New Tab Aid is an extension for Google Chrome. It is published by Spigot Inc. It is classified as a potentially unwanted browser hijacker as it injects Yahoo search into your new tab windows. This extension also adds recently viewed tabs under the search bar. It also redirects all your searches to Yahoo instead of your default browser search engine. It is often found bundled with other software found on the internet and not installed directly by the user. For these reasons, numerous anti-malware utilities flag New Tab Aid as potentially unwanted or malicious.
About Browser Hijackers
Browser hijackers (sometimes called hijackware) are a kind of malicious software that changes internet browser configurations without the user’s knowledge or permission. These types of hijacks appear to be increasing at an alarming rate around the world, and they could be actually nefarious and often harmful too. Browser hijackers could do more than just modifying homepages. The idea is to force users to visit specific websites that are looking to improve their website visitor traffic and produce higher ad earnings. Even though it may seem naive, all browser hijackers are damaging and therefore always regarded as security risks. Browser hijackers can even allow other vicious programs without your knowledge to further damage your personal computer.
Major signs that your web browser has been hijacked
There are numerous signs of browser hijacking:
1. the home page of your respective web browser is changed all of a sudden
2. you see new unwanted bookmarks or favorites added, typically directed to advertisement-filled or pornography sites
3. the default web browser settings are changed and/or your default web engine is altered
4. unwanted new toolbars are added to your browser
5. you observe numerous ads show up on your browsers or computer screen
6. your web browser gets sluggish, buggy crashes regularly
7. Inability to navigate to particular websites, particularly anti-malware and other security software sites.
How does a browser hijacker infect a computer?
Browser hijackers might use drive-by downloads or file-sharing networks or even an email attachment in order to reach a targeted computer. Many web browser hijackings come from add-on applications, i.e., toolbars, browser helper objects (BHO), or plug-ins added to browsers to provide them additional features. Browser hijackers sneak into your computer in addition to free software application downloads also that you unintentionally install alongside the original. Popular examples of browser hijackers include Conduit, CoolWebSearch, Coupon Server, OneWebSearch, RocketTab, Searchult.com, Snap.do, and Delta Search.
Browser hijacking can result in severe privacy issues and also identity theft, affect your browsing experience by taking control of outgoing traffic, substantially slows down your personal computer by consuming a lot of resources, and cause system instability also.
How to fix a browser hijack
Certain browser hijacking could be quite easily stopped by discovering and eliminating the corresponding malware software through your control panel. However, most hijackers are hard to get rid of manually. No matter how much you attempt to remove it, it may come back again and again. Moreover, browser hijackers could modify the Windows registry therefore it can be very hard to repair manually, particularly when you’re not a very tech-savvy individual.
Virus Blocking Access To Safebytes Site And Preventing Anti-Malware Downloads - What To Do?
Malware can cause all kinds of damage if they invade your computer, from stealing sensitive information to deleting files on your computer system. Certain malware goes to great lengths to stop you from installing anything on your computer system, especially anti-malware software programs. If you’re reading this, you probably have affected by malware that prevents you from installing a computer security application like Safebytes Anti-Malware. Although this sort of issue will be tougher to get around, there are a few actions you can take.
Eliminate malware in Safe Mode
If any malware is set to load immediately when Microsoft Windows starts, getting into Safe Mode could block this attempt. Just minimal required applications and services are loaded whenever you start your personal computer into Safe Mode. The following are the steps you need to follow to take out viruses in Safemode.
1) Tap the F8 key repeatedly as soon as your PC boots, however, before the large Windows logo shows up. This should bring up the Advanced Boot Options menu.
2) Select Safe Mode with Networking with arrow keys and hit ENTER.
3) When this mode loads, you should have the internet. Now, obtain the malware removal application you want by using the web browser. To install the software, follow the directions within the installation wizard.
4) Once the application is installed, let the diagnostic scan run to eliminate viruses and other threats automatically.
Switch over to an alternate browser
Malicious program code may exploit vulnerabilities on a particular browser and block access to all anti-malware software sites. The most effective solution to avoid this issue is to choose a browser that is well known for its security measures. Firefox contains built-in Malware and Phishing Protection to keep you safe online.
Install and run antivirus from your USB drive
Another way is to download and transfer an antivirus application from a clean computer to run a scan on the affected system. Do these simple measures to clean up your affected computer using a portable antivirus.
1) Download the anti-malware program on a virus-free computer.
2) Insert the USB drive on the same system.
3) Double-click the exe file to open the installation wizard.
4) When asked, select the location of the pen drive as the place in which you want to put the software files. Follow the instructions on the computer screen to finish off the installation process.
5) Now, transfer the USB drive to the infected computer.
6) Double-click the Safebytes Anti-malware icon on the pen drive to run the software.
7) Run Full System Scan to detect and get rid of all sorts of malware.
Ensure the Safety of Your PC by Installing SafeBytes Anti-Malware
These days, anti-malware software can protect your computer from various types of internet threats. But exactly how to decide on the best one among many malware protection application that is available on the market? As you might be aware, there are several anti-malware companies and products for you to consider. Some of them are good, some are ok types, and some will destroy your computer themselves! When searching for antimalware software, pick one that provides reliable, efficient, and full protection against all known viruses and malware. One of the highly recommended software by industry experts is SafeBytes Anti-Malware, the most dependable program for Microsoft Windows.
SafeBytes anti-malware is a powerful, very effective protection tool designed to assist end-users of all levels of computer literacy in detecting and eliminating malicious threats out of their computer. This program could easily detect, remove, and protect your computer from the most advanced malware attacks including spyware, adware, trojan horses, ransomware, parasites, worms, PUPs, along with other possibly damaging software programs.
SafeBytes has excellent features when compared to various other anti-malware programs. Let’s look into some of them below:
Active Protection: Malware programs trying to get into the computer are discovered and stopped as and when detected by the SafeBytes real-time protection shields. This tool will constantly monitor your computer for any suspicious activity and updates itself continuously to keep current with the latest threats.
Antimalware Protection: With its enhanced and sophisticated algorithm, this malware removal tool can identify and remove the malware threats hiding in your PC effectively.
Web Security: Safebytes allots all websites a unique safety rating that helps you to get an idea of whether the webpage you’re about to visit is safe to browse or known to be a phishing site.
Lightweight: SafeBytes is well known for its minimal impact on computer resources and great detection rate of diverse threats. It operates quietly and efficiently in the background so you are free to utilize your personal computer at full power all of the time.
24/7 Customer Service: For any technical concerns or product assistance, you can get 24/7 professional assistance through chat and email.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove NewTabAid without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by NewTabAid


 Windows Terminal is a new free Microsoft terminal sort of application. When you open either Power Shell or Command Prompt in Windows they will be opened in different windows, and if you want several of each you will have several windows of each on your screen.
Windows Terminal fixes this by opening each of the Instances of Command Prompt and Power Shell as separate tabs inside itself making it much easier to manage multiple instances of named applications.
You can also run both Power Shell and Command prompt tabs in the same Windows Terminal. Luckily running command prompt and power shell in different tabs is not the only thing you can do. Windows Terminal lets you choose your own theme, it has emoji support, GPU rendering, split panes, and many more customizable options.
Windows 11 will have Terminal as the default command-line environment for opening Power Shell or Command prompt, even Windows Subsystem for Linux (WSL)
Windows Terminal is a new free Microsoft terminal sort of application. When you open either Power Shell or Command Prompt in Windows they will be opened in different windows, and if you want several of each you will have several windows of each on your screen.
Windows Terminal fixes this by opening each of the Instances of Command Prompt and Power Shell as separate tabs inside itself making it much easier to manage multiple instances of named applications.
You can also run both Power Shell and Command prompt tabs in the same Windows Terminal. Luckily running command prompt and power shell in different tabs is not the only thing you can do. Windows Terminal lets you choose your own theme, it has emoji support, GPU rendering, split panes, and many more customizable options.
Windows 11 will have Terminal as the default command-line environment for opening Power Shell or Command prompt, even Windows Subsystem for Linux (WSL)
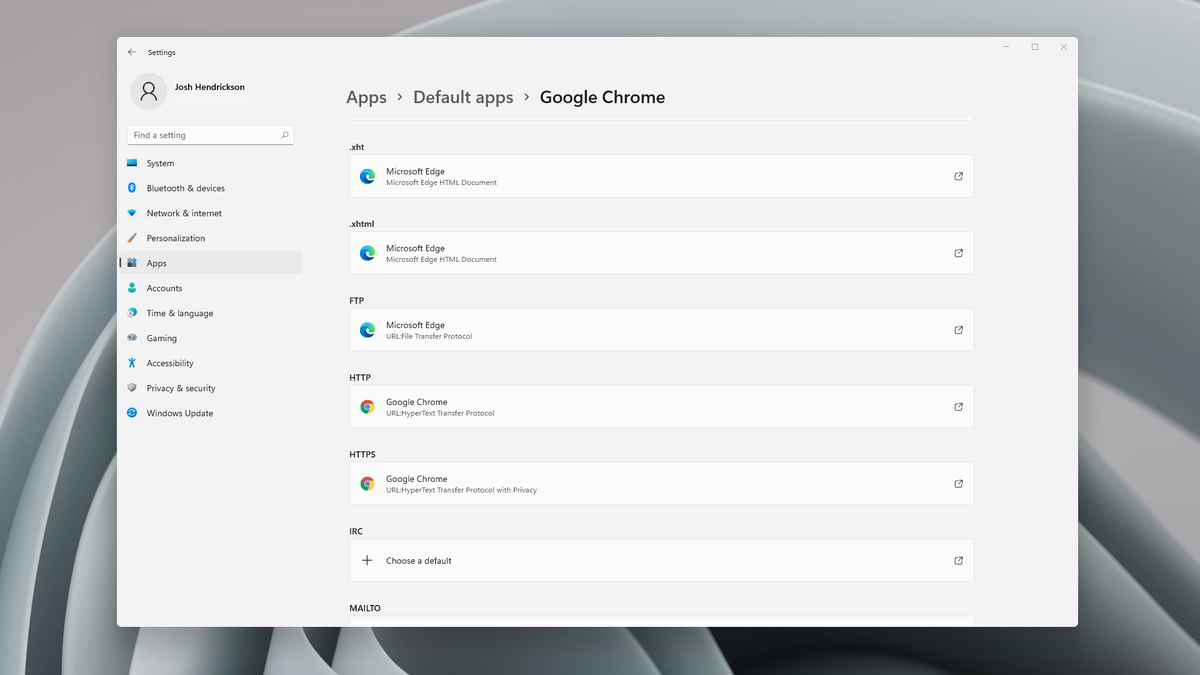 Choosing default browser in settings
Choosing default browser in settings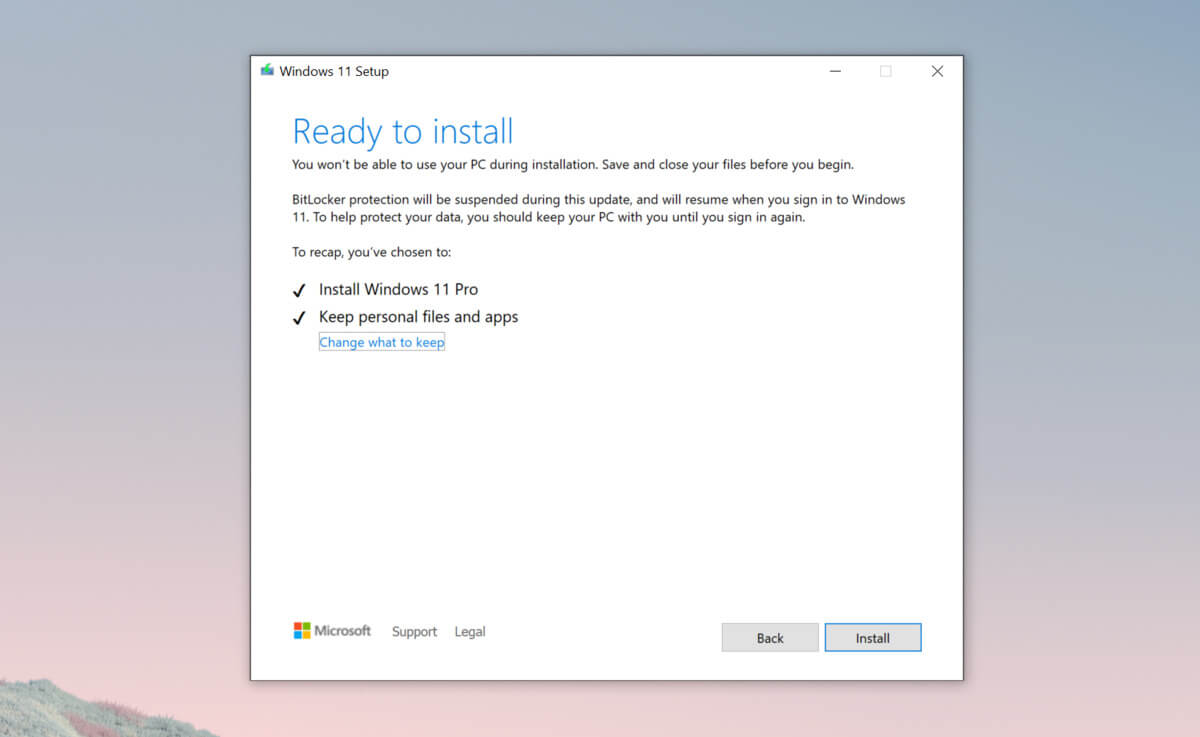 Bypass TPM with changing installation media
Bypass TPM with changing installation media Check the Epic Games Status page
Check the Epic Games Status page

