The Error Code 0x800F0923 is one that appears only when attempting to update from older versions of Microsoft Windows to Microsoft Windows 10. This error does not occur with every install and is believed to be the result of a driver incompatibility issue. It is unclear which specific drivers are having the compatibility issues, though it is widely believed that DuplexSecure's SPTD drivers are the ones at fault. When operating correctly, without errors, the update process should not take longer than 30 minutes.
Common symptoms include:
- Error message window/pop-up during the install process, giving the Error Code 0x800F0923
- Inability to install and update from older versions of Microsoft Windows to version 10
Solution
 Error Causes
Error Causes
There are various relevant factors associated with the error code 0x800F0923 incompatibility issue in Windows 10 installation/upgrade. These factors include but are not limited to:
- The Operating System (OS) upgrading does not support older hardware.
- Your computer’s specs did not meet the minimum requirements.
- Not enough hard disk space.
- The new software might lack software drivers for older hardware
Further Information and Manual Repair
Microsoft has recently released its Windows 10 operating system. While there are still a few kinks to be worked out, overall the reviews have been positive. As with any new Microsoft update, compatibility issues can arise. If you are unsure whether your current PC will be able to handle the new Windows 10, here is an easy way to check your system.Method 1: Check if your computer is compatible
- Locate the “Get Windows 10” application icon in your notification tray (bottom right corner of your screen, white Windows logo).
- Right-click on this icon, then select the “check your upgrade status” option.
- Be prepared for the menu to take a few minutes to open.
- Click on the menu on the upper left-hand corner of this new dialog box. (It looks like three blue horizontal lines)
- Select “check your PC”
- After the system checks for compatibility, it will let you know whether or not your PC has the appropriate drivers, etc. (Keep in mind that this is not a foolproof method for checking compatibility status).
Method 2: Download or upgrade your drivers/software
If you have already attempted to update to Windows 10, and have received the Error Code 0x800F0923, this is the simplest way to solve the issue yourself.1. Open the “Get Windows 10” application. 2. Open the menu in the upper left corner, looks like three blue lines. 3. Select “Check your PC”. 4. The system will tell you which drivers are incompatible. 5. Go to the Microsoft Support website to install and/or update the drivers that proved to be an issue. 6. Once the driver issue is corrected, retry the Windows 10 update.

 Intel says that the remedy to the issue for these games is the scroll lock fix which can be done so by enabling Legacy Game Compatibility mode from the BIOS of your motherboard. When running the said games, you can press scroll lock to park the E-cores on Intel's Alder Lake Desktop CPUs to get rid of DRM issues.
Certain motherboard manufacturers such as MSI and Gigabyte have made this even easier through software tools with which you don't have to access the BIOS. All you need to do is select a button in the tool which works on both Windows 11 and Windows 10 operating systems and you will enable compatibility mode.
Intel says that the remedy to the issue for these games is the scroll lock fix which can be done so by enabling Legacy Game Compatibility mode from the BIOS of your motherboard. When running the said games, you can press scroll lock to park the E-cores on Intel's Alder Lake Desktop CPUs to get rid of DRM issues.
Certain motherboard manufacturers such as MSI and Gigabyte have made this even easier through software tools with which you don't have to access the BIOS. All you need to do is select a button in the tool which works on both Windows 11 and Windows 10 operating systems and you will enable compatibility mode. 
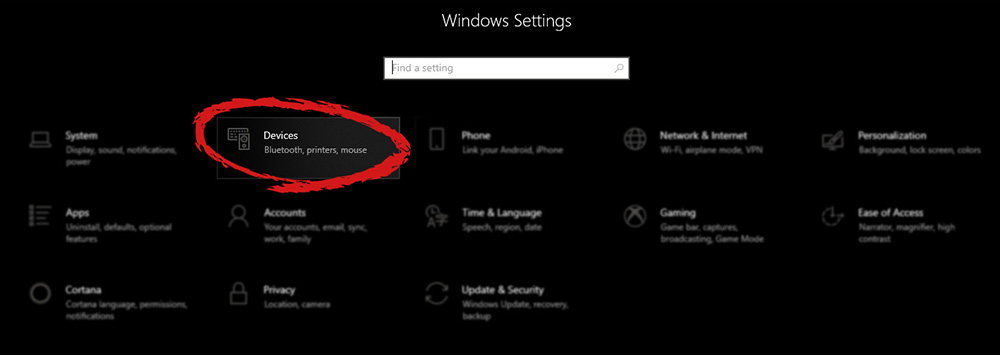 Once the device window opens, click once on printers and scanners, and on the right window go to the bottom and uncheck Let windows manage my default printer.
Once the device window opens, click once on printers and scanners, and on the right window go to the bottom and uncheck Let windows manage my default printer.
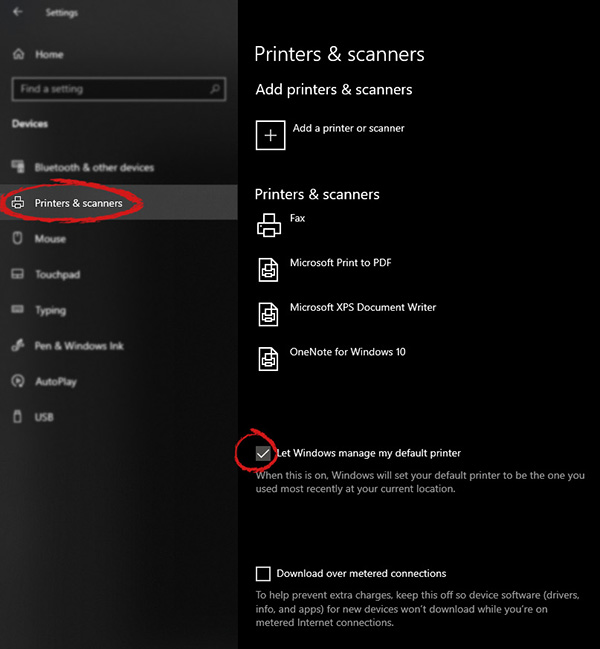 Unchecking that box will let Windows know that we do not wish anymore for him to set our default printers according to their use. Once the checkbox is clear go up to your printer list and click on the printer you wish to use as the default one. I will choose Microsoft Print to PDF as my default printer and click on it. Once the printer is clicked option menu will appear.
Unchecking that box will let Windows know that we do not wish anymore for him to set our default printers according to their use. Once the checkbox is clear go up to your printer list and click on the printer you wish to use as the default one. I will choose Microsoft Print to PDF as my default printer and click on it. Once the printer is clicked option menu will appear.
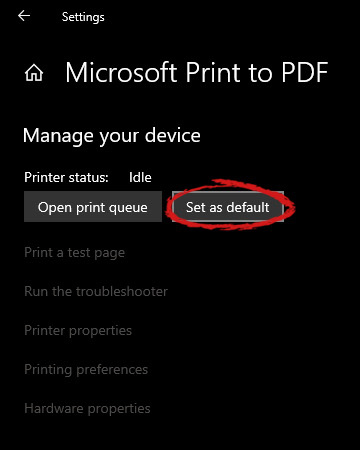
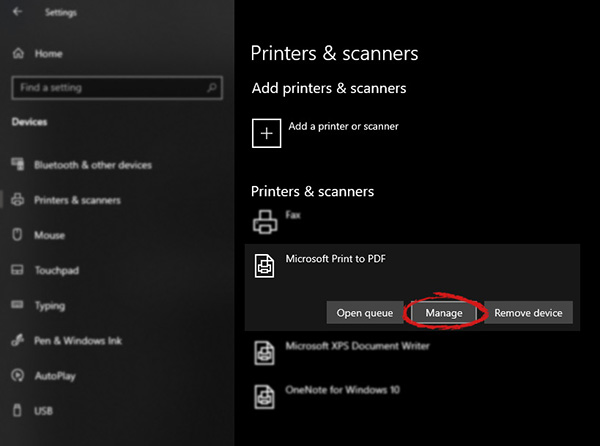 When the option menu appears under the printer name, click on Manage which will take you to the printer management screen. When you are on the manage screen, click on the Set as default button, and you are done.
When the option menu appears under the printer name, click on Manage which will take you to the printer management screen. When you are on the manage screen, click on the Set as default button, and you are done.