jZip is a software utility published by Bandoo Media and is classified as a Potentially Unwanted Program. The software is an archive tool that used to compress and extract files in the rar, zip, and other formats. The program is typically bundled upon installation with other unwanted applications and is itself often installed in co-bundles. As of publication time, over 40 AntiViruses have flagged jZip as malicious or potentially unwanted.
It injects itself in Windows shell, providing quick access to the program by right-clicking on any file. jZip displays it's advertising in your browser, instead of the default search results, to better do this, it collects information about your browsing history and your current browsing session, so it can better target ads.
This software, upon install, defines an auto-start registry key in your system, this allows the software to launch every time your computer is rebooted, no matter what Windows account you log in to, it also adds Windows Tasks, to allow it to launch by itself at random times, even when closed.
About Potentially Unwanted Applications
If you have ever downloaded software programs from the internet (shareware, freeware, etc,), odds are high you’ve unintentionally installed unwanted programs on your personal computer. Potentially Unwanted Programs (PUP), also referred to as Potentially Unwanted Applications (PUA), are applications that you never wanted in the first place and quite often come bundled with freeware software. Once installed, most of these applications can be hard to remove and become more of a nuisance rather than a necessity.
The idea of PUP was actually coined to define this crapware as something other than malware. The primary reason for this is that most PUPs get into users’ computers not because they exploit security vulnerabilities, for instance, but because the users grant consent to install it – unwittingly in many instances. Nevertheless, there isn’t any doubt that PUPs are still bad news for PC users as they could be incredibly damaging to the computer in lots of ways.
What do PUPs do on your computer, precisely?
The unwanted programs after installation display a lot of annoying pop-up advertisements create fake alerts, and quite often it even pushes the end-user to buy the software. PUPs which come as browser add-ons and toolbars are widely identifiable. Not just they needlessly take up space on your computer screen, toolbars could also manipulate search results, monitor your browsing activities, decrease your internet browser’s overall performance, and slow your net connection to a crawl.
They might seem innocent but PUPs tend to be spyware. The worst part of setting up a PUP is the spyware, adware, and keystroke loggers that might lurk inside. Even if the PUPs aren’t inherently malicious, these programs still do absolutely nothing good on your PC – they will take valuable system resources, slow down your computer or laptop, weaken your device’s security, and make your PC more susceptible to trojans.
Some tips on protecting yourself from unwanted software
• Read the EULA meticulously. Look for clauses that say that you have to accept advertisements and pop-ups or bundled programs from the company.
• Typically, when setting up a program you will get two options, ‘Standard Installation (recommended)’ and ‘Custom Installation’. Don’t pick ‘Standard’ as unwanted programs will automatically be installed that way!
• Have a solid anti-virus program such as Safebytes Anti-Malware that will protect your personal machine from PUPs. Once you install this software, the defense against viruses and PUPs is already switched on.
• Avoid installing freeware software you will not utilize. Turn off or get rid of toolbars and internet browser extensions you don’t really need.
• Only download programs from the original providers’ websites. Avoid download portals since they use their own download manager to bundle extra programs along with the initial download.
Can't Install Safebytes Anti-malware because of a Virus? Do This!
Malware may cause several kinds of damage to computers, networks, and data. Some malware types alter browser settings by including a proxy server or change the computer’s DNS configuration settings. In such cases, you will be unable to visit some or all of the websites, and therefore unable to download or install the required security software to clear out the infection. So what to do if malicious software keeps you from downloading or installing Safebytes Anti-Malware? Follow the instructions below to eliminate malware in alternate ways.
Make use of Safe Mode to fix the issue
In Safe Mode, you are able to modify Windows settings, un-install or install some software, and eliminate hard-to-delete viruses. In case the virus is set to load immediately when the computer starts, switching to this particular mode may well prevent it from doing so. In order to get into Safe Mode or Safe Mode with Networking, press the F8 key while the system is booting up or run MSConfig and find the “Safe Boot” options in the “Boot” tab. After you restart the PC into Safe Mode with Networking, you may download, install, and update the anti-malware program from there. After installation, run the malware scanner to remove most standard infections.
Download the security program using an alternate internet browser
Web-based viruses can be environment-specific, aiming for a particular web browser or attacking particular versions of the browser. The most effective solution to avoid this issue is to opt for an internet browser that is known for its security measures. Firefox contains built-in Phishing and Malware Protection to help keep you safe online.
Create a portable USB antivirus for eliminating viruses
Another solution is to save and run an anti-malware software tool completely from a USB drive. Adopt these measures to employ a USB drive to clean your corrupted system.
1) Download Safebytes Anti-Malware or MS Windows Defender Offline onto a clean computer.
2) Plug the Flash drive into the uninfected computer.
3) Double-click the exe file to open the installation wizard.
4) When asked, choose the location of the USB drive as the place in which you want to store the software files. Follow the activation instructions.
5) Now, plug the thumb drive into the corrupted PC.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Run Full System Scan to detect and clean-up up all kinds of malware.
SafeBytes Anti-Malware Features
These days, anti-malware software can protect your laptop or computer from different kinds of internet threats. But how to select the right one among several malware protection application that is available in the market? Perhaps you might be aware, there are many anti-malware companies and tools for you to consider. Some of them are good, some are decent, while some will ruin your computer themselves! You must pick one that is dependable, practical, and has a good reputation for its malware source protection. On the list of recommended software programs is SafeBytes Anti-Malware. SafeBytes carries a superb track record of top-quality service, and customers seem to be happy with it.
Safebytes is one of the well-established PC solutions companies, which offer this comprehensive anti-malware program. Once you’ve got installed this software program, SafeByte's state-of-the-art protection system will ensure that absolutely no viruses or malicious software can seep through your computer.
SafeBytes anti-malware comes with a myriad of enhanced features which sets it aside from all others. Here are a few typical features found in this application:
Active Protection: SafeBytes provides real-time active monitoring service and protection against all known computer viruses and malware. This software will constantly monitor your PC for any suspicious activity and updates itself continuously to keep current with the newest threats.
Most effective AntiMalware Protection: By using a critically acclaimed malware engine, SafeBytes offers multilayered protection that is designed to catch and remove viruses and malware which are concealed deep in your computer system.
Safe Browsing: SafeBytes gives an instant safety rating about the web pages you are about to check out, automatically blocking harmful sites and make sure that you’re certain of your safety while browsing the world wide web.
Fast Multithreaded Scanning: Safebytes Anti-Malware, using its enhanced scanning engine, gives super-fast scanning which can promptly target any active internet threat.
Minimal CPU Usage: SafeBytes is a lightweight tool. It consumes a really small amount of processing power as it works in the background which means you won’t observe any computer performance issues.
24/7 Customer Support: You will get 24/7 technical support to quickly resolve any issue with your security application.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove Jzip without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by Jzip


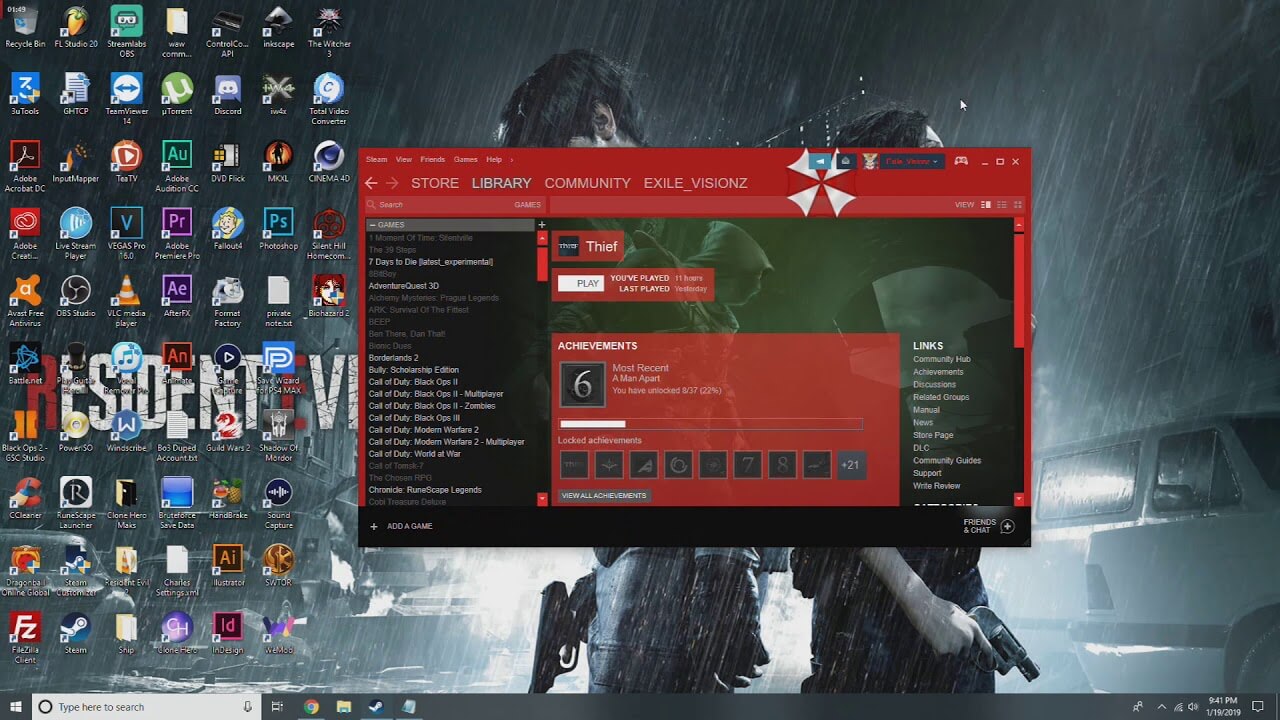 Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend
Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend 
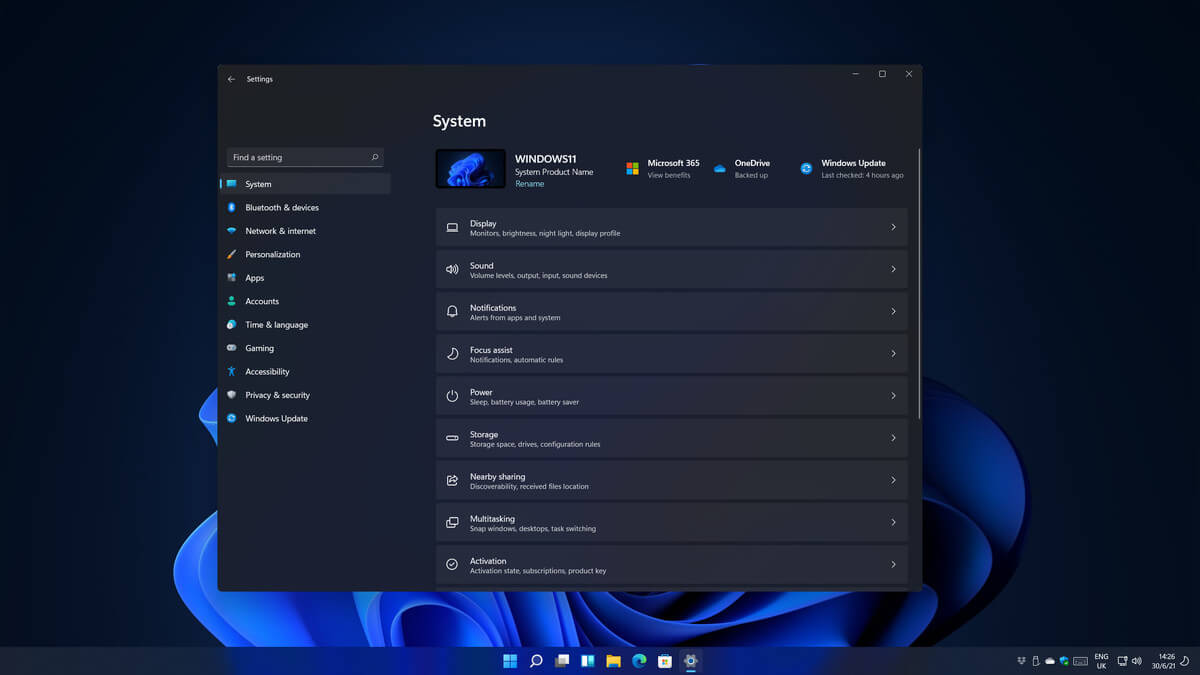 Same as Windows 10, Windows 11 also keeps track of date and time using an internet time server. But in a case that you need to change the date or time for any kind of reason here is a guide for that process:
Same as Windows 10, Windows 11 also keeps track of date and time using an internet time server. But in a case that you need to change the date or time for any kind of reason here is a guide for that process: