MySearchDial is a browser hijacker that typically comes bundled with free software on the internet. This web platform designed for searching the internet and offers the installation of its software. This software injects itself into browsers and gains access to your settings, browsing data & user information. This data is distributed to the ad providers without limitation. While covered by their EULA, most users will be unaware of what they agree to with checkboxes selected by default. The software also adds a huge amount of registry keys and links throughout the operating system. Since the software injects itself into many personal files, removing the software results in a total reset of your browser settings. For these reasons MySearchDial is classified as potentially unwanted and is flagged for removal by a number of internet security utilities.
About Browser Hijackers
Browser hijacking is a common type of online fraud where your internet browser configuration settings are altered to allow it to carry out things you do not intend. Practically the majority of browser hijackers are created for marketing or advertising purposes. Usually, hijackers are designed for the benefit of online hackers usually through income generation that comes from forced ad clicks and website visits. Even though it may seem naive, these tools are designed by vicious individuals who always look to take full advantage of you, so that hackers can make money from your naive and distraction. Some browser hijackers are designed to make certain modifications beyond the browsers, like altering entries on the computer registry and letting other types of malware further damage your computer.
How you can know if your internet browser is hijacked
There are several symptoms that point to browser hijacking:
1. your browser’s home page has been reset to some unfamiliar website
2. your web browser is constantly being redirected to pornography websites
3. default online search engine is changed
4. discover new toolbars that you simply didn’t add
5. you observe lots of pop-ups on your computer screen
6. your internet browser has become unstable or starts running slowly
7. you’re blocked to access the websites of security solution providers.
So how exactly does a browser hijacker infect a PC
Browser hijackers can enter a computer in some way or other, including via file sharing, downloads, and e-mail also. They could also come from add-on applications, also called browser helper objects (BHO), web browser extensions, or toolbars. Other times you may have inadvertently accepted a browser hijacker as part of an application package (generally freeware or shareware). Examples of popular browser hijackers are Fireball, Ask Toolbar, GoSave, CoolWebSearch, Babylon Toolbar, and RocketTab.
The existence of any browser hijacker malware on your system might significantly diminish the web browsing experience, track your internet activities that lead to severe privacy concerns, degrade overall system efficiency, and lead to software instability as well.
Getting rid of browser hijackers
Some hijackers could be removed by deleting the free software they were included with or by removing any add-ons you have recently added to your computer system. But, most hijackers are hard to remove manually. Regardless of how much you attempt to get rid of it, it can return over and over again. On top of that, manual removal needs you to execute many time-consuming and complicated actions which are very difficult to carry out for rookie computer users.
Can't Install Safebytes Anti-malware because of a Virus? Do This!
All malware is bad and the effects of the damage could differ based on the specific type of malicious software. Certain malware types alter web browser settings by adding a proxy server or change the PC’s DNS configurations. When this happens, you’ll be unable to visit certain or all sites, and therefore not able to download or install the required security software to remove the malware. If you’re reading this now, you may have probably recognized that virus infection is the reason for your blocked web traffic. So what do if you need to download and install an antivirus application like Safebytes? Although this kind of problem can be difficult to circumvent, there are a few actions you can take.
Install the anti-virus in Safe Mode
If the malware is set to run at Windows startup, then booting in Safe Mode should prevent it. Only minimal required programs and services are loaded when you start your computer or laptop in Safe Mode. To launch your Windows XP, Vista, or 7 PCs in Safe Mode with Networking, do as instructed below.
1) Press the F8 key repeatedly as soon as your computer boots, but before the big Windows logo or black screen with white texts shows up. This will bring up the Advanced Boot Options menu.
2) Use the arrow keys to choose Safe Mode with Networking and press ENTER.
3) Once you get into this mode, you should have access to the internet once again. Now, get the virus removal application you need by using the internet browser. To install the application, follow the guidelines in the installation wizard.
4) As soon as the application is installed, let the scan run to remove viruses and other malware automatically.
Utilize an alternate web browser to download an anti-malware program
Malicious program code might exploit vulnerabilities on a specific internet browser and block access to all anti-virus software websites. If you appear to have a virus attached to Internet Explorer, then switch over to an alternate browser with built-in security features, such as Chrome or Firefox, to download your favorite anti-malware program – Safebytes.
Run antivirus from a pen drive
Another approach is to download and transfer antivirus software from a clean computer to run a virus scan on the affected system. Abide by these steps to run the anti-virus on the affected computer system.
1) Make use of another virus-free computer to download Safebytes Anti-Malware.
2) Plug the Flash drive into the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded software, with a .exe file extension.
4) When asked, select the location of the USB drive as the place where you would like to store the software files. Follow the on-screen instructions to finish the installation.
5) Transfer the USB drive from the clean computer to the infected computer.
6) Double click the Safebytes Anti-malware icon on the thumb drive to run the application.
7) Click on the “Scan Now” button to start the virus scan.
SafeBytes Anti-Malware Features
In order to protect your computer or laptop from many different internet-based threats, it is very important to install an anti-malware application on your PC. However, with countless numbers anti-malware companies in the market, nowadays it is actually difficult to decide which one you should purchase for your PC. Some of them do a good job in getting rid of threats while some will damage your PC themselves. You have to choose a product that has got a good reputation and detects not just computer viruses but other sorts of malware too. When considering commercial antimalware software options, most people choose well-known brands, such as SafeBytes, and are very happy with it.
SafeBytes antimalware is a highly effective and easy-to-use protection tool that is ideal for end-users of all levels of IT literacy. Using its outstanding protection system, this tool will instantly detect and remove most of the security threats, including viruses, adware, browser hijackers, PUPs, trojans, worms, and ransomware.
SafeBytes carries a plethora of amazing features which can help you protect your laptop or computer from malware attack and damage. The following are some popular features found in this software program:
Real-time Active Protection: SafeBytes gives complete and real-time security for your personal machine. They’re highly effective in screening and getting rid of various threats because they’re constantly revised with the latest updates and safety measures.
Most Reliable AntiMalware Protection: Safebytes is made on the very best virus engine in the industry. These engines will identify and remove threats even during the early stages of a malware outbreak.
Internet Security: SafeBytes gives an instant safety rating on the pages you’re going to visit, automatically blocking risky sites and making sure that you’re certain of your safety while browsing the net.
Lightweight: SafeBytes provides total protection from internet threats at a fraction of the CPU load because of its advanced detection engine and algorithms.
24/7 Online Tech Support: Support service is readily available for 24 x 7 x 365 days through email and chats to answer your queries.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove MySearchDial without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by MySearchDial
 Error Causes
Error Causes
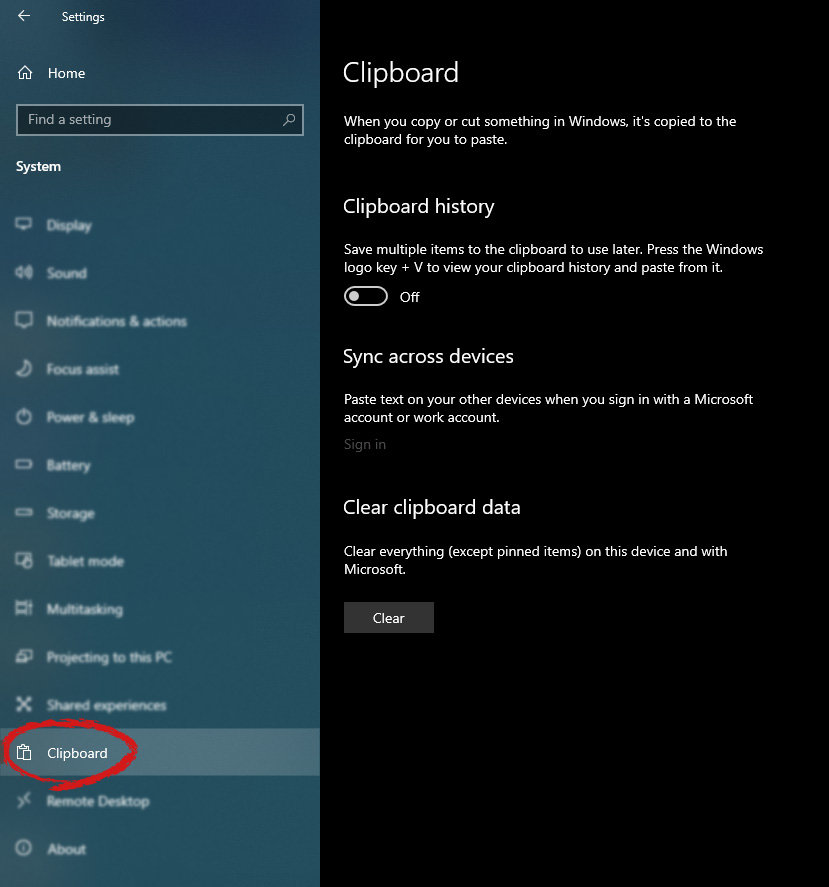
 in system dialog click on the clipboard and on the right screen turn ON CLipboard history.
in system dialog click on the clipboard and on the right screen turn ON CLipboard history.
 Changes and features
Changes and features