There are a lot of online services and a lot of ways to get your public IP address. One of them being typing whats my IP in Google search and you will get immediate results. But there is a way to get the same information inside Windows 10 which could be very useful if for any reason you can not connect to mentioned services. By checking public IP directly inside your windows you can make sure that the issue for not being able to open some websites is not due to your public IP.
In order to use this Windows feature, we will be checking our public IP using Windows PowerShell.
To open Power Shell in Windows first press ⊞ WINDOWS + R to open the run dialog
 Inside run dialog type Powershell and press ENTER
Inside run dialog type Powershell and press ENTER
In the Powershell type in the following command and press ENTER
(Invoke-WebRequest -uri "http://ifconfig.me/ip").Content
When the command finishes you will see what is your public IP address, if you wish to know more about your connection type in and press ENTER:
Invoke-RestMethod -Uri ('https://ipinfo.io/')
This command will provide you with further information like city, region, country, and others.

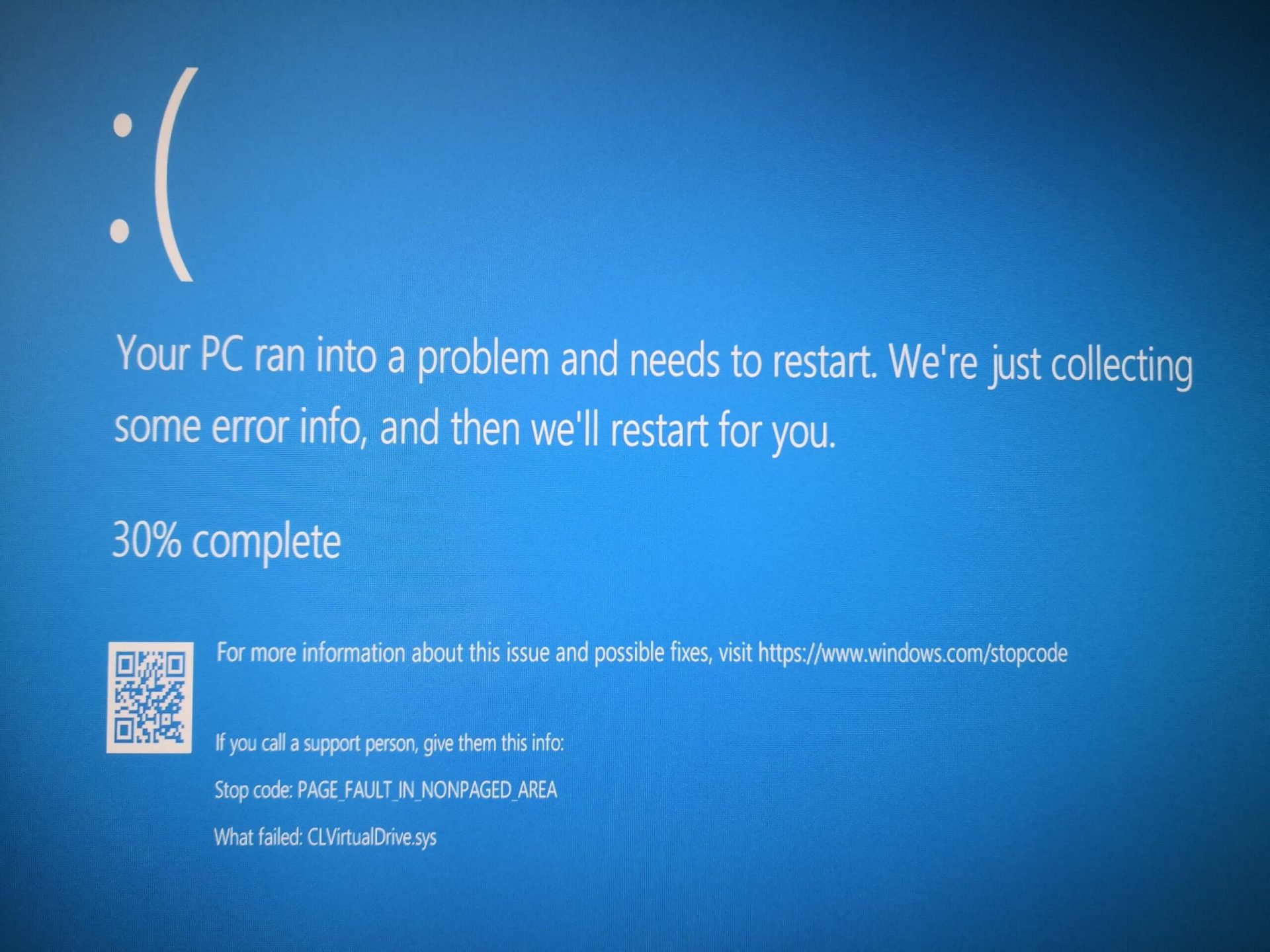 Rollback using system restore
Rollback using system restoreProduct Version: 1.0.0.0 Original File Name: crss.exe Entry Point: 0x000C5AAE
 Error Causes
Error Causes This is not the first time that Intel is trying to enter the GPU field but its adventures so far were, well let us agree not so good. All of that is hoping to be changed with the upcoming ARC GPU. The first generation of Arc graphics, code-named Alchemist and previously known as DG2, will support desktop PCs and laptops and is set to arrive in the first quarter of 2022.
Alchemist will have hardware-based Ray tracing and AI-driven supersampling. This indicates that GPU is aimed to compete in the Hi-end spectrum and battle side by side with Nvidia and AMD on the market. Alchemist will also pack full DirectX 12 Ultimate support.
Intel also released names for the next upcoming future generations of ARC GPUs: Battlemage, Celestial & Druid. More information about ARC products will be released later this year.
“Today marks a key moment in the graphics journey we started just a few years ago. The launch of the Intel Arc brand and the reveal of future hardware generations signifies Intel’s deep and continued commitment to gamers and creators everywhere,” Roger Chandler, Intel vice president, and general manager of client graphics products and solutions.
This is not the first time that Intel is trying to enter the GPU field but its adventures so far were, well let us agree not so good. All of that is hoping to be changed with the upcoming ARC GPU. The first generation of Arc graphics, code-named Alchemist and previously known as DG2, will support desktop PCs and laptops and is set to arrive in the first quarter of 2022.
Alchemist will have hardware-based Ray tracing and AI-driven supersampling. This indicates that GPU is aimed to compete in the Hi-end spectrum and battle side by side with Nvidia and AMD on the market. Alchemist will also pack full DirectX 12 Ultimate support.
Intel also released names for the next upcoming future generations of ARC GPUs: Battlemage, Celestial & Druid. More information about ARC products will be released later this year.
“Today marks a key moment in the graphics journey we started just a few years ago. The launch of the Intel Arc brand and the reveal of future hardware generations signifies Intel’s deep and continued commitment to gamers and creators everywhere,” Roger Chandler, Intel vice president, and general manager of client graphics products and solutions.  Once it opens, click on Device Manager to open it,
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.
Once it opens, click on Device Manager to open it,
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.