If you suddenly see a system icon or an application icon that has a blue and yellow shield or icon overlay at the corner, this indicates that the application has to run with admin privileges and each time you run these kinds of applications, a UAC or User Account Control prompt will appear to confirm if you really want to run the application. Although this kind of behavior is for security reasons, it can get quite annoying especially if you use the application on a daily basis. To make it convenient for you, this post will walk you through how you can remove the blue and yellow shield icon from an application on your Windows 10 computer.
The User Account Control or UAC setting is the one that ensures no program can run with administrative privileges unless it is allowed by the user. This stops any program that could be potentially harmful to the computer from making any changes which are why keeping this setting to its default state is for the best and making any changes in its setting is not recommended unless it is really needed.
So if you really have to remove the icon overlay in an application, there are several ways you can do that. You can try reinstalling the program and set Compatibility or change the UAC level. For more information, refer to every option given below.
As you know, the application icons where you can see the shields are shortcuts mostly and they signify that the User Account Control will appear each time you launch the app. Thus, if you have an app that you use regularly and you’re certain that the app can be trusted, you can try to reinstall the app and set its compatibility by following these steps:

“Updates failed There were problems installing some updates, but we’ll try again later. If you keep seeing this and want to search the web or contact support for information, this may help: 2018-07 Cumulative Update for Windows 10 Version 1803 for x64-based Systems (KB4345421) – Error 0xca00a000”This kind of Windows Update error pops up when Windows has missed installing one of the cumulative updates needed or when there is some problem with the driver that won’t let the installation of the updates push through. There are also instances when the system files are modified with incorrect permission that may result in the Windows update error 0xca00a000. Thus, you need to fix the trusted installer permission as well as resolve the issue with the driver. To do these things, you need to follow the options laid out below.
SC config trustedinstaller start=auto
net stop wuauserv net stop bits
net start wuauserv net start bitsSince the folder has already been flushed, it will be populated afresh the instant your restart your computer and open Windows Update.
 So far we probably all know what are good new and exciting features that W11 is bringing to the table, let’s talk now about features that will be removed and are not there but we had them in W10
So far we probably all know what are good new and exciting features that W11 is bringing to the table, let’s talk now about features that will be removed and are not there but we had them in W10
“The dynamic library dll failed to load.” “Failed to load dll library.”This kind of error can occur when your Windows operating system fails to locate the DLL library which the system needs to access during startup. It can also occur when the DLL file is not in a directory specified in the path or when the DLL file is corrupted or has gone missing. Moreover, you can also encounter this error if the DLL file is infected with some malware. Whatever the case is, here are some suggestions you have to check out to resolve the problem.
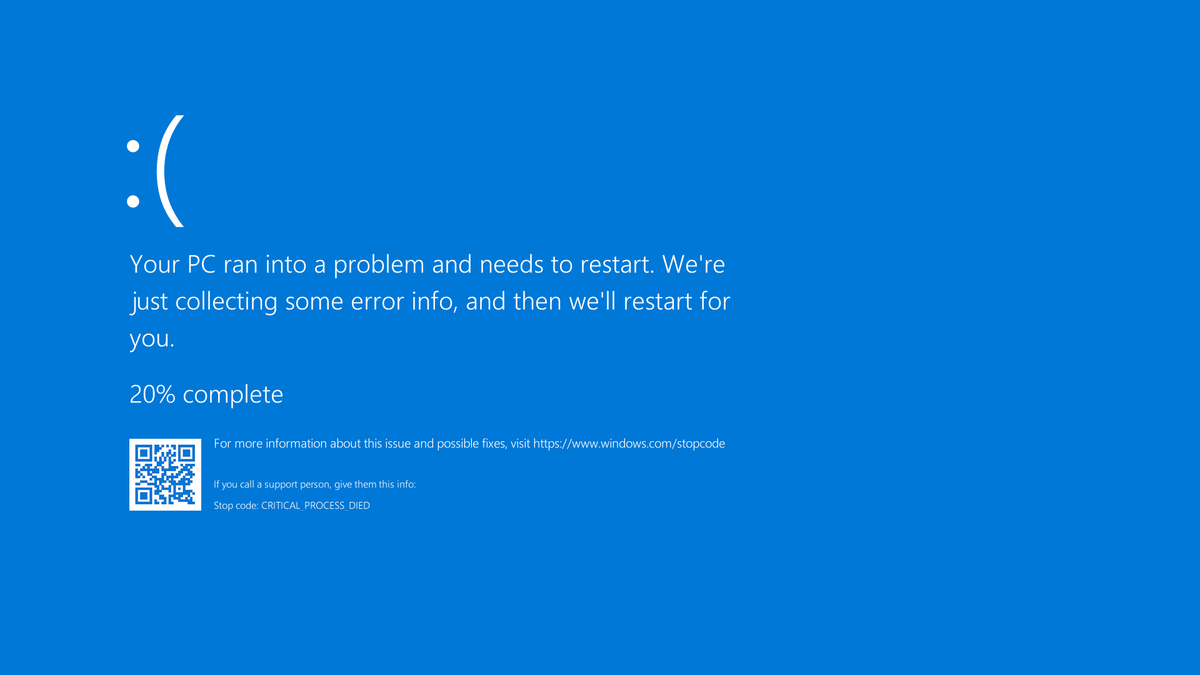 A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
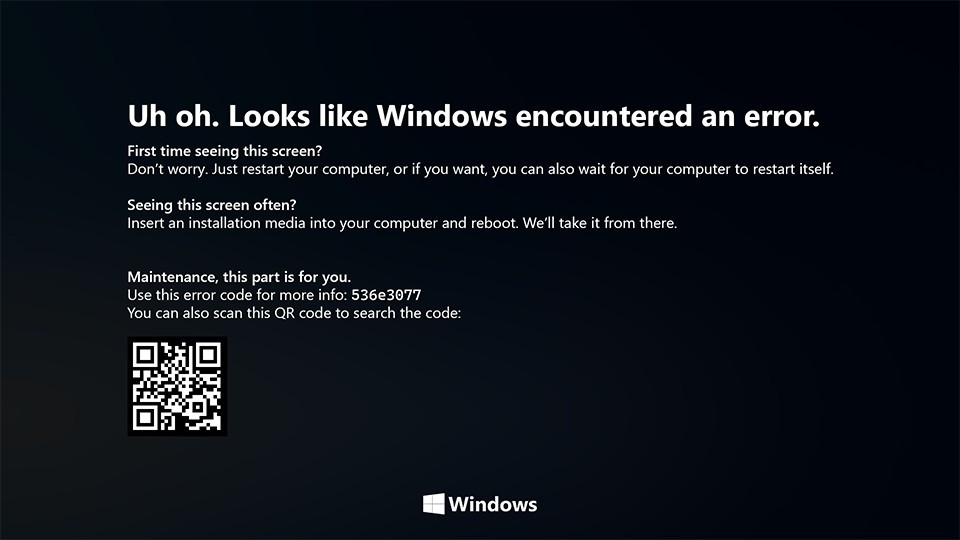 On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update. To resolve this problem, simply hold the power button down on your PC or laptop to switch off the computer. A cold start should result in the system booting properly.
On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update. To resolve this problem, simply hold the power button down on your PC or laptop to switch off the computer. A cold start should result in the system booting properly.
 It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
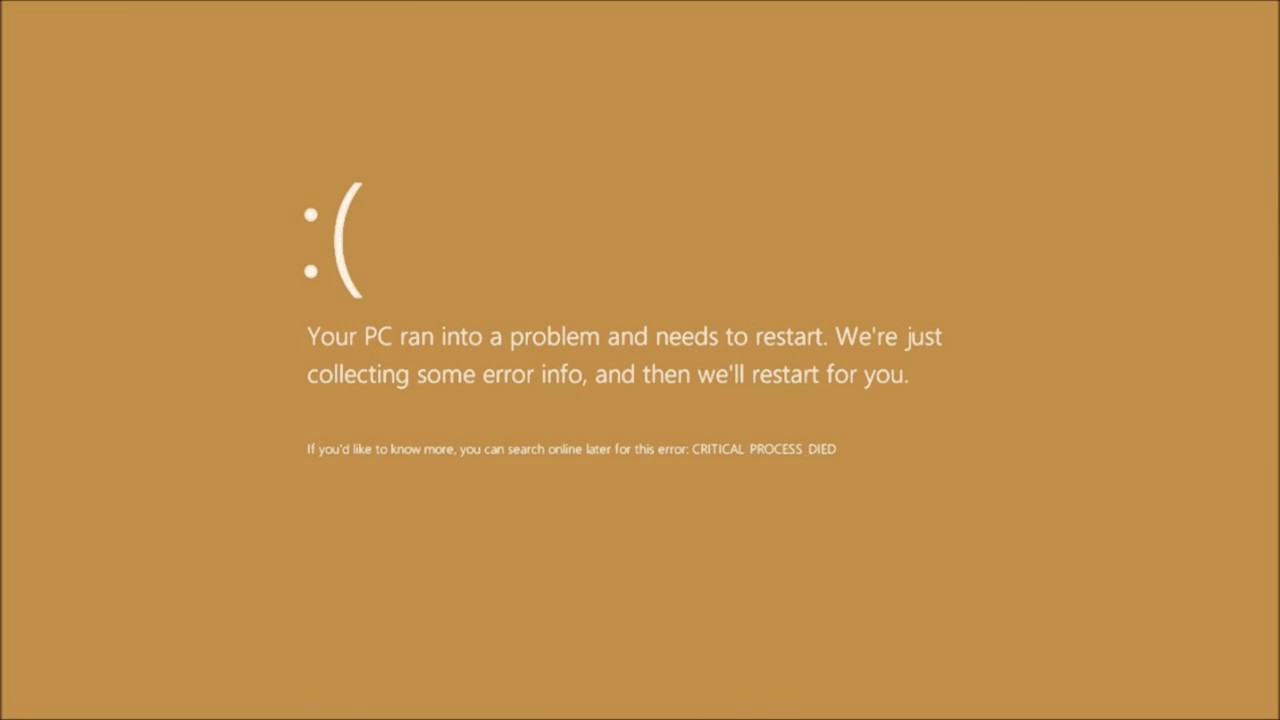 The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers).
The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers).
 It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
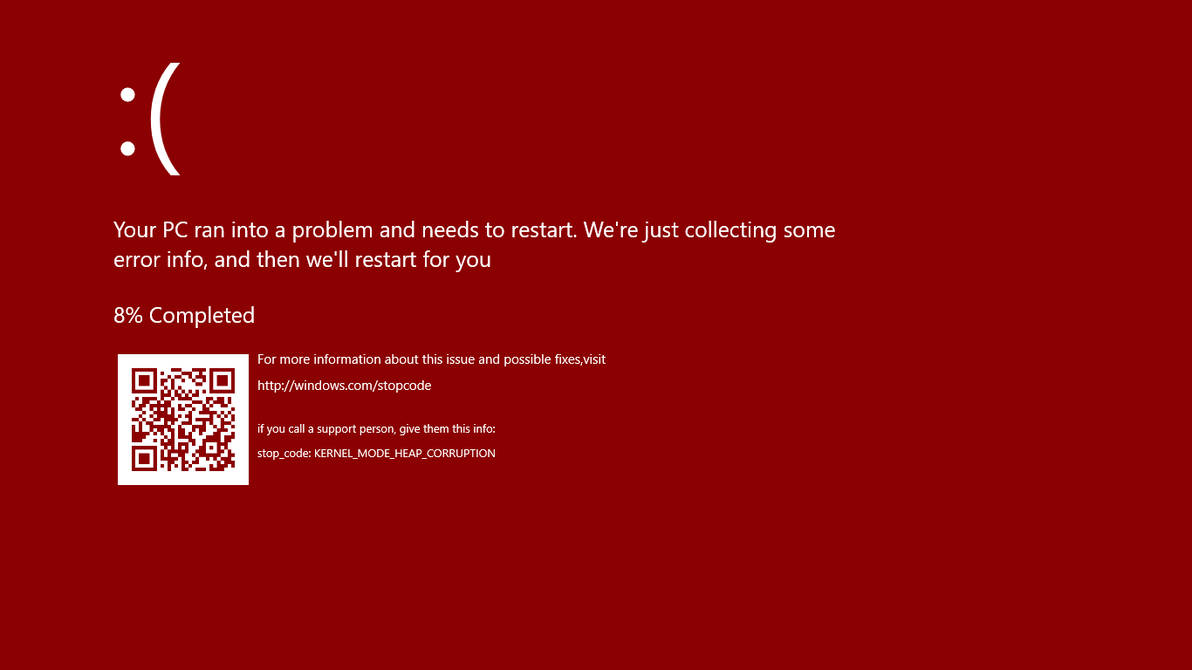 Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.
Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.
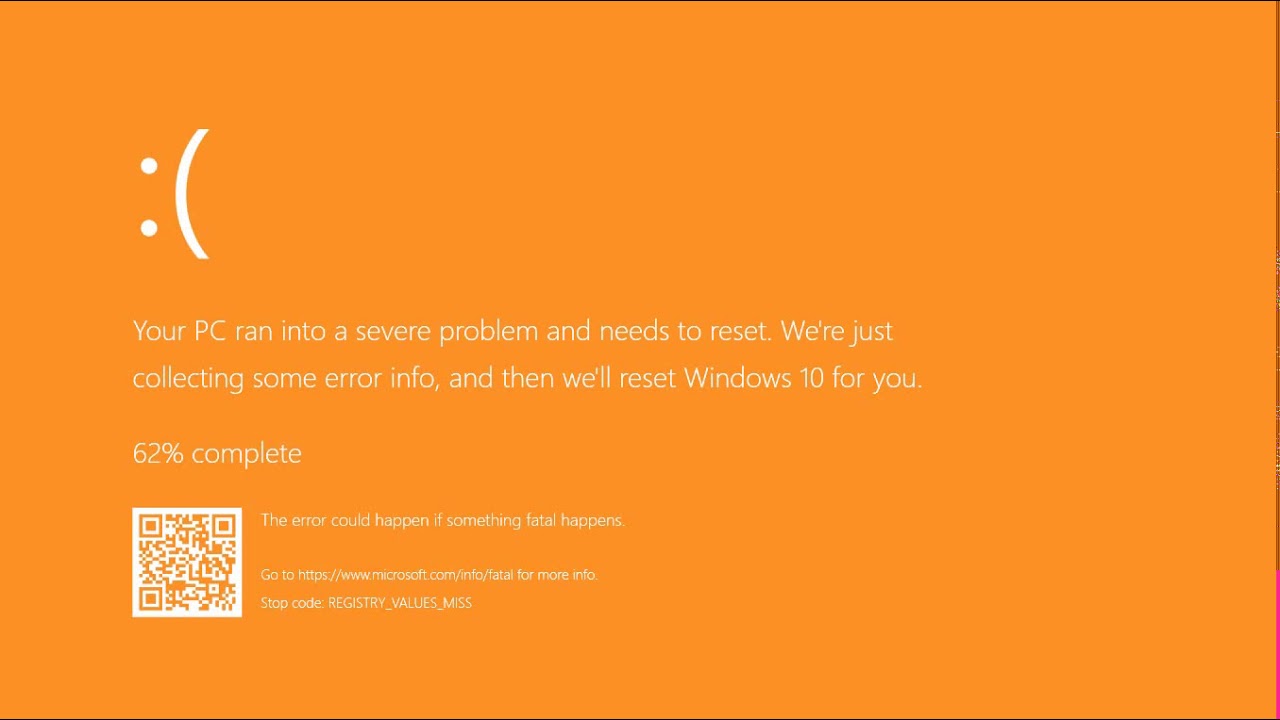 The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
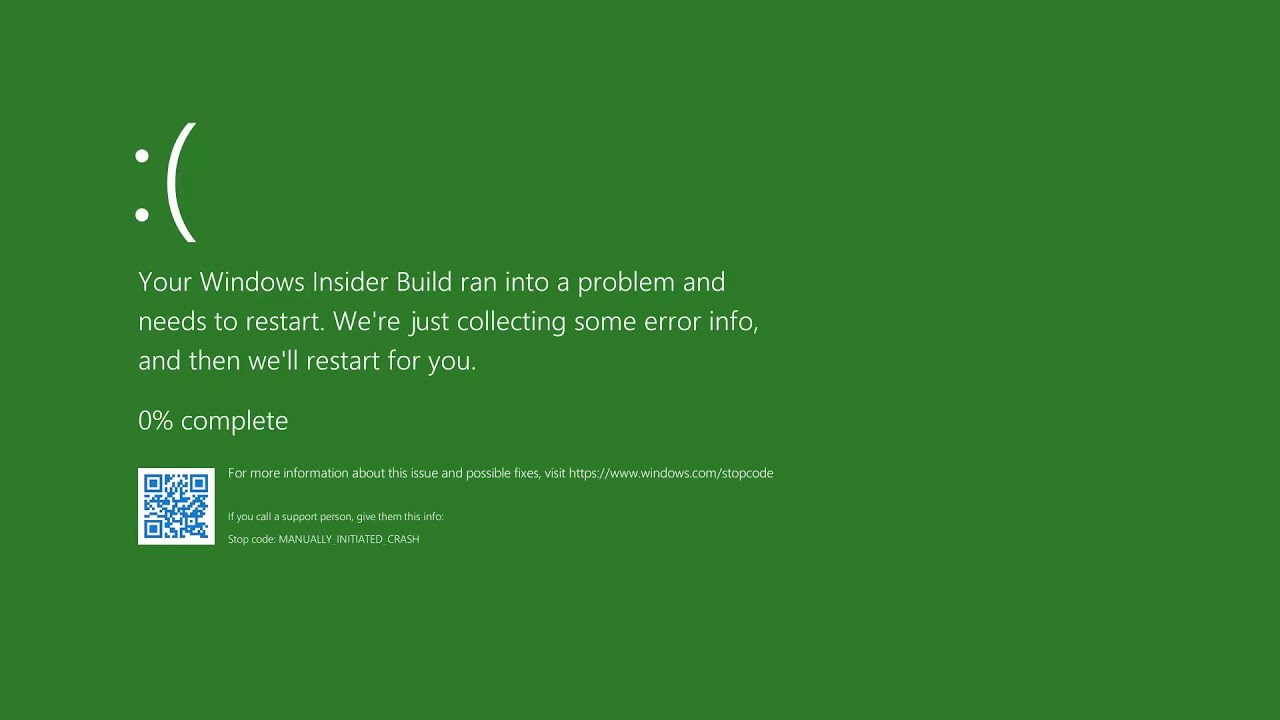 The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10.
The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10.
 The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware.
The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware. mixGames is an Extension for Google Chrome that adds “Games:” functions to Google Chrome. In our testing, this function did not work and only redirects you back to the extension page. There are two variations of mixGames: mixGames Search, which changes the Chrome homepage to one managed by their own advertising-driven search; and mixGames Start, which changes the homepage in Chrome. These extensions utilize Searchalo to change search engine functions from the default or user-set preferences to Yahoo, injecting additional advertising. Due to the browser function modifications, mixGames is classified as potentially unwanted and is flagged for detection and optional removal by some Antivirus programs.
“Socket.error: [Errno 10013] an attempt was made to access a socket in a way forbidden by its access permissions”
 Error Causes
Error Causes Error Causes
Error Causes