Error Code 0x8007001 - What is it?
Error Code 0x8007001 occurs during installations that take place in Windows 10. Various versions of this same error have also been present in previous editions of the software and the methods to resolve the error across these versions are the same
Common symptoms include:
- Inability to complete the installation process for updates, programs, and system versions.
- Installations quitting out in the middle of the process, particularly as the files are unpacked.
Several solutions for Error Code 0x8007001 require the user to complete semi-complex tasks. If you aren’t comfortable with the processes necessary to finish the methods below, make sure that you get in touch with a certified professional who is familiar with the Windows operating system to assist you in the resolution of the error code.
Solution
 Error Causes
Error Causes
In many cases, Error Code 0x8007001 is caused by an installation disk that is not functioning properly or installation files that have been corrupted or changed. When this is the case, the operating system will not be able to begin actually installing the files and will instead hang up as the files are unpacked from the installation set.
Further Information and Manual Repair
For Error Code 0x8007001 to be repaired properly, the missing or corrupted installation files need to be repaired or the system needs to be able to recognize the files that it is missing. This can require some advanced computing knowledge. If you don’t feel comfortable with the idea of undertaking the methods below on your own, contact a computer repair technician who can assist you in following these steps.
Method One: Load the Install Files on an Alternative Disk
In some cases, the operating system simply cannot recognize the installation files that are present on the disk in question, whether it is on a hard drive, a set of downloaded files, or files from a flash drive. If this is the case on your particular machine, the simplest way to work around the problem is to load the installation files onto an alternative disk source, whether it be a flash drive, CD, DVD, or secondary hard drive. After these files have been properly loaded onto that alternative disk, attempt to run the installation from the alternative source instead.
If this method is successful, it means that the system may have had trouble recognizing the files involved in the installation from the first source, but that the files themselves were not corrupted or changed.
Make sure that you save the alternative disk source after your installation is complete in case you ever need to do a fresh installation on your machine.
Method Two: Clean Your Disc and Your Drive
If you are installing files from a DVD or CD, check to make sure that the back of the disc is free from scratches and dust. If there are no visible marks on the disc, you may need to open up your disk drive to see if there is a build-up of dust or debris inside of the drive. If this is the case, simply clean your drive and re-attempt your installation process from the included disk.
Method Three: Run the Windows Update Troubleshooter and Update Your Programs
If the error code is still appearing on your machine, you can open up your Windows Update tool and run the troubleshooting wizard, which will then scan your machine to see if there are any potential problems that it can fix. Next, run the Update tool itself if there are any updates that need to be performed. Sometimes, this can resolve the error at hand. Make sure to restart your computer after any updates or changes have been made so that you can ensure that they are applied by the operating system appropriately.
Method Four: Use An Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise,
download and install a powerful automated tool.
 Once it opens, click on Device Manager to open it,
Once it opens, click on Device Manager to open it,
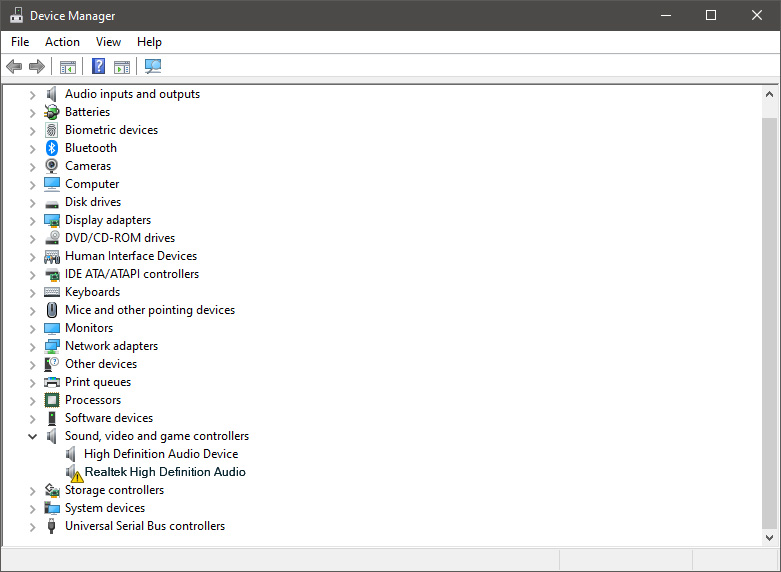 If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.

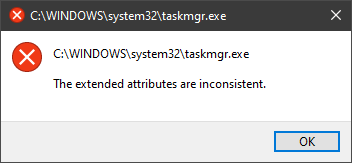 In this guide, we will show you common ways in fixing Extended Attributes are inconsistent errors inside your Windows that are easy to do and less time-consuming than complete reinstallation of the system.
In this guide, we will show you common ways in fixing Extended Attributes are inconsistent errors inside your Windows that are easy to do and less time-consuming than complete reinstallation of the system.
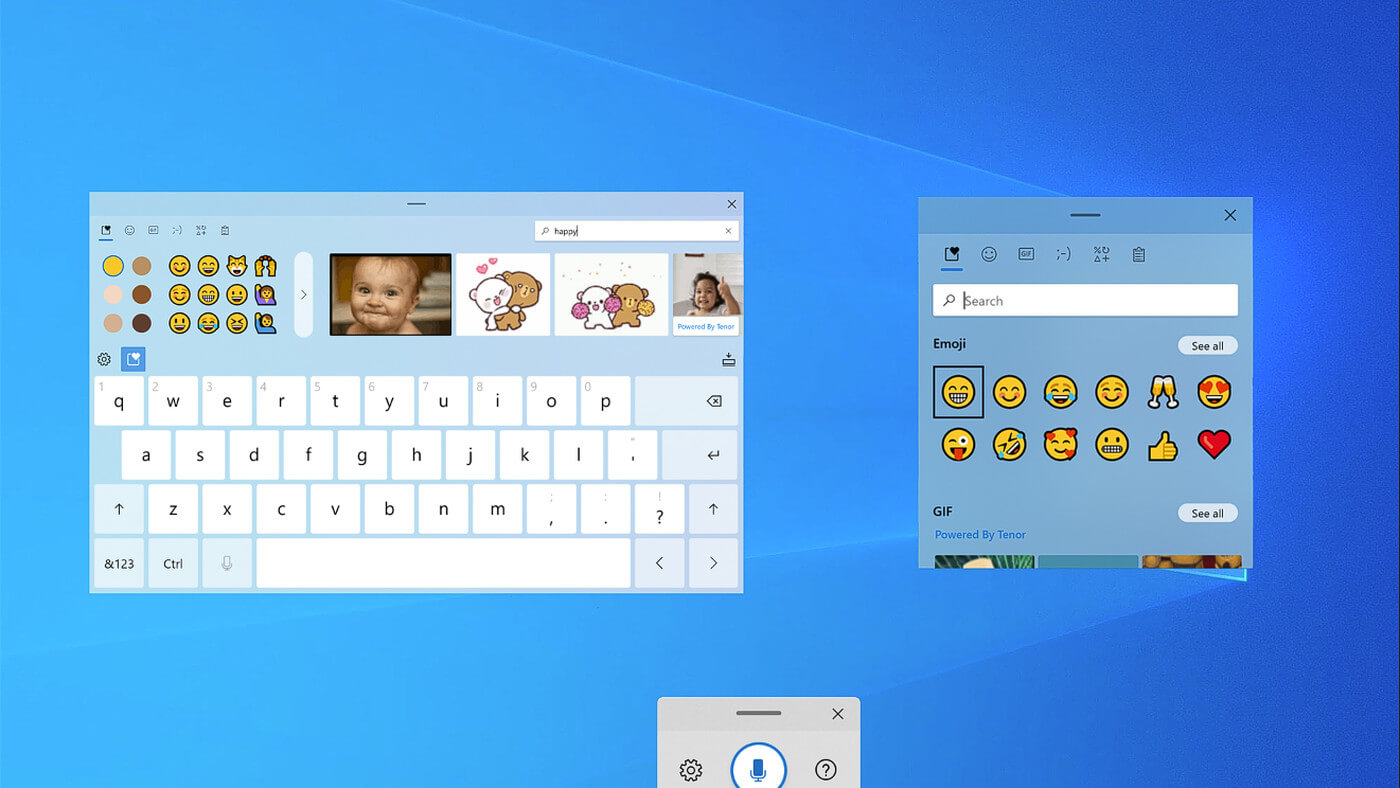 If by any chance you are working on a touchscreen PC, tablet, or any similar device and have no access to a hardware keyboard there is a way to place Touch Keyboard on your screen for easy typing, and you can enable icon on the taskbar for easy access.
If by any chance you are working on a touchscreen PC, tablet, or any similar device and have no access to a hardware keyboard there is a way to place Touch Keyboard on your screen for easy typing, and you can enable icon on the taskbar for easy access.
 Inside run dialog type Powershell and press ENTER
In the Powershell type in the following command and press ENTER
Inside run dialog type Powershell and press ENTER
In the Powershell type in the following command and press ENTER

