Boost My PC is a program developed by 1.0.2.6. During setup, a scheduled task is added to Windows Task Scheduler in order to launch the program at various scheduled times (the schedule varies depending on the version). When installed, it will add a context menu handler to the Windows shell in order to provide quick access to the program.
Boost My PC presents itself as a legit PC speed-up utility, it scans your computer for problems and displays errors that need to be fixed. Upon accepting to fix these alleged errors, you are asked for a Payment in order to activate this product for a few months.
Many anti-virus scanners have marked this application as a Potentially Unwanted Program, and while Boost My PC is not so harmful on its own, it comes bundled with other Potentially Unwanted Programs that might harm your computer.
About Potentially Unwanted Applications
If you’ve ever downloaded and installed a software package via the internet (shareware, freeware, etc,), odds are high you’ve unwittingly installed unwanted programs on your computer. Potentially Unwanted Programs (PUP), also referred to as Potentially Unwanted Applications (PUA), are programs that you never wanted in the first place and sometimes come bundled with freeware software. Once installed, most of these applications can be hard to remove and become more of a pain rather than a benefit.
It’s clear by the name – unwanted applications – but did not really constitute “malware” in the traditional sense. Much like malware, PUPs create problems when downloaded and installed on your machine, but what makes a PUP different is that you grant consent to download it – though the truth is vastly different – the software installation bundle actually tricks you into agreeing to the installation. Regardless of whether it is considered malware or otherwise, PUPs are almost always detrimental to the user as they could bring on adware, spyware, keystroke logging, along other dangerous “crapware” features on your computer.
Exactly how do unwanted programs look like?
Potentially Unwanted Programs appear in different forms and varieties, however, most times, these are typically adware programs that show annoying pop-up adverts and advertisements on web pages you drop by. PUPs that come as browser add-ons and toolbars are widely identifiable. These toolbars change your homepage and your search engine in the installed web browser, track your web activities, influence your search results with redirects and sponsored links, and eventually slow down your web browser and diminish your browsing experience.
PUPs lie inside the gray part of the software spectrum. They may carry keyloggers, dialers, along with other software built right into them that might monitor you or send out your sensitive information to 3rd parties. Even if the PUPs aren’t inherently malicious, these programs still do practically nothing good on your personal computer – they will take valuable resources, slow your PC, weaken your device’s security, making your PC more susceptible to malware.
Tips on protecting yourself from PUPs
• Read the EULA carefully. Look for clauses that say that you ought to accept advertising and pop-ups or bundled programs from the company.
• Choose the “custom” install whenever downloading a program. In particular, look closely at those tiny boxes that have been checked as default, where you might ‘agree’ to receive ads or install software bundlers.
• Use an ad blocker/pop-up blocker; Deploy anti-malware products such as Safebytes Anti-malware. These types of applications will establish a wall between the computer and cybercriminals.
• Avoid installing freeware software you will not make use of. Avoid installing browser extensions and applications you aren’t knowledgeable about.
• Only download software from the original providers’ sites. Stay away from download portals because they use their own download manager to pack additional programs together with the initial download.
What you can do if Malware Prevents You From Downloading Anything?
Malware could cause all sorts of damage after they invade your system, from stealing your private details to deleting files on your computer system. Certain malware types alter web browser settings by including a proxy server or change the computer’s DNS configuration settings. In these cases, you’ll be unable to visit certain or all websites, and therefore unable to download or install the required security software to remove the infection. So what you should do if malicious software prevents you from downloading or installing Anti-Malware? Even though this kind of problem can be difficult to get around, there are a few steps you can take.
Download the application in Safe Mode with Networking
If any virus is set to run immediately when Windows starts, stepping into safe mode could block this attempt. Just the minimum required applications and services are loaded whenever you start your PC in Safe Mode. To start your Windows XP, Vista, or 7 computers in Safe Mode with Networking, follow the instructions below.
1) Press the F8 key continuously as soon as your system boots, but before the large Windows logo shows up. This should bring up the Advanced Boot Options menu.
2) Select Safe Mode with Networking with arrow keys and hit ENTER.
3) Once you get into this mode, you should have online access once again. Now, use your internet browser normally and navigate to https://safebytes.com/products/anti-malware/ to download and install Safebytes Anti-Malware.
4) Immediately after installation, run a full scan and let the software remove the threats it discovers.
Switch over to a different web browser
Some malware only targets specific web browsers. If this sounds like your situation, employ another web browser as it may circumvent the computer virus. If you’re not able to download the security software using Internet Explorer, this means the virus may be targeting IE’s vulnerabilities. Here, you must switch to another internet browser like Chrome or Firefox to download the Safebytes program.
Install and run anti-virus from a USB drive
Another option is to store and operate an anti-malware program completely from a Flash drive. Try these simple steps to clear up your infected computer by using portable anti-malware.
1) Download the anti-malware on a virus-free computer.
2) Plug the Flash drive into the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded software, with a .exe file extension.
4) Select the drive letter of the flash drive as the place when the wizard asks you where you want to install the anti-malware. Do as instructed on the computer screen to finish off the installation process.
5) Transfer the pen drive from the uninfected computer to the infected computer.
6) Double-click the EXE file to open the Safebytes tool right from the thumb drive.
7) Click on “Scan Now” to run a scan on the affected computer for viruses.
Ensure the Safety of Your PC by Installing SafeBytes Anti-Malware
If you’re looking to buy anti-malware for your computer, there are numerous brands and packages for you to consider. A few are very good ones, some are ok types, and some are merely fake anti-malware programs that could damage your personal computer themselves! You have to be very careful not to pick the wrong product, especially if you purchase a paid application. On the list of strongly recommended software programs is SafeBytes Anti-Malware. SafeBytes carries a very good history of top-quality service, and clients appear to be happy with it.
SafeBytes anti-malware is a trustworthy tool that not only secures your system completely but is also very easy to use for people of all ability levels. Through its cutting-edge technology, this software protects your personal computer against infections caused by various kinds of malware and other threats, including spyware, adware, computer viruses, worms, trojan horses, keyloggers, potentially unwanted programs (PUPs), and ransomware.
There are plenty of wonderful features you’ll get with this particular security product. These are some of the highlighted features included in the software.
World-class AntiMalware Protection: Built on a highly acclaimed anti-virus engine, this malware removal application has the capacity to detect and get rid of several stubborn malware threats like browser hijackers, PUPs, and ransomware that other common antivirus programs will miss.
Live Protection: SafeBytes gives you round-the-clock protection for your PC restricting malware attacks in real-time. It will regularly monitor your pc for hacker activity and also provides users with advanced firewall protection.
Safe Web Browsing: SafeBytes provides an instant safety rating about the web pages you’re going to visit, automatically blocking risky sites and making sure that you are certain of your online safety while browsing the world wide web.
Low CPU Usage: This program is lightweight and can run silently in the background, and that does not impact your computer efficiency.
24/7 Customer Support: SafeBytes provides 24/7 technical support, automatic maintenance, and updates for the best user experience.
To sum it up, SafeBytes has created a meaningful anti-malware solution that is aimed to protect your computer against various malware. Malware problems can become a thing of the past once you put this software program to use. For top protection and the best value for your money, you can’t get better than SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you don’t wish to use an automated tool and like to eliminate Boost My PC manually, you could possibly do so by going to the Add/Remove Programs menu in the Control Panel and deleting the offending program; in cases of web browser add-ons, you could remove it by going to the browsers Add-on/Extension manager. You will definitely also want to reset your internet browser.
If you opt to manually delete the system files and Windows registry entries, make use of the following list to ensure that you know precisely what files to remove before executing any actions. Please remember that this is for skilled users only and may be challenging, with wrong file removal leading to additional PC errors. In addition, certain malware is capable of replicating itself or preventing deletion. It is highly recommended that you carry out the removal procedure in Safe Mode.
 Error Causes
Error Causes
 Fear not because we had this issue and tried several things in order to overcome the problem and after some time here is a list of what can you do if you are facing this exact issue. The list is written from most simple solutions to more complex ones and it is advisable to follow it as presented. That being said, let's dive into solving the problem.
Fear not because we had this issue and tried several things in order to overcome the problem and after some time here is a list of what can you do if you are facing this exact issue. The list is written from most simple solutions to more complex ones and it is advisable to follow it as presented. That being said, let's dive into solving the problem.

 Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
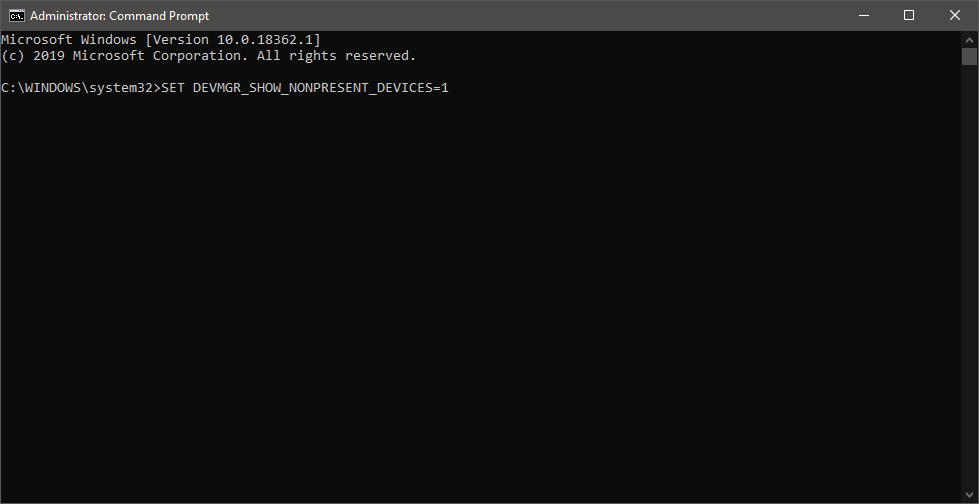
 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
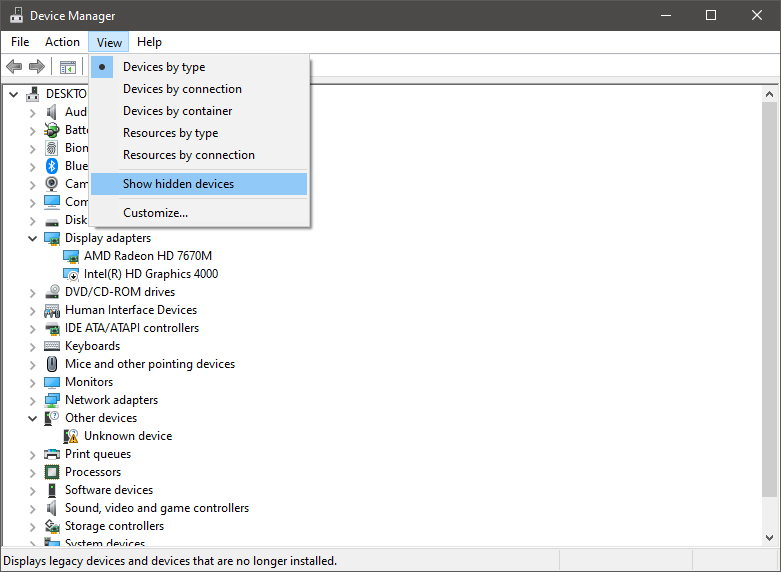
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
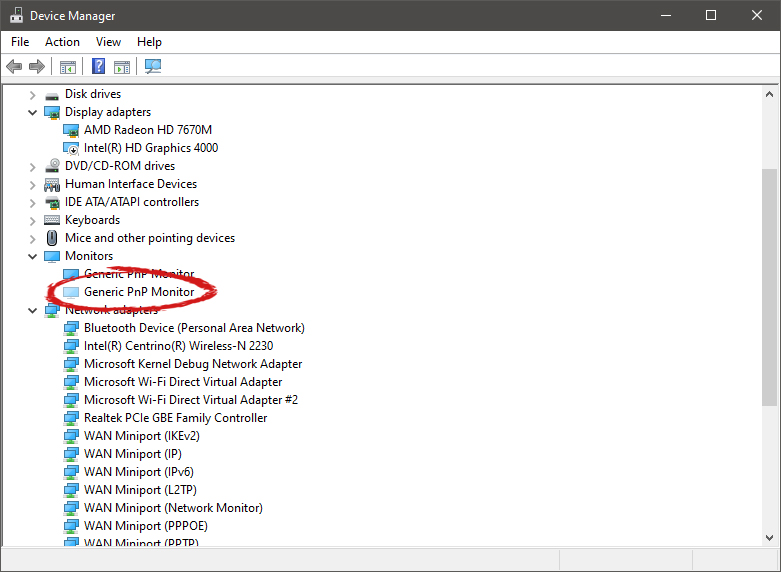 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
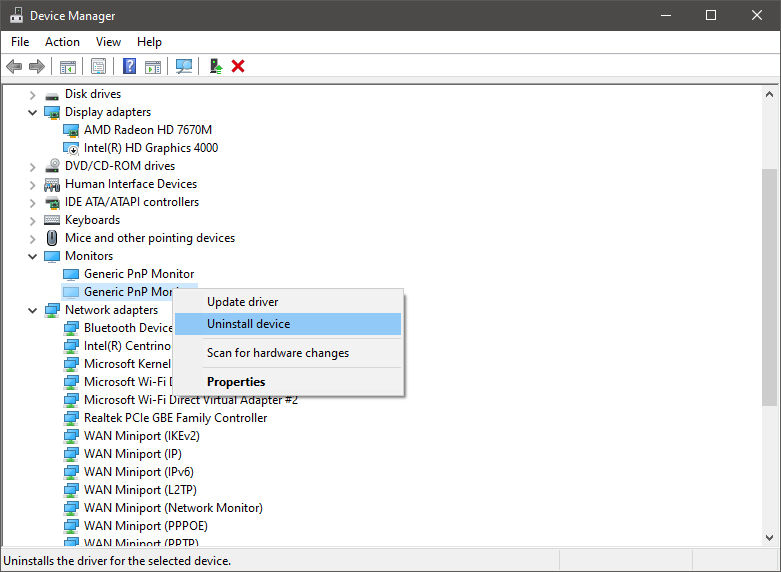 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. 