance rather than a benefit.
The term PUP was coined to outline this crapware as something other than malicious software. Similar to malicious software, PUPs cause problems when downloaded and placed on your PC, but what makes a PUP different is you grant consent to download it – the fact is very different – the software installation bundle actually tricks you into accepting the installation. No matter whether it is viewed as malware or otherwise, PUPs are nearly always harmful to a computer owner as they will bring on spyware, adware, keystroke logging, along with other nasty “crapware” features on the PC.
What do PUPs do on your PC, precisely?
PUPs come in many forms. Commonly, they will be seen in adware bundlers which are known to use aggressive and misleading advertising. Most bundlers install multiple adware applications from various vendors, each of which has its own EULA policy. Safebytes Anti-Malware totally eliminates this threat and safeguards the computer against unwanted programs or adware infection. They will also come in the form of web browser extension add-ons and toolbars. They may keep track of your online movements, redirect your search results to risky sites where spyware and adware can be downloaded, hijack your search page, and slow your web-browser down to a crawl.
PUPs lie in the gray part of the software spectrum. Also in the large majority of the cases, people won’t be aware that they are installing an unwanted program. Even if the PUPs really aren’t inherently malicious, these software programs still do practically nothing good on your computer system – they will take valuable resources, slow your PC, weaken your computer security, making your PC more vulnerable to viruses.
How you can stop PUPs
• Read carefully before accepting the license agreement as it might have a clause about PUPs.
• Do not accept standard, express, default, or any other installation settings which are recommended. Always select “custom” installation.
• Install an advert blocker/pop-up blocker; Deploy anti-malware products like Safebytes Anti-Malware. These types of software programs could establish a wall between the computer and online criminals.
• Be alert if you download and install freeware, open-source software, or shareware. Never install applications that seem suspicious or malicious.
• Use official product websites for downloading software. Stay away from download portals altogether as most websites compel users to download the software using their own download manager, which is often bundled with some sort of unwanted programs.
Can't Install Safebytes Anti-malware due to the presence of Malware? Do This!
Practically all malware is bad, but certain types of malicious software do more damage to your computer or laptop than others. Some malware sits in between the computer and the internet connection and blocks a few or all websites which you want to check out. It might also prevent you from the installation of anything on your PC, particularly anti-virus programs. If you’re reading this article right now, you’ve perhaps recognized that virus infection is a reason for your blocked internet traffic. So what to do when you want to install an anti-malware application like Safebytes? There are a few actions you can take to circumvent this issue.
Download the software in Safe Mode with Networking
In Safe Mode, you are able to change Windows settings, uninstall or install some software, and remove hard-to-delete viruses and malware. If the virus is set to load immediately when the computer boots, switching to this mode may prevent it from doing so. To get into Safe Mode or Safe Mode with Networking, press the F8 key while the computer is booting up or run MSConfig and look for the “Safe Boot” options under the “Boot” tab. After you restart into Safe Mode with Networking, you can download, install, as well as update anti-malware software from there. Following installation, run the malware scanner to eliminate most standard infections.
Switch to an alternate web browser
Certain viruses might target vulnerabilities of a particular web browser that block the downloading process. If you seem to have a trojan attached to Internet Explorer, then switch to an alternate web browser with built-in security features, such as Chrome or Firefox, to download your preferred anti-malware program – Safebytes.
Install and run anti-malware from a USB drive
Another method is to download and transfer an anti-malware application from a clean PC to run a virus scan on the infected system. Follow these steps to run the antivirus on the infected computer.
1) On a clean PC, download and install Safebytes Anti-Malware.
2) Plug in the USB drive into the uninfected PC.
3) Double click on the downloaded file to open the installation wizard.
4) Choose a USB flash drive as the place when the wizard asks you where you wish to install the application. Follow activation instructions.
5) Remove the USB drive. You may now use this portable antivirus on the infected computer.
6) Double-click the antivirus software EXE file on the pen drive.
7) Run Full System Scan to identify and clean-up up all types of malware.
A Look at the Best Anti-Malware Program
These days, anti-malware software can protect your PC from different types of internet threats. But exactly how to decide on the right one among various malware protection application that is available out there? As you might be aware, there are numerous anti-malware companies and products for you to consider. Some are worth your money, but most aren’t. You have to purchase a product that has obtained a good reputation and detects not only viruses but other sorts of malware too. Amongst few good programs, SafeBytes Anti-Malware is the highly recommended program for the security-conscious end user.
Safebytes is among the well-established computer solutions firms, which provide this all-inclusive anti-malware software program. With its cutting-edge technology, this application will let you eliminate several types of malware like computer viruses, trojans, PUPs, worms, adware, ransomware, and browser hijackers.
SafeBytes has great features when compared to other anti-malware programs. The following are some of the features you will like in SafeBytes.
Real-time Protection: Malware programs trying to enter the computer are identified and stopped as and when detected by the SafeBytes active protection shields. They are very efficient in screening and getting rid of various threats because they’re constantly revised with new updates and alerts.
World-class AntiMalware Protection: This deep-cleaning anti-malware software goes much deeper than most anti-virus tools to clean out your computer. Its critically acclaimed virus engine locates and disables hard-to-remove malware that conceals deep within your personal computer.
Internet Security: SafeBytes checks and gives a unique safety ranking to each and every site you visit and block access to web pages known to be phishing sites, thus protecting you against identity theft, or known to contain malware.
Fast Scan: Safebytes Anti-Malware, with its advanced scanning engine, offers ultra-fast scanning which can immediately target any active on-line threat.
Lightweight: This program is not “heavy” on your computer’s resources, so you will not notice any performance problems when SafeBytes is operating in the background.
Premium Support: For any technical issues or product support, you can get 24/7 professional assistance via chat and email.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove RegCleanPro without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by RegCleanPro
Files:
File %APPDATASystweakRegClean ProVersion 6.1ExcludeList.rcp.
File %APPDATASystweakRegClean ProVersion 6.1German_rcp.dat.
File %APPDATASystweakRegClean ProVersion 6.1log_06-13-2013.log.
File %APPDATASystweakRegClean ProVersion 6.1results.rcp.
File %APPDATASystweakRegClean ProVersion 6.1TempHLList.rcp.
File %COMMONDESKTOPRegClean Pro.lnk.
File %COMMONPROGRAMSRegClean ProRegClean Pro entfernen.lnk.
File %COMMONPROGRAMSRegClean ProRegClean Pro.lnk.
File %COMMONPROGRAMSRegClean ProRegister RegClean Pro.lnk.
File %PROGRAMFILESRegClean ProChinese_rcp.ini.
File %PROGRAMFILESRegClean ProCleanSchedule.exe.
File %PROGRAMFILESRegClean ProCloud_Backup_Setup.exe.
File %PROGRAMFILESRegClean ProCloud_Backup_Setup_Intl.exe.
File %PROGRAMFILESRegClean Proisxdl.dll.
File %PROGRAMFILESRegClean ProRCPUninstall.exe.
File %PROGRAMFILESRegClean ProRegCleanPro.dll.
File %PROGRAMFILESRegClean ProRegCleanPro.exe.
File %PROGRAMFILESRegClean Prosystweakasp.exe.
File %PROGRAMFILESRegClean Proxmllite.dll.
File %WINDIRTasksRegClean Pro_DEFAULT.job.
File %WINDIRTasksRegClean Pro_UPDATES.job.
Directory %APPDATASystweakRegClean ProVersion 6.1.
Directory %APPDATASystweakRegClean Pro.
Directory %COMMONPROGRAMSRegClean Pro.
Directory %PROGRAMFILESRegClean Pro.
Registry:
Key Distromatic at HKEY_CURRENT_USERSoftware.
Key Systweak at HKEY_CURRENT_USERSoftware.
Key Systweak at HKEY_LOCAL_MACHINESOFTWARE.
 Error Causes
Error Causes
 This is the second large game company acquisition by Microsoft, Acquiring Bethesda first and a big hit to Sony since Xbox will now have more games in its catalog and as exclusives.
Of course, the sale has to go through the standard closing conditions and completion of regulatory review and Activision Blizzard’s shareholder approval before it’s finalized. Assuming that all goes well, the deal is slated to be completed during the fiscal year 2023, which is July 1, 2022, through June 30, 2023.
This is the second large game company acquisition by Microsoft, Acquiring Bethesda first and a big hit to Sony since Xbox will now have more games in its catalog and as exclusives.
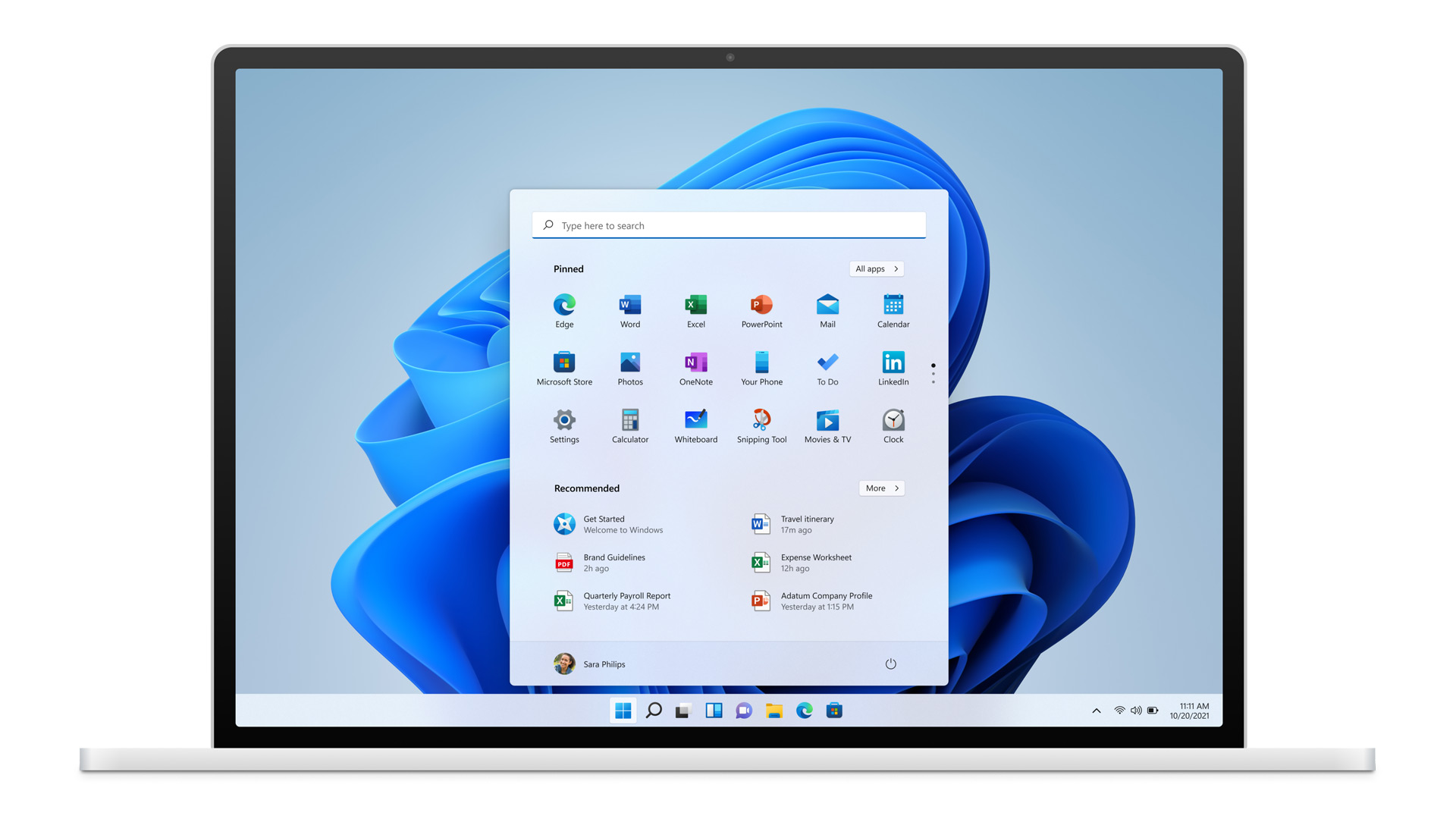
Of course, the sale has to go through the standard closing conditions and completion of regulatory review and Activision Blizzard’s shareholder approval before it’s finalized. Assuming that all goes well, the deal is slated to be completed during the fiscal year 2023, which is July 1, 2022, through June 30, 2023. 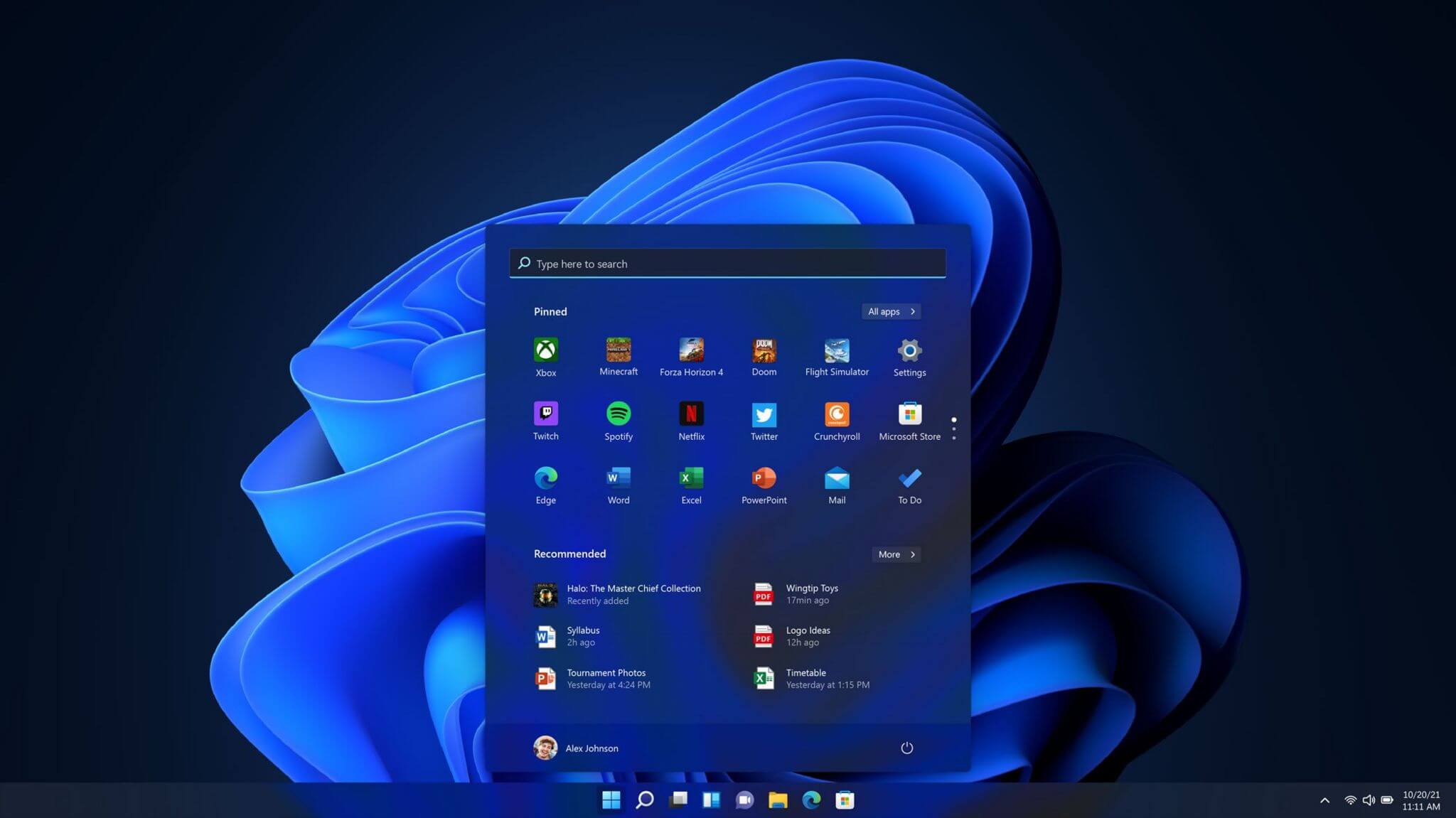 One of the first things that everyone saw when Microsoft has unveiled Windows 11 is its Start menu. Funny enough this is what has caused most of the divide among users, some find it interesting, and some do not like it. Truth is, it is different, and it is centered in the middle instead of the lower left part of the screen.
It has been confirmed however that the Start menu can be moved to any part of the screen so if you want, you could place it on the lower left as it has always been.
Live tiles do not longer exist in the Start menu, instead, we have styled simple icons.
One of the first things that everyone saw when Microsoft has unveiled Windows 11 is its Start menu. Funny enough this is what has caused most of the divide among users, some find it interesting, and some do not like it. Truth is, it is different, and it is centered in the middle instead of the lower left part of the screen.
It has been confirmed however that the Start menu can be moved to any part of the screen so if you want, you could place it on the lower left as it has always been.
Live tiles do not longer exist in the Start menu, instead, we have styled simple icons.
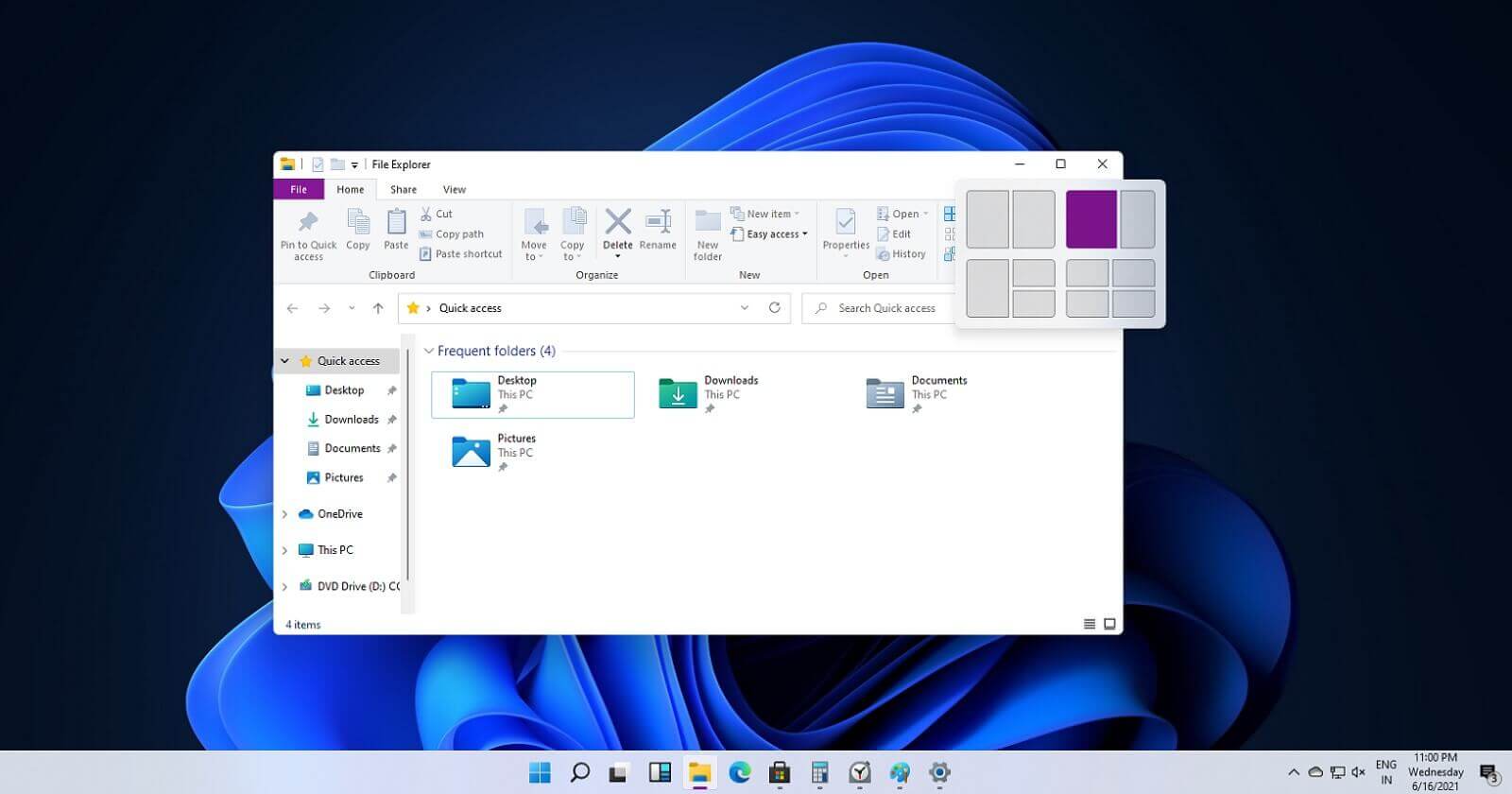 If you have used the cascade option in previous Windows versions then it is most likely that you will like the new Snap controls.
You can quickly snap windows side by side, or arrange them in sections on your desktop just by hovering over maximize button on the title bar.
If you have used the cascade option in previous Windows versions then it is most likely that you will like the new Snap controls.
You can quickly snap windows side by side, or arrange them in sections on your desktop just by hovering over maximize button on the title bar.
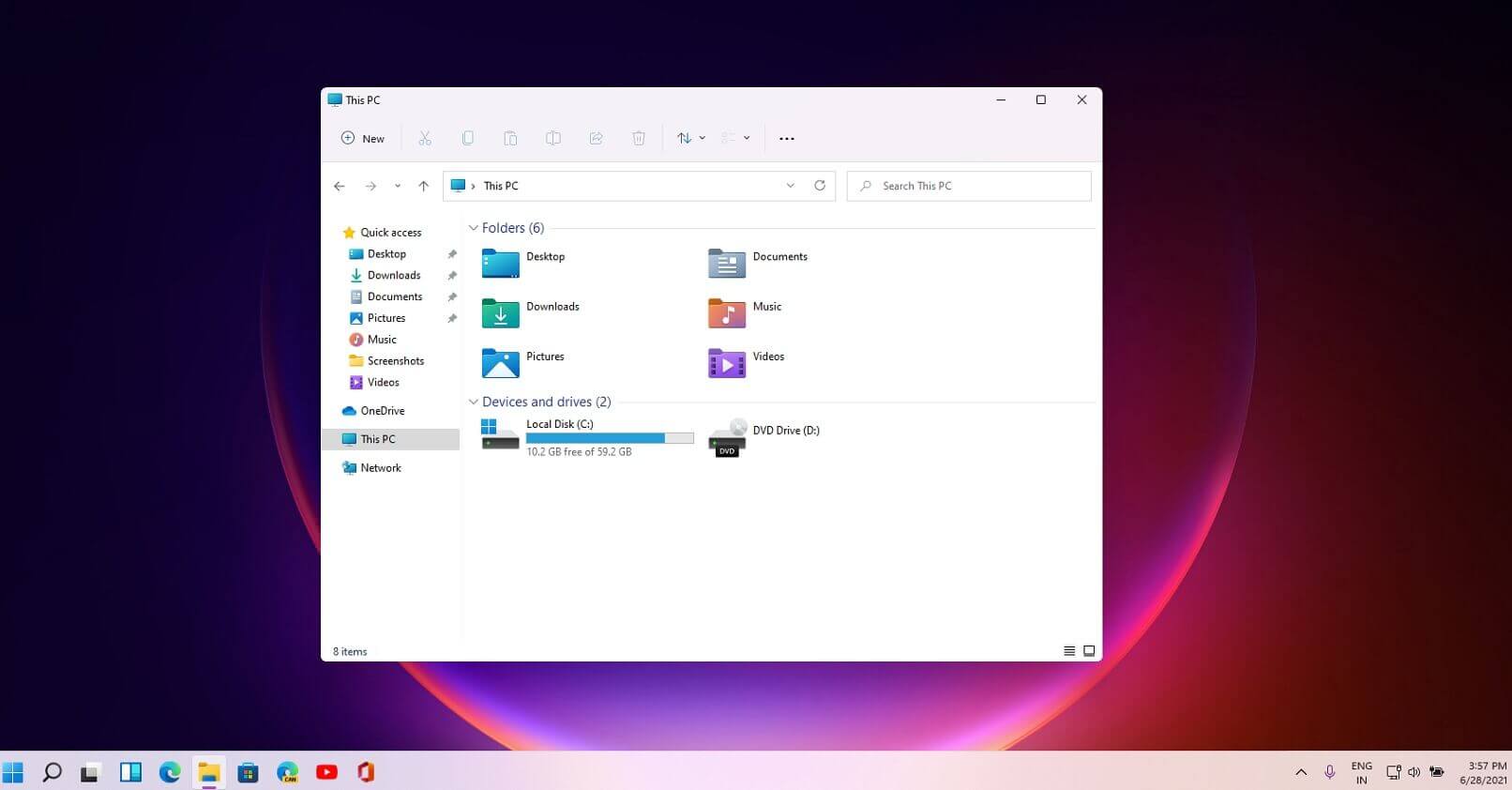 File explorer has gone through some visual and design changes, the ribbon on top has been completely removed and replaced with a header-like feature with a slick and clean design.
The header contains a nice organized and designed single row of icons like cut, paste, copy, rename, delete, and new folder icons.
File explorer has gone through some visual and design changes, the ribbon on top has been completely removed and replaced with a header-like feature with a slick and clean design.
The header contains a nice organized and designed single row of icons like cut, paste, copy, rename, delete, and new folder icons.
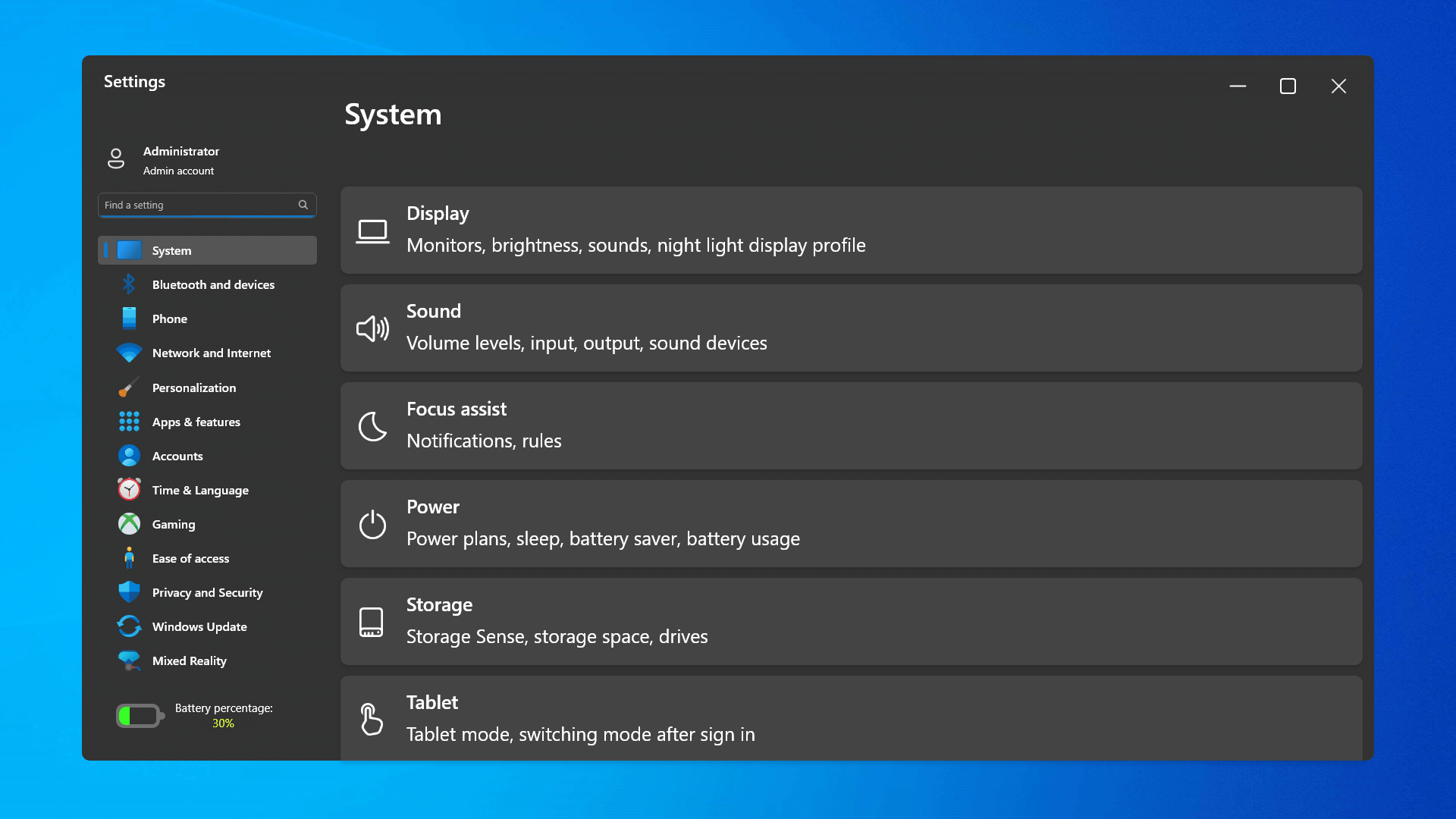 The settings app also has gone through visual and design changes. It has a new design that is very visually appealing and navigation has been simplified and more organized. Finding the right and desired setting is much faster and clearer now.
The settings app also has gone through visual and design changes. It has a new design that is very visually appealing and navigation has been simplified and more organized. Finding the right and desired setting is much faster and clearer now.
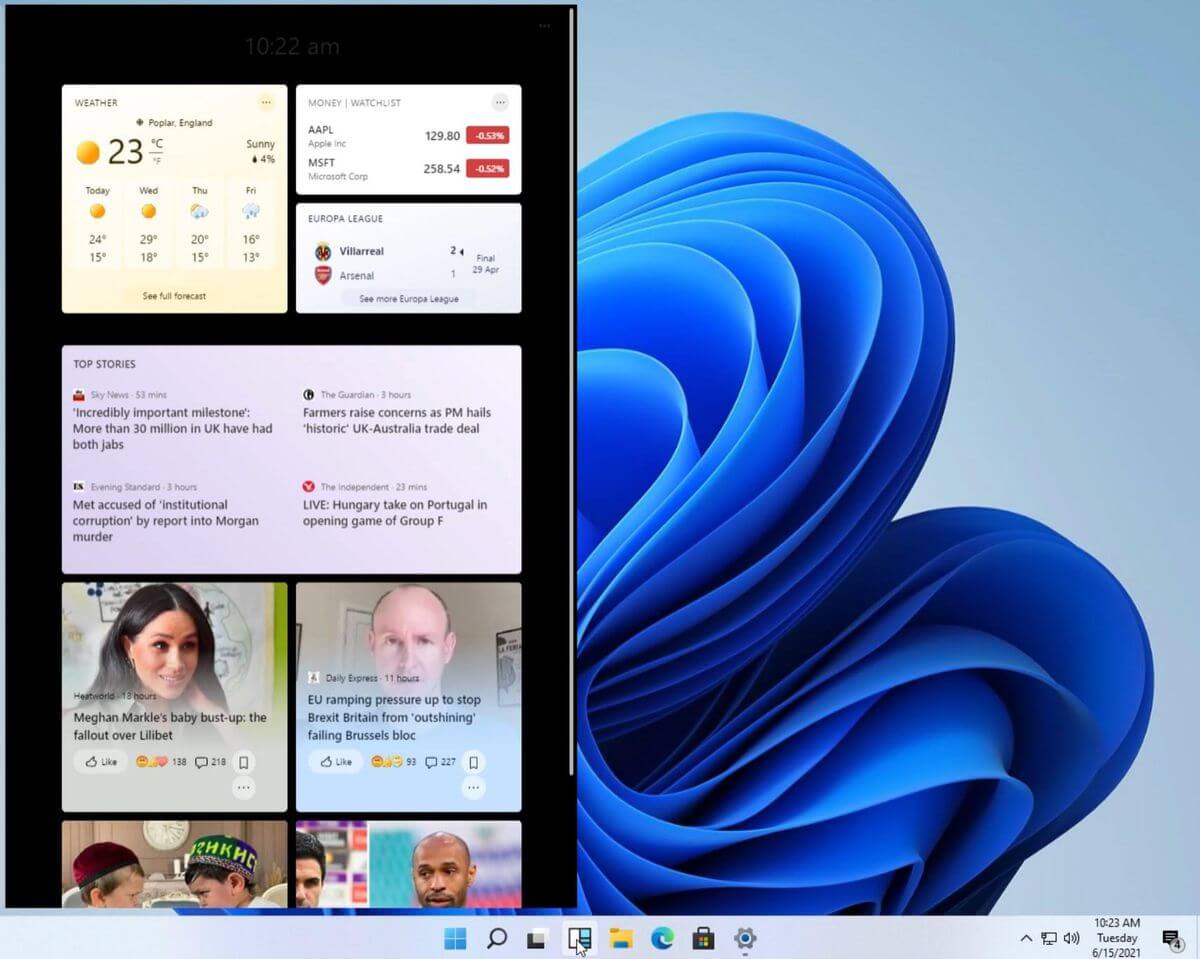 Yes, widgets are back but not like you remember them.
Instead of being all-time present at your desktop like once they used to be, now there is a button on the taskbar which brings the widget bar up that contains desired widgets. This way they are easily accessible and do not clutter desktops.
So far we have weather, news, calendar, and stocks widget but we will see how development on these goes. I expect to have community-made widgets like in old days for all of our needs.
Yes, widgets are back but not like you remember them.
Instead of being all-time present at your desktop like once they used to be, now there is a button on the taskbar which brings the widget bar up that contains desired widgets. This way they are easily accessible and do not clutter desktops.
So far we have weather, news, calendar, and stocks widget but we will see how development on these goes. I expect to have community-made widgets like in old days for all of our needs.
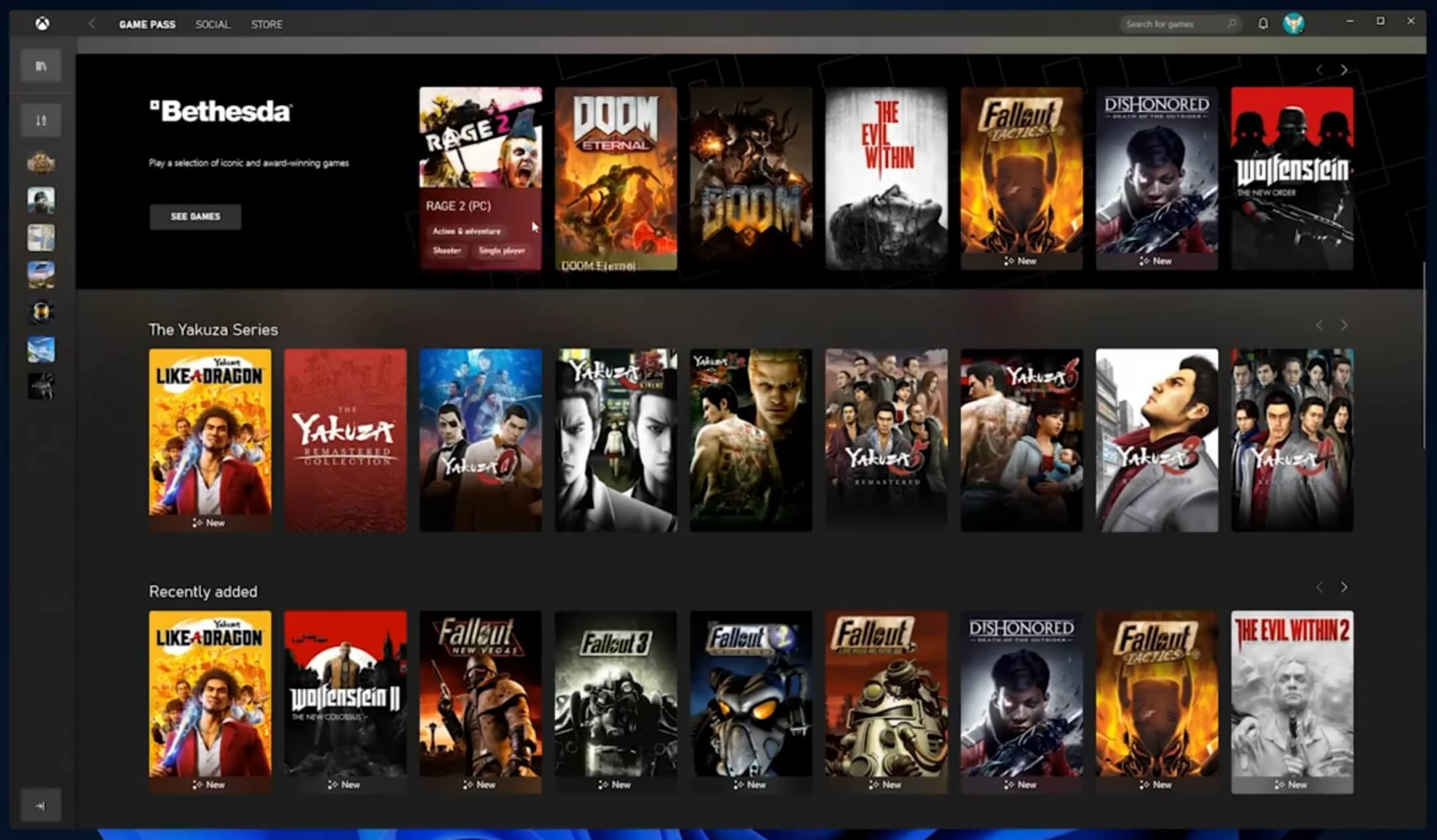 The new Xbox app is now integrated into Windows 11, offering quick access to Xbox Game Pass games, the social parts of the Xbox network, and the Xbox store.
The new Xbox app is now integrated into Windows 11, offering quick access to Xbox Game Pass games, the social parts of the Xbox network, and the Xbox store.
 As widely known by now Windows 11 will require you to have a TPM 2.0 module capable CPU in order to install it.
This system requirement has caused a lot of controversies but essentially it seems that MS's goal is to protect your personal data by using this module.
The upside of course is that your data will be protected much more than in previous Windows versions, the downside, of course, will be that you will need newer hardware to run OS on it.
and that is essentially it, keep on tuned on more Windows 11 information and overall articles tied to PC and technology here at errortools.com
As widely known by now Windows 11 will require you to have a TPM 2.0 module capable CPU in order to install it.
This system requirement has caused a lot of controversies but essentially it seems that MS's goal is to protect your personal data by using this module.
The upside of course is that your data will be protected much more than in previous Windows versions, the downside, of course, will be that you will need newer hardware to run OS on it.
and that is essentially it, keep on tuned on more Windows 11 information and overall articles tied to PC and technology here at errortools.com 
 Bug and security fixes:
Bug and security fixes: