The Gardening Enthusiast toolbar is another product that is advertised as a helpful addition to your browsing experience when it is really nothing more than the software you should remove as soon as possible. It is touted as a toolbar that will provide you with a lot of useful gardening tips. That is the hook to get you to install it. But, in truth, the only thing that it does is provide you with links to popular gardening websites that you can easily find on any search engine.
When installed the extension will change your default search engine and home page to MyWay.com
While browsing the internet with this extension you will see additional sponsored ads and links throughout your browsing session.
Anti-virus applications have marked this extension as a Browser Hijacker and are therefore marked for removal. While not considered malware, the fact that many users find it to hinder browser performance has led to its detection and flag for optional removal.
About Browser Hijackers
Browser hijacking means a malicious program code has control over and modified the settings of your browser, without your permission. Practically all browser hijackers are made for marketing or advertising purposes. Usually, hijackers will force hits to internet sites of their preference either to increase web traffic producing higher ad earnings, or to obtain a commission for every user visiting there. Nevertheless, it isn’t that harmless. Your internet safety is jeopardized and it is extremely annoying. Once the malware attacks your laptop or computer, it starts to mess things up a whole that slows your PC down to a crawl. In the worse case, you will be forced to tackle serious malware threats too.
Browser hijacking symptoms
The typical symptoms that suggest having this malware on your PC are: your home page has been reset to some unfamiliar website; you see new unwanted favorites or bookmarks added, usually directed to ad-filled or pornography sites; the default online search engine has been changed and the web browser security settings have been lowered without your knowledge; find new toolbars that you didn’t add; you notice lots of pop-up ads on your screen; your web browser gets sluggish, buggy, crashes quite often; Inability to navigate to certain sites, especially anti-malware and also other security software webpages.
Exactly how browser hijacker finds its way to your PC
A browser hijacker can be installed on your computer when you go to an infected site, click an e-mail attachment, or download something from a file-sharing website. They could be included with toolbars, BHO, add-ons, plug-ins, or browser extensions. Other times you might have accidentally accepted a browser hijacker as part of a software program package (generally freeware or shareware). Examples of popular browser hijackers are Fireball, Ask Toolbar, GoSave, CoolWebSearch, Babylon Toolbar, and RocketTab.
Browser hijackers can record user keystrokes to gather potentially invaluable information that leads to privacy issues, cause instability on computers, significantly disrupt user’s browsing experience, and ultimately slow down the PC to a point where it will become unusable.
Removing browser hijackers
Certain browser hijacking could be easily reversed by identifying and eliminating the corresponding malware application from your control panel. Unfortunately, many of the software products used to hijack an internet browser are deliberately designed to be hard to detect or get rid of. You should think of undertaking manual fixes only if you are a tech-savvy person, as risks are associated with tinkering with the computer registry and HOSTS file.
Browser hijackers can be effectively removed by installing anti-malware software on the affected PC. If you need to remove persistent hijackers effectively, install the award-winning anti-malware tool Safebytes Anti-Malware. And employ a system optimizer, like Total System Care, to eliminate all related files in the registry and fix browser issues.
How To Get Eliminate Malware That Is Preventing Anti-Malware Installation?
All malware is inherently harmful, but certain kinds of malicious software do more damage to your computer or laptop than others. Certain malware types alter internet browser settings by including a proxy server or change the computer’s DNS configuration settings. When this happens, you’ll be unable to visit certain or all of the sites, and thus unable to download or install the necessary security software to get rid of the computer virus. If you are reading this, chances are you’re stuck with a virus infection that is preventing you to download and/or install Safebytes Anti-Malware software on your computer. Even though this sort of problem can be harder to get around, there are some steps you can take.
Remove viruses in Safe Mode
Safe Mode is a special, basic version of Microsoft Windows where only the bare minimum services are loaded to prevent viruses as well as other problematic applications from loading. In the event, the malware is set to load immediately when PC boots, shifting to this particular mode can prevent it from doing so. To enter into Safe Mode or Safe Mode with Networking, press F8 while the PC is starting up or run MSCONFIG and locate the “Safe Boot” options under the “Boot” tab. Once you reboot into Safe Mode with Networking, you could download, install, as well as update anti-malware software from there. At this point, you can run the antivirus scan to eliminate viruses and malware without any interference from another application.
Switch over to an alternate internet browser
Malicious code might exploit vulnerabilities on a specific browser and block access to all antivirus software websites. In the event you suspect that your Internet Explorer happens to be hijacked by a virus or otherwise compromised by cybercriminals, the most effective thing to do would be to switch over to a different browser like Firefox, Chrome, or Safari to download your chosen computer security software – Safebytes Anti-Malware.
Install security software on a flash drive
To successfully get rid of the malware, you need to approach the problem of installing the anti-malware program on the affected computer system from a different perspective. To run antivirus from a USB drive, follow these simple measures:
1) Make use of another virus-free computer to download Safebytes Anti-Malware.
2) Plug the USB drive into the clean computer.
3) Double click on the downloaded file to open the installation wizard.
4) When asked, select the location of the pen drive as the place in which you want to store the software files. Follow the activation instructions.
5) Unplug the pen drive. You may now use this portable antivirus on the infected computer.
6) Double-click the anti-malware program EXE file on the pen drive.
7) Click on “Scan Now” to run a complete scan on the affected computer for viruses.
Benefits and Features of SafeBytes Security Suite
If you’re planning to purchase anti-malware for your desktop, there are numerous brands and utilities for you to consider. Some are well worth your money, but most aren’t. You must select a company that creates industry-best anti-malware and has earned a reputation as trustworthy. Among few good applications, SafeBytes Anti-Malware is the highly recommended software program for security-conscious people.
SafeBytes anti-malware is a very effective and easy-to-use protection tool that is designed for end-users of all levels of IT literacy. Using its cutting-edge technology, this application will help you get rid of several types of malware like viruses, worms, PUPs, trojans, adware, ransomware, and browser hijackers.
SafeBytes anti-malware takes PC protection to a totally new level with its enhanced features. Here are some of the features you will like in SafeBytes.
Anti-Malware Protection: Built upon a highly acclaimed anti-virus engine, this malware removal tool can detect and remove several stubborn malware threats such as browser hijackers, potentially unwanted programs, and ransomware that other typical antivirus programs will miss.
Real-time Threat Response: SafeBytes offers real-time active supervision and protection from all known viruses and malware. It will constantly monitor your computer for hacker activity and also gives end-users sophisticated firewall protection.
Safe Browsing: Safebytes allots all sites a unique safety ranking that helps you to have an idea of whether the website you’re about to visit is safe to browse or known to be a phishing site.
Lightweight: SafeBytes is renowned for its low impact on processing power and great detection rate of countless threats. It works silently and efficiently in the background so you are free to make use of your personal computer at full power all the time.
24/7 Premium Support: You will get 24/7 technical support to quickly resolve any issue with your security software.
SafeBytes will keep your personal computer safe from the latest malware threats automatically with hardly any input needed from you again. Malware problems will become a thing of the past once you put this software to use. You’ll get the best all-around protection for the money you spend on SafeBytes Anti-Malware subscription, there is no doubt about it.
Technical Details and Manual Removal (Advanced Users)
If you do not wish to use malware removal software and like to remove Gardening Enthusiast manually, you could do so by going to the Add/Remove Programs menu in the Control Panel and deleting the offending program; in cases of browser add-ons, you may uninstall it by visiting the browsers Add-on/Extension manager. You might also want to reset your home page and search engine providers, and also delete browsing history, temporary files, and internet cookies.
To make sure of complete removal, find the following Windows registry entries on your computer and remove them or reset the values appropriately. However, editing the Windows registry is really a difficult job that only experienced computer users and professionals should attempt to fix the problem. In addition, certain malware keeps replicating which makes it difficult to eliminate. Completing this task in Safe Mode is advised.
 Error Causes
Error Causes
 Hacker group recently came up with claims that they have stolen data from 100 million T-Mobile customers. T-Mobile has responded with confirmation it has been compromised and that over 40 million records were stolen, among them are not just present customers, but anyone who has applied for T-Mobile service as well as past accounts.
Hacker group recently came up with claims that they have stolen data from 100 million T-Mobile customers. T-Mobile has responded with confirmation it has been compromised and that over 40 million records were stolen, among them are not just present customers, but anyone who has applied for T-Mobile service as well as past accounts.
 If your browser of choice is Google Chrome then sit back and enjoy the ride as we are going through some great productivity tips for it.
So without further talking let's dive right into them.
If your browser of choice is Google Chrome then sit back and enjoy the ride as we are going through some great productivity tips for it.
So without further talking let's dive right into them.
 Microsoft starting as of today will block its Office 365 users if they are using Internet Explorer or early versions of Edge browsers.
So if you are using older non Chromium Edge versions of Microsoft browsers you can no longer access Office services until you switch. Now normally I would fully support this kind of decision since Internet explorer is a slow and vulnerable browser and the edge is similar in that regard.
The new edge browser is great and it should be used but the issue I have is that Office 365 is not free, it is a premium feature and I am wondering how Microsoft plans to deal with people that have already paid for service but suddenly cannot access it anymore.
Microsoft starting as of today will block its Office 365 users if they are using Internet Explorer or early versions of Edge browsers.
So if you are using older non Chromium Edge versions of Microsoft browsers you can no longer access Office services until you switch. Now normally I would fully support this kind of decision since Internet explorer is a slow and vulnerable browser and the edge is similar in that regard.
The new edge browser is great and it should be used but the issue I have is that Office 365 is not free, it is a premium feature and I am wondering how Microsoft plans to deal with people that have already paid for service but suddenly cannot access it anymore.  Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
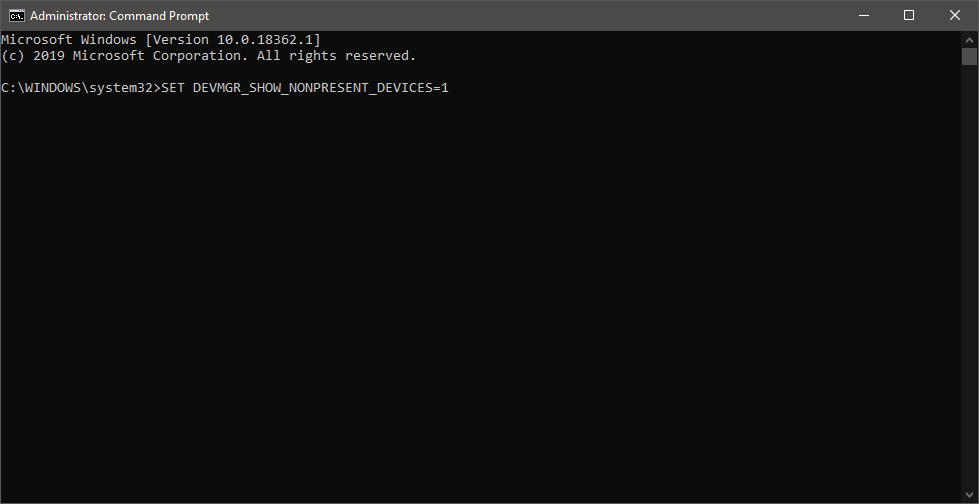 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
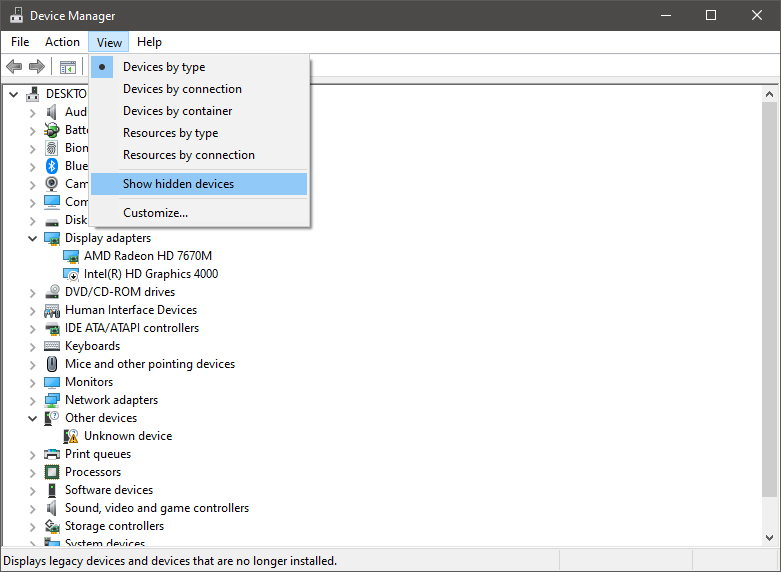
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
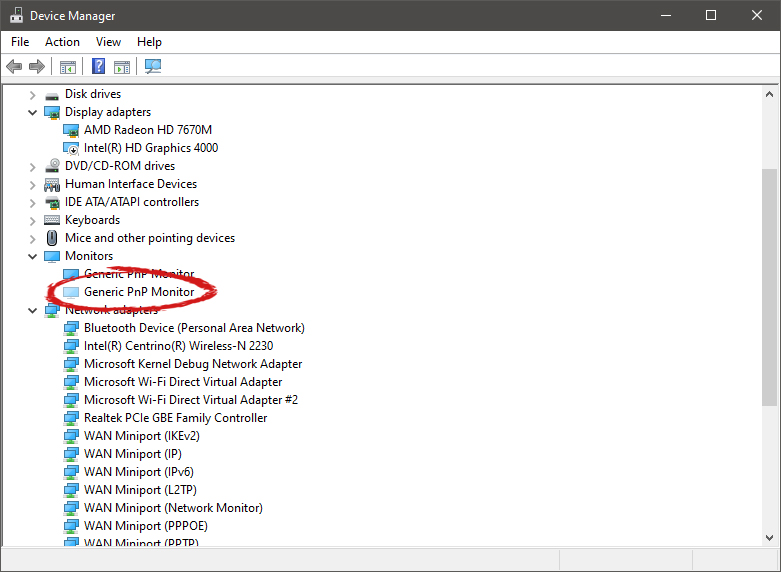 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
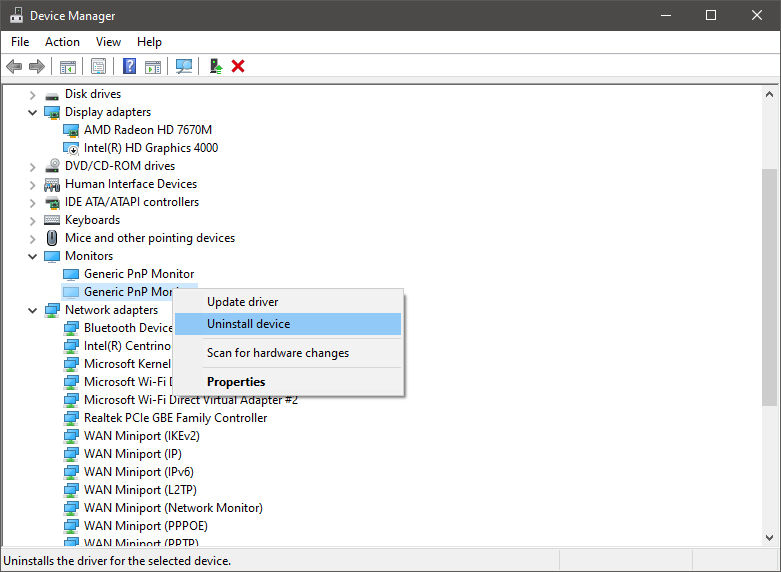 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. 