Error Code 0x80070003, 0x20007 - What is it?
Update Error 0x80070003, 0x20007 One of the most common errors encountered by users who updated to Windows 10 is the Error Code 0x80070003-0x20007. Normally, this error code is accompanied by the message saying “Windows could not search for new updates. An error occurred while checking for new updates or your computer” or “Error(s) found: Code 0x80070003 Windows update encountered an unknown error”.
This update-related error is often encountered any time while your device automatically installs updates once there’s an available system update or during manually installing updates for a specific app. Regardless if you are using a tablet, laptop, or PC, this update-related error could occur after upgrading your system to Windows 10.
Solution
 Error Causes
Error Causes
There are several reasons why the update-related Error Code 0x80070003-0x20007 occurs. This includes the following:
- Windows Firewall-related problem
- A conflict in your device’s system might be present
- Not enough space in your RAM
- Not enough space in your installation disk
- Problems in your system memory
Further Information and Manual Repair
An effective way to address problems like the Error Code 0x80070003-0x20007 is by applying certain manual repair methods. However, ensure that you strictly follow instructions since one slight slip-up might result in critical issues. If you’re not knowledgeable enough, it would be best to consult help from a professional Windows technician or you can make use of an automated tool to solve any issues you’re encountering.
When you encounter the update-related Error Code 0x80070003-0x20007, you must take action immediately to address the problem to lessen the risk of losing all your data or damaging the Windows registry host.
In fixing Error Code 0xC1900101-0x30018, you can repeat the same steps used for 0xc000021a (Method One) then apply the following steps as well:
- Uninstall your antivirus prior to upgrading your system
- Ensure that you have a simple machine name with no periods, dashes, or hyphens.
- Restart several times then try again.
- Disable the General USB Devices in your machine like the Smart Card Reader.
- If you use a SCSI hard disk, ensure that you have available drivers you can use as your storage such as a thumb drive, and ensure as well that it is connected. Once you’re on the Windows 10 setup, click on Custom Advanced Option then use the Load Driver command in order to load the right driver for the SCSI drive. If this fails, try switching to an IDE-based hard disk.
- Once done, perform a clean boot then try restarting the device again.
- If you are upgrading your system using the .ISO file, disconnect your device from the Internet during setup. If your device is connected to the Internet by LAN or Wi-Fi, you need to disable both first then proceed to set up again.
- If you’re performing the update through Windows Update, disconnect from the Internet LAN or Wi-Fi once the download reaches 100% then proceed with the installation.
- If this still does not work, you can try using the .ISO file in upgrading.
- Switch to a local account if your machine is connected to a domain.
- Disconnect all external devices attached to your machine including gaming controllers, external hard disk, USB keys, and printers.
If the above steps still do not work, you can try performing a repair by doing the following steps:
- Put the installation disc into the disc drive. Afterward, boot the computer.
- Once the message: “Press any key to boot from CD or DVD…” appears, press any key.
- Choose a language, currency, time, and a keyboard or another input method. Click Next.
- Click on Repair your computer
- Select the operating system that you wish to repair then click Next
- Open the Command Prompt by clicking it in the System Recovery Options dialog box.
- Type BOOTREC /FIXMBR then hit Enter
- Type BOOTREC /FIXBOOT then hit Enter
- Type Drive:bootBootsect.exe /NT69 All then hit Enter
Can’t seem to put up with the long and technical manual repair process? You can still fix this error by downloading and installing a powerful automated tool that will surely get the job done in a jiffy!

 To personalize the lock screen do:
To personalize the lock screen do: The World of Superhero movies has gone through some interesting variations, from good ones to bad ones, from big-budget ones to small ventures, even from large well-known characters to niche ones.
No matter what you think of some of them no one would disagree that since the release of Iron Man and starting Marvel cinematic universe superheroes movies exploded in popularity.
Following the Superhero craze, let’s see what is coming up in comic books transferred to big screens with their release dates.
The World of Superhero movies has gone through some interesting variations, from good ones to bad ones, from big-budget ones to small ventures, even from large well-known characters to niche ones.
No matter what you think of some of them no one would disagree that since the release of Iron Man and starting Marvel cinematic universe superheroes movies exploded in popularity.
Following the Superhero craze, let’s see what is coming up in comic books transferred to big screens with their release dates.
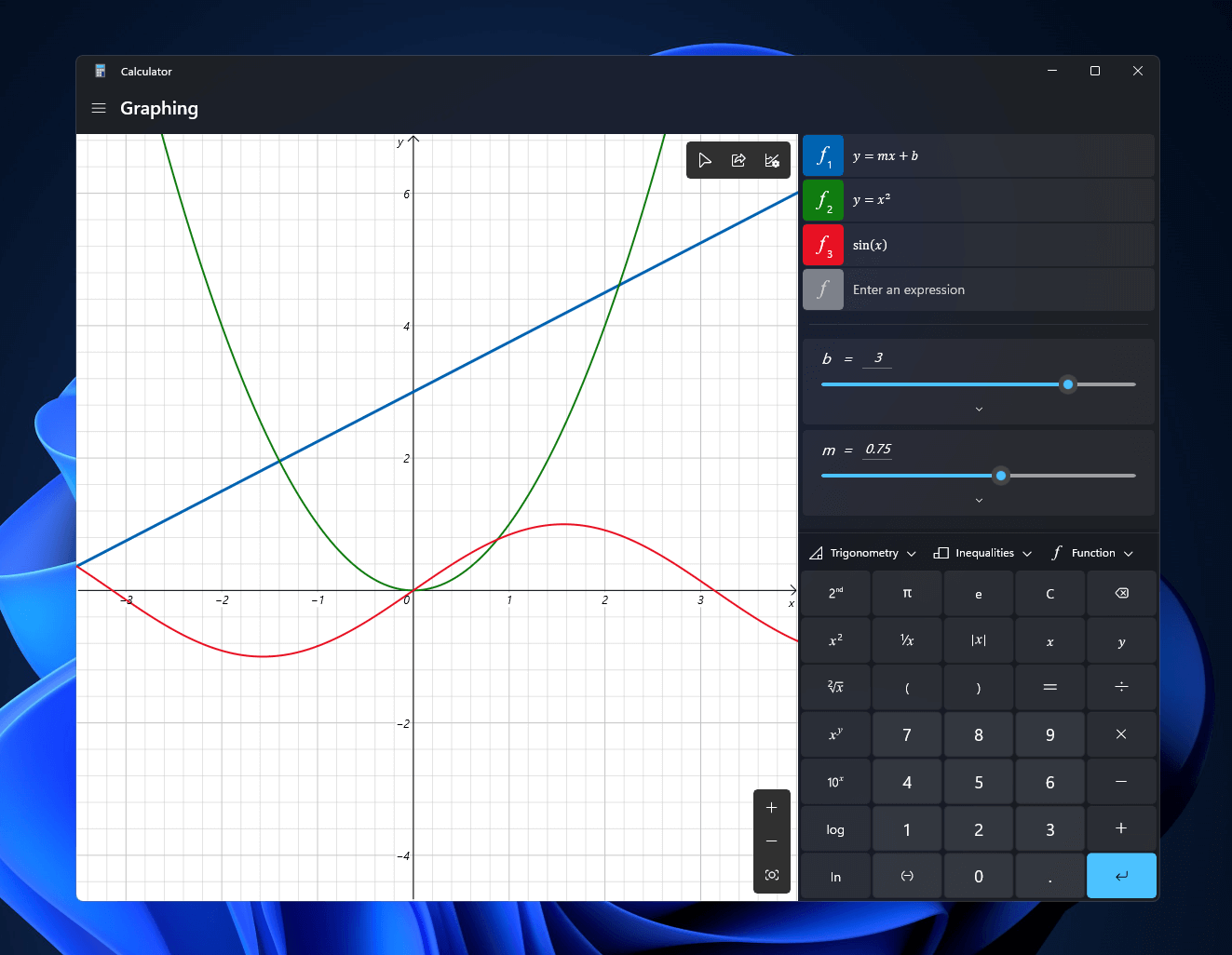 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
 Inside run dialog type Powershell and press ENTER
In the Powershell type in the following command and press ENTER
Inside run dialog type Powershell and press ENTER
In the Powershell type in the following command and press ENTER

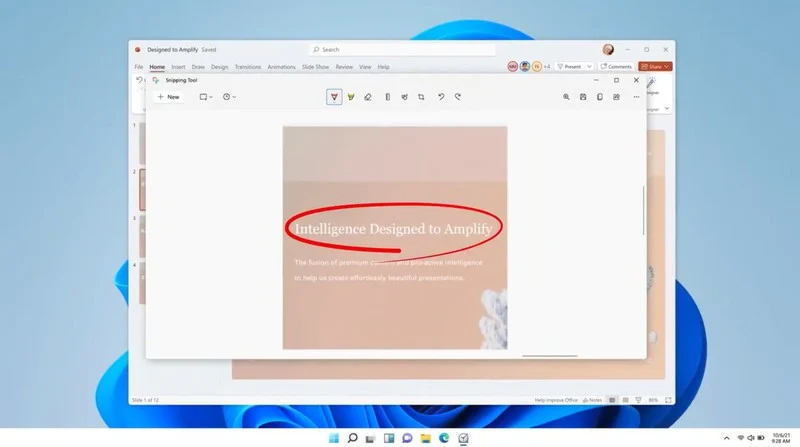 The latest update from Panos Panay on Twitter is including New and redesigned Snipping tool inside Windows 11. From the shared video, we can see that it includes modern Windows 11 UI redesign and it looks and feels like a part of Windows 11.
More things that can be seen from the shared video is that it looks like the new snipping tool is a merged version of the old with snip & sketch.
It is good to see that it is still possible to capture screen with easier way natively inside Windows 11 but some more functionality would be more welcome I guess.
Users were asking for added functions for a long time like adding simple text for example but from shared video, no new features were presented so for some users 3rd party solutions will still be the way to go.
The new and redesigned Snipping tool will roll out with the next update and we will see then about all new features inside it firsthand. Until then, take care.
The latest update from Panos Panay on Twitter is including New and redesigned Snipping tool inside Windows 11. From the shared video, we can see that it includes modern Windows 11 UI redesign and it looks and feels like a part of Windows 11.
More things that can be seen from the shared video is that it looks like the new snipping tool is a merged version of the old with snip & sketch.
It is good to see that it is still possible to capture screen with easier way natively inside Windows 11 but some more functionality would be more welcome I guess.
Users were asking for added functions for a long time like adding simple text for example but from shared video, no new features were presented so for some users 3rd party solutions will still be the way to go.
The new and redesigned Snipping tool will roll out with the next update and we will see then about all new features inside it firsthand. Until then, take care. 