So, you have finished with work, game, movie, music, email, or whatever on your PC, you look at the clock, it is late, you decide to go to sleep or outside, you click on the power button and choose shutdown. Now when a PC is shut down you feel good and go with your business but the next time you power it up you get the same error like the computer never really shut down in the first place. You wonder why and reboot it, just in case and all of the sudden error is gone.
If something similar has happened to you or you had the feeling that after shutting down your computer has not really felt like shutting it down, do not seek professional help, everything is OK with you because when you click on shut down, your computer does not really shut down!
Truth is that Microsoft has changed how to shut down works and how rebooting works in Windows with an update but has not publicly said anything about it so some users may experience this feeling of not shutdown phenomenon and might even think there is something wrong with their PC.
Why this change?
A few years ago shutdown button and option in Windows were really shutting down OS, but things changed when Microsoft wanted to increase boot-up speed. Now when that decision was made shutdown option was changed. So, what was changed? Well in order to increase Windows booting time, the shutdown will now turn off power to PC components and it will look like everything is indeed shutdown but the Windows kernel will actually be saved to a hard drive with all settings and just awaken once the PC is turned back ON. This will result in all errors and other stuff being just still present same as they were once the system was instructed to be turned off.
Rebooting your PC will now clear kernel and file from the hard drive and you will get a clean system startup without any issues tied with the kernel itself.
Workaround
Now that we know why and what change has been made to Windows logical question is can we shut down our PC at all properly? Luckily for us, the answer is yes and we will not need any external application to do it, we can still do it inside Windows itself and it is quite quick and easy.
Bringing back the old shutdown
In order to bring the old shutdown functionality of your PC please follow the instructions but be aware that by doing this your PC will boot a little bit slower since it will have to load the kernel from scratch each time computer is turned ON.
First thing is to go to settings and go to System
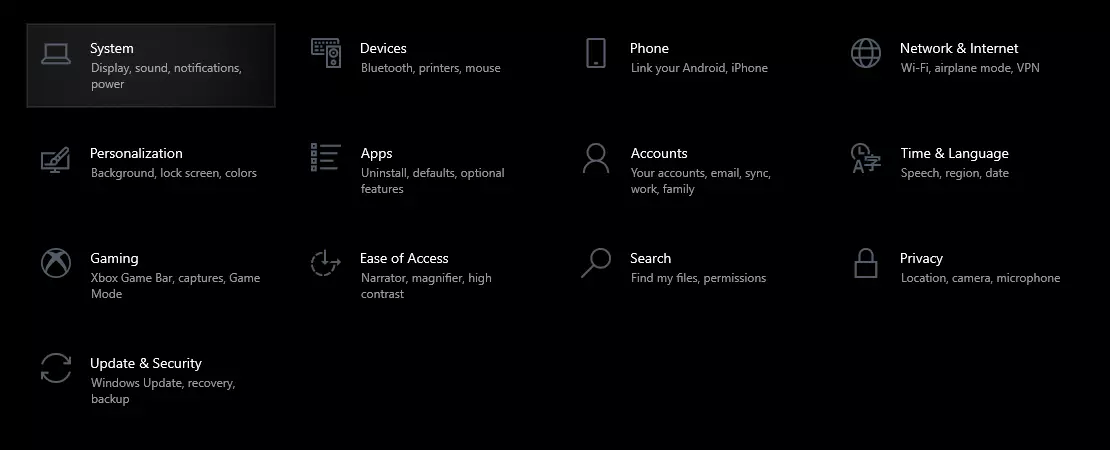
Then once you are inside the system, navigate to the power and sleep and click on it to select it. Once you have it selected to all the way to the right and click on additional power settings.
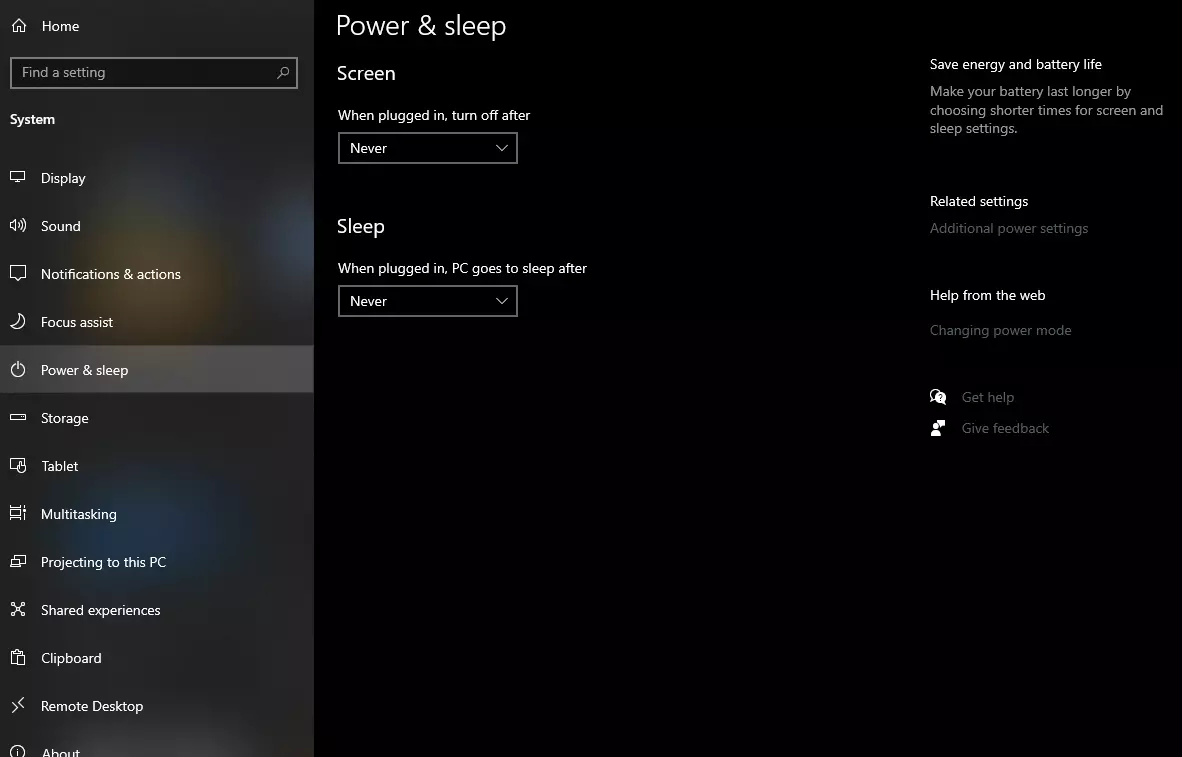
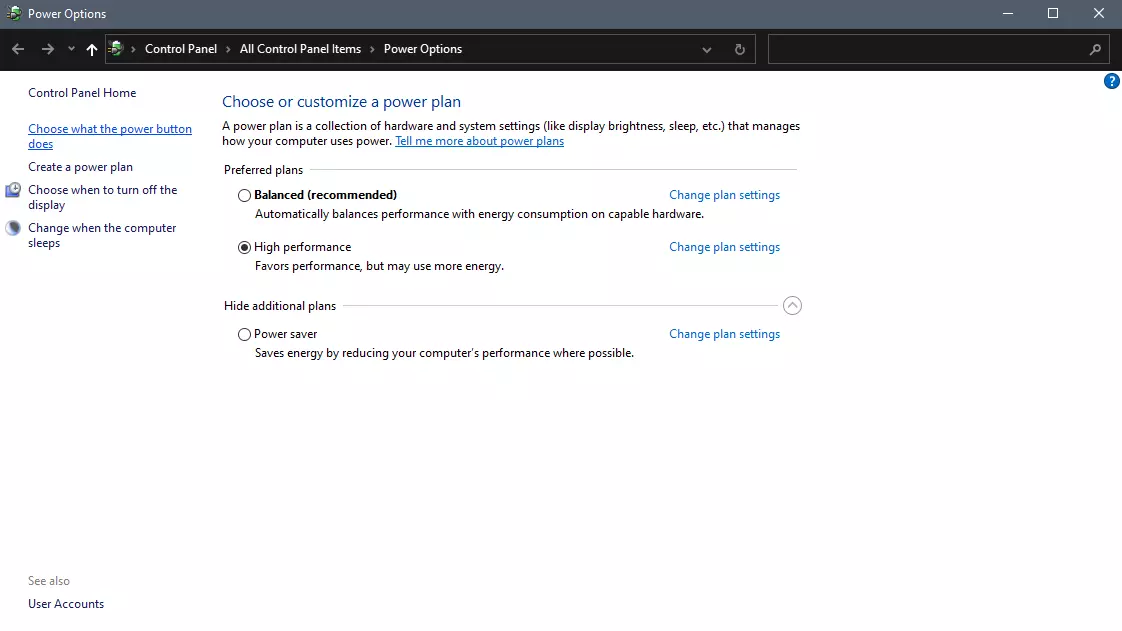
When you click on advanced power settings you should be led to the control panel's power options. Inside this panel click on top left link where it says Choose what the power button does.
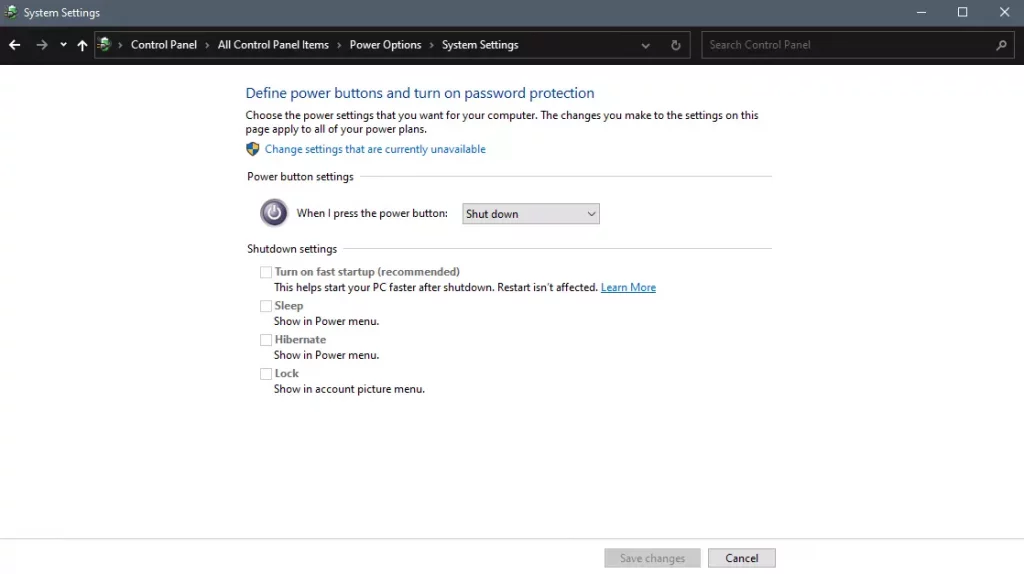
Inside options, you will need to untick the box next to Turn on fast startup (recommended), this option has been ticked ON by the Windows update and probably without notifying you. Option means exactly what was described, it will save kernel state on the hard drive for faster boot time but sadly it can cause some issues since it will never be reloaded from 0.
If you are unable to uncheck the box click on the text beside the shield icon that says: Change settings that are currently unavailable (you will have to be logged in as administrator).
Conclusion
Altho turning off fast startup and shutting down the PC completely will for sure extend your bootup time I still believe that it is the right choice since sometimes a lot of clutter and bad things accumulate over time inside the OS and can cause a vast variety of problems in a long run. So stay safe and shut down that PC as it used to be in the past.

 Well if anyone told me just a few years ago that I will see the day when Microsoft releases a new OS based on Linux I would be very amused, but that day has come. Mariner is the newest OS out of nowhere.
Microsoft’s new Linux Distro, dubbed Common Base Linux (CBL)-Mariner, isn’t the type of distro you’d want to install directly on any old machine. It’s primarily meant for cloud infrastructure and edge products. Specifically Microsoft’s Cloud and Edge products.
But if you are curious, it’s possible to run. Juan Manuel Rey, a Microsoft Senior Program Manager for Azure VMware, recently published a guide to ISO CBL-Mariner image. With that, you can easily get it up and running. And you can build CBL-Mariner on an Ubuntu 18.04 desktop. So you can try it out since it is free.
You can get it from here:
Well if anyone told me just a few years ago that I will see the day when Microsoft releases a new OS based on Linux I would be very amused, but that day has come. Mariner is the newest OS out of nowhere.
Microsoft’s new Linux Distro, dubbed Common Base Linux (CBL)-Mariner, isn’t the type of distro you’d want to install directly on any old machine. It’s primarily meant for cloud infrastructure and edge products. Specifically Microsoft’s Cloud and Edge products.
But if you are curious, it’s possible to run. Juan Manuel Rey, a Microsoft Senior Program Manager for Azure VMware, recently published a guide to ISO CBL-Mariner image. With that, you can easily get it up and running. And you can build CBL-Mariner on an Ubuntu 18.04 desktop. So you can try it out since it is free.
You can get it from here: 
 Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11.
Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11. 
