Hello and welcome to another problem-solving tutorial on errortools.com. Today we will be solving
error 0x80070057, we could not format the selected partition which occurs during setup and installation when performing a clean install of Windows from a USB drive.
So, you have backed up your files and decided to format and do clean WIndows installation, you have your USB ready, you reboot the system, plug in USB, start Windows setup, choose the hard drive on which you want to do a clean install and then this happens.
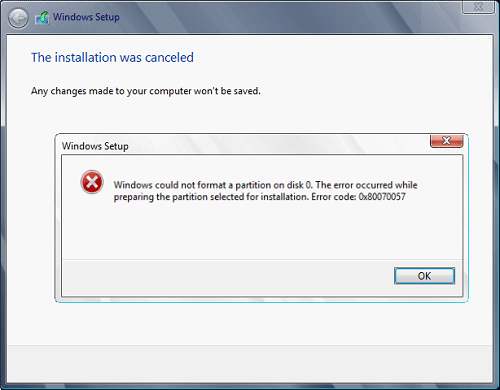
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt,
Click on the
OK button and then on
X to exit Windows 10 installation wizard.
Click on
yes to confirm that you want to
exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on
Repair your computer. Choose an option screen that will pop up, click on
Troubleshoot. In the advanced options, click on the
command prompt.
Once you are in command prompts type
DISKPART and hit
ENTER
In the diskpart prompt type
LIST DISK and hit
ENTER again.
type
SELECT DISK #, where # is listed disk number where you would like to install Windows.
type
LIST VOLUME in order to list volumes in the selected disk and hit
ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in
SELECT VOLUME #, where # is the listed number of the volume
Finally, type
FORMAT FS=NTFS and hit
ENTER
You have successfully formated a given volume, you can now exit
DISKPART and return to
setup, to exit
DISKPART simply type
exit and hit
ENTER.
Leave command prompt as well by again typing
exit and hitting
ENTER
You will be returned to
Choose an option screen,
click on
Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now
restart your Windows 10 installation and the process will complete without errors.

 This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors. 
