As you know, each one of the applications that you use in your Windows 10 computer has its own set of permissions by default. These applications either allows or denies the interactions between a few other applications, depending on their own needs. This is why you might suddenly encounter a message that says,
“This app wants to access your pictures”
or
“This app wants to access your account info”
both of which are followed by two buttons that will ask you to Allow or Deny the action. You can always click on any of the given options. This will determine the permission of the application.
Users in Windows 10 are given the option to either allow or deny applications in accessing their account information like name, picture and other account information. Thus, in this post, you will be guided on how you can change the Privacy settings of these apps to allow or deny them permission to access not just your account info but for all users, as well as specific apps in Windows 10.
The user account information is part of the Privacy data in Windows 10 that you can control easily using the Settings app. In fact, you can revoke or grant access permission for your account information, all the users and specific applications to do that, follow each one of the instructions provided below carefully.
Allow or deny apps permission to account info for yourself:
Step_1: The first thing you have to do is open Settings. From there, select Privacy.
Step_2: After that, scroll and look for Account info and select it.
Step_3: Now turn off the toggle button for the “Allow apps to access your account info” option if you want to deny apps permission to your account info. But if you want to allow them access, simply turn the toggle button on. Keep in mind that when you allow access or permission, you can select which apps can access your picture, name, and other account info by simply using the settings on the page you’re currently in.
Now if you want to allow or deny apps to access your account info for all the users, here’s what you have to do:
Step_1: First, open Settings and click on the icon for Privacy.
Step_2: Next, scroll down until you see the Account info located on the left side and then click on it.
Step_3: After that, click on the Change button under the “Allow access to account info on this device” section. If you want to deny account info access for all other users, then turn the toggle button off. Doing so will automatically disable not just the account info access for all users but also for all the apps as well.
On the other hand, if you want to allow or deny account info access to specific apps, you can do so by following these steps:
Step_1: As you did earlier, go to Settings and click on the Privacy icon.
Step_2: After that, scroll down and select Account info located on the left side.
Step_3: Now turn on or off the toggle button under the “Choose which apps can access your account info” section if you want to deny or allow specific apps permission to access Account Info. If you’ve turned on the toggle button under the “Allow apps to access your account info”, all the apps get access permissions by default.
 Error Causes
Error Causes
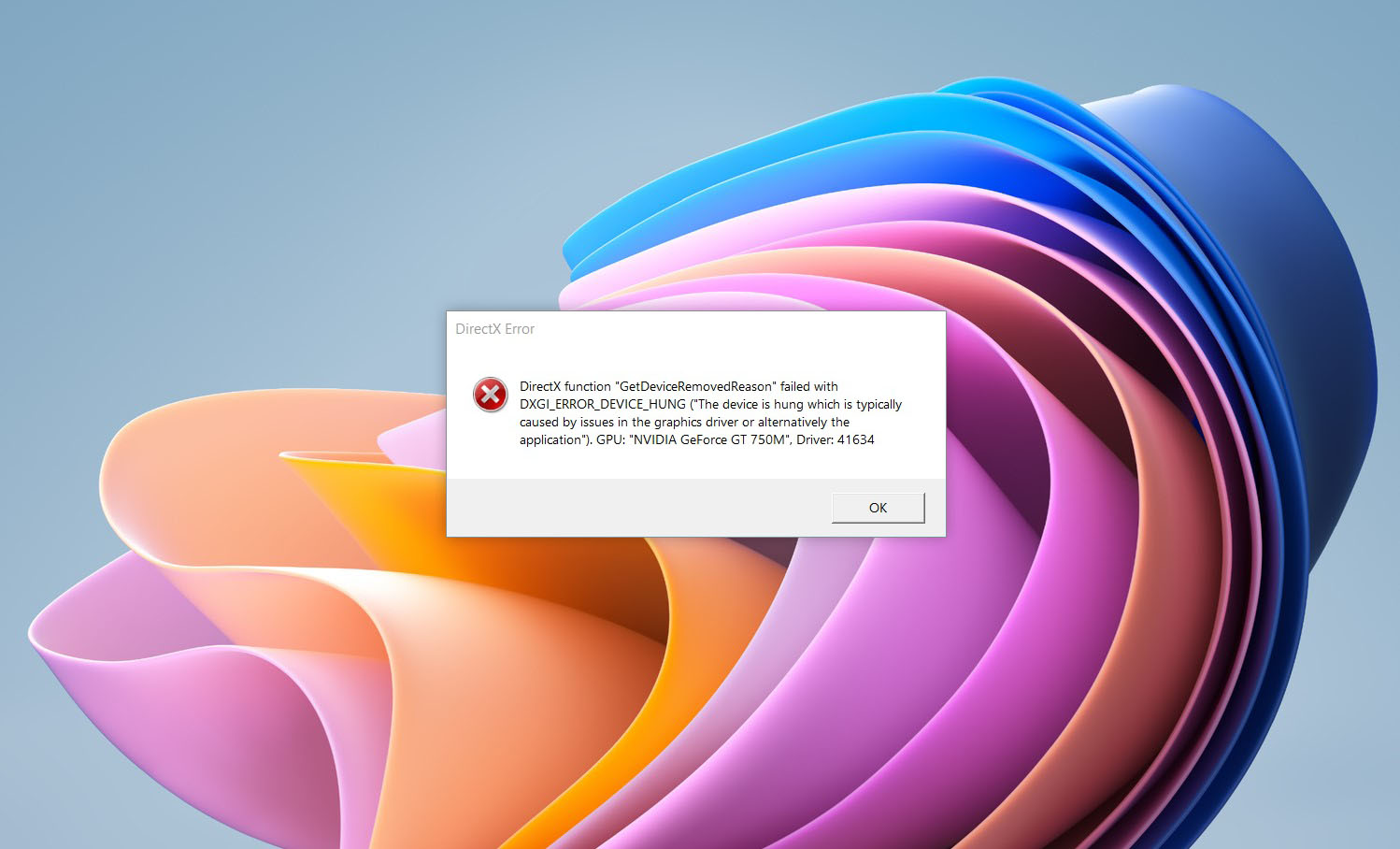 If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
 They can encrypt files in order to make you pay for a decrypter, they can straight up delete files or even cause some hardware damage. Like mentioned before protecting yourself is important, but protecting does not mean only having antivirus software installed, information, where are common places in which they lurk and could be picked up, is also very important. That is why we are exploring in this article the most common place where you can pick viruses or other malware.
They can encrypt files in order to make you pay for a decrypter, they can straight up delete files or even cause some hardware damage. Like mentioned before protecting yourself is important, but protecting does not mean only having antivirus software installed, information, where are common places in which they lurk and could be picked up, is also very important. That is why we are exploring in this article the most common place where you can pick viruses or other malware.

