
A not long time ago we had an article about the deep WEB and dark WEB here on errortools.com explaining its origins and its purpose. The article can be found here if you are interested:
https://errortools.com/windows/what-is-deep-and-dark-web/
Now at this point in time, we want to present you with 15 great Deep WEB sites that could offer you some information not found anywhere else, that could offer you some privacy, or simply to have some fun and safely explore how it is like to be part of deep WEB.
Take notice that for successful visiting of given sites you will need to have installed TOR browser. More about Tor browser itself can be found here:
https://errortools.com/blog/software-review-series-tor-browser/ and its official website for download here:
https://www.torproject.org/download/
Make sure that you copy the onion link and paste it into your TOR browser in order to access the site. That being said, let’s begin.
Mail2Tor
http://mail2tor2zyjdctd.onion/
If you want secure and private ways of sending your emails then look no further. Mail2Tor uses a webmail client and encrypts each email received or sent, combine that for not storing IP addresses and you have a private and safe environment for your emails.
The Hidden Wiki
http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page
The Hidden Wiki is the go-to site if you want to explore more of deep WEB since it is the site of collected .onion sites. Think of it as a registry of onion sites that want to be accessed publicly but offer anonymity.
TorLinks
http://torlinksd6pdnihy.onion/
TorLinks is another site focusing on .onion site listings. Site themselves are divided into categories and are easy to find. Take note that .onion sites come and go so make sure to visit frequently both The Hidden Wiki and TorLinks in order to be updated.
Torch Search Engine
ttp://xmh57jrzrnw6insl.onion/
Torch is the oldest and most well-known search engine for dark web links, with its database of over a million .onion websites there is a chance that you will find what you are looking for on it.
DuckDuckGo
http://3g2upl4pq6kufc4m.onion/
Integrated into TOR itself as a default search engine DucDuckGo has proven itself to be a great competitor and challenger to Google. But unlike Google, DuckDuckGo will not track you nor store your search activities making it a great general private search engine.
Facebook
https://www.facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion/
Yup, Facebook has its own .onion version of its popular platform. Now since Facebook itself is a social media platform anonymity is out of the question but with .onion routing, you can have and maintain a Facebook account from locations where you normally could not like in some countries where Facebook.com is banned.
Galaxy3
http://galaxy3bhpzxecbywoa2j4tg43muepnhfalars4cce3fcx46qlc6t3id.onion/
Galaxy3 is also a social platform, the site is mostly populated with code experts and other individuals posting all kinds of stuff.
The Dark Lair
http://vrimutd6so6a565x.onion/index.php/Board
Dark Lair was the first image exchange website that evolved into a social network. One difference from the other two mentioned is that you can engage in the website without registration as an anonymous user.
Pro Publica
https://www.propub3r6espa33w.onion/
The aim of the five-time Pulitzer Prize winner ProPublica is “To expose abuses of power and betrayals of the public trust by government, business, and other institutions, using the moral force of investigative journalism to spur reform through the sustained spotlighting of wrongdoing.”
It’s the first major online publication to have a .onion address. The non-profit newsroom is funded by organizations such as the Sandler Foundation and has made countless contributions to the fight for free speech and privacy.
Soylent News
http://7rmath4ro2of2a42.onion/
Soylent news is an onion site that well brings news. The difference from other sites of the same content is that Soylent news is community moderated without any big names involved so it is authentic in its content.
CIA
ttp://ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion/
Tor’s history is an unlikely tale. It was created by the U.S Navy with the purpose of helping informants in foreign nations to communicate safely over the Internet. The Central Intelligence Agency (CIA), in that spirit, released a .onion site so that people from across the globe can browse their resources securely and anonymously.
Secure drop
https://secrdrop5wyphb5x.onion/
Secure drop is a platform for changing leaked information and for journalists to communicate with their leads in private. It is used by Washington Post, Pro Publica, and The Guardian.
Hidden Answers
http://answerszuvs3gg2l64e6hmnryudl5zgrmwm3vh65hzszdghblddvfiqd.onion/
Hidden Answers is Reddit or Quora of the dark web but as in the spirit of the dark web, all discussed topics and stories are in total anonymity.
SCI-HUB
http://scihub22266oqcxt.onion/
With over 50 million research papers in the domain of science shared freely, Sci-Hub eliminates all barriers of free knowledge and offers a unique approach to education and scientific information.
Smartmixer.IO
http://smrtmxdxognxhv64.onion/
Smartmixer is a bitcoin mixer. The service scrambles your bitcoin with other users making your purchases completely anonymous.
And that's it. 15 dark WEB onion sites you need to visit. I hope that you enjoyed the list and found something useful in it. Also, note that onion links can change overnight so if any of provided links do not work just go to DuckDuckGo and search for the site with the onion at the end.
 Error Causes
Error Causes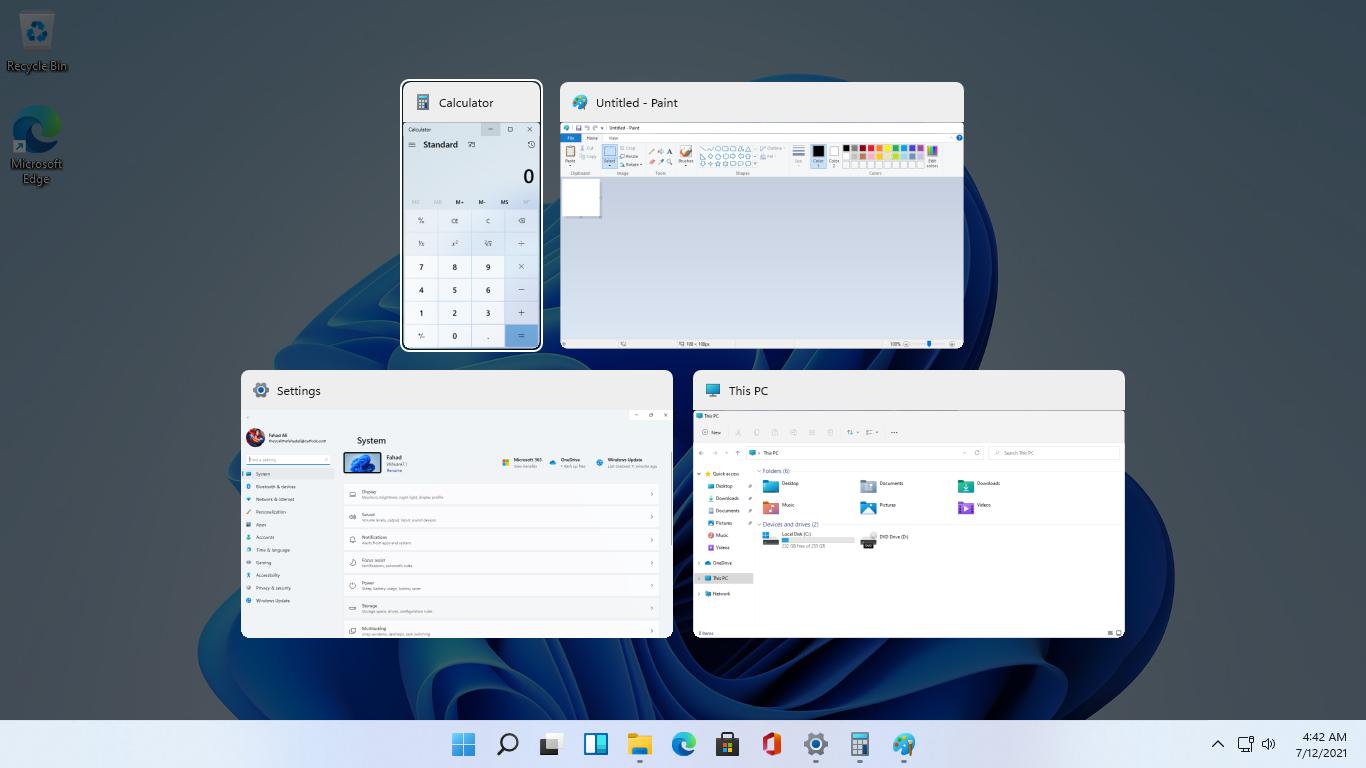 As in previous Windows 10, inside Windows 11 also when you press the ALT + TAB key combination you will get a preview of all running applications along with all Browser tabs so you can go through them and pick the one you want to switch to.
As in previous Windows 10, inside Windows 11 also when you press the ALT + TAB key combination you will get a preview of all running applications along with all Browser tabs so you can go through them and pick the one you want to switch to.
 Over time Applications change, some for the better some for worse. Some of them even stop receiving updates and are old and vulnerable. Sometimes standards change and some file types are not used anymore. Software evolves along with technology and that is good.
Keeping old and useless applications inside your Windows is not so good. From various exploits to simply taking up space, maybe even slowing down OS it is always wise and good to clean your Windows from unwanted old applications.
In this article, we will be mentioning some relics of old and providing you with an explanation of why you should remove them from your system if by any chance you still have them on it.
Over time Applications change, some for the better some for worse. Some of them even stop receiving updates and are old and vulnerable. Sometimes standards change and some file types are not used anymore. Software evolves along with technology and that is good.
Keeping old and useless applications inside your Windows is not so good. From various exploits to simply taking up space, maybe even slowing down OS it is always wise and good to clean your Windows from unwanted old applications.
In this article, we will be mentioning some relics of old and providing you with an explanation of why you should remove them from your system if by any chance you still have them on it.
 A not long time ago we had an article about the deep WEB and dark WEB here on errortools.com explaining its origins and its purpose. The article can be found here if you are interested:
A not long time ago we had an article about the deep WEB and dark WEB here on errortools.com explaining its origins and its purpose. The article can be found here if you are interested: 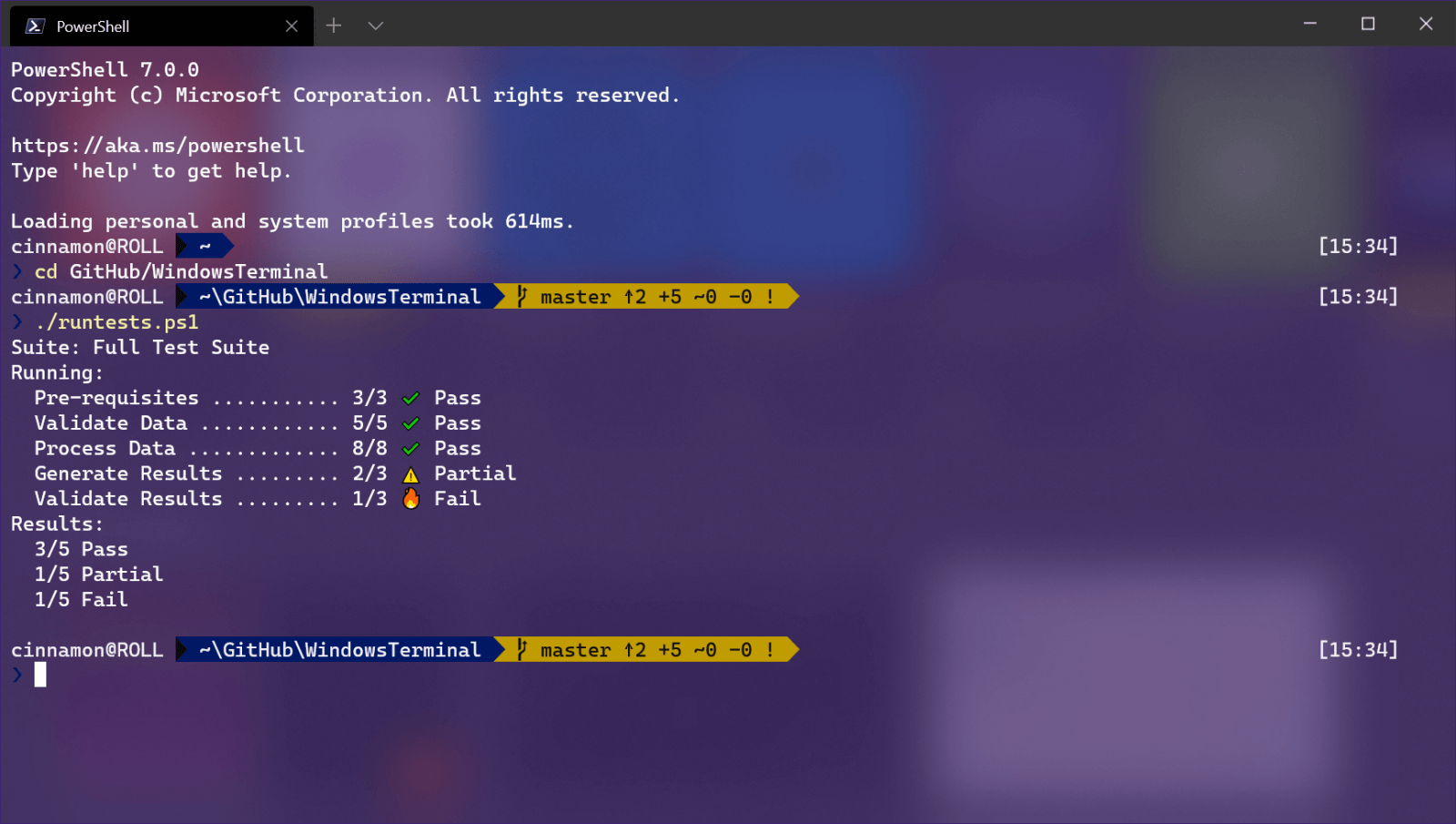 Windows Terminal is a new free Microsoft terminal sort of application. When you open either Power Shell or Command Prompt in Windows they will be opened in different windows, and if you want several of each you will have several windows of each on your screen.
Windows Terminal fixes this by opening each of the Instances of Command Prompt and Power Shell as separate tabs inside itself making it much easier to manage multiple instances of named applications.
You can also run both Power Shell and Command prompt tabs in the same Windows Terminal. Luckily running command prompt and power shell in different tabs is not the only thing you can do. Windows Terminal lets you choose your own theme, it has emoji support, GPU rendering, split panes, and many more customizable options.
Windows 11 will have Terminal as the default command-line environment for opening Power Shell or Command prompt, even Windows Subsystem for Linux (WSL)
Windows Terminal is a new free Microsoft terminal sort of application. When you open either Power Shell or Command Prompt in Windows they will be opened in different windows, and if you want several of each you will have several windows of each on your screen.
Windows Terminal fixes this by opening each of the Instances of Command Prompt and Power Shell as separate tabs inside itself making it much easier to manage multiple instances of named applications.
You can also run both Power Shell and Command prompt tabs in the same Windows Terminal. Luckily running command prompt and power shell in different tabs is not the only thing you can do. Windows Terminal lets you choose your own theme, it has emoji support, GPU rendering, split panes, and many more customizable options.
Windows 11 will have Terminal as the default command-line environment for opening Power Shell or Command prompt, even Windows Subsystem for Linux (WSL)
 So let's dive into this cool handheld in more detail and find out why we like it so much.
So let's dive into this cool handheld in more detail and find out why we like it so much.
